- Kubernetes(K8S)学习笔记(2):Kubernetes架构
徐卷
分布式与并行计算kubernetes学习笔记云计算
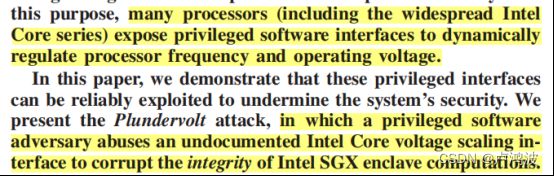
注:该笔记整理自Kubernetes官方文档中的内容,笔记中使用的观点与资源均来源于官方文档以及我个人的理解,如果涵盖其它来源的观点,会额外标明引用。1、相关概念Kubernetes集群由一个控制平面与一组用于运行容器化应用的工作机器组成,我们把这些工作机器称之为节点(Node)。工作节点托管着组成工作负载的Pod,控制平面负责管理工作节点以及Pod,以下为Kubernetes集群组件的逻辑关系图
- Python 爬虫实战:全球公司财报数据抓取与财务健康分析
西攻城狮北
python爬虫开发语言
一、引言在当今数字化时代,数据已成为企业决策、投资分析和市场研究的关键要素。公司财报数据作为企业经营状况的重要反映,对于投资者、分析师以及企业管理者来说具有极高的价值。通过获取和分析全球公司的财报数据,我们可以深入了解企业的财务健康状况,为投资决策提供有力支持。本文将详细介绍如何使用Python爬虫技术抓取全球公司财报数据,并进行财务健康分析。二、爬虫环境搭建在开始爬取数据之前,我们需要先搭建好P
- IntelliJ IDEA 常用快捷键大全(Windows 版)
L_!!!
ideaintellij-ideaide
IntelliJIDEA常用快捷键大全(Windows版)注意事项:部分快捷键与QQ、QQ音乐、输入法等常用软件冲突,可能导致失效!推荐优先解决Ctrl+Alt+L(格式化代码)和Ctrl+Space(代码补全)的冲突。一、导航与搜索功能快捷键冲突提醒打开最近文件Ctrl+E无跳转到类Ctrl+N无跳转到文件Ctrl+Shift+N无跳转到行Ctrl+G无全局搜索文件内容Ctrl+Shift+F可
- Java中Scanner类应用详解
海边漫步者
Java基础java开发语言
Java中的Scanner类应用详解在java编程中,Scanner类是一个用于读取数据的常用工具,可以从文件、输入流、字符串中读取数据。本文从常用构造方法、常用方法两个方面讲解其功能并举例说明。该类尚有其他的构造方法与一般方法,有技术开发需求的读者可以从官网查看API文档学习应用。一、常用构造方法1.Scanner(InputStreamsource)功能:构造一个新的Scanner,它生成的值
- Java基础——常用运算符、scanner类介绍
咋说话呢?
java
目录一、.scanner类介绍1.使用方法2.next()方法与nextLine()方法二、常用运算符1.赋值运算符2.算术运算符3.关系运算符4.逻辑运算符5.位运算符6.条件运算符7.运算符的优先级一、.scanner类介绍Scanner类是一个用于Scanner指的是java.util包下的Scanner类,可以接收控制台输入的数据。位置:Java.util.Scanner;1.使用方法第一
- Linux的权限
巷子里的童年ya
linux运维服务器centos
基本权限与归属读取:允许查看内容-readr写入:允许修改内容-writew可执行:允许运行和切换-excutex1、对于文本文件:r读取权限:cat、less、grep、head、tailw写入权限:vim、>、>>x可执行权限:Shell与Python\Go2、对于目录:r读取权限:ls命令查看目录内容w写入权限:能够创建、删除、修改等目录的内容x执行权限:能够cd切换到此目录下(进入此目录)
- Java项目设计文档:架构、模块与实现策略详解
体制教科书
本文还有配套的精品资源,点击获取简介:Java项目设计文档是项目规划、实施和维护的重要指导工具,包含系统架构、模块划分、接口定义、类设计、数据库设计、异常处理、测试计划、性能优化以及部署运维等方面。本设计文档集合对于理解Java项目的架构设计和提升项目开发质量具有极高的参考价值。1.项目背景阐述在当今数字化转型的大潮中,企业对于IT系统的依赖日益加重。项目背景阐述这一章,将为您揭示本次项目的发起缘
