RHEL8_Linux防火墙
本章树妖介绍RHEL8中的firewalld的配置
- firewalld中的名词介绍
- firewalld的基本配置
- firewalld的规则添加
- firewalld的富规则
1.了解firewalld
在RHEL8中用的防火墙是firewalld,在 firewalld中又涉及zone的概念。首先来了解一下什么是zone。
如在进地铁或高铁时需要安检,安检有不同的入口,如图所示。
不同的入口严格度不一样,有的入口大包小包都要检测;有的入口只要检测大包即可,背包或单肩包就不用检测了;有的入口是绿色通道,不用检测直接通过。这里不同的安检入口制定了不同的规则。
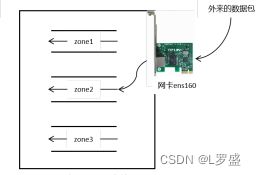
同理,firewalld中的zone我们就理解为如上的安检入口,不同的zone中制定了不同的规则。某网卡要和某一个zone进行关联,如图所示,ens160和 zone2进行关联,这样从网卡ens160进来的数据包都要使用zone2中的过滤规则。
网卡是不能同时和多个 zone关联的,最多只能和一个 zone关联。如果网卡没有和任何zone关联,则使用默认的zone中的规则。
2.firewalld的基本配置
[root@node01 ~]# firewall-cmd --get-default-zone
public
[root@node01 ~]#
1)查看系统中有多少个 zone,命令如下
[root@node01 ~]# firewall-cmd --get-zones
block dmz drop external home internal libvirt nm-shared public trusted work
[root@node01 ~]#
在这许多的zone中,其中 block拒绝所有的数据包通过,trusted允许所有的数据包通过。所以,如果把网卡和 trusted关联,则来自这张网卡的数据包都能通过。
_
2)查看系统默认的 zone,命令如下。
[root@node01 ~]# firewall-cmd --get-default-zone
public
[root@node01 ~]#
可以看到,默认的zone是 public。
3)把默认的zone修改为trusted,命令如下。
[root@node01 ~]# firewall-cmd --set-default-zone=trusted
success
[root@node01 ~]# firewall-cmd --get-default-zone
trusted
[root@node01 ~]#
4)再次把默认的zone改成public,命令如下。
[root@node01 ~]# firewall-cmd --set-default-zone=public
success
[root@node01 ~]#
5)查看网卡ens160和哪个zone关联,命令如下。
[root@node01 ~]# firewall-cmd --get-zone-of-interface=ens160
public
[root@node01 ~]#
可以看到,网卡 ens160是和public关联的。
6)把网卡加入某个 zone,语法如下。
firewall-cmd --add-interface=网卡名称 --zone=zone名 如果不指定zone名,则是默认的zone
把ens160和home这个 zone关联,命令如下。
[root@node01 ~]# firewall-cmd --add-interface=ens160 --zone=home
Error: ZONE_CONFLICT: 'ens160' already bound to a zone
[root@node01 ~]#
一张网卡只能在一个zone中,这里可以看到ens160已经属于一个zone了,所以发生了冲突。
可以先把网卡从public中删除,然后重新添加,这里把ens160 从 public中删除,命令如下。
[root@node01 ~]# firewall-cmd --remove-interface=ens160 --zone=public
success
[root@node01 ~]# firewall-cmd --get-zone-of-interface=ens160
no zone
[root@node01 ~]#
这样ens160就不属于任何zone了,如果不属于任何zone,则使用默认的zone中的规则。
然后把 ens160加入 home中,命令如下。
[root@node01 ~]# firewall-cmd --add-interface=ens160 --zone=home
success
[root@node01 ~]# firewall-cmd --get-zone-of-interface=ens160
home
[root@node01 ~]#
以后ens160会使用home中的规则,不再使用public中的规则。先从 zone中删除,然后再添加到其他的zone 中,这个过程可以用一条命令替换,命令如下。
[root@node01 ~]# firewall-cmd --change-interface=ens160 --zone=public
success
[root@node01 ~]#
这里的意思是把ens160切换到public这个zone,如果不指定zone,则是默认的zone,命令如下。
[root@node01 ~]# firewall-cmd --get-zone-of-interface=ens160
public
[root@node01 ~]#
后面的练习均是在public 中做。
3.配置firewalld的规则
网卡在哪个zone中就使用那个zone 中的规则,如果网卡不属于任何zone,则使用默认的zone中的规则。
一个zone中的规则可以通过“firewall-cmd --list-all --zone=zone名”来查看,如果不指定zone,则是默认的zone.
