网络协议 — IPSec 安全隧道协议族
目录
文章目录
- 目录
- IPSec 安全隧道协议族
- 封装协议
-
- Authentication Header 协议
- Encapsulating Security Payload 协议
- 封装模式
-
- Transport(传输模式)
- Tunnel(隧道模式)
- 安全偶联协商
-
- Security Association 协议
- Internet Key Exchange 协议
- IKE 的对称密钥交换过程
- IPSec NAT-Tranversal
-
- NAT-T 的封装模式
- NAT-T 的协商过程
- IPSec 的 MTU 分片和加密问题
- IPSec Virtual Private Network
-
- IPSec Virtual Tunnel Interface
-
- IPSec VTI 的工作原理
- Linux iptables 与 VTI 的结合
- GRE over IPSec VPN
- L2TP over IPSec VPN
- Strongswan 的应用实践
-
- net2net-psk 网络拓扑
- base configuration
- moon Site
- sun Site
- 测试
- 运维
-
- 常用配置说明
IPSec 安全隧道协议族
IPSec(Internet Protocol Security,互联网协议安全)是一个基于 IP 网络的安全隧道协议族,包含了一系列认证、加密、隧道封装协议。包括:
- 安全认证协议(Authentication Header,AH)
- 安全封装协议(Encapsulating Security Payload,ESP)
- 安全偶联协议(Security Association,SA)
- 安全密钥交换协议(Internet Key Exchange,IKE)
这些协议共同构建了 IPSec 的安全框架:
-
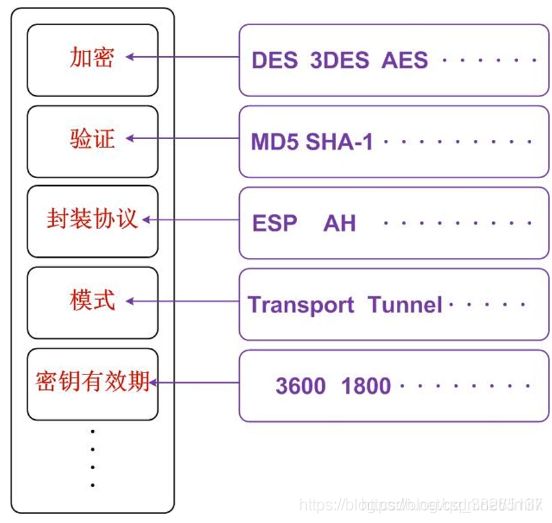
加密算法:用于加密数据,有:
- 对称加密算法:AES、DES、3DES 等。
- 非对称加密算法:RSA、DH(Diffie-Hellman)等。
-
验证算法:用于校验数据完整性,有 MD5、SHA-1、SHA-2 等。
-
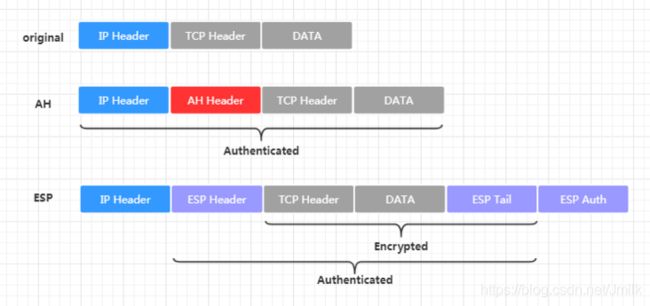
封装模式:IPSec 还支持 Transport(传输模式)和 Tunnel(隧道模式)这 2 种不同的封装模式。不同的封装模式和封装格式可以组合出多种安全特性,在实际应用中需要根据不同的应用场景进行选择,如下图所示。
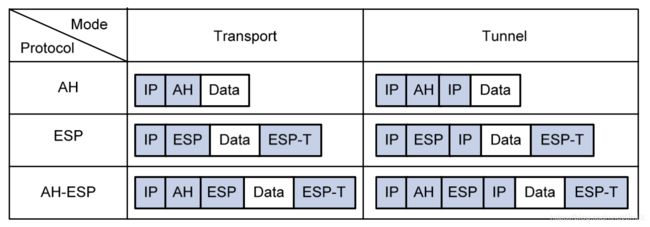
封装协议
在实际应用中,AH 和 ESP 封装协议可以单独使用,也可以组合使用。
- AH 协议可以确保数据的完整性和数据源身份认证;
- ESP 协议可以提供更高级别的数据加密特性;
- AH-ESP 协议组合可以提供最完备的安全保障,但协议开销也最高。
具体选择使用哪种协议,以及如何配置和组合它们,取决于特定的安全需求和网络环境。
Authentication Header 协议
AH(Authentication Header,安全认证协议)通常与 Transport 模式一起使用,用于 E2E 的身份认证安全通信,但不能加密数据的内容,具有以下安全特性:
- 数据认证范围:AH 对几乎整个 Original IP Packet 进行身份认证,包括 Header 和 Payload(Header 中的可变域除外)。
- 数据加密范围:AH 不对数据进行加密。
- 数据完整性校验:AH 使用 HASH 算法(e.g. MD5、SHA)生成 MAC(消息认证码)的方式来校验数据的完整性。
AH 的封装格式如下图所示:
- Next Header(下一个头):标识被封装数据的协议类型。
- Payload Length(载荷长度):标识 Original IP Payload 的长度。
- Reserved(保留位):置 0。
- Security Parameter Index(SPI,安全参数索引):标识安全参数。
- Sequence Number(序列号):32bits 长度的单调递增的数值,此数值溢出后,需要重新建立 SA,并使用 DH 加密算法交换密钥,以此来防止重放攻击。
- Authentication Data(身份认证数据):包含了对当前 IP Packet 进行身份认证所必须的数据。
Encapsulating Security Payload 协议
ESP(Encapsulating Security Payload,安全封装协议)可以在 Transport 模式和 Tunnel 模式下使用,可以提供 E2E 或网络之间的身份认证和加密安全通信。
安全特性:
- 数据认证范围:ESP 只会对除了 Original IP Payload 进行身份认证,并没有专门对 Original IP Header 的内容进行任何保护。
- 数据加密范围:ESP 使用加密算法(e.g. DES、3DES、AES等)对 IP Payload 进行加密。
- 数据完整性校验:ESP 使用 HASH 算法(e.g. MD5、SHA)生成 MAC(消息认证码)的方式来校验数据的完整性。
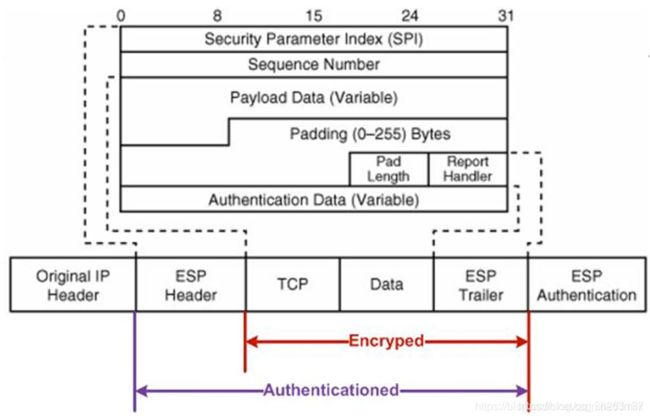
ESP 的封装格式如下图所示:出了会添加 ESP Header 之外还会在 IP Packet 尾部添加一个 ESP Tail 和 ESP Auth data。
- Security Parameter Index(SPI,安全参数索引):标识安全参数。
- Sequence Number(序列号):32bits 长度的单调递增的数值,此数值溢出后,需要重新建立 SA,并使用 DH 加密算法交换密钥,以此来防止重放攻击。
- Payload Data(载荷数据):Original IP Payload。
- Padding(填充位):某些块加密算法需要填充至特定的长度。
- Pad Length(填充长度):标识具体的填充长度。
- Authentication Data(身份认证数据):包含了对当前 IP Packet 进行身份认证所必须的数据。
封装模式
无论是 Tunnel 模式还是 Transport 模式,添加的除了 Original IP Packet 之外的封装头部和尾部的总长度不能超过 58Bytes,具体长度视乎于具体的封装模型而定。
Transport(传输模式)
Transport(传输模式)具有以下特性:
- Transport 模式提供主机级别的安全性,因为只有 IP Payload 被加密了,而 IP Header 在网络中是可见的。所以通常用于端到端通信场景,例如:两个主机之间的通信。
- 在 Transport 模式中,Original IP Packet 的 srcIP 和 dstIP 不会更改。
Tunnel(隧道模式)
Tunnel(隧道模式)具有以下特性:
- 在 Tunnel 模式下,IPSec 会创建一个 New IP Packet,并将 Original IP Packet 作为 New IP Packet 的 Payload 进行封装。
- Tunnel 模式提供了网络级别的安全性,因为整个 Original IP Packet 都被加密和认证。所以可以用于网络之间的通信,例如:在两个远程网络之间建立安全通信。
安全偶联协商
Security Association 协议
一个 IPSec 通信连接需要首先在两端建立 Security Association(安全偶联),通过 SA 协议的交互流程来协商 AH 或 ESP 封装协议所需要使用到的加密协议、对称秘钥、对端 IP 地址等信息。其中,关键的对称秘钥还需要额外的通过 IKE 协议来进行互换。
一个 IPSec 连接对应一个 SA,由 3-tuple 来唯一标识,包括:
- SPI(Security Parameter Index,安全参数索引)
- 目的 IP 地址
- 安全协议号(AH 或 ESP)
其中,SPI(32bits)用于唯一标识一个 SA,它会被添加到 AH 或 ESP Header 中。
Internet Key Exchange 协议
IKE(Internet Key Exchange,安全密钥交换协议)是建立在 ISAKMP(Internet Security Association and Key Management Protocol,互联网安全联盟和密钥管理协议)之上的、专用于保证对称密钥安全交换的自动协商协议,并提供了 SA 自动建立、CA 身份认证等功能。
使用 IKE 来建立和维护 SA,可以有效简化了 IPSec 的使用和管理,并提供更好的安全性。包括:
- 使用 IKE 自动随机生成 SPI 的取值,代替手工生成。
- 使用 IKE 自动生成对称密钥,代替手工生成。
- 大规模的 IPSec VPN 端到网关场景中,往往需要使用 CA 认证机制,使用 IKE 的 CA 身份认证代替手动生成。
