网络爬虫-tx滑块验证码
仅供研究学习使用。
目标站点 --> 腾讯防水墙官网
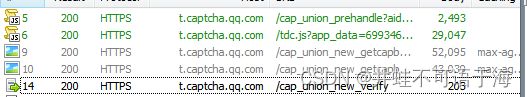
首先打开Fiddler,刷新下页面完成一组操作,发现主要请求有这几个
1是初始化验证码。详细请求为
GET https://t.captcha.qq.com/cap_union_prehandle?aid=2100049389&protocol=https&accver=1&showtype=popup&ua=TW96aWxsYS81LjAgKFdpbmRvd3MgTlQgNi4xOyBXT1c2NCkgQXBwbGVXZWJLaXQvNTM3LjM2IChLSFRNTCwgbGlrZSBHZWNrbykgQ2hyb21lLzk0LjAuNDYwNi43MSBTYWZhcmkvNTM3LjM2IENvcmUvMS45NC4xNzguNDAwIFFRQnJvd3Nlci8xMS4yLjUxNzAuNDAw&noheader=1&fb=1&aged=0&enableAged=0&enableDarkMode=0&grayscale=1&clientype=2&cap_cd=&uid=&lang=zh-cn&entry_url=https%3A%2F%2F007.qq.com%2F&elder_captcha=0&js=%2Ftcaptcha-frame.32287577.js&login_appid=&wb=2&subsid=1&callback=_aq_139895&sess= HTTP/1.1
Host: t.captcha.qq.com
Connection: keep-alive
sec-ch-ua: ";Not A Brand";v="99", "Chromium";v="94"
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36 Core/1.94.178.400 QQBrowser/11.2.5170.400
sec-ch-ua-platform: "Windows"
Accept: */*
Sec-Fetch-Site: same-site
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: script
Referer: https://007.qq.com/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Q-UA2: PR=PC&CO=WBK&QV=3&PL=WIN&PB=GE&PPVN=11.2.0.5170&COVC=049400&CHID=44786&RL=1920*1080&MO=QB&VE=GA&BIT=64&OS=6.1.7601
Q-GUID: 12eb8448974e4152c6b727b2377988cb
参数的详细介绍(猜想),仅仅介绍需要变动的参数,不介绍的固定就可以:
aid:项目的ID,不同网站的aid不同
asig:这个验证码请求的id,每次验证码不同。这个asig在前面几个http请求中,网站都会返回
ua:浏览器的user-agent,进行了base64编码
uid:登录账号,在有些网站可能这个需要
其他参数固定就可以。
返回内容为:
_aq_139895({"state":1,"ticket":"","capclass":"1","subcapclass":"10052","src_1":"cap_union_new_show","src_2":"template/new_placeholder.html","src_3":"template/new_slide_placeholder.html","sess":"s0VOw_97_vJctxxc0EL1-vmZBsw4fmYz92h2Bv--q8qaMCLtr0W8E40yrPjWUfV_zdQby0l39fEFyFlTqdTMojXyhZUfmhzX_KVSvBPjQP9s8CQa32ZKxdGgyx2ojb6F2f1hCmDT4rKWzVE-pz0YBf8U71zoRMKjKr4AB-iQRcCsdxw77XNU5iCSuKUgW_TIomdN0HTMAssyUEKpIexy6VYe5aoVcuQs12H-5isrqaQeaELIiMNbfSLKSZiWJzeZkIFMCYfJVM-CTxOSGEUxgp7_6L35DwSjoel7mlQYzoTBsgLMnnGC9repeBl_I6U0Xj6cLzk1FahbHItPj260STXA**","randstr":"","sid":"6994123938815057921","log_js":"","data":{"comm_captcha_cfg":{"tdc_path":"/tdc.js?app_data=6994123938815057921&t=1285156112","feedback_url":"https://support.qq.com/products/304457","pow_cfg":{"prefix":"6a76ff402b053df2#","md5":"f2c7789f216268808b8bc756ed6d2ab9"}},"dyn_show_info":{"lang":"zh-cn","instruction":"拖动下方滑块完成拼图","bg_elem_cfg":{"sprite_pos":[0,0],"size_2d":[672,480],"img_