安装部署K8S集群及Dashboard
转载请表明出处 https://blog.csdn.net/Amor_Leo/article/details/108466765 谢谢
安装部署K8S集群及Dashboard
- 环境
- 部署
-
- 网络及其他配置
- 安装
- 部署Kubernetes Master
- 部署Kubernetes Node
- 安裝Dashboard
环境
3台CentOS7(7.6以上)的虚拟机分别为:
192.168.0.229
192.168.0.237
192.168.0.191
搭建K8S的一个主节点两个Node节点
都是桥接模式 并且为静态ip
4G内存4内核
部署
网络及其他配置
- 检查
在 master 节点和 worker 节点都要执行
cat /etc/redhat-release
此处 hostname 的输出将会是该机器在 Kubernetes 集群中的节点名字
hostname
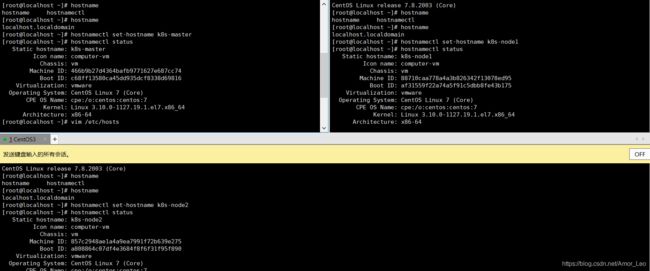
- 修改hostname
如果hostname一样则需要修改
# 修改 hostname
hostnamectl set-hostname your-new-host-name
# 查看修改结果
hostnamectl status
# 设置 hostname 解析
echo "127.0.0.1 $(hostname)" >> /etc/hosts
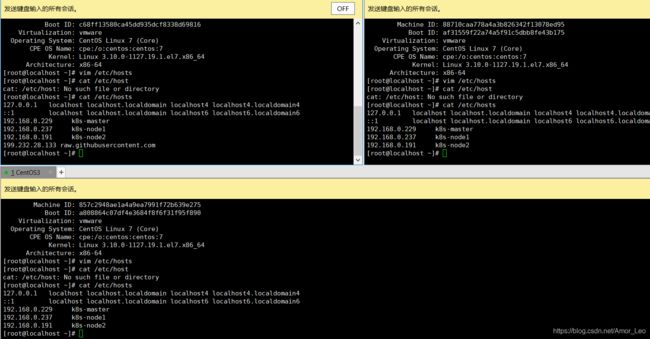
- 添加主机与ip的对应关系
vim /etc/hosts
192.168.0.229 k8s-master
192.168.0.237 k8s-node1
192.168.0.191 k8s-node2
- 关闭selinux
setenforce 0 # 临时关闭
sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/config # 永久关闭
- 关闭swap
swapoff -a # 临时关闭;关闭swap主要是为了性能考虑
sed -ri 's/.*swap.*/#&/' /etc/fstab # 永久关闭
free -g # 可以通过这个命令查看swap是否关闭了
- 防火墙
- 方案一: 关闭防火墙
systemctl stop firewalld
systemctl disable firewalld
- 方案二: 不关闭防火墙,开启端口(生产环境建议使用)
k8s master需要开启以下端口
firewall-cmd --permanent --add-port=6443/tcp
firewall-cmd --permanent --add-port=8080/tcp
firewall-cmd --permanent --add-port=2379-2380/tcp
firewall-cmd --permanent --add-port=10250/tcp
firewall-cmd --permanent --add-port=10251/tcp
firewall-cmd --permanent --add-port=10252/tcp
firewall-cmd --permanent --add-port=10255/tcp
firewall-cmd --permanent --add-port=8472/udp
firewall-cmd --permanent --add-port=443/udp
firewall-cmd --permanent --add-port=53/udp
firewall-cmd --permanent --add-port=53/tcp
