kubernetes(4)
目录
flannel网络插件
calico网络插件
部署
网络策略
限制pod流量
限制namespace流量
同时限制namespace和pod
限制集群外部流量
k8s存储
configmap
字面值创建
通过文件创建
通过目录创建
通过yaml文件创建
使用configmap设置环境变量
使用conigmap设置命令行参数
通过数据卷使用configmap
configmap热更新
secrets
从文件创建
编写yaml文件
将Secret挂载到Volume中
向指定路径映射 secret 密钥
将Secret设置为环境变量
存储docker registry的认证信息
flannel网络插件
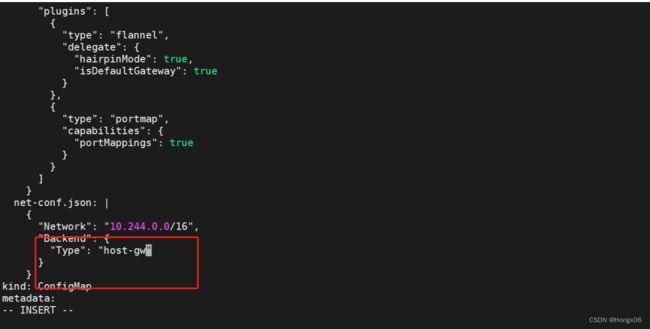
使用host-gw模式
[root@k8s2 ~]# kubectl -n kube-flannel edit cm kube-flannel-cfg
[root@k8s2 ~]# kubectl -n kube-flannel delete pod --all
calico网络插件
部署
删除flannel插件、删除所有节点上flannel配置文件,避免冲突
[root@k8s2 ~]# kubectl delete -f kube-flannel.yml
[root@k8s2 ~]# rm -f /etc/cni/net.d/10-flannel.conflist
[root@k8s3 ~]# rm -f /etc/cni/net.d/10-flannel.conflist
[root@k8s4 ~]# rm -f /etc/cni/net.d/10-flannel.conflist
下载部署文件、修改镜像路径、上传镜像
[root@k8s2 calico]# kubectl apply -f calico.yaml
重启所有集群节点,让pod重新分配IP
等待集群重启正常后测试网络
网络策略
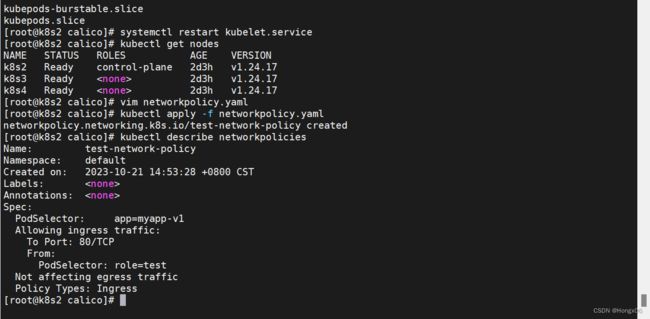
限制pod流量
[root@k8s2 calico]# vim networkpolicy.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
app: myapp-v1
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
role: test
ports:
- protocol: TCP
port: 80
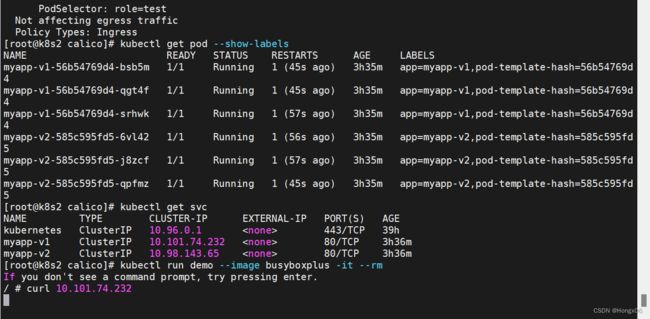
控制的对象是具有app=myapp-v1标签的pod
此时访问svc是不通的
给测试pod添加指定标签后,可以访问
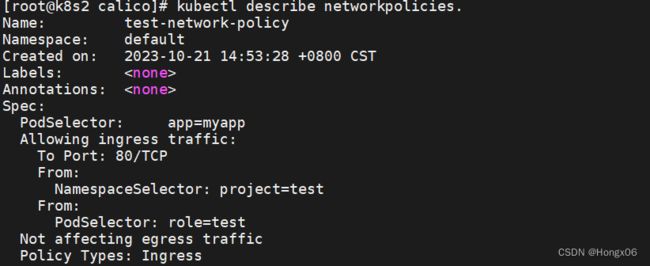
限制namespace流量
[root@k8s2 calico]# vim networkpolicy.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
app: myapp
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector:
matchLabels:
project: test
- podSelector:
matchLabels:
role: test
ports:
- protocol: TCP
port: 80
[root@k8s2 ~]# kubectl create namespace test
给namespace添加指定标签
[root@k8s2 calico]# kubectl label ns test project=test
同时限制namespace和pod
[root@k8s2 calico]# vim networkpolicy.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
app: myapp
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector:
matchLabels:
project: test
podSelector:
matchLabels:
role: test
ports:
- protocol: TCP
port: 80
给test命令空间中的pod添加指定标签后才能访问
[root@k8s2 calico]# kubectl -n test label pod demo role=test
限制集群外部流量
[root@k8s2 calico]# vim networkpolicy.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
app: myapp
policyTypes:
- Ingress
ingress:
- from:
- ipBlock:
cidr: 192.168.56.0/24
- namespaceSelector:
matchLabels:
project: myproject
podSelector:
matchLabels:
role: frontend
ports:
- protocol: TCP
port: 80
k8s存储
configmap
字面值创建
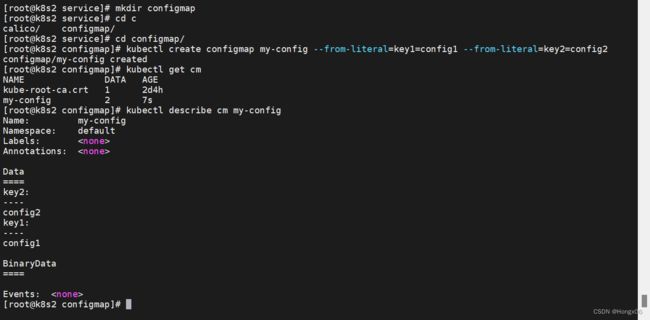
[root@k8s2 configmap]# kubectl create configmap my-config --from-literal=key1=config1 --from-literal=key2=config2
//ConfigMap 可以包含任意键值对,可以从文件、目录、命令行参数等来源创建
在上面的命令中,使用 kubectl 命令创建了名为 my-config 的 ConfigMap 对象,并设置了两个键值对。
[root@k8s2 configmap]# kubectl get cm