url":"/cap_union_new_getcapbysig?img_index=1&image=0244270000ff480900000009da2592502ec5&sess=s04lpAPNzBKI8cwN98XCyGgnjPdbywlD4HclpSZywBCWDAh9CWYWGKVdykKdBheaInUw5bgs2K5jZYP3qr5AjkbNOD-WRmMWNy1oYRLZYyQL01_SV3vVMqksWoMd0836aU-kdzOL5FAYUQut92w5J2QAAGYRbQHLlVC6fKUv-PY_Cx1XtAn-O8TxS4dXhjpWCpjxiUP1G5IcxaATKd6b-jN4UcIEGW73vbQvVRbMFMW57yRE37ycnj31Se3fj8UxHiyp3Z0Lsn3-V4QNjzZmDDGCrjTXmgMYr9uQi1NI1Gz_wsUHTSzCKKfgK_V71ygzcVotfdss4prXxTWkzJEPqSmg**"},"fg_elem_list":[{"id":3,"sprite_pos":[0,422],"size_2d":[672,32],"init_pos":[0,422]},{"id":1,"sprite_pos":[140,490],"size_2d":[120,120],"init_pos":[50,69],"move_cfg":{"track_limit":"x>=50&&x<=552","move_factor":[1,0],"data_type":["DynAnswerType_POS"]}},{"id":2,"sprite_pos":[0,490],"size_2d":[130,70],"init_pos":[45,402],"move_cfg":{"track_limit":"x>=50&&x<=552","move_factor":[1,0]},"type":"slider"}],"fg_binding_list":[{"master":1,"slave":2,"bind_type":"DynBindType_DX_DX","bind_factor":1},{"master":2,"slave":1,"bind_type":"DynBindType_DX_DX","bind_factor":1}],"sprite_url":"/cap_union_new_getcapbysig?img_index=0&image=0244270000ff480900000009da2592502ec5&sess=s04lpAPNzBKI8cwN98XCyGgnjPdbywlD4HclpSZywBCWDAh9CWYWGKVdykKdBheaInUw5bgs2K5jZYP3qr5AjkbNOD-WRmMWNy1oYRLZYyQL01_SV3vVMqksWoMd0836aU-kdzOL5FAYUQut92w5J2QAAGYRbQHLlVC6fKUv-PY_Cx1XtAn-O8TxS4dXhjpWCpjxiUP1G5IcxaATKd6b-jN4UcIEGW73vbQvVRbMFMW57yRE37ycnj31Se3fj8UxHiyp3Z0Lsn3-V4QNjzZmDDGCrjTXmgMYr9uQi1NI1Gz_wsUHTSzCKKfgK_V71ygzcVotfdss4prXxTWkzJEPqSmg**","color_scheme":"#1A65FF"}},"uip":"125.86.119.41"})
都是验证码需要的一些参数,后面会用到
2是验证码的获取 获取之后可以计算出滑块的距离 这个我们可以通过ddddocr来进行识别
GET https://t.captcha.qq.com/cap_union_new_getcapbysig?img_index=1&image=0244270000ff480900000009da2592502ec5&sess=s04lpAPNzBKI8cwN98XCyGgnjPdbywlD4HclpSZywBCWDAh9CWYWGKVdykKdBheaInUw5bgs2K5jZYP3qr5AjkbNOD-WRmMWNy1oYRLZYyQL01_SV3vVMqksWoMd0836aU-kdzOL5FAYUQut92w5J2QAAGYRbQHLlVC6fKUv-PY_Cx1XtAn-O8TxS4dXhjpWCpjxiUP1G5IcxaATKd6b-jN4UcIEGW73vbQvVRbMFMW57yRE37ycnj31Se3fj8UxHiyp3Z0Lsn3-V4QNjzZmDDGCrjTXmgMYr9uQi1NI1Gz_wsUHTSzCKKfgK_V71ygzcVotfdss4prXxTWkzJEPqSmg** HTTP/1.1
Host: t.captcha.qq.com
Connection: keep-alive
sec-ch-ua: ";Not A Brand";v="99", "Chromium";v="94"
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36 Core/1.94.178.400 QQBrowser/11.2.5170.400
sec-ch-ua-platform: "Windows"
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: image
Referer: https://t.captcha.qq.com/template/drag_ele.html