- 使用 IKE 提供周期性的动态建立 SA,并且每次重建 SA 都会使用 DH(Diffie-Hellman)加密算法,使得每个 SA 所使用的 Pre-Master Secret 对称密钥都是不相同的,支持向前保密(Forward Secret)特性。
- AH 和 ESP Header 中基于 Sequence Number 字段的防重放保护同样需要 IKE 动态建立 SA 的机制。
IKE 支持的 SA 生命周期具有 2 种定义方式:
- 基于时间:定义一个 SA 从建立到失效的时间;
- 基于流量:定义一个 SA 允许处理的最大流量。
在 SA 终结条件到达后、SA 失效前,IKE 会自动协商建立新的 SA:
- 在新的 SA 开始协商而没有协商好之前,继续使用旧的 SA 保护通信;
- 在新的 SA 协商好之后,则立即采用新的 SA 保护通信。
IKE 的对称密钥交换过程
值得注意的是,IKE 不是简单的在网络上传输对称密钥(会遭受中间人攻击),而是通过一系列数据的交换,最终计算出双方共享的对称密钥,类似 TLS 协议。
IKE 使用了 2 个阶段为 IPSec 通信连接进行密钥协商并建立 SA:
- 第一阶段:通信各方彼此间建立了一个已通过身份认证和安全保护的通道,即:建立一个 ISAKMP SA。
- 第二阶段:用在第一阶段建立的 ISAKMP SA 安全隧道为 IPSec 协商安全服务,即:为 IPSec 协商和建立一个用于安全传输 IP Packets 的 IPSec SA。
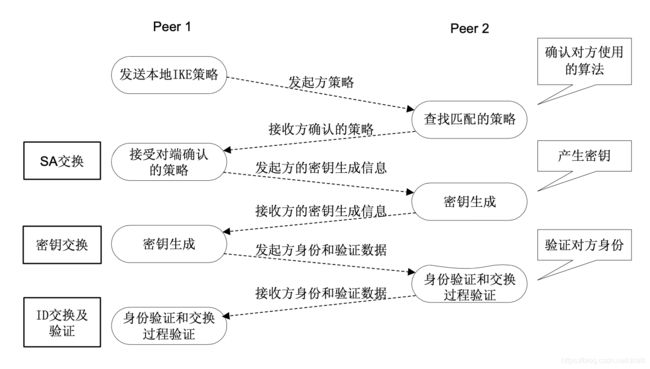
其中,第一阶段具有主模式(Main Mode)和野蛮模式(Aggressive Mode)这 2 种 IKE 交换方法。
- 主模式的 IKE 协商过程中包含了 3 对消息:
- 第一对叫 SA 交换,是协商确认有关安全策略的过程;
- 第二对消息叫密钥交换,交换 Diffie-Hellman 公共值和辅助数据(如:随机数),密钥材料在这个阶段产生;
- 最后一对消息是 ID 信息和认证数据交换,进行身份认证和对整个第一阶段交换内容的认证。
- 野蛮模式交换的主要区别在于:野蛮模式不提供身份保护,只交换 3 条消息。
所以,在对身份保护要求不高的场合,使用交换报文较少的野蛮模式可以提高协商的速度。而在对身份保护要求较高的场合,则应该使用主模式。
IPSec NAT-Tranversal
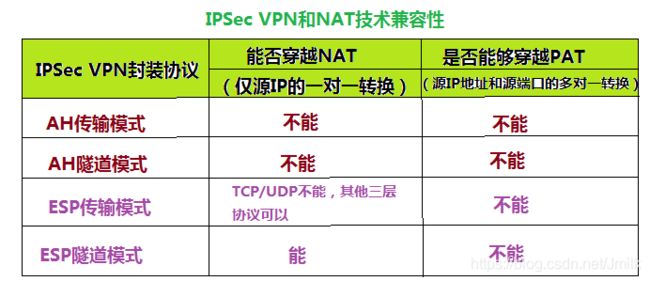
由于 IPSec 的安全加密特性,所以从技术实现上会与 NAT 存在冲突。如下图所示总结了这种冲突的情况:
- Transport-AH、Tunnel-AH 和 Transport-ESP 都不支持 NAPT。
- Tunnel-ESP 只支持一对一的 NAT,但不支持 PAT。
具体而言,Transport 模式的冲突原因如下:
- Transport-AH 的 Authenticate(数据身份认证)范围为整个 IP Packet,而 NAT 会修改 IP Header 的 Address,所以就会导致接收方 Authenticate 失败。同样,PAT 会修改 TCP Header 的 Port,也会导致 Authenticate 失败。
- Transport-ESP 的 Authenticate 范围为 ESP Header 和 ESP Tail 之间。因为 ESP 不校验 IP Header 所以 NAT 行为并不会导致接收方的 Authenticate 失败,但由于 NAT 修改了 IP Header 中的 Address,理论上后面的 TCP checksum 也会随之修改,而 TCP checksum 已经属于 ESP 校验范围之内了,NAT 设备无法进行修改,所以接收端在 TCP 层接收时会导致 checksum 校验失败。
Tunnel 模式的冲突原因如下:
- Tunnel-AH 的 Authenticate 范围会包含外层的 New IP Header,因此 NAT 同样会造成接收方 Authenticate 失败。
- Tunnel-ESP 经过 NAT 后,内层的 Original IP Header 并不会被改变,所以 TCP checksum 也不会改变,接收方也就不会再出现 checksum 失败了。但也存在着缺点:它只能支持一对一的 NAT,即:NAT 后面只有一台内网主机。如果考虑 PAT 来补充的话,又回因为 TCP Header 已经被加密而无法实现。
NAT-T 的封装模式
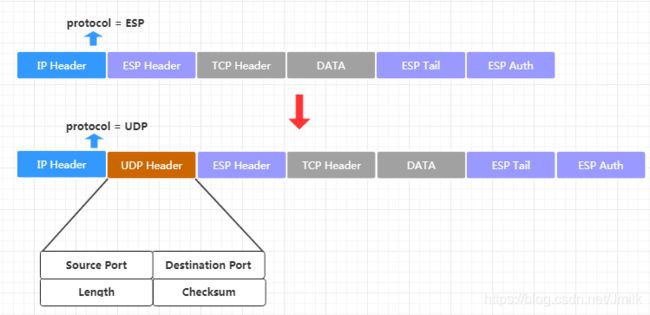
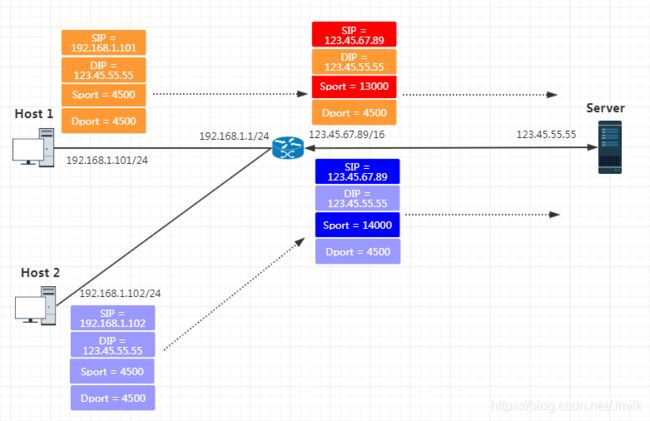
IPSec NAT-Tranversal 用于解决上述提到的 IPSec 和 NAT 冲突问题。而解决方案就是使用 ESP-UDP-Encapsulate 封装模式,即:在 ESP Header 前加上一个 New UDP Header,srcPort 和 dstPort 均是 4500,使得 NAT 设备按照处理一个普通的 UDP 数据报的方式对它进行处理。这个方法同时适用于 Transport-ESP 和 Tunnel-ESP 模型,以及同时支持 PAT 和 NAT。
应用了 IPSec NAT-T 后,NAT 设备后有多台内网主机,它们都可以通过 NAT 之后并与 Server 建立 IPSec 连接了。
NAT-T 的协商过程
IPSec 连接两端需要在 IKE 完成协商后才能使用 NAT-T。
阶段一:
- 探测出双方都支持 NAT-T。
- 探测出双方报文传输路径上存在 NAT 设备。
- 前 4 个 Msg 都是使用 Sport=Dport=500 进行通信。但当探测到 NAT 设备后,作为 Initiator 再发出第 5 个 Msg 就会将端口切换到 Sport=Dport=4500,Responder 收到该消息后,如果解密成功,后续也会使用新的 4500 端口。注意,RFC3948 规定了 New UDP Header 中的端口要使用和 IKE 协商时相同的端口号,这个端口号在 RFC3947 中规定为 4500。
阶段二:
- 双方协商 NAT-T 的封装模式,UDP-Encapsulated-Tunnel 还是 UDP-Encapsulated-Transport。
- 其中,UDP-Encapsulated-Transport 模式还会向对方发送自己的原始 IP 地址,让对方可以据此修正后续 TCP 报文的 checksum。要知道,经过 NAT 设备之后,报文的 IP 地址发生了变化,就会导致接收端校验失败。IPsec 采用的方法是在 IKE 协商时,就将自己原始 IP 地址信息发给对端,这样 Server 在解密出 TCP 报文后,可以根据这个信息修正 checksum。
IPSec 的 MTU 分片和加密问题
由于 AH 和 ESP 封装协议会增加额外的首部和尾部,这可能会导致添加封装后 IPSec 报文超出了 L2 MTU,从而导致分片。IPSec 分片可能会引发一些问题,包括:增加网络延迟、增加网络负载、增加数据包丢失的风险等。例如:据统计 IPSec 分片可能会导致硬件加解密加速卡 50%~90% 的性能下降。这是因为 IPSec 分片首先需要进行软件重组,然后再传送给硬件卡进行解密,使得软件重组成为了限制硬件加速的瓶颈。
因此 IPSec 设备上线前往往需要仔细评估网络环境、设备能力和需求,选择合适的 IP MTU 配置策略,并进行充分的测试和验证,以确保 L2 MTU >= IP MTU + IPSec。
在大多数场景中,可以采用常规的 IP MTU 配置措施来避免 IPSec 分片,例如:
- 修改 IPSec 设备的 IP MTU 设置,确保内层的 Original IPv4 Packet 分片再添加上外层的 IPSec 封装后仍然不会超过 L2 MTU,继而导致 IPSec 封装报文的分片。比如说,在视频流场景中,由于无法避免的大包问题,Original IP Packet 分片是固然存在的,此时需要计算并设定更小的 IP MTU。
- 在措施 1 的基础上,通过在网络设备中启用 PMTUD(Path MTU Discovery)技术,在 L2 传输链路上进行 MTU 探测和协商出最佳的 L2 MTU 值,并在 IPSec 设备中自动调整 IP MTU 设置。
对于措施 2 而言,不同的网络设备型号会具有相应的功能特性,以 Cisco Router 作为 IPSec Gateway 时对 Tunnel-ESP(52B 开销)的处理特性为例,支持使用 ipsec 配置命令来修改对 IPSec 封装包的 PMTUD 处理,包括:clear、copy、set IP Header Flags DF 位。例如:
-
假设整个路径上的 L2 MTU 为 1500Bytes,未设置 IP Header Flags DF(Don’t Fragment)位,存在 IPSec 分片。
- Router 收到发往 H1 的 1500B 的 Original IP Packet(IPv4 Header 20B + TCP Payload 1480B)。