- Java 程序员必读书单
AI天才研究院
DeepSeekR1&大数据AI人工智能大模型Java实战深度学习实战自然语言处理人工智能语言模型编程实践开发语言架构设计
作者:禅与计算机程序设计艺术1.简介Java是一门高级、新兴的静态面向对象编程语言,在互联网、移动互联网、大数据、云计算、人工智能、物联网等领域都有广泛应用。作为Java程序员的你是否也经常被面试官或者HR问到有关Java的知识点呢?如果你最近在准备面试或阅读相关技术文档,则本文正是适合你。在本文中,我将给你一些你可能不知道的关于Java的重要概念和知识,并通过具体的代码示例和图表来帮助你理解这些
- SvelteKit 最新中文文档教程(9)—— 部署静态站点与单页应用
前言Svelte,一个语法简洁、入门容易,面向未来的前端框架。从Svelte诞生之初,就备受开发者的喜爱,根据统计,从2019年到2024年,连续6年一直是开发者最感兴趣的前端框架No.1:Svelte以其独特的编译时优化机制著称,具有轻量级、高性能、易上手等特性,非常适合构建轻量级Web项目。为了帮助大家学习Svelte,我同时搭建了Svelte最新的中文文档站点。如果需要进阶学习,也可以入手我
- HarmonyOS NEXT 基于原生能力获取视频缩略图
大家好,我是V哥。不得不佩服HarmonyOSNEXT原生能力的强大,如果你想在鸿蒙APP开发中获取视频缩略图,不用依赖第三方库,就可以高效和稳定的实现,AVMetadataHelper就是一个好帮手,下面V哥整理实现步骤的代码,帮助你快速理解,开整。想要学习鸿蒙开发,一定绕不开学习ArkTS语言,V哥写了三本鸿蒙开发之路的书,第一本《鸿蒙HarmonyOSNEXT开发之路卷1ArkTS篇》已上市
- 灵活运用HarmonyOS NEXT布局管理器,实现完美的自适应布局
harmonyos
灵活运用HarmonyOSNEXT布局管理器,实现完美的自适应布局在多设备和多样化的屏幕尺寸环境中开发应用时,创建一个既能适应不同屏幕尺寸又能保持良好视觉效果的布局至关重要。本文将深入探讨HarmonyOSNEXT提供的几种布局管理器及其工作原理,指导开发者如何利用这些工具实现高效的自适应布局,并提供API12版本的具体示例代码。Flex布局:沿主轴和交叉轴排列子元素Flex布局是一种强大的布局模
- 鸿蒙开发:正则中的match和matchAll
前言本文基于Api13关于正则表达式,其实之前也撰写过相关文章,但没有对match和matchAll做过详细的分析,虽然都是用于常见的字符串匹配,但是在使用方式上还是具有一定的区别;大家记住一点,正则表达式适用于所有的编程语言,可能有些语法和使用方式有些不同,但基本的原理是一样的。我们先看下源码:match:将字符串与正则表达式匹配,并返回一个包含该搜索结果的数组。/***Matchesastri
- ArkTS函数与模块的定义与调用
harmonyos
ArkTS是一种面向全场景的声明式编程语言,它在函数与模块的定义和调用方面有着独特的特点和优势。一、ArkTS函数的定义在ArkTS中,函数是一段可以重复使用的代码块,用于执行特定的任务。函数可以接受输入参数,并返回一个值。例如:在这个例子中,add是函数名,a和b是输入参数,number是参数和返回值的类型。通过定义函数,可以将复杂的任务分解为较小的、可管理的部分,提高代码的可读性和可维护性。二
- 深入探索HarmonyOS NEXT自定义组件与样式,提升应用个性化水平
harmonyos
深入探索HarmonyOSNEXT自定义组件与样式,提升应用个性化水平在HarmonyOSNEXT平台上开发应用程序时,创建自定义组件和有效应用样式是实现独特用户体验的关键。本文将详细介绍如何从零开始构建自定义组件,并探讨如何利用样式系统来统一整个应用的视觉风格。我们将重点介绍API12版本中支持的功能和技术,帮助开发者提升应用的个性化水平。创建自定义组件:封装特定功能和外观自定义组件允许开发者封