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Q-UA2: PR=PC&CO=WBK&QV=3&PL=WIN&PB=GE&PPVN=11.2.0.5170&COVC=049400&CHID=44786&RL=1920*1080&MO=QB&VE=GA&BIT=64&OS=6.1.7601
Q-GUID: 12eb8448974e4152c6b727b2377988cb
这里提供一个参考方法
import ddddocr
def get_gap(target_img:bytes, background_img:bytes):
det = ddddocr.DdddOcr(det=False, ocr=False, show_ad=False)
res = det.slide_match(target_img, background_img,simple_target=True)
print(res)
return res["target"][0]
3是提交验证码获取ticket
POST https://t.captcha.qq.com/cap_union_new_verify HTTP/1.1
Host: t.captcha.qq.com
Connection: keep-alive
Content-Length: 2621
sec-ch-ua: ";Not A Brand";v="99", "Chromium";v="94"
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36 Core/1.94.178.400 QQBrowser/11.2.5170.400
sec-ch-ua-platform: "Windows"
Origin: https://t.captcha.qq.com
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://t.captcha.qq.com/template/drag_ele.html
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Q-UA2: PR=PC&CO=WBK&QV=3&PL=WIN&PB=GE&PPVN=11.2.0.5170&COVC=049400&CHID=44786&RL=1920*1080&MO=QB&VE=GA&BIT=64&OS=6.1.7601
Q-GUID: 12eb8448974e4152c6b727b2377988cb
collect=uJ6zP0Gw%2BhnLR8DozwV%2BRpXsJ6YCiqIRf%2BkFkPM2CIrexkCfC%2FMdkZgaT5%2BtWYACqu2vJyjtif0X%2BoF%2BBn35nOHsWo7OGfyNFIsjoawaPVLG%2F3U1pTQVoAqOf%2Bh0u0NotNdjfYrJ9oVPgdTp4Zjz%2FkFO0WxGlKi%2FER8BZGVMEHIKuC7BGBfxbVjyE%2FFRYMynoGQcQ1Z0qJ%2B5HvG21Z2AGVEY3XnGzXC6SIGqRvhRqmf0E8ZHvOFLLPQTxke84UssKE4yroEcpiC8ffcOHH7fURxNVQsmmuqExqBt119VSRMvbr7421C1LOTVyaDUFifarZC8UCdCZ8nVCt1wPD2YDFGXbdu1IlTGeExiBuBpOI3umeXccNt79WBXxRZn0xf9n4xNqenpb8daJdqHxVP1SFlsst15cOi%2FmOR4lYWlt9xScClwZuGkA75hIbJ%2FNFVyxKugQG7KlI1HrySuN9qsoN92QfvbOOIpeNxvFBrscFTyW44IwrDzLINGuD%2F%2Bs7j3nheUL5Fs3Lgqtz4A9wTsaNhXWaTTxDULENtr12eOtLqiMXbvJo8kvUX0WGdN2JqOIFzPkGvWU2KC4Kzyz95zTdyVbHj2XJNhMAqCzjUXS6lNzTUl01qyJK32ZIgkorhFvOSvppGHZPURwQkyrO3GgOwF9qTg8dF9cBbx99F2dgOPV73GotDnPHpzc9Z2Qcng2ZDmN7D1agxD5crIraRB2zSUYuP%2FAQn9m4jEpDSOU8UdabE0cvIhdET0DmttqIvWcWh0pZdrmFyLIPga9d7CiDd1qECRYoHAPfJeVlRq2SQfrT05c82SrdXeM%2BAL781zzfPlyd3Nq5Lsg4%2B3B3QTWgo3iRP%2FFbg%2BdwXAVgE%2Fe1A2t02sCpNm0x51mrpfNw0zr5SMfpUcYr7V3jPgC%2B%2FNc1lsst15cOi%2FTbQQkZSOfp1%2B3Z3UG2Brjs6Ut%2FwK2ZvXQttkazg2Wmg%2FX5MTa66FhGcTeq5CHnqQfae2J2500iq6NQUH7rZek27rBVAQYCONY3WIHr11pD5VxBl%2Bp8qhDkPthg8Nu2UhH609OXPNkq2qBVitH15P3gD19rJCDlqQppdcm0cbFIX0E8ZHvOFLLPQTxke84UsswtwRLTB%2BGOFlfoPRegaQfnjDk9aM1Bwbou%2FCYEaZ665FP5%2