- Original IP Packet 经过 Tunnel-ESP 封装,增加了 52B 的开销(New IP Header + ESP Header + ESP Tail)。
- 此时的 IPSec 封装包为 1552B,超出了 L2 MTU 1500B,因此会进行分片。
- PSec 封装包被分为 2 片,分别为 1500B 和 72B(添加了额外的 New IPv4 Header 20B)。
- IPSec Tunnel 对端的 Router 接收到 2 个分片后,剥离附加的 New IPv4 Header,并重组为 IPSec 封装包,然后解密和解封装。
- 最终,Router 将 1500B 的 Original IP Packet 交给 H2。
-
假设整个路径上的 L2 MTU 为 1500Bytes,设置了 IP Header Flags DF(Don’t Fragment)位,避免 IPSec 分片。如下图所示。
- Router 收到 1500B 的 Original IP Packet 就将其丢弃,因为添加 IPSec 封装后会大于 PMTU(1500B)。
- Outer 向 H1 发送一条 ICMP 消息,并通知该 H1 下一跳 MTU 为 1442(1500 - 58 = 1442)。H1 会在其路由表中以 H2 主机路由的形式记录该信息。
- H1 将 H2 的 PMTU 降低到 1442B,因此 H1 在将数据重新发送到 H2 时发送更小的 Original IP Packet,然后添加 52B 的开销,由此产生 1496B 的 IPSec 封装包。
- 由于 IPSec 封装包的 New IP Header 中设置了 DF 位,因此,采用 1400B L2 MTU 的中间路由器将丢弃此数据包。
- 丢弃数据包的中间路由器向 IPSec 的发送端(第一个 Router)发送一条 ICMP 消息,告知其下一跳 L2 MTU 为 1400B,这个值记录在 IPSec Gateway SA 的 PMTU 中。
- H1 下次重新传输 1442B 的 Original IP Packet 时,Router 依旧会丢弃该数据包,因为最新的 PMTU 实际上更小。
- 所以 Router 继续向 H1 发送一条 ICMP 消息,通知它下一跳 MTU 现在为 1342(1400 - 58 = 1342),然后 H1 再次记录此信息。
- 当 H1 再次重新传输数据时,它使用 1342B MTU。此时,IPSec 封装包就不再需要分片了。
IPSec Virtual Private Network
Virtual Private Network 是 IPSec 的主要应用场景,具体的还可以分为以下细分场景:
-
Site-to-Site(站点到站点):S2S 通常是 2 个 IPSec VPN Gateway 之间的互联。应用在企业的多个分支机构互联场景中,这些站点之间的多台主机的数据通过 Gateway 建立的 IPSec 连接进行安全传输。
-
End-to-End(端到端):E2E 通常是 2 个 IPSec VPN Client 之间的互联。应用在主机互联场景中,这些主机之间的数据通过 IPSec 连接进行安全传输。
-
End-to-Site(端到网关):E2S 通常是 IPSec VPN Client 和 Gateway 之间的互联。应用在两个不同网络中的主机之间的数据通过 Gateway 建立的 IPSec 连接进行安全传输。通常会采用 L2TP over IPSec 方案进行部署,即:在 L2TP VPN 基础上采用 IPSec 来提供更好的安全保护。
![]()
IPSec Virtual Tunnel Interface
IPSec VTI(Virtual Tunnel Interface,虚拟隧道接口)是网络操作系统或服务器操作系统中的一种虚拟网络接口设备。
IPSec VTI 提供了一种将 IPSec VPN 配置为某个特定的网络接口上的能力,以便结合操作系统的 Routing 功能,实现将特定 Subnet 得网络流量通过特定的 VTI 发送到对应的 IPSec VPN 中。
- Tunnel 模式:IPSec VTI 将整个 Original IP Packet 封装在另一个 New IP Packet 中,此时 New IP Packet 的 srcIP 和 dstIP 会被更改为 Tunnel 两端的 IP 地址,然后进行加密。
- Transport 模式:IPSec VTI 仅对 Original IP Payload 进行加密和封装,而不会修改 IP Header,所以 Original IP Packet 的 srcIP 和 dstIP 不会被更改,IPSec VTI 仅用于加密。
使用 IPSec VTI 来建立 IPSec 安全连接具有以下优点:
-
简化配置:通过 Routes 来确定对哪些 IP Packets 需要进行 IPSec 保护。与通过 ACL 指定 IP Flow 范围的方式相比,这种方式简化了用户在部署 IPSec 安全策略时配置上的复杂性,使得 IPSec 的配置不会受到网络规划的影响,增强了网络规划的可扩展性,降低了网络维护成本。
-
减少开销:在保护远程接入用户流量的组网应用中,在 IPSec VTI 处进行报文封装,与 GRE over IPSec 或者 L2TP over IPSec 隧道封装方式相比,无需额外为入隧道流量加封装 GRE Header 或者 L2TP Header,减少了报文封装的层次,节省了带宽。
-
业务应用更灵活:IPsec VTI 在实施过程中明确地区分出 “加密前” 和 “加密后” 两个阶段,用户可以根据不同的组网需求灵活选择其它业务(例如:NAT、ACL、QoS)实施的阶段。例如:
- 如果用户希望对 IPSec 封装加密前的 IP Packets 应用 NAT、ACL、QoS,则可以在 IPSec VTI(Logical Interface)上应用策略;
- 如果希望对 IPSec 封装后的 IP Packets 应用 NAT、ACL、QoS,则可以在 Physical Interface 上应用策略。
IPSec VTI 的工作原理
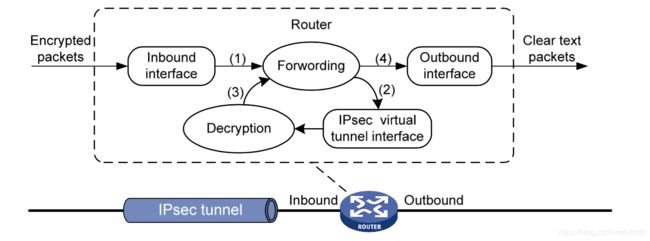
下面以更复杂的 Tunnel 模式为例。IPSec VTI 对 Original IP Packets 的封装/解封装发生在 VTI 上,并将报文的 IPSec 处理过程区分为两个阶段:“加密前” 和 “加密后”。用户流量到达实施 IPSec 配置的设备后,需要 IPSec 处理的报文会被转发到 IPSec VTI 上进行加封装/解封装。
发包封装流程:
- Router 将从入接口接收到的 IP 明文送到转发模块进行处理;
- 转发模块依据路由查询结果,将 IP 明文发送到 IPSec VTI 进行加封装,Original IP Packet 被封装在一个 New IP Packet 中,New IP Packet 的 srcIP 和 dstIP 分别为 Tunnel 的 srcIP 和 dstIP。
- IPSec VTI 完成对 IP 明文的加封装处理后,将 IP 密文送到转发模块进行处理;
- 转发模块进行第二次路由查询后,将 IP 密文通过隧道接口的实际物理接口转发出去。
收包解封装流程:
- Router 将从入接口接收到的 IP 密文送到转发模块进行处理;
- 转发模块识别到此 IP 密文的目的地为本设备的隧道接口地址且 IP 协议号为 AH 或 ESP 时,会将 IP 密文送到相应的 IPSec VTI 进行解封装:将 IP 密文的 New IP Header 去掉,对 Original IP Packet 进行解密处理。
- IPSec VTI 完成对 IP 密文的解封装处理之后,将 IP 明文重新送回转发模块处理;
- 转发模块进行第二次路由查询后,将明文的 Original IP Packet 从隧道的实际物理接口转发出去。
Linux iptables 与 VTI 的结合
最初往 Linux Kernel 增加 VTI 功能的作者提到:
Virtual tunnel interface is a way to represent policy based IPsec tunnels as virtual interfaces in linux. This is similar to Cisco’s VTI (virtual tunnel interface) and Juniper’s representaion of secure tunnel (st.xx). The advantage of representing an IPsec tunnel as an interface is that it is possible to plug Ipsec tunnels into the routing protocol infrastructure of a router. Therefore it becomes possible to influence the packet path by toggling the link state of the tunnel or based on routing metrics.