- HarmonyOS NEXT 应用开发:用户反馈收集与处理
harmonyos
在应用的生命周期中,用户反馈是提升应用质量、优化用户体验以及增强市场竞争力的重要依据。对于开发者来说,如何有效地收集、分析和处理用户反馈,已成为一项关键的运营任务。在HarmonyOSNEXT环境中,开发者不仅需要关注功能实现和技术优化,还需要建立高效的用户反馈机制,以确保应用能够持续满足用户需求、解决用户痛点,并在市场中不断迭代和进步。本部分将介绍在HarmonyOSNEXT应用开发中,如何通过
- YashanDB yasrman恢复
数据库
本文内容来自YashanDB官网,原文内容请见https://doc.yashandb.com/yashandb/23.3/zh/%E6%95%B0%E6%8D%AE%...操作说明执行恢复操作的数据库版本需与生成备份集的数据库版本完全一致。恢复语法详细说明请参考工具手册yasrman。分布式部署模式下,需要保证待恢复的集群部署状态与备份前节点部署状态一致,包括节点类型、节点监听IP、节点个数、节
- 一文彻底搞清楚HarmonyOS NEXT的元服务
harmonyos-next
程序员Feri一名12年+的程序员,做过开发带过团队创过业,擅长Java、嵌入式、鸿蒙、人工智能等,专注于程序员成长那点儿事,希望在成长的路上有你相伴!君志所向,一往无前!1.什么是元服务在万物互联时代,人均持有设备量不断攀升,设备种类和使用场景更加多样,使得应用开发、应用入口变得更加复杂。在此背景下,应用提供方和用户迫切需要一种新的服务提供方式,使应用开发更简单、服务(如听音乐、打车等)的获取和
- 190.HarmonyOS NEXT系列教程之图案锁振动反馈功能实现
harmonyos-next
温馨提示:本篇博客的详细代码已发布到git:https://gitcode.com/nutpi/HarmonyosNext可以下载运行哦!HarmonyOSNEXT系列教程之图案锁振动反馈功能实现效果预览1.振动功能概述1.1功能定义//振动功能实现startVibrator(vibratorCount?:number){try{vibrator.startVibration({type:'pre
- 费控系统是做什么的
费控系统
费控系统主要用于费用监控**、成本控制、风险预警。其中费用监控通过实时采集和精细数据分析,帮助企业实时掌握资金流向和支出情况,从而确保预算执行与资金使用的准确性。企业借助该系统可以提前预警异常支出、降低运营风险,并借助数据反馈不断优化管理策略,从而提升整体财务透明度和管理效率。一、费控系统的概念与基本功能费控系统是企业在财务管理中的重要工具,主要用于对企业各项费用进行实时监控和管理。它通过对各部门
- 蓝桥杯算法实战:技巧、策略与进阶之路
竣雄
蓝桥杯算法职场和发展
摘要蓝桥杯作为国内颇具影响力的程序设计竞赛,对提升大学生算法思维与编程能力意义重大。本文深入剖析蓝桥杯算法竞赛,结合历年真题总结核心考点与典型题型,分享实用解题技巧与备考策略,并探讨算法优化与进阶方向。通过系统学习与实践,助力参赛者提升算法水平,在竞赛中取得优异成绩。关键词蓝桥杯;算法竞赛;解题技巧;备考策略;算法优化一、引言蓝桥杯全国软件和信息技术专业人才大赛旨在选拔优秀的软件和信息技术人才,推
- 多元素Slots游戏数值设计与平衡:特色玩法的深度策略
小宝哥Code
游戏策划游戏microsoft网络
问题:如何深入研究针对特色游戏(如多元素组合类游戏,多重路线设计游戏)进行专业的数值设计与平衡,确保游戏体验与平台效益双赢?多元素Slots游戏数值设计与平衡:特色玩法的深度策略一、特色Slots游戏的市场定位与设计理念在当今竞争激烈的Slots游戏市场中,传统单一玩法已难以满足玩家日益增长的复杂需求。作为资深Slots游戏策划,我深知特色玩法如多元素组合和多重路线设计已成为市场差异化的关键。1.