FTXPV7V7Lf4IrdWFUXs21TT5OA4GW8Sq5HmuIuUrUo0BOh55ZvaJRfV%2BUPO9OSUOXRfQRJJdijZPdPzB0QpRZPrXc5U%2B8phML34yVLpEB4uGzhRp3TEkP5vMZa%2FWR2zZdwq60OZWlhpKH4a9I23hCIqF%2BY6i9lS6Olr22Q%2BLzyYEDwqrRNvAL2GLzDUt0%2BxIDkZxbDYrNtU0%2BTgOBlvyDXoQXg6IzF%2F3cvmI0QI42OdnT0eGCq5JX3Q8yzAKVglnK7YqzrgtqhnTE6PWaMzyG68ralf5iH5QfaR2QOQuEChJF00ecgFj1Nqvf42IbvUPe5d1PCqJtkl9Y13xcrZUejJh%2BEVP6aMXPYlD35FbNodN%2FkxO7jBGdLs8FBMQEjiaU2RXO4eQUFkoQwNNXllH8ncK2oNZFeUinwmsXcjxtZunEzNMVJU86u7Mf0zF8N0jIvDmQhNHG5BuW5HZb4uSAWR05uUrNrCTVKAge2DZUseCnuYly%2F9BPGR7zhSyz0E8ZHvOFLLPQTxke84UsshovKdPcq7atiCwS%2BHJ36PU77qB2g5uDADb6KqBARtEIjeIDgKij1wQ%3D%3D&tlg=1752&eks=yw7zybDLv%2FBiP48QZl1s8awLr775AKQThnRNaDm2Jc4XtOueigsUUgxqPmjufduUDC7dF5NUEHIsqQR2xOfz6vZ7rdUdiEtiQXZrPqZE%2FWRSeQZVKw6fl2BiQkUWJGMKeLkvJPv7BMzBEgSgH9zqw4UCenQRTLApvfsQOVrfdNG95aohTys5vYKaXH8XpQyp9CZet9wGZsIUSYOdE8e%2FDaDcKTngQx8XpYkygJ7%2FpNg%3D&sess=s0VOw_97_vJctxxc0EL1-vmZBsw4fmYz92h2Bv--q8qaMCLtr0W8E40yrPjWUfV_zdQby0l39fEFyFlTqdTMojXyhZUfmhzX_KVSvBPjQP9s8CQa32ZKxdGgyx2ojb6F2f1hCmDT4rKWzVE-pz0YBf8U71zoRMKjKr4AB-iQRcCsdxw77XNU5iCSuKUgW_TIomdN0HTMAssyUEKpIexy6VYe5aoVcuQs12H-5isrqaQeaELIiMNbfSLKSZiWJzeZkIFMCYfJVM-CTxOSGEUxgp7_6L35DwSjoel7mlQYzoTBsgLMnnGC9repeBl_I6U0Xj6cLzk1FahbHItPj260STXA**&ans=%5B%7B%22elem_id%22%3A1%2C%22type%22%3A%22DynAnswerType_POS%22%2C%22data%22%3A%22431%2C69%22%7D%5D&pow_answer=6a76ff402b053df2%238036&pow_calc_time=52
参数分析:
ans为滑块缺口坐标
主要参数就是eks 和 collect这两个参数,eks对应 TDC.getInfo, collect 对应 TDC.getData
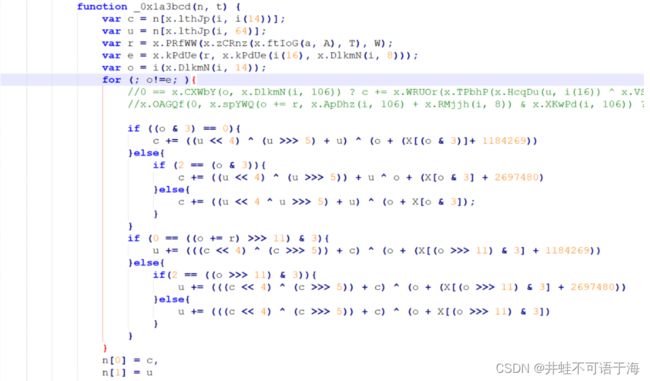
加密参数分析
部分还原代码
function r(t, n) {
var e = (65535 & t) + (65535 & n);
return (t >> 16) + (n >> 16) + (e >> 16) << 16 | 65535 & e
}
function o(t, n, e, o, u, f) {
return r(function (t, n) {
return t << n | t >>> 32 - n
}(r(r(n, t), r(o, f)), u), e)
}
function u(t, n, e, r, u, f, a) {
return o(n & e | ~n & r, t, n, u, f, a)
}
function f(t, n, e, r, u, f, a) {
return o(n & r | e & ~r, t, n, u, f, a)
}
function a(t, n, e, r, u, f, a) {
return o(n ^ e ^ r, t, n, u, f, a)
}
function i(t, n, e, r, u, f, a) {
return o(e ^ (n | ~r), t, n, u, f, a)
}
function c(t, n) {
var e, o, c, l, s;
t[n >> 5] |= 128 << n % 32, t[14 + (n + 64 >>> 9 << 4)] = n;
var d = 1732584193, p = -271733879, g = -1732584194, _ = 271733878;