这表明了 VTI 在 Linux Kernel 中也是一种虚拟网络设备,主要作用是将经过这个设备的 IP 流量打上标签,IPSec 的策略再根据这个标签和相关信息来判断流量该怎么转发。
在 Linux 中,经常使用 iptables 来为各类网络应用打标签,例如:通过 iptables 打标签给 tc 来控制流量,通过 iptables 打标签来给 iproute 来控制路由等做法。所以,通常也可以通过 iptables 给 IP 网络流量打上标签,继而实现让其数据包被 IPSec 转发的效果的。
GRE over IPSec VPN
由于 IPSec 只能加密并传输单播流量,而无法加密和传输组播数据,例如:语音、视频、动态路由协议,所以需要通过 GRE over IPSec 来弥补了这一缺陷。
首先通过 GRE(Generic Routing Encapsulation,通用路由封装)对报文进行封装,然后再由 IPSec 对封装后的报文进行加密和传输,从而保证了组播业务的安全。协议栈结构如下:
![]()
L2TP over IPSec VPN
由于 IPSec 只能加密并传输 IP 三层流量,而无法加密和传输 L2 二层流程,所以需要通过 L2TP over IPSec 来弥补这一缺陷。其封装格式如下图所示,在安全的 IPSec Tunnel 之间传输 PPP 数据帧。
Strongswan 的应用实践
Strongswan 是一个 IPSec 协议的开源实现,意为:StrongS/WAN(强安全的广域网),常用于 Linux 中。
Strongswan 具有以下特性:
- 使用了 Linux Kernel 的 IPSec 实现,包括:AH、ESP 封装协议,VTI 等。
- 支持 IKEv2 版本。
- 在 IKE 阶段,Strongswan 使用了 OpenSSL 和其他安全传输层库。
- 同时支持 x.509 证书身份认证,和基于 Pre-Shared-Key(预共享密钥)的身份认证。
- 能被使用在 End-to-Site(端到网关)和 Site-to-Site(网关到网关)场景中。如下所示:
# Roadwarrior Case
10.1.0.0/16 -- | 192.168.0.1 | === | x.x.x.x |
moon-net moon carol
# Site-to-Site Case
10.1.0.0/16 -- | 192.168.0.1 | === | 192.168.0.2 | -- 10.2.0.0/16
moon-net moon sun sun-net
在 Strongswan 的官网中还可以找到大量的 TestScenarios,下面选择其中的 net2net-psk 来进行实践。
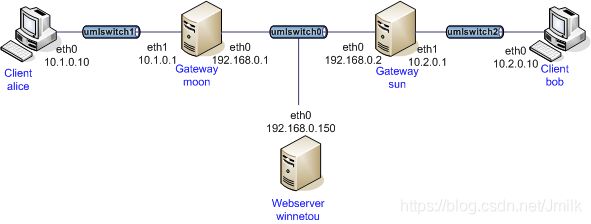
net2net-psk 网络拓扑
- Client:Alice、Bob
- Gateway:moon、sun
可见,这是一个 Site-to-Site Case 的场景。Strongswan 被安装在两个 GW 上,IPSec 采用了 Pre-Shared-Key(预共享密钥)的认证方式。
base configuration
- 安装软件
# 使用 EPEL 源安装 strongSwan,因为 EPEL 包含 strongSwan 最新版本,EPEL 更新比较快。
yum -y install epel-release
yum install strongswan -y
systemctl list-unit-files | grep swan
- 开启路由转发
$ vi /etc/sysctl.conf
# 开启路由转发。
net.ipv4.ip_forward = 1
# 关闭重定向,防止恶意用户可以使用 IP 重定向来修改远程主机中的路由表。
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
$ sysctl -p
- 修改 hosts:
$ vi /etc/hosts
192.168.0.75 moon.strongswan.org
192.168.0.137 sun.strongswan.org
- 关闭 SELinux:
sed -i '/SELINUX/s/enforcing/disabled/' /etc/selinux/config
- 启动 Strongswan:
$ systemctl start strongswan && systemctl enable strongswan && systemctl status strongswan
# charon 是 IKEv2 的 Daemon,监听在 UDP 500 和 4500 两个端口,其中 500 用作 IKE 密钥交换协商信令面,4500 用于 NAT-T。
$ netstat -lpntu | grep charon
moon Site
- ipsec.conf:是 Strongswan 的主配置文件。(官网文档:https://wiki.strongswan.org/projects/strongswan/wiki/ConnSection)
# ipsec.conf - strongSwan IPsec configuration file
# 全局配置,只能存在一个 Section。
config setup
# 默认连接参数。
conn %default
ikelifetime=60m # 指定 IPSec SA 生命周期协商时间间隔。
keylife=20m # 指定 ISAKMP SA 生命周期协商时间间隔。
rekeymargin=3m # 指定密钥更新时间间隔。
keyingtries=1 # 指定 ISAKMP SA 协商重试次数。
authby=secret # 指定认证方式。
keyexchange=ikev2 # 指定 IKE 版本,枚举:ikev1,ikev2。
mobike=no
# 自定义连接实例及参数。
conn net-net
leftfirewall=yes # 指定自动插入基于 iptables 的防火墙规则。作为 ipsec_updown 脚本的参数被开发出来,表明你的 Local Subnet 是不是用 iptables 转发/伪装出来的。如果是的话,就调用 left/rightupdown 定义的路径下的脚本,脚本的作用是对通过 IPSec 连接的数据包进行 iptables 豁免。
leftid=@moon.strongswan.org # 指定 Local 标识。
# - 可以是证书的判别名(DN),比如 "C=CN, O=strongSwan, CN=strongSwan CA"。
# - 也可以是 IP 地址。
# - 也可以是 EAP 的用户名。
# - 还可以是魔术字 %any,表示什么都行。
leftauth=psk # 指定 Local 采用共享密钥机制。枚举:pubkey 表示用证书,psk 表示用密码,eap 表示用扩展验证协议。
left=192.168.0.10 # 指定 Local GW 的 IP 地址。
leftsubnet=10.1.0.0/24 # 指定 Local Subnet IP 地址段。
#leftcert=server.pem # 指定 x.509 证书名字。
rightid=@sun.strongswan.org # 指定 Remote 标识。
rightauth=psk # 指定 Rmote 采用共享密钥机制。
right=192.168.0.20 # 指定 Remote GW 的 IP 地址。
rightsubnet=10.2.0.0/24 # 指定 Remote Subnet IP 地址段。
#rightcert=server.pem # 指定 x.509 证书名字。
auto=add # 指定连接方式,枚举:
# - add 手动触发启动。添加连接类型但不启动,执行指令 strongswan up net-net 启动。
# - route 连接触发启动。添加路由表,有数据通过就启动。
# - start 启动进程时触发。
# - ignore 忽略该策略。
#type=transport # 指定隧道模式,枚举:transport,tunnel。
#ike=3des-md5-modp1024 # 指定 IKE 第一阶段的加密算法、认证算法、DH Group,两边要保持一致。
#esp=3des-md5-modp1024 # 指定 IPSec 的加密算法、认证算法、PFS(完美向前保密)。
NOTE:PFS 完美向前保密,用于 rekey 时。意思是:如果现在的密钥互换过程如果被攻破了,会不会对已经互换过的密钥产生影响。以前一般设置成 no 来适用于 IOS 这种客户端会以积极模式发出非加密的 rekey 请求的情况。现在这个选项完全没作用了。第一阶段永远是完美向前保密的,第二阶段(ESP)如果指定了 DH Group 那么也是完美向前保密的,但是默认加密方法就已经指定了 DH Group。所以该选项永远为 yes。
- ipsec.secrets:使用 PSK 方式。
# ipsec.secrets - strongSwan IPsec secrets file
@moon.strongswan.org @sun.strongswan.org : PSK 0sv+NkxY9LLZvwj4qCC2o/gGrWDF2d21jL
@moon.strongswan.org %any : PSK 0x45a30759df97dc26a15b88ff
@sun.strongswan.org : PSK "This is a strong password"
: PSK 'My "home" is my "castle"!'