firewall-cmd --permanent --add-port=9153/tcp
firewall-cmd --permanent --add-port=30000-32767/tcp
firewall-cmd --add-masquerade --permanent
systemctl restart firewalld
k8s node需要开启以下端口
firewall-cmd --permanent --add-port=8080/tcp
firewall-cmd --permanent --add-port=10250/tcp
firewall-cmd --permanent --add-port=10255/tcp
firewall-cmd --permanent --add-port=8472/udp
firewall-cmd --permanent --add-port=443/udp
firewall-cmd --permanent --add-port=53/udp
firewall-cmd --permanent --add-port=53/tcp
firewall-cmd --permanent --add-port=9153/tcp
firewall-cmd --permanent --add-port=30000-32767/tcp
firewall-cmd --add-masquerade --permanent
systemctl restart firewalld
注意:
8472/udp为flannel的通信端口
443/tcp 为Kubernetes server端口
注意一点:一定要执行以下命令打开NAT,默认是关闭状态
# 打开NAT
firewall-cmd --add-masquerade --permanent
# 检查是否允许NAT转发
firewall-cmd --query-masquerade
# 关闭NAT转发
# firewall-cmd --remove-masquerade
如果你使用了istio还有把istio-pilot的端口加到防火墙里:
firewall-cmd --permanent --add-port=15010-15014/tcp
否则会出现以下报错:
Envoy proxy is NOT ready
- 网络桥接设置
echo 'net.bridge.bridge-nf-call-iptables = 1'>>/etc/sysctl.conf
echo 'net.bridge.bridge-nf-call-ip6tables = 1'>>/etc/sysctl.conf
echo 'net.ipv4.ip_forward = 1'>>/etc/sysctl.conf
sysctl -p
安装
- 安装docker
之前的文章docker安装
更改docker的启动参数
vim /usr/lib/systemd/system/docker.service
#ExecStart=/usr/bin/dockerd
ExecStart=/usr/bin/dockerd --exec-opt native.cgroupdriver=systemd
# 重启docker
systemctl daemon-reload
systemctl restart docker
- 设置k8s的yum源
cat > /etc/yum.repos.d/kubernetes.repo << EOF
[k8s]
name=k8s
enabled=1
gpgcheck=0
baseurl=https://mirrors.aliyun.com/kubernetes/yum/repos/kubernetes-el7-x86_64/
