0018-TIPS-pawnyable : NULL-Pointer-Dereference
原文
NULL Pointer Dereference
题目下载
环境宽松限制
启动选项中可以看到,SMAP在被攻击的机器上被禁用。除非禁用 SMAP,否则无法利用本章中讨论的 NULL 指针取消引用。
还可以尝试启动该内核并输入以下命令:
$ cat /proc/sys/vm/mmap_min_addr
0
mmap_min_addr是一个 Linux 内核变量,顾名思义,它限制可以从用户态mmap映射的最低地址。
请注意,默认情况下它是一个非零值,但在我们的攻击目标中设置为 0。
该变量是从 Linux 内核版本 2.6.23 引入的,作为 NULL 指针取消引用的缓解措施,我们将在此处处理该问题。
本章的内容是基于可以避免SMAP和mmap缓解的前提下的攻击。
代码分析
#include module_open
CMD_INIT
CMD_SETKEY
CMD_SETDATA
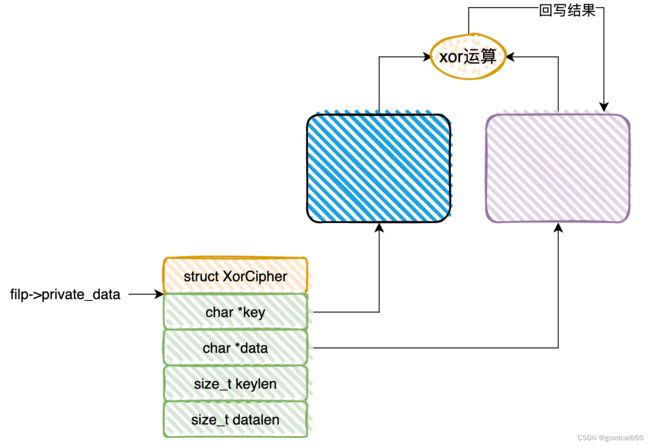
CMD_ENCRYPT && CMD_ENCRYPT
CMD_GETDATA
漏洞分析
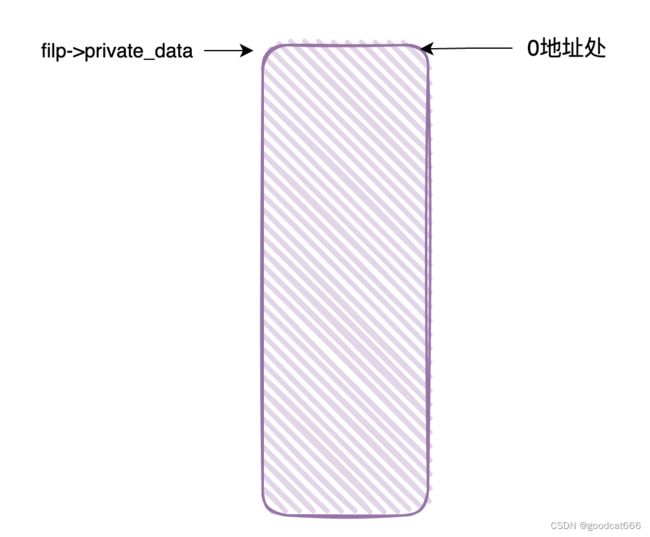
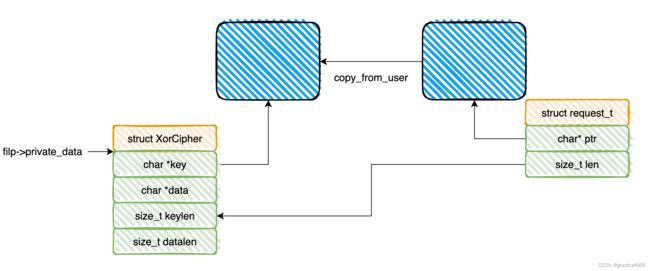
代码在CMD_SETKEY和CMD_SETDATA,会检查filp->private_data是否指向null,这没问题
ctx = (XorCipher*)filp->private_data;
case CMD_SETDATA:
if (!ctx) return -EINVAL;
case CMD_SETKEY:
if (!ctx) return -EINVAL;
但是在CMD_GETDATA、CMD_SETDATA、CMD_ENCRYPT、CMD_DECRYPT处没有检查filp->private_data是否指向null
(重要前提,没有开启smap保护、关闭了mmap_min_addr限制)
会产生如下的问题
exp
#define _GNU_SOURCE
#include