- 嵌入式系统开发如何选择和备考软考高级
矿渣渣
系统架构
针对已通过软考中级嵌入式系统设计师的开发者或者从事嵌入式系统设计的人员,以下是为您量身定制的高级科目推荐及备考方案:一、软考高级科目推荐1.系统架构设计师(首推)推荐理由:技术延续性:与嵌入式系统设计高度相关,涉及硬件/软件协同设计、实时系统架构、低功耗设计等核心领域。职业发展:适合向架构师或技术负责人转型,提升复杂系统设计能力。考试内容匹配:覆盖嵌入式场景(如物联网架构、边缘计算系统设计)。考试
- 单片机原理及应用
风亦辰739
单片机
单片机(Microcontroller,简称MCU)是集成度高、功能强大的微型计算机,广泛应用于嵌入式系统、智能家居、工业控制、汽车电子、物联网等领域。作为一种重要的硬件平台,单片机具有小巧、低功耗、高效、成本低等特点。本文将介绍单片机的基本原理、结构特点以及其在实际应用中的使用方法。一、单片机的基本原理单片机是由中央处理单元(CPU)、存储器(RAM、ROM)、输入输出接口、定时器、串行通信接口
- 从阅读空间到知识孵化器,AI时代智慧图书馆何为?
技能咖
生成式人工智能认证GAI认证人工智能
在人工智能(AI)浪潮席卷全球的当下,图书馆作为知识传播与文化传承的重要场所,正面临着前所未有的变革。从传统的阅读空间到如今的知识孵化器,智慧图书馆在AI时代肩负着新的使命与挑战。本文将探讨智慧图书馆在AI时代的发展方向,并引入生成式人工智能认证(GAI)认证,为图书馆从业者的技能提升提供新思路。AI时代智慧图书馆的新角色知识资源整合与挖掘者在AI时代,信息爆炸式增长,图书馆不再仅仅是纸质书籍的收
- 鸿蒙harmonyOS:笔记 正则表达式
一只小风华~
笔记前端华为harmonyos正则表达式
从给出的文本中,按照既定的相关规则,匹配出符合的数据,其中的规则就是正则表达式,使用正则表达式,可以使得我们用简洁的代码就能实现一定复杂的逻辑,比如判断一个邮箱账号是否符合正常的邮箱账号,再比如判断一个手机号是否正常的手机号,等等,正因为有了正则,得以让文本处理起来更加的简单。日常开发中主要用来做三件事:匹配、替换、提取。手机号表单要求用户只能输入11位的数字(匹配)过滤掉页面内容中的一些敏感词(
- 蓝桥杯备赛(7):ST表
神里流~霜灭
蓝桥备赛蓝桥杯贪心算法c++c语言数据结构动态规划
RMQ问题RMQ问题是针对于数组,每次给一个区间[l,r],要求返回区间内的最大值或最小值(的下标),也就是说,RMQ问题就是求区间最值的问题。对于RMQ问题,容易想到一种O(n)的方法,就是用i直接遍历[l,r]区间,不断比较a[i]与max的大小关系,然后不断更新max,最后得出的就是最大值。但是,我们可以利用倍增和动态规划的思想,利用“ST表”这个数据结构来帮助解决。ST表ST表是一种可以“
- Goroutine 与 Channel
九班长
Golang算法数据库网络golangGoroutineChannel
Goroutine和Channel是Go语言并发编程的核心概念。理解它们的原理和使用方法,对于编写高效、安全的并发程序至关重要。以下是对Goroutine和Channel的深入解析,包括它们的原理、使用场景、常见问题及最佳实践。1.Goroutine1.1什么是Goroutine?Goroutine是Go语言中的轻量级线程,由Go运行时(runtime)管理。与操作系统线程相比,Goroutine
- FFmpeg 命令行全解析:高效音视频处理从入门到精通
码流怪侠
ffmpeg音视频ffplayffprobe实时音视频视频编解码直播转码
FFmpegFFmpeg是一款开源的多媒体处理工具集,支持音视频编解码、格式转换、流媒体处理等全链路操作。核心功能与工具:多媒体全链路支持支持1000+音视频编解码格式(如H.264、HEVC、AV1)和协议(RTMP、RTSP、HLS),覆盖录制、转码、流化等全流程。提供三大核心工具:ffmpeg:转码与流处理(如ffmpeg-iinput.mp4output.avi)。ffplay:媒体播放(
- 单例模式中的饿汉和懒汉模式
筑梦小子
单例模式javac++
目录一.什么是单例模式一.饿汉模式1.饿汉模式的概念2.饿汉模式代码2.多线程是否线程安全二.懒汉模式1.懒汉模式的概念2.单线程情况下的懒汉模式2.多线程情况下的懒汉模式(1)导致懒汉模式在多线程情况下的不安全原因(2)解决方法代码示例版本1版本2版本2的解释说明一.什么是单例模式保证某个类在程序中只存在一份实例,而不会创建多个实例,这样就会提高效率。在单利模式中一般只提供一个getInstan
- 基于ssm的药房管理系统
AI天才研究院
计算AI大模型企业级应用开发实战ChatGPT计算科学神经计算深度学习神经网络大数据人工智能大型语言模型AIAGILLMJavaPython架构设计AgentRPA