EOF
- 安装kubeadm,kubelet和kubectl
yum install -y kubelet-<version> kubectl-<version> kubeadm-<version>
yum install kubelet kubeadm kubectl -y
- 启动kubelet,设置开机自启动
systemctl enable kubelet
部署Kubernetes Master
- 查看版本信息
rpm -qi kubeadm
- 初始化
kubeadm init --apiserver-advertise-address=192.168.0.229 --image-repository registry.aliyuncs.com/google_containers --kubernetes-version v1.19.0 --service-cidr=10.10.0.0/16 --pod-network-cidr=10.244.0.0/16
# –image-repository string: 这个用于指定从什么位置来拉取镜像(1.13版本才有的),默认值是k8s.gcr.io,我们将其指定为国内镜像地址:registry.aliyuncs.com/google_containers
# –kubernetes-version string: 指定kubenets版本号,默认值是stable-1,会导致从https://dl.k8s.io/release/stable-1.txt下载最新的版本号,我们可以将其指定为固定版本(v1.15.1)来跳过网络请求。
# –apiserver-advertise-address 指明用 Master 的哪个 interface 与 Cluster 的其他节点通信。如果 Master 有多个 interface,建议明确指定,如果不指定,kubeadm 会自动选择有默认网关的 interface。
# –pod-network-cidr 指定 Pod 网络的范围。Kubernetes 支持多种网络方案,而且不同网络方案对 –pod-network-cidr有自己的要求,这里设置为10.244.0.0/16 是因为我们将使用 flannel 网络方案,必须设置成这个 CIDR。
#
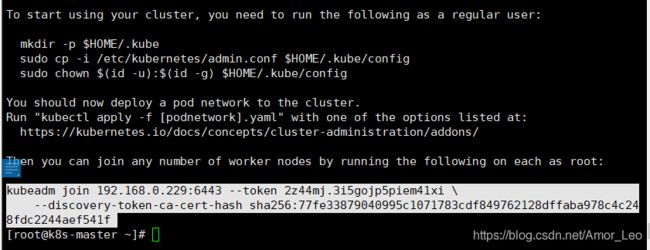
- 其它node节点执行,如果重置了,就不一样了,得根据上面执行情况(node)
kubeadm join 192.168.0.229:6443 --token 2z44mj.3i5gojp5piem41xi \
--discovery-token-ca-cert-hash sha256:77fe33879040995c1071783cdf849762128dffaba978c4c248fdc2244aef541f
如果需要重置:
docker rm -f `docker ps -a -q`
rm -rf /etc/kubernetes/*
rm -rf /var/lib/etcd/
kubeadm reset
查看docker镜像
docker images
- 使用kubectl工具
复制如下命令直接执行
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
下面就可以直接使用kubectl命令了
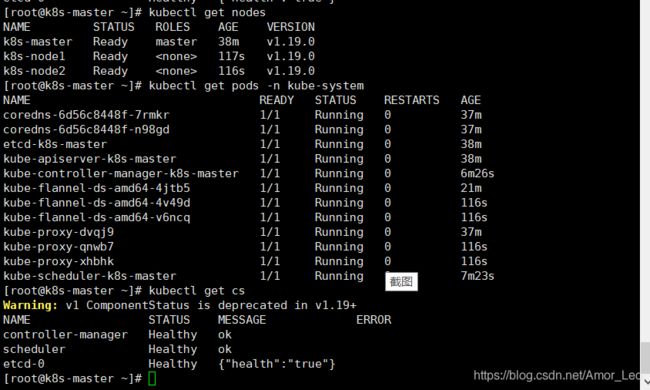
kubectl get nodes
kubectl get po -o wide -n kube-system
kubectl get pods --all-namespaces