1)现在查看 public这个 zone中的规则。
[root@node01 ~]# firewall-cmd --list-all --zone=public
public (active)
target: default
icmp-block-inversion: no
interfaces: ens160
sources:
services: cockpit dhcpv6-client mountd nfs rpc-bind ssh
ports: 123/udp 323/udp 20-21/tcp 10010-10020/tcp
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@node01 ~]#
因为默认的zone就是 public,所以这里即使不加--zone=public选项,显示的也是public这个zone中的规则。
我们看一下最常用的一些设置。
1.icmp-blocks
平时测试网络通或不通是用ping进行测试的,使用的是 icmp 协议,如图所示
icmp有很多类型的数据包,ping的时候用的是以下两种。
- echo-request:我ping对方时发出去的包。
- echo-reply:对方回应我的包。
一共有多少种类型的icmp包,可以通过“firewall-cmd --get-icmptypes”来查看。
1)在node01上执行 tcpdump命令进行抓包,命令如下。
[root@node01 ~]# tcpdump -i ens160 icmp
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens160, link-type EN10MB (Ethernet), capture size 262144 bytes
2)在node03 上ping node01的IP两次,命令如下。
[root@node03 ~]# ping 192.168.182.200
PING 192.168.182.200 (192.168.182.200) 56(84) bytes of data.
64 bytes from 192.168.182.200: icmp_seq=1 ttl=64 time=0.321 ms
64 bytes from 192.168.182.200: icmp_seq=2 ttl=64 time=0.611 ms
64 bytes from 192.168.182.200: icmp_seq=3 ttl=64 time=0.488 ms
3)然后到node01上查看,命令如下。
[root@node01 ~]# tcpdump -i ens160 icmp
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens160, link-type EN10MB (Ethernet), capture size 262144 bytes
11:58:33.122650 IP 192.168.182.193 > node01: ICMP echo request, id 2179, seq 1, length 64
11:58:33.122758 IP node01 > 192.168.182.193: ICMP echo reply, id 2179, seq 1, length 64
11:58:34.141822 IP 192.168.182.193 > node01: ICMP echo request, id 2179, seq 2, length 64
11:58:34.141877 IP node01 > 192.168.182.193: ICMP echo reply, id 2179, seq 2, length 64
^C
58 packets captured
68 packets received by filter
8 packets dropped by kernel
[root@node01 ~]#
这里node03往node01发送了两个echo-request包,node01均回应了echo-reply包。
4)在node01上用防火墙设置拒绝别人发过来的echo-request包,命令如下。
[root@node01 ~]# firewall-cmd --add-icmp-block=echo-request //拒绝请求
success
[root@node01 ~]# firewall-cmd --list-all //查看是否添加成功
public (active)
target: default
icmp-block-inversion: no
interfaces: ens160
sources:
services: cockpit dhcpv6-client mountd nfs rpc-bind ssh
ports: 123/udp 323/udp 20-21/tcp 10010-10020/tcp
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks: echo-request //已经添加
rich rules:
[root@node01 ~]#
5)此时,node01就不再接收别人发过来的echo-request包了,然后到node03再次 ping,命令如下。
[root@node03 ~]# ping 192.168.182.200 -c2
PING 192.168.182.200 (192.168.182.200) 56(84) bytes of data.