基于ssm的药房管理系统作者:禅与计算机程序设计艺术1.背景介绍1.1药房管理系统的重要性在现代医疗体系中,药房管理系统扮演着至关重要的角色。高效、准确、安全的药品管理不仅关系到患者的健康,更是医院运营的重要一环。传统的人工管理模式已经难以满足日益增长的医疗需求,因此,开发一套功能完善、易于操作的药房管理系统势在必行。1.2SSM框架的优势SSM(Spring、SpringMVC、MyBatis)
- Maven
Array_06
eclipsejdkmaven
Maven
Maven是基于项目对象模型(POM), 信息来管理项目的构建,报告和文档的软件项目管理工具。
Maven 除了以程序构建能力为特色之外,还提供高级项目管理工具。由于 Maven 的缺省构建规则有较高的可重用性,所以常常用两三行 Maven 构建脚本就可以构建简单的项目。由于 Maven 的面向项目的方法,许多 Apache Jakarta 项目发文时使用 Maven,而且公司
- ibatis的queyrForList和queryForMap区别
bijian1013
javaibatis
一.说明
iBatis的返回值参数类型也有种:resultMap与resultClass,这两种类型的选择可以用两句话说明之:
1.当结果集列名和类的属性名完全相对应的时候,则可直接用resultClass直接指定查询结果类
- LeetCode[位运算] - #191 计算汉明权重
Cwind
java位运算LeetCodeAlgorithm题解
原题链接:#191 Number of 1 Bits
要求:
写一个函数,以一个无符号整数为参数,返回其汉明权重。例如,‘11’的二进制表示为'00000000000000000000000000001011', 故函数应当返回3。
汉明权重:指一个字符串中非零字符的个数;对于二进制串,即其中‘1’的个数。
难度:简单
分析:
将十进制参数转换为二进制,然后计算其中1的个数即可。
“
- 浅谈java类与对象
15700786134
java
java是一门面向对象的编程语言,类与对象是其最基本的概念。所谓对象,就是一个个具体的物体,一个人,一台电脑,都是对象。而类,就是对象的一种抽象,是多个对象具有的共性的一种集合,其中包含了属性与方法,就是属于该类的对象所具有的共性。当一个类创建了对象,这个对象就拥有了该类全部的属性,方法。相比于结构化的编程思路,面向对象更适用于人的思维
- linux下双网卡同一个IP
被触发
linux
转自:
http://q2482696735.blog.163.com/blog/static/250606077201569029441/
由于需要一台机器有两个网卡,开始时设置在同一个网段的IP,发现数据总是从一个网卡发出,而另一个网卡上没有数据流动。网上找了下,发现相同的问题不少:
一、
关于双网卡设置同一网段IP然后连接交换机的时候出现的奇怪现象。当时没有怎么思考、以为是生成树
- 安卓按主页键隐藏程序之后无法再次打开
肆无忌惮_
安卓
遇到一个奇怪的问题,当SplashActivity跳转到MainActivity之后,按主页键,再去打开程序,程序没法再打开(闪一下),结束任务再开也是这样,只能卸载了再重装。而且每次在Log里都打印了这句话"进入主程序"。后来发现是必须跳转之后再finish掉SplashActivity
本来代码:
// 销毁这个Activity
fin
- 通过cookie保存并读取用户登录信息实例
知了ing
JavaScripthtml
通过cookie的getCookies()方法可获取所有cookie对象的集合;通过getName()方法可以获取指定的名称的cookie;通过getValue()方法获取到cookie对象的值。另外,将一个cookie对象发送到客户端,使用response对象的addCookie()方法。
下面通过cookie保存并读取用户登录信息的例子加深一下理解。
(1)创建index.jsp文件。在改
- JAVA 对象池
矮蛋蛋
javaObjectPool
原文地址:
http://www.blogjava.net/baoyaer/articles/218460.html
Jakarta对象池
☆为什么使用对象池
恰当地使用对象池化技术,可以有效地减少对象生成和初始化时的消耗,提高系统的运行效率。Jakarta Commons Pool组件提供了一整套用于实现对象池化
- ArrayList根据条件+for循环批量删除的方法
alleni123
java
场景如下:
ArrayList<Obj> list
Obj-> createTime, sid.