192.168.0.1 : PSK "Andi's home"
NOTE:Strongswan 支持 x.509、PSK、xAUTH、IKEv2 User 等多种安全认证方式,如:
# x.509 证书认证。
: RSA server.pem
# PSK 认证。
: PSK "myPSKkey"
%any %any : PSK "PSK password"
# xAUTH 认证。
: XAUTH "myXAUTHPass"
# IKEv2 User 认证,可以添加多行,得到多个用户。
myUsername %any : EAP "myPassword"
- strongswan.conf:
# strongswan.conf - strongSwan configuration file
#
# Refer to the strongswan.conf(5) manpage for details
#
# Configuration changes should be made in the included files
charon {
load_modular = yes
plugins {
include strongswan.d/charon/*.conf
}
}
include strongswan.d/*.conf
- charon.conf:
# Options for the charon IKE daemon.
...
# Plugins to load in the IKE daemon charon.
load = random nonce aes sha1 sha2 curve25519 hmac stroke kernel-netlink socket-default updown
...
# Enable multiple authentication exchanges (RFC 4739).
multiple_authentication = no
- charon-logging.conf:
charon {
filelog {
charon-debug-log {
path = /var/log/strangswan.log
time_format = %b %e %T
default = 2
mgr = 0
net = 1
enc = 1
asn = 1
job = 1
ike_name = yes
append = no
flush_line = yes
}
}
}
sun Site
- ipsec.conf:
# ipsec.conf - strongSwan IPsec configuration file
config setup
conn %default
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=1
authby=secret
keyexchange=ikev2
mobike=no
conn net-net
leftfirewall=yes
leftid=@sun.strongswan.org
leftauth=psk
left=192.168.0.20
leftsubnet=10.2.0.0/24
rightid=@moon.strongswan.org
rightauth=psk
right=192.168.0.10
rightsubnet=10.1.0.0/24
auto=add
- ipsec.secrets:
# ipsec.secrets - strongSwan IPsec secrets file
@moon.strongswan.org @sun.strongswan.org : PSK 0sv+NkxY9LLZvwj4qCC2o/gGrWDF2d21jL
- strongswan.conf:同上。
- charon.conf:同上。
- charon-logging.conf:同上。
测试
clientA、clientB 可以 ping 通,表示配置 strongswan IPSec 成功。
sun $ tcpdump -l --immediate-mode -i eth0 not port ssh and not port domain >/tmp/tcpdump.log 2>/tmp/tcpdump.err.log &
moon $ strongswan start
Starting strongSwan 5.7.2 IPsec [starter]...
sun $ strongswan start
Starting strongSwan 5.7.2 IPsec [starter]...
# moon Site 主动发起 IKEv2 协商并建立 IPSec 隧道。
moon or sun $ strongswan up net-net
moon $ strongswan status 2> /dev/null | grep 'net-net.*ESTABLISHED.*moon.strongswan.org.*sun.strongswan.org'
net-net[2]: ESTABLISHED 7 minutes ago, 192.168.0.10[moon.strongswan.org]...192.168.0.20[sun.strongswan.org]
sun $ strongswan status 2> /dev/null | grep 'net-net.*ESTABLISHED.*sun.strongswan.org.*moon.strongswan.org'
net-net[1]: ESTABLISHED 7 minutes ago, 192.168.0.20[sun.strongswan.org]...192.168.0.10[moon.strongswan.org]
moon $ strongswan status 2> /dev/null | grep 'net-net.*INSTALLED, TUNNEL'
net-net{2}: INSTALLED, TUNNEL, reqid 2, ESP SPIs: caa065c7_i c5cfece6_o
sun $ strongswan status 2> /dev/null | grep 'net-net.*INSTALLED, TUNNEL'
net-net{1}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: c5cfece6_i caa065c7_o
clientA $ ping -c 1 10.2.0.10 | grep '64 bytes from 10.2.0.10: icmp_.eq=1'
64 bytes from 10.2.0.10: icmp_seq=1 ttl=62 time=0.591 ms
moon $ strongswan stop
Stopping strongSwan IPsec...
sun $ strongswan stop
Stopping strongSwan IPsec...
运维
- 重启 Stroageswan
moon & sun $ systemctl restart strongswan
- 查看 SA 状态
moon & sun $ strongswan status
Security Associations (0 up, 0 connecting):
none
- 查看启动日志
moon $ tail -f /var/log/strangswan.log
Apr 5 23:36:43 00[DMN] Starting IKE charon daemon (strongSwan 5.7.2, Linux 3.10.0-1062.1.1.el7.x86_64, x86_64)
Apr 5 23:36:43 00[LIB] plugin 'acert': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'aesni': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'attr': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'ccm': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'chapoly': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'cmac': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'constraints': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'counters': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'ctr': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'curl': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'des': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'dhcp': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'dnskey': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'duplicheck': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-aka': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-aka-3gpp': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-aka-3gpp2': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-dynamic': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-gtc': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-identity': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-md5': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-mschapv2': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-peap': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-radius': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-sim': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-sim-file': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-tls': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'eap-ttls': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'ext-auth': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'farp': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'fips-prf': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'gcm': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'gcrypt': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'gmp': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'ha': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'ipseckey': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'led': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'md4': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'md5': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'mgf1': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'newhope': loaded successfully
Apr 5 23:36:43 00[LIB] openssl FIPS mode(2) - enabled
Apr 5 23:36:43 00[LIB] plugin 'openssl': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'pem': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'pgp': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'pkcs1': loaded successfully
Apr 5 23:36:43 00[CFG] PKCS11 module '' lacks library path
Apr 5 23:36:43 00[LIB] plugin 'pkcs11': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'pkcs12': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'pkcs7': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'pkcs8': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'pubkey': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'random': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'rc2': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'resolve': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'revocation': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'sql': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'sshkey': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'tpm': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'unity': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'vici': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'x509': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'xauth-eap': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'xauth-generic': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'xauth-noauth': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'xauth-pam': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'xcbc': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'nonce': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'aes': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'sha1': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'sha2': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'curve25519': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'hmac': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'stroke': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'kernel-netlink': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'socket-default': loaded successfully