- 安装Pod网络插件(CNI)
kubectl apply -f https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml
或者:
kubectl apply -f kube-flannel.yml
报错:The connection to the server raw.githubusercontent.com was refused - did you specify the right host or port?
原因:外网不可访问
解决办法:
# 在https://www.ipaddress.com/查询raw.githubusercontent.com的真实IP。
sudo vim /etc/hosts
199.232.28.133 raw.githubusercontent.com
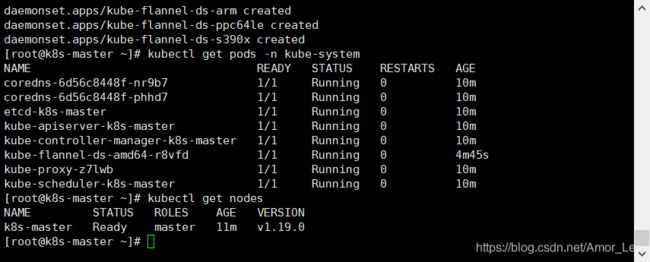
- 查看是否部署成功
kubectl get pods -n kube-system
- 再次查看node,可以看到状态为ready
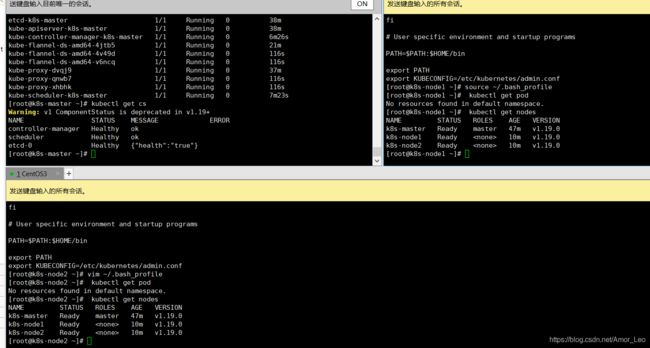
kubectl get nodes
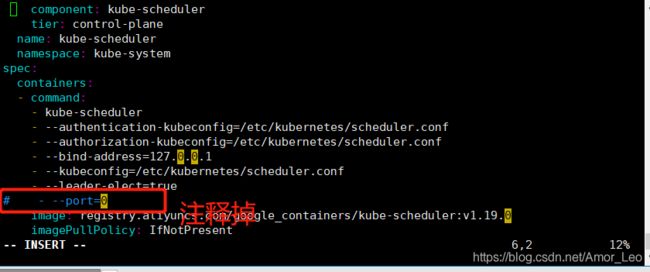
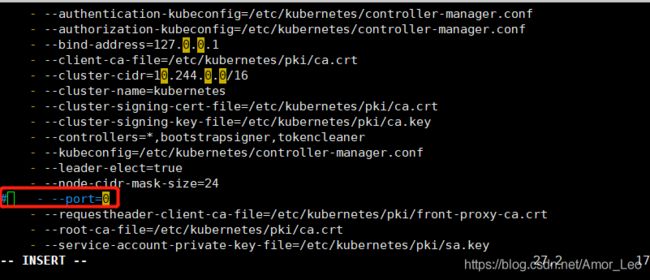
- 查看kube-scheduler和kube-controller-manager组件配置是否禁用了非安全端口
(如果子节点加入集群后 在master 输入命令kubectl get cs查看组件状态kube-scheduler和kube-controller-manager显示unhealthy则修改以下配置)
配置文件路径:
/etc/kubernetes/manifests/scheduler.conf
/etc/kubernetes/manifests/controller-manager.conf
两个配置文件去掉–port=0这个设置,然后重启sudo systemctl restart kubelet
vim /etc/kubernetes/manifests/kube-scheduler.yaml
vim /etc/kubernetes/manifests/kube-controller-manager.yaml
sudo systemctl restart kubelet
部署Kubernetes Node
- 在node上安装flannel
docker pull lizhenliang/flannel:v0.11.0-amd64
- 向集群上增加新节点
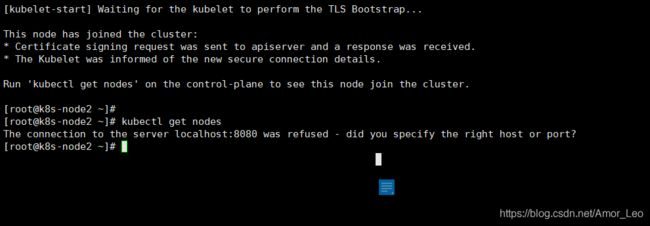
执行在kubeadm init输出的kubeadm join命令:
这里的–token 来自前面kubeadm init输出提示,如果当时没有记录下来可以通过kubeadm token list 查看。
kubeadm join 192.168.0.229:6443 --token 2z44mj.3i5gojp5piem41xi \
--discovery-token-ca-cert-hash sha256:77fe33879040995c1071783cdf849762128dffaba978c4c248fdc2244aef541f
如果join的token之前没有记住,没关系,在master重新生成一下
kubeadm token create --print-join-command
- 在master端查看:
kubectl get nodes
kubectl get pods -n kube-system