现在要根据obj的createTime来进行定期清理。(释放内存)
-------------------------
首先想到的方法就是
for(Obj o:list){
if(o.createTime-currentT>xxx){
- 阿里巴巴“耕地宝”大战各种宝
百合不是茶
平台战略
“耕地保”平台是阿里巴巴和安徽农民共同推出的一个 “首个互联网定制私人农场”,“耕地宝”由阿里巴巴投入一亿 ,主要是用来进行农业方面,将农民手中的散地集中起来 不仅加大农民集体在土地上面的话语权,还增加了土地的流通与 利用率,提高了土地的产量,有利于大规模的产业化的高科技农业的 发展,阿里在农业上的探索将会引起新一轮的产业调整,但是集体化之后农民的个体的话语权 将更少,国家应出台相应的法律法规保护
- Spring注入有继承关系的类(1)
bijian1013
javaspring
一个类一个类的注入
1.AClass类
package com.bijian.spring.test2;
public class AClass {
String a;
String b;
public String getA() {
return a;
}
public void setA(Strin
- 30岁转型期你能否成为成功人士
bijian1013
成功
很多人由于年轻时走了弯路,到了30岁一事无成,这样的例子大有人在。但同样也有一些人,整个职业生涯都发展得很优秀,到了30岁已经成为职场的精英阶层。由于做猎头的原因,我们接触很多30岁左右的经理人,发现他们在职业发展道路上往往有很多致命的问题。在30岁之前,他们的职业生涯表现很优秀,但从30岁到40岁这一段,很多人
- [Velocity三]基于Servlet+Velocity的web应用
bit1129
velocity
什么是VelocityViewServlet
使用org.apache.velocity.tools.view.VelocityViewServlet可以将Velocity集成到基于Servlet的web应用中,以Servlet+Velocity的方式实现web应用
Servlet + Velocity的一般步骤
1.自定义Servlet,实现VelocityViewServl
- 【Kafka十二】关于Kafka是一个Commit Log Service
bit1129
service
Kafka is a distributed, partitioned, replicated commit log service.这里的commit log如何理解?
A message is considered "committed" when all in sync replicas for that partition have applied i
- NGINX + LUA实现复杂的控制
ronin47
lua nginx 控制
安装lua_nginx_module 模块
lua_nginx_module 可以一步步的安装,也可以直接用淘宝的OpenResty
Centos和debian的安装就简单了。。
这里说下freebsd的安装:
fetch http://www.lua.org/ftp/lua-5.1.4.tar.gz
tar zxvf lua-5.1.4.tar.gz
cd lua-5.1.4
ma
- java-14.输入一个已经按升序排序过的数组和一个数字, 在数组中查找两个数,使得它们的和正好是输入的那个数字
bylijinnan
java
public class TwoElementEqualSum {
/**
* 第 14 题:
题目:输入一个已经按升序排序过的数组和一个数字,
在数组中查找两个数,使得它们的和正好是输入的那个数字。
要求时间复杂度是 O(n) 。如果有多对数字的和等于输入的数字,输出任意一对即可。
例如输入数组 1 、 2 、 4 、 7 、 11 、 15 和数字 15 。由于
- Netty源码学习-HttpChunkAggregator-HttpRequestEncoder-HttpResponseDecoder
bylijinnan
javanetty
今天看Netty如何实现一个Http Server
org.jboss.netty.example.http.file.HttpStaticFileServerPipelineFactory:
pipeline.addLast("decoder", new HttpRequestDecoder());
pipeline.addLast(&quo
- java敏感词过虑-基于多叉树原理
cngolon
违禁词过虑替换违禁词敏感词过虑多叉树
基于多叉树的敏感词、关键词过滤的工具包,用于java中的敏感词过滤
1、工具包自带敏感词词库,第一次调用时读入词库,故第一次调用时间可能较长,在类加载后普通pc机上html过滤5000字在80毫秒左右,纯文本35毫秒左右。
2、如需自定义词库,将jar包考入WEB-INF工程的lib目录,在WEB-INF/classes目录下建一个
utf-8的words.dict文本文件,
- 多线程知识
cuishikuan
多线程
T1,T2,T3三个线程工作顺序,按照T1,T2,T3依次进行
public class T1 implements Runnable{
@Override
- spring整合activemq
dalan_123
java spring jms
整合spring和activemq需要搞清楚如下的东东1、ConnectionFactory分: a、spring管理连接到activemq服务器的管理ConnectionFactory也即是所谓产生到jms服务器的链接 b、真正产生到JMS服务器链接的ConnectionFactory还得
- MySQL时间字段究竟使用INT还是DateTime?