Apr 5 23:36:43 00[LIB] plugin 'updown': loaded successfully
Apr 5 23:36:43 00[KNL] known interfaces and IP addresses:
Apr 5 23:36:43 00[KNL] lo
Apr 5 23:36:43 00[KNL] 127.0.0.1
Apr 5 23:36:43 00[KNL] ::1
Apr 5 23:36:43 00[KNL] eth0
Apr 5 23:36:43 00[KNL] 192.168.0.10
Apr 5 23:36:43 00[KNL] fe80::f816:3eff:fec4:8791
Apr 5 23:36:43 00[KNL] eth1
Apr 5 23:36:43 00[KNL] 10.1.0.1
Apr 5 23:36:43 00[KNL] fe80::f816:3eff:fe0d:5ec5
Apr 5 23:36:43 00[LIB] feature PUBKEY:DSA in plugin 'pem' has unmet dependency: PUBKEY:DSA
Apr 5 23:36:43 00[LIB] feature PUBKEY:BLISS in plugin 'pem' has unmet dependency: PUBKEY:BLISS
Apr 5 23:36:43 00[CFG] loaded 0 RADIUS server configurations
Apr 5 23:36:43 00[CFG] opening triplet file /etc/strongswan/ipsec.d/triplets.dat failed: No such file or directory
Apr 5 23:36:43 00[LIB] feature CUSTOM:eap-sim-file-triplets in plugin 'eap-sim-file' failed to load
Apr 5 23:36:43 00[LIB] feature CUSTOM:sim-card in plugin 'eap-sim-file' has unmet dependency: CUSTOM:eap-sim-file-triplets
Apr 5 23:36:43 00[LIB] feature CUSTOM:sim-provider in plugin 'eap-sim-file' has unmet dependency: CUSTOM:eap-sim-file-triplets
Apr 5 23:36:43 00[CFG] no script for ext-auth script defined, disabled
Apr 5 23:36:43 00[LIB] feature CUSTOM:ext_auth in plugin 'ext-auth' failed to load
Apr 5 23:36:43 00[LIB] feature PRIVKEY_SIGN:RSA_EMSA_PKCS1_SHA3_224 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_224
Apr 5 23:36:43 00[LIB] feature PRIVKEY_SIGN:RSA_EMSA_PKCS1_SHA3_256 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_256
Apr 5 23:36:43 00[LIB] feature PRIVKEY_SIGN:RSA_EMSA_PKCS1_SHA3_384 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_384
Apr 5 23:36:43 00[LIB] feature PRIVKEY_SIGN:RSA_EMSA_PKCS1_SHA3_512 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_512
Apr 5 23:36:43 00[LIB] feature PUBKEY_VERIFY:RSA_EMSA_PKCS1_SHA3_224 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_224
Apr 5 23:36:43 00[LIB] feature PUBKEY_VERIFY:RSA_EMSA_PKCS1_SHA3_256 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_256
Apr 5 23:36:43 00[LIB] feature PUBKEY_VERIFY:RSA_EMSA_PKCS1_SHA3_384 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_384
Apr 5 23:36:43 00[LIB] feature PUBKEY_VERIFY:RSA_EMSA_PKCS1_SHA3_512 in plugin 'gmp' has unmet dependency: HASHER:HASH_SHA3_512
Apr 5 23:36:43 00[CFG] HA config misses local/remote address
Apr 5 23:36:43 00[LIB] feature CUSTOM:ha in plugin 'ha' failed to load
Apr 5 23:36:43 00[LIB] feature CUSTOM:ipseckey in plugin 'ipseckey' has unmet dependency: RESOLVER
Apr 5 23:36:43 00[LIB] feature DH:NEWHOPE_128 in plugin 'newhope' has unmet dependency: XOF:XOF_SHAKE128
Apr 5 23:36:43 00[LIB] feature PRIVKEY:DSA in plugin 'pem' has unmet dependency: PRIVKEY:DSA
Apr 5 23:36:43 00[LIB] feature PRIVKEY:BLISS in plugin 'pem' has unmet dependency: PRIVKEY:BLISS
Apr 5 23:36:43 00[LIB] feature CERT_DECODE:OCSP_REQUEST in plugin 'pem' has unmet dependency: CERT_DECODE:OCSP_REQUEST
Apr 5 23:36:43 00[LIB] feature CUSTOM:sql in plugin 'sql' has unmet dependency: DATABASE:any
Apr 5 23:36:43 00[CFG] loading ca certificates from '/etc/strongswan/ipsec.d/cacerts'
Apr 5 23:36:43 00[CFG] loading aa certificates from '/etc/strongswan/ipsec.d/aacerts'
Apr 5 23:36:43 00[CFG] loading ocsp signer certificates from '/etc/strongswan/ipsec.d/ocspcerts'
Apr 5 23:36:43 00[CFG] loading attribute certificates from '/etc/strongswan/ipsec.d/acerts'
Apr 5 23:36:43 00[CFG] loading crls from '/etc/strongswan/ipsec.d/crls'
Apr 5 23:36:43 00[CFG] loading secrets from '/etc/strongswan/ipsec.secrets'
Apr 5 23:36:43 00[CFG] loaded IKE secret for @moon.strongswan.org @sun.strongswan.org
Apr 5 23:36:43 00[CFG] loaded IKE secret for @moon.strongswan.org %any
Apr 5 23:36:43 00[CFG] loaded IKE secret for @sun.strongswan.org
Apr 5 23:36:43 00[CFG] loaded IKE secret for %any
Apr 5 23:36:43 00[CFG] loaded IKE secret for 192.168.0.1
Apr 5 23:36:43 00[LIB] unloading plugin 'eap-sim-file' without loaded features
Apr 5 23:36:43 00[LIB] unloading plugin 'ext-auth' without loaded features
Apr 5 23:36:43 00[LIB] unloading plugin 'ha' without loaded features
Apr 5 23:36:43 00[LIB] unloading plugin 'ipseckey' without loaded features
Apr 5 23:36:43 00[LIB] unloading plugin 'newhope' without loaded features
Apr 5 23:36:43 00[LIB] unloading plugin 'sql' without loaded features
Apr 5 23:36:43 00[LIB] loaded plugins: charon acert aesni attr ccm chapoly cmac constraints counters ctr curl des dhcp dnskey duplicheck eap-aka eap-aka-3gpp eap-aka-3gpp2 eap-dynamic eap-gtc eap-identity eap-md5 eap-mschapv2 eap-peap eap-radius eap-sim eap-tls eap-ttls farp fips-prf gcm gcrypt gmp led md4 md5 mgf1 openssl pem pgp pkcs1 pkcs11 pkcs12 pkcs7 pkcs8 pubkey random rc2 resolve revocation sshkey tpm unity vici x509 xauth-eap xauth-generic xauth-noauth xauth-pam xcbc nonce aes sha1 sha2 curve25519 hmac stroke kernel-netlink socket-default updown
Apr 5 23:36:43 00[LIB] unable to load 21 plugin features (18 due to unmet dependencies)
Apr 5 23:36:43 00[JOB] spawning 16 worker threads
Apr 5 23:36:43 01[LIB] created thread 01 [31198]
Apr 5 23:36:43 04[LIB] created thread 04 [31201]
Apr 5 23:36:43 03[LIB] created thread 03 [31200]
Apr 5 23:36:43 05[LIB] created thread 05 [31202]
Apr 5 23:36:43 06[LIB] created thread 06 [31205]
Apr 5 23:36:43 02[LIB] created thread 02 [31199]
Apr 5 23:36:43 09[LIB] created thread 09 [31208]
Apr 5 23:36:43 07[LIB] created thread 07 [31206]
Apr 5 23:36:43 12[LIB] created thread 12 [31207]
Apr 5 23:36:43 10[LIB] created thread 10 [31204]
Apr 5 23:36:43 08[LIB] created thread 08 [31203]
Apr 5 23:36:43 11[LIB] created thread 11 [31211]
Apr 5 23:36:43 13[LIB] created thread 13 [31209]
Apr 5 23:36:43 14[LIB] created thread 14 [31212]
Apr 5 23:36:43 15[LIB] created thread 15 [31210]
Apr 5 23:36:43 16[LIB] created thread 16 [31213]
Apr 5 23:36:43 05[CFG] received stroke: add connection 'net-net'
Apr 5 23:36:43 05[CFG] conn net-net
Apr 5 23:36:43 05[CFG] left=192.168.0.10
Apr 5 23:36:43 05[CFG] leftsubnet=10.1.0.0/24
Apr 5 23:36:43 05[CFG] leftauth=psk
Apr 5 23:36:43 05[CFG] leftid=@moon.strongswan.org
Apr 5 23:36:43 05[CFG] leftupdown=strongswan _updown iptables
Apr 5 23:36:43 05[CFG] right=192.168.0.20
Apr 5 23:36:43 05[CFG] rightsubnet=10.2.0.0/24
Apr 5 23:36:43 05[CFG] rightauth=psk
Apr 5 23:36:43 05[CFG] rightid=@sun.strongswan.org
Apr 5 23:36:43 05[CFG] dpddelay=30
Apr 5 23:36:43 05[CFG] dpdtimeout=150
Apr 5 23:36:43 05[CFG] sha256_96=no
Apr 5 23:36:43 05[CFG] mediation=no
Apr 5 23:36:43 05[CFG] keyexchange=ikev2
Apr 5 23:36:43 05[KNL] 192.168.0.20 is not a local address or the interface is down
Apr 5 23:36:43 05[CFG] added configuration 'net-net'
- 启动 net-net SA 连接
moon $ strongswan up net-net
initiating IKE_SA net-net[1] to 192.168.0.20
generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
sending packet: from 192.168.0.10[500] to 192.168.0.20[500] (1064 bytes)
received packet: from 192.168.0.20[500] to 192.168.0.10[500] (264 bytes)
parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) ]
selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_AES128_XCBC/ECP_256
authentication of 'moon.strongswan.org' (myself) with pre-shared key
establishing CHILD_SA net-net{1}
generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH SA TSi TSr N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
sending packet: from 192.168.0.10[500] to 192.168.0.20[500] (320 bytes)
received packet: from 192.168.0.20[500] to 192.168.0.10[500] (224 bytes)
parsed IKE_AUTH response 1 [ IDr AUTH SA TSi TSr N(AUTH_LFT) ]
authentication of 'sun.strongswan.org' with pre-shared key successful
IKE_SA net-net[1] established between 192.168.0.10[moon.strongswan.org]...192.168.0.20[sun.strongswan.org]
scheduling reauthentication in 3325s
maximum IKE_SA lifetime 3505s
selected proposal: ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ
CHILD_SA net-net{1} established with SPIs c93df650_i c1d5eaa3_o and TS 10.1.0.0/24 === 10.2.0.0/24
received AUTH_LIFETIME of 3344s, scheduling reauthentication in 3164s
connection 'net-net' established successfully
moon $ strongswan status
Security Associations (1 up, 0 connecting):
net-net[1]: ESTABLISHED 9 seconds ago, 192.168.0.10[moon.strongswan.org]...192.168.0.20[sun.strongswan.org]
net-net{1}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: c93df650_i c1d5eaa3_o
net-net{1}: 10.1.0.0/24 === 10.2.0.0/24
sun $ strongswan status
Security Associations (1 up, 0 connecting):
net-net[1]: ESTABLISHED 12 seconds ago, 192.168.0.20[sun.strongswan.org]...192.168.0.10[moon.strongswan.org]
net-net{1}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: c1d5eaa3_i c93df650_o
net-net{1}: 10.2.0.0/24 === 10.1.0.0/24
- 查看 SA 建立日志
moon $ tail -f /var/log/strangswan.log
Apr 5 23:40:49 07[CFG] received stroke: initiate 'net-net'
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_VENDOR task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_INIT task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_NATD task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_CERT_PRE task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_AUTH task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_CERT_POST task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_CONFIG task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing IKE_AUTH_LIFETIME task
Apr 5 23:40:49 08[IKE] <net-net|1> queueing CHILD_CREATE task
Apr 5 23:40:49 08[IKE] <net-net|1> activating new tasks
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_VENDOR task
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_INIT task
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_NATD task
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_CERT_PRE task
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_AUTH task
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_CERT_POST task
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_CONFIG task
Apr 5 23:40:49 08[IKE] <net-net|1> activating CHILD_CREATE task
Apr 5 23:40:49 08[IKE] <net-net|1> activating IKE_AUTH_LIFETIME task
Apr 5 23:40:49 08[IKE] <net-net|1> initiating IKE_SA net-net[1] to 192.168.0.20
Apr 5 23:40:49 08[IKE] <net-net|1> IKE_SA net-net[1] state change: CREATED => CONNECTING
Apr 5 23:40:49 08[CFG] <net-net|1> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/CAMELLIA_CTR_128/CAMELLIA_CTR_192/CAMELLIA_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/AES_XCBC_96/AES_CMAC_96/HMAC_SHA1_96/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/CAMELLIA_CCM_16_128/CAMELLIA_CCM_16_192/CAMELLIA_CCM_16_256/CHACHA20_POLY1305/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/CAMELLIA_CCM_8_128/CAMELLIA_CCM_8_192/CAMELLIA_CCM_8_256/CAMELLIA_CCM_12_128/CAMELLIA_CCM_12_192/CAMELLIA_CCM_12_256/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Apr 5 23:40:49 08[CFG] <net-net|1> sending supported signature hash algorithms: sha256 sha384 sha512 identity
Apr 5 23:40:49 08[ENC] <net-net|1> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Apr 5 23:40:49 08[NET] <net-net|1> sending packet: from 192.168.0.10[500] to 192.168.0.20[500] (1064 bytes)
Apr 5 23:40:49 11[NET] <net-net|1> received packet: from 192.168.0.20[500] to 192.168.0.10[500] (264 bytes)
Apr 5 23:40:49 11[ENC] <net-net|1> parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) ]
Apr 5 23:40:49 11[IKE] <net-net|1> received FRAGMENTATION_SUPPORTED notify
Apr 5 23:40:49 11[IKE] <net-net|1> received SIGNATURE_HASH_ALGORITHMS notify
Apr 5 23:40:49 11[CFG] <net-net|1> selecting proposal:
Apr 5 23:40:49 11[CFG] <net-net|1> proposal matches
Apr 5 23:40:49 11[CFG] <net-net|1> received proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_AES128_XCBC/ECP_256
Apr 5 23:40:49 11[CFG] <net-net|1> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/CAMELLIA_CTR_128/CAMELLIA_CTR_192/CAMELLIA_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/AES_XCBC_96/AES_CMAC_96/HMAC_SHA1_96/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/CAMELLIA_CCM_16_128/CAMELLIA_CCM_16_192/CAMELLIA_CCM_16_256/CHACHA20_POLY1305/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/CAMELLIA_CCM_8_128/CAMELLIA_CCM_8_192/CAMELLIA_CCM_8_256/CAMELLIA_CCM_12_128/CAMELLIA_CCM_12_192/CAMELLIA_CCM_12_256/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Apr 5 23:40:49 11[CFG] <net-net|1> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_AES128_XCBC/ECP_256
Apr 5 23:40:49 11[CFG] <net-net|1> received supported signature hash algorithms: sha256 sha384 sha512 identity
Apr 5 23:40:49 11[IKE] <net-net|1> reinitiating already active tasks
Apr 5 23:40:49 11[IKE] <net-net|1> IKE_CERT_PRE task
Apr 5 23:40:49 11[IKE] <net-net|1> IKE_AUTH task
Apr 5 23:40:49 11[IKE] <net-net|1> authentication of 'moon.strongswan.org' (myself) with pre-shared key
Apr 5 23:40:49 11[IKE] <net-net|1> successfully created shared key MAC
Apr 5 23:40:49 11[CFG] <net-net|1> proposing traffic selectors for us:
Apr 5 23:40:49 11[CFG] <net-net|1> 10.1.0.0/24
Apr 5 23:40:49 11[CFG] <net-net|1> proposing traffic selectors for other:
Apr 5 23:40:49 11[CFG] <net-net|1> 10.2.0.0/24
Apr 5 23:40:49 11[CFG] <net-net|1> configured proposals: ESP:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/NO_EXT_SEQ
Apr 5 23:40:49 11[IKE] <net-net|1> establishing CHILD_SA net-net{1}
Apr 5 23:40:49 11[KNL] <net-net|1> got SPI c93df650
Apr 5 23:40:49 11[ENC] <net-net|1> generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH SA TSi TSr N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
Apr 5 23:40:49 11[NET] <net-net|1> sending packet: from 192.168.0.10[500] to 192.168.0.20[500] (320 bytes)
Apr 5 23:40:49 13[NET] <net-net|1> received packet: from 192.168.0.20[500] to 192.168.0.10[500] (224 bytes)
Apr 5 23:40:49 13[ENC] <net-net|1> parsed IKE_AUTH response 1 [ IDr AUTH SA TSi TSr N(AUTH_LFT) ]
Apr 5 23:40:49 13[IKE] <net-net|1> authentication of 'sun.strongswan.org' with pre-shared key successful
Apr 5 23:40:49 13[IKE] <net-net|1> IKE_SA net-net[1] established between 192.168.0.10[moon.strongswan.org]...192.168.0.20[sun.strongswan.org]
Apr 5 23:40:49 13[IKE] <net-net|1> IKE_SA net-net[1] state change: CONNECTING => ESTABLISHED
Apr 5 23:40:49 13[IKE] <net-net|1> scheduling reauthentication in 3325s
Apr 5 23:40:49 13[IKE] <net-net|1> maximum IKE_SA lifetime 3505s
Apr 5 23:40:49 13[CFG] <net-net|1> selecting proposal:
Apr 5 23:40:49 13[CFG] <net-net|1> proposal matches
Apr 5 23:40:49 13[CFG] <net-net|1> received proposals: ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ
Apr 5 23:40:49 13[CFG] <net-net|1> configured proposals: ESP:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/NO_EXT_SEQ
Apr 5 23:40:49 13[CFG] <net-net|1> selected proposal: ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ
Apr 5 23:40:49 13[CFG] <net-net|1> selecting traffic selectors for us:
Apr 5 23:40:49 13[CFG] <net-net|1> config: 10.1.0.0/24, received: 10.1.0.0/24 => match: 10.1.0.0/24
Apr 5 23:40:49 13[CFG] <net-net|1> selecting traffic selectors for other:
Apr 5 23:40:49 13[CFG] <net-net|1> config: 10.2.0.0/24, received: 10.2.0.0/24 => match: 10.2.0.0/24
Apr 5 23:40:49 13[CHD] <net-net|1> CHILD_SA net-net{1} state change: CREATED => INSTALLING
Apr 5 23:40:49 13[CHD] <net-net|1> using AES_CBC for encryption
Apr 5 23:40:49 13[CHD] <net-net|1> using HMAC_SHA2_256_128 for integrity
Apr 5 23:40:49 13[CHD] <net-net|1> adding inbound ESP SA
Apr 5 23:40:49 13[CHD] <net-net|1> SPI 0xc93df650, src 192.168.0.20 dst 192.168.0.10
Apr 5 23:40:49 13[KNL] <net-net|1> adding SAD entry with SPI c93df650 and reqid {1}
Apr 5 23:40:49 13[KNL] <net-net|1> using encryption algorithm AES_CBC with key size 128
Apr 5 23:40:49 13[KNL] <net-net|1> using integrity algorithm HMAC_SHA2_256_128 with key size 256
Apr 5 23:40:49 13[KNL] <net-net|1> using replay window of 32 packets
Apr 5 23:40:49 13[KNL] <net-net|1> HW offload: no
Apr 5 23:40:49 13[CHD] <net-net|1> adding outbound ESP SA
Apr 5 23:40:49 13[CHD] <net-net|1> SPI 0xc1d5eaa3, src 192.168.0.10 dst 192.168.0.20
Apr 5 23:40:49 13[KNL] <net-net|1> adding SAD entry with SPI c1d5eaa3 and reqid {1}
Apr 5 23:40:49 13[KNL] <net-net|1> using encryption algorithm AES_CBC with key size 128
Apr 5 23:40:49 13[KNL] <net-net|1> using integrity algorithm HMAC_SHA2_256_128 with key size 256
Apr 5 23:40:49 13[KNL] <net-net|1> using replay window of 0 packets
Apr 5 23:40:49 13[KNL] <net-net|1> HW offload: no
Apr 5 23:40:49 13[KNL] <net-net|1> adding policy 10.2.0.0/24 === 10.1.0.0/24 in [priority 375423, refcount 1]
Apr 5 23:40:49 13[KNL] <net-net|1> adding policy 10.2.0.0/24 === 10.1.0.0/24 fwd [priority 375423, refcount 1]
Apr 5 23:40:49 13[KNL] <net-net|1> adding policy 10.1.0.0/24 === 10.2.0.0/24 out [priority 375423, refcount 1]
Apr 5 23:40:49 13[KNL] <net-net|1> getting a local address in traffic selector 10.1.0.0/24
Apr 5 23:40:49 13[KNL] <net-net|1> using host 10.1.0.1
Apr 5 23:40:49 13[KNL] <net-net|1> getting iface name for index 2
Apr 5 23:40:49 13[KNL] <net-net|1> using 192.168.0.20 as nexthop and eth0 as dev to reach 192.168.0.20/32
Apr 5 23:40:49 13[KNL] <net-net|1> installing route: 10.2.0.0/24 via 192.168.0.20 src 10.1.0.1 dev eth0
Apr 5 23:40:49 13[KNL] <net-net|1> getting iface index for eth0
Apr 5 23:40:49 13[IKE] <net-net|1> CHILD_SA net-net{1} established with SPIs c93df650_i c1d5eaa3_o and TS 10.1.0.0/24 === 10.2.0.0/24
Apr 5 23:40:49 13[CHD] <net-net|1> CHILD_SA net-net{1} state change: INSTALLING => INSTALLED
Apr 5 23:40:49 13[KNL] <net-net|1> 192.168.0.10 is on interface eth0
Apr 5 23:40:49 13[IKE] <net-net|1> received AUTH_LIFETIME of 3344s, scheduling reauthentication in 3164s
Apr 5 23:40:49 13[IKE] <net-net|1> activating new tasks
Apr 5 23:40:49 13[IKE] <net-net|1> nothing to initiate
- 查看 Subnet 转发的 iptables 规则。这是由 Strongswan 自动生成的 iptables 规则,完成了 IPSec VPN GW 到 Subnet IP 的转发。就不需要手动添加 route 规则了。同时,也可以查看到 mark(e.g. reqid 2)的匹配情况。tcpdump 是看不到 mark 值的,因为 mark 值在内核维护,不体现在包的内容上面。
moon $ iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 10.2.0.0/24 10.1.0.0/24 policy match dir in pol ipsec reqid 2 proto esp
ACCEPT all -- 10.1.0.0/24 10.2.0.0/24 policy match dir out pol ipsec reqid 2 proto esp
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
sun $ iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 10.1.0.0/24 10.2.0.0/24 policy match dir in pol ipsec reqid 1 proto esp
ACCEPT all -- 10.2.0.0/24 10.1.0.0/24 policy match dir out pol ipsec reqid 1 proto esp
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
- 查看 IPSec 的策略,包括其 mark(e.g. reqid 2)值等
moon $ ip -s xfrm policy
src 10.1.0.0/24 dst 10.2.0.0/24 uid 0
dir out action allow index 569 priority 375423 ptype main share any flag (0x00000000)
lifetime config:
limit: soft (INF)(bytes), hard (INF)(bytes)
limit: soft (INF)(packets), hard (INF)(packets)
expire add: soft 0(sec), hard 0(sec)
expire use: soft 0(sec), hard 0(sec)
lifetime current:
0(bytes), 0(packets)
add 2021-04-05 23:44:12 use 2021-04-05 23:48:06
tmpl src 192.168.0.10 dst 192.168.0.20
proto esp spi 0xc5cfece6(3318738150) reqid 2(0x00000002) mode tunnel
level required share any
enc-mask ffffffff auth-mask ffffffff comp-mask ffffffff
src 10.2.0.0/24 dst 10.1.0.0/24 uid 0
dir fwd action allow index 562 priority 375423 ptype main share any flag (0x00000000)
lifetime config:
limit: soft (INF)(bytes), hard (INF)(bytes)
limit: soft (INF)(packets), hard (INF)(packets)
expire add: soft 0(sec), hard 0(sec)
expire use: soft 0(sec), hard 0(sec)
lifetime current:
0(bytes), 0(packets)
add 2021-04-05 23:44:12 use 2021-04-05 23:48:06
tmpl src 192.168.0.20 dst 192.168.0.10
proto esp spi 0x00000000(0) reqid 2(0x00000002) mode tunnel
level required share any
enc-mask ffffffff auth-mask ffffffff comp-mask ffffffff
src 10.2.0.0/24 dst 10.1.0.0/24 uid 0
dir in action allow index 552 priority 375423 ptype main share any flag (0x00000000)
lifetime config:
limit: soft (INF)(bytes), hard (INF)(bytes)
limit: soft (INF)(packets), hard (INF)(packets)
expire add: soft 0(sec), hard 0(sec)
expire use: soft 0(sec), hard 0(sec)
lifetime current:
0(bytes), 0(packets)
add 2021-04-05 23:44:12 use -
tmpl src 192.168.0.20 dst 192.168.0.10
proto esp spi 0x00000000(0) reqid 2(0x00000002) mode tunnel
level required share any
enc-mask ffffffff auth-mask ffffffff comp-mask ffffffff
常用配置说明
- ipsec.conf:
config setup
cachecrls = yes # 是否缓存证书吊销列表
strictcrlpolicy=yes # 是否严格执行证书吊销规则
uniqueids=no # 如果同一个用户在不同的设备上重复登录,枚举:
# - yes 表示断开旧连接,创建新连接;
# - no 表示保持旧连接,并发送通知;
# - never 同 no,但不发送通知。
ca %default # 配置根证书,如果不使用证书吊销列表,可以不用这段。命名为 %default 所有配置节都会继承它。
crluri = <uri> # 证书吊销列表 URL,可以是 LDAP、HTTP 或文件路径。
conn %default # 定义连接项,命名为 %default 所有连接实例都会继承它。
# 是否启用压缩,yes 表示如果支持压缩会启用。
compress = yes
# 当意外断开后尝试的操作,hold,保持并重连直到超时。
dpdaction = hold
# 意外断开后尝试重连时长。
dpddelay = 30s
# 意外断开后超时时长,只对 IKEv1 起作用。
dpdtimeout = 60s
# 闲置时长,超过后断开连接。
inactivity = 300s
# 数据传输协议加密算法列表。
esp = aes256-sha256,aes256-sha1,3des-sha1!
# 密钥交换协议加密算法列表。
ike = aes256-sha1-modp1024,aes128-sha1-modp1024,3des-sha1-modp1024!
# 默认的密钥交换算法,ike 为自动,优先使用 IKEv2。
keyexchange = ike
# 服务端公网 IP,可以是魔术字 %any,表示从本地 IP 地址表中取。
left = %any
# 客户端 IP,同上。
right = %any
# 指定服务端与客户端的 DNS,多个用 “,” 分隔。
leftdns = 8.8.8.8,8.8.4.4
rightdns = 8.8.8.8,8.8.4.4
# 服务端用于 ike 认证时使用的端口,默认为 500,如果使用了 NAT-T,则使用 4500。
leftikeport = 500
# 服务器端虚拟 IP 地址。
leftsourceip = %config
# 客户端虚拟 IP 段。
rightsourceip = 10.0.0.0/24
# 服务器端子网,魔术字 0.0.0.0/0 。如果为客户端分配虚拟 IP 地址的话,那表示之后要做 iptables 转发,那么服务器端就必须是用魔术字。
leftsubnet = 0.0.0.0/0
# rightsubnet = [[]][,...]
conn IKEv2-BASE
# 服务器端根证书 DN 名称。
leftca = "C=CN, O=123si, CN=123si StrongSwan CA"
# 服务器证书,可以是 PEM 或 DER 格式。
leftcert = server.cert.pem
# 不指定客户端证书路径。
# rightcert = |
# 是否发送服务器证书到客户端。
leftsendcert = always
# 客户端不发送证书。
rightsendcert = never
# 服务端认证方法,使用证书。
leftauth = pubkey
# 客户端认证使用 EAP 扩展认证,貌似 eap-mschapv2 比较通用。
rightauth = eap-mschapv2
# 服务端 ID,可以任意指定,默认为服务器证书的 subject,还可以是魔术字 %any,表示什么都行。
leftid = .itnmg.net
# 客户端 id,任意。
rightid = %any
# ios, mac os, win7+, linux
conn IKEv2-EAP
also = IKEv2-BASE
# 指定客户端 eap id。
eap_identity = %any
# 不自动重置密钥。
rekey = no
# 开启 IKE 消息分片。
fragmentation = yes
# 当服务启动时,应该如何处理这个连接项。add 添加到连接表中。
auto = add