0019-TIPS-2019-tokyowesterns-gnote : switch(jump-table) && Doubule Fetch
漏洞源码
#include 漏洞分析
没有开启smap保护
首先看启动脚本和/proc/cpuinfo,没有看起smap保护
#!/bin/sh
cd /home/gnote
stty intr ^]
exec \
timeout 120 \
qemu-system-x86_64 \
-m 64M \
-kernel bzImage \
-initrd rootfs.cpio -append "loglevel=3 console=ttyS0 oops=panic panic=1 kaslr" \
-nographic \
-net user -net nic \
-device e1000 -smp cores=2,threads=2 \
-cpu kvm64,+smep \
-monitor /dev/null 2>/dev/null
/ $ cat /proc/cpuinfo | grep "smep"
flags : fpu de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ht syscall nx lm cop
flags : fpu de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ht syscall nx lm cop
flags : fpu de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ht syscall nx lm cop
flags : fpu de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ht syscall nx lm cop
/ $ cat /proc/cpuinfo | grep "smap"
/ $
漏洞分析
先看gnote_write的源码
ssize_t gnote_write(struct file *filp, const char __user *buf, size_t count, loff_t *f_pos)
{
[...]
switch(*(unsigned int *)buf){
[...]
notes[cnt].size = *((unsigned int *)buf+1);
[...]
index = *((unsigned int *)buf+1);
}
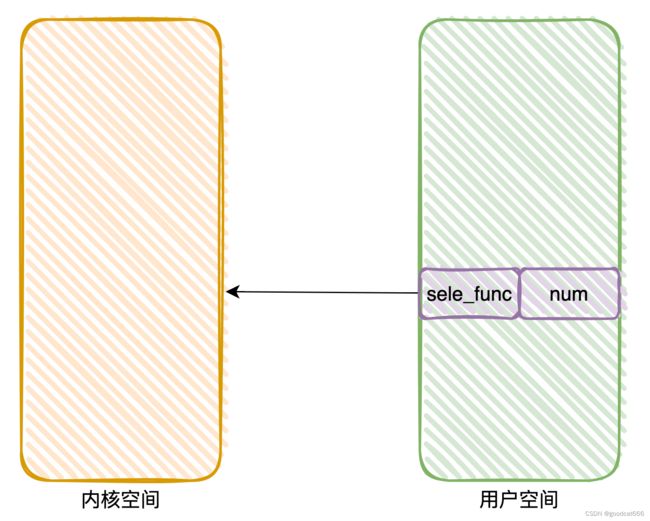
在调用gnote_write时,buf指针指向的结构体类似于
struct write_struct{
unsigned int sele_func;
unsigned int num;
}
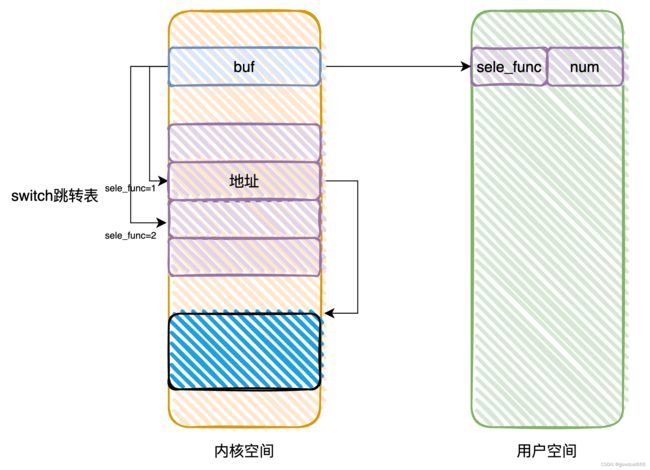
再看gnote_write的switch跳转表(首先需要知道syscall时,参数1~参数6是保存在 rdi,rsi,rdx,r10,r8,r9),rsi保存的是buf的地址
.text:0000000000000000 public gnote_write
.text:0000000000000000 gnote_write proc near ; DATA XREF: .data:00000000000002D8↓o
.text:0000000000000000 push rbp
.text:0000000000000001 mov rdi, offset lock
.text:0000000000000008 mov rbp, rsp
.text:000000000000000B push r12