[root@k8s2 configmap]# kubectl describe cm my-config
通过文件创建
[root@k8s2 configmap]# kubectl create configmap my-config-2 --from-file=/etc/resolv.conf
通过目录创建
[root@k8s2 configmap]# mkdir test
[root@k8s2 configmap]# cp /etc/passwd test/
[root@k8s2 configmap]# cp /etc/fstab test/
[root@k8s2 configmap]# kubectl create configmap my-config-3 --from-file=test
通过yaml文件创建
[root@k8s2 configmap]# vim cm1.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: cm1-config
data:
db_host: "172.25.0.250"
db_port: "3306"
[root@k8s2 configmap]# kubectl apply -f cm1.yaml
使用configmap设置环境变量
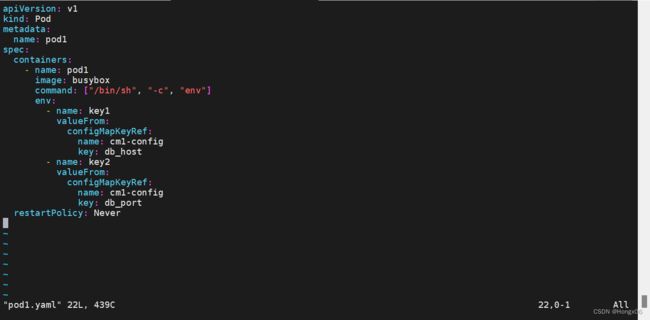
[root@k8s2 configmap]# vim pod1.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod1
spec:
containers:
- name: pod1
image: busybox
command: ["/bin/sh", "-c", "env"]
env:
- name: key1
valueFrom:
configMapKeyRef:
name: cm1-config
key: db_host
- name: key2
valueFrom:
configMapKeyRef:
name: cm1-config
key: db_port
restartPolicy: Never
[root@k8s2 configmap]# kubectl delete pod pod1
[root@k8s2 configmap]# vim pod2.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod2
spec:
containers:
- name: pod2
image: busybox
command: ["/bin/sh", "-c", "env"]
envFrom:
- configMapRef:
name: cm1-config
restartPolicy: Never
[root@k8s2 configmap]# kubectl apply -f pod2.yaml
使用conigmap设置命令行参数
[root@k8s2 configmap]# vim pod3.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod3
spec:
containers:
- name: pod3
image: busybox
command: ["/bin/sh", "-c", "echo $(db_host) $(db_port)"]
envFrom:
- configMapRef:
name: cm1-config
restartPolicy: Never
[root@k8s2 configmap]# kubectl apply -f pod3.yaml
通过数据卷使用configmap
[root@k8s2 configmap]# vim pod4.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod4
spec:
containers:
- name: pod4
image: busybox
command: ["/bin/sh", "-c", "cat /config/db_host"]
volumeMounts:
- name: config-volume
mountPath: /config
volumes:
- name: config-volume
configMap:
name: cm1-config
restartPolicy: Never
[root@k8s2 configmap]# kubectl apply -f pod4.yaml
configmap热更新
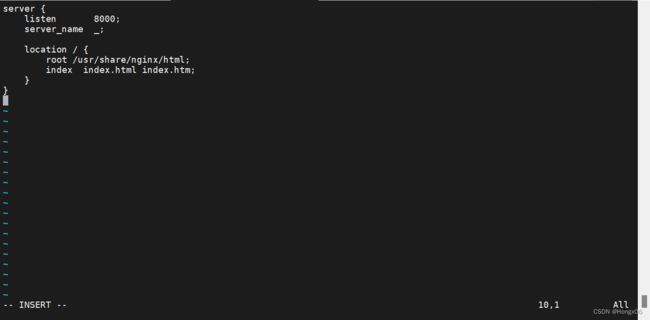
[root@k8s2 configmap]# vim nginx.conf
server {
listen 8000;
server_name _;
location / {
root /usr/share/nginx/html;
index index.html index.htm;
}
}
[root@k8s2 configmap]# kubectl create configmap nginxconf --from-file=nginx.conf
[root@k8s2 configmap]# vim my-nginx.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-nginx
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx
volumeMounts:
- name: config-volume
mountPath: /etc/nginx/conf.d
volumes:
- name: config-volume
configMap:
name: nginxconf
[root@k8s2 configmap]# kubectl apply -f my-nginx.yaml