From 192.168.182.200 icmp_seq=1 Packet filtered
From 192.168.182.200 icmp_seq=2 Packet filtered
--- 192.168.182.200 ping statistics ---
2 packets transmitted, 0 received, +2 errors, 100% packet loss, time 1061ms
[root@node03 ~]#
可以看到,在node03上已经 ping不通node01 了
6)如果要想继续ping操作,就取消对应的设置,命令如下
[root@node01 ~]# firewall-cmd --remove-icmp-block=echo-request
success
[root@node01 ~]#
2.services
两台主机通信必须使用某个协议,例如,浏览器访问网站用的是http,远程登录到Linux 服务器用的是ssh 协议等。
1)默认情况下,public这个 zone只允许很少的服务通过,如下所示。
[root@node01 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens160
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@node01 ~]#
可以看到,这里没有允许http通过。
2)如果要查看防火墙是否开放了某个协议,也可以通过如下语法来查看
firewall-cmd --query-service=服务名称3)要获取系统所支持的所有服务,可以通过如下命令来查看。
[root@node01 ~]# firewall-cmd --get-services
4)再次验证http是否被firewall允许,命令如下。
[root@node01 ~]# firewall-cmd --query-service=http
no
[root@node01 ~]#
5)在node01上通过yum install httpd -y安装httpd包,启动服务并写一些测试数据,命令如下。
[root@node01 ~]# systemctl start httpd //启动http服务
[root@node01 ~]# echo "hello ls" > /var/www/html/index.html //把hello ls重定向导入网页文件内
[root@node01 ~]# cat /var/www/html/index.html //查看文件内容
hello ls
[root@node01 ~]#
6)然后在宿主机上用浏览器访问node01(IP地址是192.168.182.200),
7) 可以看到,现在根本访问不了,这是因为node01上的防火墙并不允许http的数据包通过,然后在防火墙中开放http,命令如下。
[root@node01 ~]# firewall-cmd --add-service=http
success
[root@node01 ~]# firewall-cmd --query-service=http
yes
[root@node01 ~]#
8)再次打开浏览器验证,结果如图。
9)此时可以正常打开了。如果要从防火墙中把此服务删除,则可用--remove-service选项,命令如下。
[root@node01 ~]# firewall-cmd --remove-service=http
success
[root@node01 ~]# firewall-cmd --query-service=http
no
[root@node01 ~]#
此时浏览器中是访问不了192.168.182.200的。
3.ports
前面介绍了对服务进行过滤与放行,这些服务使用的都是标准端口,例如,http对应的是端口80,ssh对应的是端口22等。
但有时服务使用的是一个非标准端口,例如,把服务httpd的端口更改为8080。如果在防火墙中只是放行http这个服务,本质上就是放行了端口80,此时用户肯定是访问不到Web服务的,因为只能通过端口8080才能访问到Web 服务。下面做一下这个实验。
1)先临时关闭SELinux,命令如下。
[root@node01 ~]# setenforce 0
[root@node01 ~]# getenforce
Permissive
[root@node01 ~]#
确保SELinux是处在Permissive模式的。
2)用如下命令把 httpd的端口替换为8080,并重启httpd服务,命令如下。
[root@node01 ~]# sed -i '/^Listen/cListen 8080' /etc/httpd/conf/httpd.conf 3)首先在防火墙中放行http,命令如下。
[root@node01 ~]# firewall-cmd --add-service=http
success
[root@node01 ~]#
4)在浏览器中访问192.168.182.200:8080,结果如图所示。
可以看到,访问失败,因为放行http也只是允许端口80而非端口8080
5)把 http服务从防火墙中删除,命令如下。
[root@node01 ~]# firewall-cmd --remove-service=http
success