dcj3sjt126com
mysql
环境:Windows XPPHP Version 5.2.9MySQL Server 5.1
第一步、创建一个表date_test(非定长、int时间)
CREATE TABLE `test`.`date_test` (`id` INT NOT NULL AUTO_INCREMENT ,`start_time` INT NOT NULL ,`some_content`
- Parcel: unable to marshal value
dcj3sjt126com
marshal
在两个activity直接传递List<xxInfo>时,出现Parcel: unable to marshal value异常。 在MainActivity页面(MainActivity页面向NextActivity页面传递一个List<xxInfo>): Intent intent = new Intent(this, Next
- linux进程的查看上(ps)
eksliang
linux pslinux ps -llinux ps aux
ps:将某个时间点的进程运行情况选取下来
转载请出自出处:http://eksliang.iteye.com/admin/blogs/2119469
http://eksliang.iteye.com
ps 这个命令的man page 不是很好查阅,因为很多不同的Unix都使用这儿ps来查阅进程的状态,为了要符合不同版本的需求,所以这个
- 为什么第三方应用能早于System的app启动
gqdy365
System
Android应用的启动顺序网上有一大堆资料可以查阅了,这里就不细述了,这里不阐述ROM启动还有bootloader,软件启动的大致流程应该是启动kernel -> 运行servicemanager 把一些native的服务用命令启动起来(包括wifi, power, rild, surfaceflinger, mediaserver等等)-> 启动Dalivk中的第一个进程Zygot
- App Framework发送JSONP请求(3)
hw1287789687
jsonp跨域请求发送jsonpajax请求越狱请求
App Framework 中如何发送JSONP请求呢?
使用jsonp,详情请参考:http://json-p.org/
如何发送Ajax请求呢?
(1)登录
/***
* 会员登录
* @param username
* @param password
*/
var user_login=function(username,password){
// aler
- 发福利,整理了一份关于“资源汇总”的汇总
justjavac
资源
觉得有用的话,可以去github关注:https://github.com/justjavac/awesome-awesomeness-zh_CN 通用
free-programming-books-zh_CN 免费的计算机编程类中文书籍
精彩博客集合 hacke2/hacke2.github.io#2
ResumeSample 程序员简历
- 用 Java 技术创建 RESTful Web 服务
macroli
java编程WebREST
转载:http://www.ibm.com/developerworks/cn/web/wa-jaxrs/
JAX-RS (JSR-311) 【 Java API for RESTful Web Services 】是一种 Java™ API,可使 Java Restful 服务的开发变得迅速而轻松。这个 API 提供了一种基于注释的模型来描述分布式资源。注释被用来提供资源的位
- CentOS6.5-x86_64位下oracle11g的安装详细步骤及注意事项
超声波
oraclelinux
前言:
这两天项目要上线了,由我负责往服务器部署整个项目,因此首先要往服务器安装oracle,服务器本身是CentOS6.5的64位系统,安装的数据库版本是11g,在整个的安装过程中碰到很多的坑,不过最后还是通过各种途径解决并成功装上了。转别写篇博客来记录完整的安装过程以及在整个过程中的注意事项。希望对以后那些刚刚接触的菜鸟们能起到一定的帮助作用。
安装过程中可能遇到的问题(注
- HttpClient 4.3 设置keeplive 和 timeout 的方法
supben
httpclient
ConnectionKeepAliveStrategy kaStrategy = new DefaultConnectionKeepAliveStrategy() {
@Override
public long getKeepAliveDuration(HttpResponse response, HttpContext context) {
long keepAlive
- Spring 4.2新特性-@Import注解的升级
wiselyman
spring 4
3.1 @Import
@Import注解在4.2之前只支持导入配置类
在4.2,@Import注解支持导入普通的java类,并将其声明成一个bean
3.2 示例
演示java类
package com.wisely.spring4_2.imp;
public class DemoService {
public void doSomethin