.text:000000000000000D push rbx
.text:000000000000000E mov rbx, rsi <<<<<<<<<<<<<<<<<<<<<<<<<<<
.text:0000000000000011 mov r12, rdx
.text:0000000000000014 call mutex_lock
.text:0000000000000019 cmp dword ptr [rbx], 5 <<<<<<<<<<<<<<<<<<<<<<<<<<<
.text:000000000000001C ja short loc_6E
.text:000000000000001E mov eax, [rbx] <<<<<<<<<<<<<<<<<<<<<<<<<<< 获取switch跳转索引
.text:0000000000000020 mov rax, ds:off_220[rax*8]<<<<<<<<<<<<<<<<<<<<<<<<<<< 跳转表中case代码块地址
.text:0000000000000028 jmp __x86_indirect_thunk_rax
.rodata:0000000000000220 off_220 dq offset loc_6E ; DATA XREF: gnote_write+20↑r
.rodata:0000000000000228 dq offset loc_2D
.rodata:0000000000000230 dq offset sub_A5
.rodata:0000000000000238 dq offset sub_97
.rodata:0000000000000240 dq offset sub_B3
.rodata:0000000000000248 dq offset sub_82
.rodata:0000000000000248 _rodata ends
简化为
[0] .text:000000000000000E mov rbx, rsi <<<<<<<<<<<<
[1] .text:0000000000000019 cmp dword ptr [rbx], 5 <<<<<<<<<<<<
.text:000000000000001C ja short loc_6E
[2] .text:000000000000001E mov eax, [rbx] <<<<<<<<<<<< 获取switch跳转索引
[3] .text:0000000000000020 mov rax, ds:off_220[rax*8] <<<<<<<<<<<< 跳转表中case代码块地址
[4] .text:0000000000000028 jmp __x86_indirect_thunk_rax
rsi为用户空间的地址buf,将用户空间buf的地址赋值给rbx
[1] 从用户空间获取内容sele_func,与5进行比较,检查sele_func的大小
[2] 再次从用户空间获取sele_func
[3] 从第二次获取的sele_func,获取跳转表中的地址
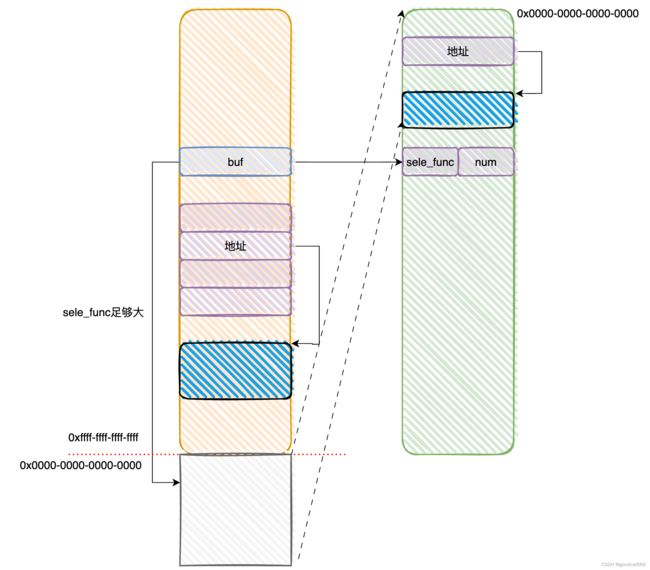
问题在于[1]、[2]都是从用户空间获取sele_func,这里有个问题,在[1]验证通过,在[2]执行之前,修改用户空间的sele_func,就有可能出现这样的问题
由于没有smap保护,再通过竞争sele_func,使得sele_func足够大,使得跳转表溢出到用户空间
漏洞利用
exp_kpti
//$ gcc -O3 -pthread -static -g -masm=intel ./exp.c -o exp
#include exp_modpath
//$ gcc -O3 -pthread -static -g -masm=intel ./exp.c -o exp
#include