[root@k8s2 configmap]# kubectl exec my-nginx-85fb986977-hp72w -- cat /etc/nginx/conf.d/nginx.conf
server {
listen 8000;
server_name _;
location / {
root /usr/share/nginx/html;
index index.html index.htm;
}
}
编辑cm,修改端口
[root@k8s2 configmap]# kubectl edit cm nginxconf
修改cm后,过上几秒配置信息会同步到容器,但是容器内运行的服务并不会加载生效,需要手动刷新
方式一:(推荐)
[root@k8s2 configmap]# kubectl delete pod my-nginx-85fb986977-hp72w
方式二:(手动触发版本更新,会新建一个replicaset)
[root@k8s2 configmap]# kubectl patch deployments.apps my-nginx --patch '{"spec": {"template": {"metadata": {"annotations": {"version/config": "20230312"}}}}}'
secrets
从文件创建
[root@k8s2 secret]# echo -n 'admin' > ./username.txt
[root@k8s2 secret]# echo -n 'westos' > ./password.txt
[root@k8s2 secret]# kubectl create secret generic db-user-pass --from-file=./username.txt --from-file=./password.txt
编写yaml文件
[root@k8s2 secret]# echo -n 'admin' | base64
YWRtaW4=
[root@k8s2 secret]# echo -n 'westos' | base64
d2VzdG9z
[root@k8s2 secret]# vim mysecret.yaml
apiVersion: v1
kind: Secret
metadata:
name: mysecret
type: Opaque
data:
username: YWRtaW4= #必须编码后的值
password: d2VzdG9z
[root@k8s2 secret]# kubectl apply -f mysecret.yaml
将Secret挂载到Volume中
[root@k8s2 secret]# vim pod1.yaml
apiVersion: v1
kind: Pod
metadata:
name: mysecret
spec:
containers:
- name: nginx
image: nginx
volumeMounts:
- name: secrets
mountPath: "/secret"
readOnly: true
volumes:
- name: secrets
secret:
secretName: mysecret
[root@k8s2 secret]# kubectl apply -f pod1.yaml
向指定路径映射 secret 密钥
[root@k8s2 secret]# vim pod2.yaml
apiVersion: v1
kind: Pod
metadata:
name: mysecret
spec:
containers:
- name: nginx
image: nginx
volumeMounts:
- name: secrets
mountPath: "/secret"
readOnly: true
volumes:
- name: secrets
secret:
secretName: mysecret
items:
- key: username
path: my-group/my-username
[root@k8s2 secret]# kubectl apply -f pod2.yaml
[root@k8s2 secret]# kubectl exec mysecret -- cat /secret/my-group/my-username
admin
将Secret设置为环境变量
[root@k8s2 secrets]# vim pod3.yaml
apiVersion: v1
kind: Pod
metadata:
name: secret-env
spec:
containers:
- name: pod3
image: busybox
command: ["/bin/sh", "-c", "env"]
env:
- name: SECRET_USERNAME
valueFrom:
secretKeyRef:
name: mysecret
key: username
- name: SECRET_PASSWORD
valueFrom:
secretKeyRef:
name: mysecret
key: password
restartPolicy: Never
存储docker registry的认证信息
新建私有仓库
[root@k8s2 secret]# kubectl create secret docker-registry myregistrykey --docker-server=reg.westos.org --docker-username=admin --docker-password=shg12345 [email protected]
[root@k8s2 secret]# vim pod4.yaml
apiVersion: v1
kind: Pod
metadata:
name: mypod
spec:
containers:
- name: game2048
image: reg.westos.org/westos/game2048
imagePullSecrets:
- name: myregistrykey