for (e = 0; e < t.length; e += 16) o = d, c = p, l = g, s = _, p = i(p = i(p = i(p = i(p = a(p = a(p = a(p = a(p = f(p = f(p = f(p = f(p = u(p = u(p = u(p = u(p, g = u(g, _ = u(_, d = u(d, p, g, _, t[e], 7, -680876936), p, g, t[e + 1], 12, -389564586), d, p, t[e + 2], 17, 606105819), _, d, t[e + 3], 22, -1044525330), g = u(g, _ = u(_, d = u(d, p, g, _, t[e + 4], 7, -176418897), p, g, t[e + 5], 12, 1200080426), d, p, t[e + 6], 17, -1473231341), _, d, t[e + 7], 22, -45705983), g = u(g, _ = u(_, d = u(d, p, g, _, t[e + 8], 7, 1770035416), p, g, t[e + 9], 12, -1958414417), d, p, t[e + 10], 17, -42063), _, d, t[e + 11], 22, -1990404162), g = u(g, _ = u(_, d = u(d, p, g, _, t[e + 12], 7, 1804603682), p, g, t[e + 13], 12, -40341101), d, p, t[e + 14], 17, -1502002290), _, d, t[e + 15], 22, 1236535329), g = f(g, _ = f(_, d = f(d, p, g, _, t[e + 1], 5, -165796510), p, g, t[e + 6], 9, -1069501632), d, p, t[e + 11], 14, 643717713), _, d, t[e], 20, -373897302), g = f(g, _ = f(_, d = f(d, p, g, _, t[e + 5], 5, -701558691), p, g, t[e + 10], 9, 38016083), d, p, t[e + 15], 14, -660478335), _, d, t[e + 4], 20, -405537848), g = f(g, _ = f(_, d = f(d, p, g, _, t[e + 9], 5, 568446438), p, g, t[e + 14], 9, -1019803690), d, p, t[e + 3], 14, -187363961), _, d, t[e + 8], 20, 1163531501), g = f(g, _ = f(_, d = f(d, p, g, _, t[e + 13], 5, -1444681467), p, g, t[e + 2], 9, -51403784), d, p, t[e + 7], 14, 1735328473), _, d, t[e + 12], 20, -1926607734), g = a(g, _ = a(_, d = a(d, p, g, _, t[e + 5], 4, -378558), p, g, t[e + 8], 11, -2022574463), d, p, t[e + 11], 16, 1839030562), _, d, t[e + 14], 23, -35309556), g = a(g, _ = a(_, d = a(d, p, g, _, t[e + 1], 4, -1530992060), p, g, t[e + 4], 11, 1272893353), d, p, t[e + 7], 16, -155497632), _, d, t[e + 10], 23, -1094730640), g = a(g, _ = a(_, d = a(d, p, g, _, t[e + 13], 4, 681279174), p, g, t[e], 11, -358537222), d, p, t[e + 3], 16, -722521979), _, d, t[e + 6], 23, 76029189), g = a(g, _ = a(_, d = a(d, p, g, _, t[e + 9], 4, -640364487), p, g, t[e + 12], 11, -421815835), d, p, t[e + 15], 16, 530742520), _, d, t[e + 2], 23, -995338651), g = i(g, _ = i(_, d = i(d, p, g, _, t[e], 6, -198630844), p, g, t[e + 7], 10, 1126891415), d, p, t[e + 14], 15, -1416354905), _, d, t[e + 5], 21, -57434055), g = i(g, _ = i(_, d = i(d, p, g, _, t[e + 12], 6, 1700485571), p, g, t[e + 3], 10, -1894986606), d, p, t[e + 10], 15, -1051523), _, d, t[e + 1], 21, -2054922799), g = i(g, _ = i(_, d = i(d, p, g, _, t[e + 8], 6, 1873313359), p, g, t[e + 15], 10, -30611744), d, p, t[e + 6], 15, -1560198380), _, d, t[e + 13], 21, 1309151649), g = i(g, _ = i(_, d = i(d, p, g, _, t[e + 4], 6, -145523070), p, g, t[e + 11], 10, -1120210379), d, p, t[e + 2], 15, 718787259), _, d, t[e + 9], 21, -343485551), d = r(d, o), p = r(p, c), g = r(g, l), _ = r(_, s);