[root@node01 ~]#
下面开始放行端口,常用的语句如下:
-
firewall-cmd --query-port=N/协议:查询是否开放了端口N
-
firewall-cmd --add-port=N/协议:开放端口N。
-
firewall-cmd --remove-port=N/协议:删除端口N。这里的协议包括TCP、UDP等。
6)在防火墙中添加端口,也可以添加一个范围。例如,要在防火墙中开放1000~-2000范围 的端口,可以用如下命令。
[root@node01 ~]# firewall-cmd --add-port=1000-2000/tcp
success
[root@node01 ~]# 这里“-”表示到的意思。
7)下面把端口8080放行,命令如下。
[root@node01 ~]# firewall-cmd --add-port=8080/tcp
success
[root@node01 ~]# firewall-cmd --query-port=8080/tcp
yes
[root@node01 ~]#
8)然后再次在浏览器中访问,结果如图
现在已经可以正常访问了。
9)在防火墙中删除此端口,命令如下
[root@node01 ~]# firewall-cmd --remove-port=8080/tcp
success
[root@node01 ~]# firewall-cmd --query-port=8080/tcp
no
[root@node01 ~]#
10)下面把环境还原,再次开启SELinux,确保状态为Enforcing模式,命令如下。
[root@node01 ~]# setenforce 1
[root@node01 ~]# getenforce
Enforcing
[root@node01 ~]#
11)再次把httpd的端口改为80,并重启服务,命令如下。
[root@node01 ~]# sed -i '/^Listent/cListent 80' /etc/httpd/conf/httpd.conf
[root@node01 ~]# systemctl restart httpd
[root@node01 ~]#
4.富规则
前面不管是对端口放行还是对服务放行,都会遇到一个问题就是,如果允许则是允许所有的客户端,如果拒绝则是拒绝所有的客户端,有种一刀切的感觉。
有时需要设置只允许特定的客户端访问,其他客户端都不能访问,此时就需要使用到富规则。
富规则可以对服务进行限制,也可以对端口进行限制。放行服务的语法如下。
[root@node01 ~]# firewall-cmd --add-rich-rule='rule family=ipv4 source address=源网段 service name=服务名 accept'
这里用单引号或双引号均可,先查看现在是否有富规则。
[root@node01 ~]# firewall-cmd --list-rich-rules
[root@node01 ~]#
现在还没有任何富规则,下面开始创建富规则。
1.练习:允许192.168.26.1访问本机的 http服务,其他客户端都不能访问。
1)先确保在防火墙的services中没有添加 http,否则所有的客户端都能访问了。
[root@node01 ~]# firewall-cmd --query-service=http
no
[root@node01 ~]#
现在确定在services中是没有添加 http的,所以现在所有客户端都是被拒绝访问的。
2)下面开始添加富规则,命令如下。
[root@node01 ~]# firewall-cmd --add-rich-rule="rule family=ipv4 source address=192.168.182.1 service name=http accept"
success
[root@node01 ~]#
3)在192.168.182.1(笔记本电脑)上用浏览器 访问node01(P地址是192.168.182.200),结果如图。
4)可以看到,现在是正常的,然后在192.168.182.220(node03机器)上用浏览器访问node01(IP地址是192.168.182.200)
可以看到,访问不了。
5)查看现有富规则,命令如下。
[root@node01 ~]# firewall-cmd --list-rich-rules
rule family="ipv4" source address="192.168.182.1" service name="http" accept
[root@node01 ~]#
6)富规则的命令只要把添加时的add换成remove即可删除此富规则,命令如下。
[root@node01 ~]# firewall-cmd --remove-rich-rule="rule family=ipv4 source address=192.168.182.1 service name=http accept"
success
[root@node01 ~]#
7)放行端口的语法如下。
[root@node01 ~]# firewall-cmd --add-rich-rule='rule family=ipv4 source address=源网段 port port=M-N protocol=协议 accept'
这里M-N的意思是从端口M到端口N。