kubectl get cs
先在主节点master上的/etc/kubernetes/admin.conf文件拷贝到从节点相同目录下,然后配置环境变量

echo "export KUBECONFIG=/etc/kubernetes/admin.conf" >> ~/.bash_profile
source ~/.bash_profile
- 检验
kubectl get nodes
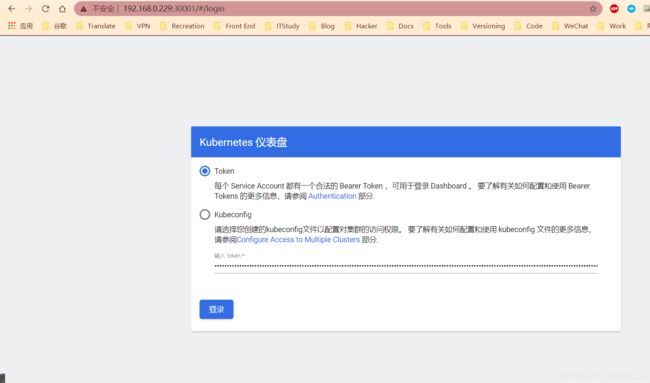
安裝Dashboard
Dashboard GitHub
- 下载yaml
yum install -y wget
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.4/aio/deploy/recommended.yaml
- 下载镜像
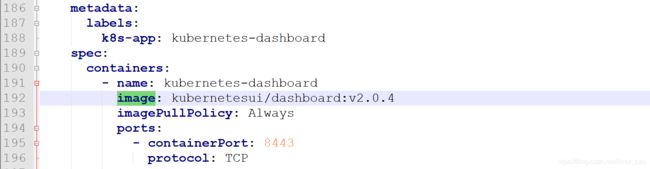
docker pull kubernetesui/dashboard:v2.0.4
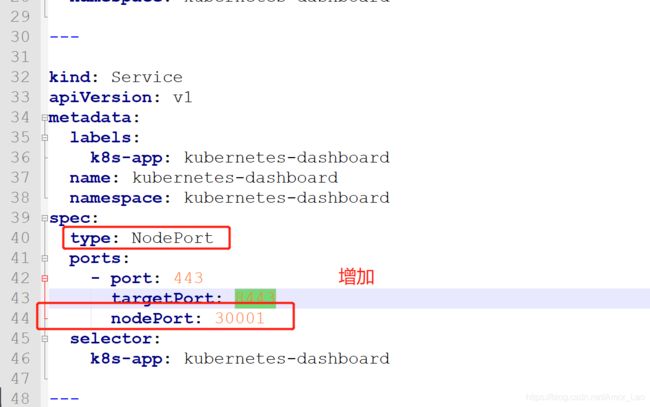
- 修改配置文件
vim recommended.yaml
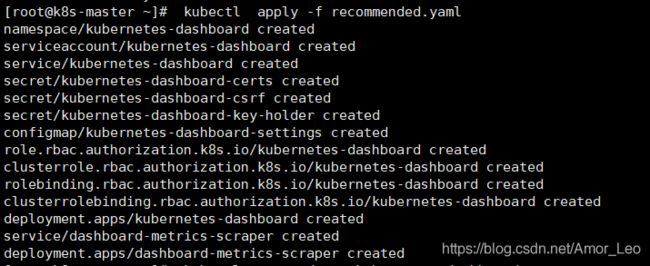
- 安装
kubectl apply -f recommended.yaml
- 如果之前安过,可以卸载重装
kubectl delete -f recommended.yaml
- 查看节点是否启动
kubectl get pods --all-namespaces
- 生成token
kubectl -n kube-system describe $(kubectl -n kube-system get secret -n kube-system -o name | grep namespace) | grep token
- 查看
kubectl get pods -n kubernetes-dashboard
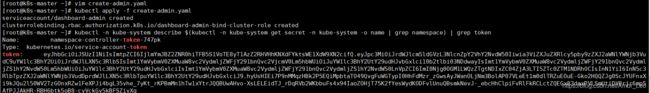
vim create-admin.yaml
create-admin.yaml
##################增加一个dashbboard的管理账户#########################
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: dashboard-admin
namespace: kubernetes-dashboard
---
##################给dashbboard的管理账户分配权限#####################
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: dashboard-admin-bind-cluster-role
labels:
k8s-app: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kubernetes-dashboard
- 生成用户
kubectl apply -f create-admin.yaml
- 生成token
kubectl -n kube-system describe $(kubectl -n kube-system get secret -n kube-system -o name | grep namespace) | grep token
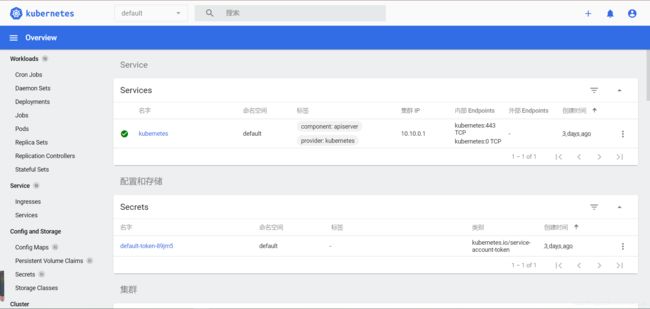
- 访问页面