return [d, p, g, _]
}
function l(t) {
var n, e = "";
for (n = 0; n < 32 * t.length; n += 8) e += String.fromCharCode(t[n >> 5] >>> n % 32 & 255);
return e
}
function s(t) {
var n, e = [];
for (e[(t.length >> 2) - 1] = void 0, n = 0; n < e.length; n += 1) e[n] = 0;
for (n = 0; n < 8 * t.length; n += 8) e[n >> 5] |= (255 & t.charCodeAt(n / 8)) << n % 32;
return e
}
function d(t) {
var n, e, r = "0123456789abcdef", o = "";
for (e = 0; e < t.length; e += 1) n = t.charCodeAt(e), o += r.charAt(n >>> 4 & 15) + r.charAt(15 & n);
return o
}
function p(t) {
return unescape(encodeURIComponent(t))
}
function g(t) {
return function (t) {
return l(c(s(t), 8 * t.length))
}(p(t))
}
function _(t, n) {
return function (t, n) {
var e, r, o = s(t), u = [], f = [];
for (u[15] = f[15] = void 0, o.length > 16 && (o = c(o, 8 * t.length)), e = 0; e < 16; e += 1) u[e] = 909522486 ^ o[e], f[e] = 1549556828 ^ o[e];
return r = c(u.concat(s(n)), 512 + 8 * n.length), l(c(f.concat(r), 640))
}(p(t), p(n))
}
function v(t, n, e) {
return n ? e ? _(n, t) : function (t, n) {
return d(_(t, n))
}(n, t) : e ? g(t) : function (t) {
return d(g(t))
}(t)
}
function get_ans (t, n) {
for (var e = t.nonce, r = t.target, o = +new Date, u = 0, f = "number" == typeof n ? n : 3e4; v("" + e + u) !== r
&& (u += 1, !(+new Date - o > f));) ;
// console.log(t);
console.log(u);
return u
}
get_ans({target: '29acdd2524943c824aaf0d0f38daa2c9', nonce: '80b6d873c59ffb74#'})
function md5(n, t, r) {
return t ? r ? m(t, n) : s(t, n) : r ? C(n) : A(n)
}
function cdata(y) {
if ("string" == typeof y && "" != y) {
var r = 0;
y = y.replace(/"/g, '"'), y = y.replace(/'/g, "'");
var n;
try {
n = eval('(' + y + ')')
} catch (e) {
}
;
if ("object" == typeof n && "string" == typeof n.randstr && ("string" == typeof n.M || "number" == typeof n.M) && "string" == typeof n.ans) {
n.ans = n.ans.toLowerCase(), n.M = parseInt(n.M);
for (var s = 0; s < n.M && s < 1e3; s++) {
var i = n.randstr + s, c = md5(i);
if (n.ans == c.toLowerCase()) {
r = s;
return r;
}
}
}
}
};
function rnd() {
return Math.floor(1e6 * Math.random())
};
function random() {
return +new Date();
};