《工具录》dig
工具录
- 1:dig
- 2:选项介绍
- 3:示例
- 4:其他
本文以 kali-linux-2023.2-vmware-amd64 为例。
1:dig
dig 是域名系统(DNS)查询工具,常用于域名解析和网络故障排除。比 nslookup 有更强大的功能。
基本语法:
dig [选项]
2:选项介绍
选项总览:
┌──(root㉿kali)-[~]
└─# dig -h
Usage: dig [@global-server] [domain] [q-type] [q-class] {q-opt}
{global-d-opt} host [@local-server] {local-d-opt}
[ host [@local-server] {local-d-opt} [...]]
Where: domain is in the Domain Name System
q-class is one of (in,hs,ch,...) [default: in]
q-type is one of (a,any,mx,ns,soa,hinfo,axfr,txt,...) [default:a]
(Use ixfr=version for type ixfr)
q-opt is one of:
-4 (use IPv4 query transport only)
-6 (use IPv6 query transport only)
-b address[#port] (bind to source address/port)
-c class (specify query class)
-f filename (batch mode)
-k keyfile (specify tsig key file)
-m (enable memory usage debugging)
-p port (specify port number)
-q name (specify query name)
-r (do not read ~/.digrc)
-t type (specify query type)
-u (display times in usec instead of msec)
-x dot-notation (shortcut for reverse lookups)
-y [hmac:]name:key (specify named base64 tsig key)
d-opt is of the form +keyword[=value], where keyword is:
+[no]aaflag (Set AA flag in query (+[no]aaflag))
+[no]aaonly (Set AA flag in query (+[no]aaflag))
+[no]additional (Control display of additional section)
+[no]adflag (Set AD flag in query (default on))
+[no]all (Set or clear all display flags)
+[no]answer (Control display of answer section)
+[no]authority (Control display of authority section)
+[no]badcookie (Retry BADCOOKIE responses)
+[no]besteffort (Try to parse even illegal messages)
+bufsize[=###] (Set EDNS0 Max UDP packet size)
+[no]cdflag (Set checking disabled flag in query)
+[no]class (Control display of class in records)
+[no]cmd (Control display of command line -
global option)
+[no]comments (Control display of packet header
and section name comments)
+[no]cookie (Add a COOKIE option to the request)
+[no]crypto (Control display of cryptographic
fields in records)
+[no]defname (Use search list (+[no]search))
+[no]dns64prefix (Get the DNS64 prefixes from ipv4only.arpa)
+[no]dnssec (Request DNSSEC records)
+domain=### (Set default domainname)
+[no]edns[=###] (Set EDNS version) [0]
+ednsflags=### (Set EDNS flag bits)
+[no]ednsnegotiation (Set EDNS version negotiation)
+ednsopt=###[:value] (Send specified EDNS option)
+noednsopt (Clear list of +ednsopt options)
+[no]expandaaaa (Expand AAAA records)
+[no]expire (Request time to expire)
+[no]fail (Don't try next server on SERVFAIL)
+[no]header-only (Send query without a question section)
+[no]https[=###] (DNS-over-HTTPS mode) [/]
+[no]https-get (Use GET instead of default POST method while using HTTPS)
+[no]http-plain[=###] (DNS over plain HTTP mode) [/]
+[no]http-plain-get (Use GET instead of default POST method while using plain HTTP)
+[no]identify (ID responders in short answers)
+[no]idn (convert international domain names)
+[no]ignore (Don't revert to TCP for TC responses.)
+[no]keepalive (Request EDNS TCP keepalive)
+[no]keepopen (Keep the TCP socket open between queries)
+[no]multiline (Print records in an expanded format)
+ndots=### (Set search NDOTS value)
+[no]nsid (Request Name Server ID)
+[no]nssearch (Search all authoritative nameservers)
+[no]onesoa (AXFR prints only one soa record)
+[no]opcode=### (Set the opcode of the request)
+padding=### (Set padding block size [0])
+qid=### (Specify the query ID to use when sending queries)
+[no]qr (Print question before sending)
+[no]question (Control display of question section)
+[no]raflag (Set RA flag in query (+[no]raflag))
+[no]rdflag (Recursive mode (+[no]recurse))
+[no]recurse (Recursive mode (+[no]rdflag))
+retry=### (Set number of UDP retries) [2]
+[no]rrcomments (Control display of per-record comments)
+[no]search (Set whether to use searchlist)
+[no]short (Display nothing except short
form of answers - global option)
+[no]showbadcookie (Show BADCOOKIE message)
+[no]showsearch (Search with intermediate results)
+[no]split=## (Split hex/base64 fields into chunks)
+[no]stats (Control display of statistics)
+subnet=addr (Set edns-client-subnet option)
+[no]tcflag (Set TC flag in query (+[no]tcflag))
+[no]tcp (TCP mode (+[no]vc))
+timeout=### (Set query timeout) [5]
+[no]tls (DNS-over-TLS mode)
+[no]tls-ca[=file] (Enable remote server's TLS certificate validation)
+[no]tls-hostname=hostname (Explicitly set the expected TLS hostname)
+[no]tls-certfile=file (Load client TLS certificate chain from file)
+[no]tls-keyfile=file (Load client TLS private key from file)
+[no]trace (Trace delegation down from root [+dnssec])
+tries=### (Set number of UDP attempts) [3]
+[no]ttlid (Control display of ttls in records)
+[no]ttlunits (Display TTLs in human-readable units)
+[no]unknownformat (Print RDATA in RFC 3597 "unknown" format)
+[no]vc (TCP mode (+[no]tcp))
+[no]yaml (Present the results as YAML)
+[no]zflag (Set Z flag in query)
global d-opts and servers (before host name) affect all queries.
local d-opts and servers (after host name) affect only that lookup.
-h (print help and exit)
-v (print version and exit)
3:示例
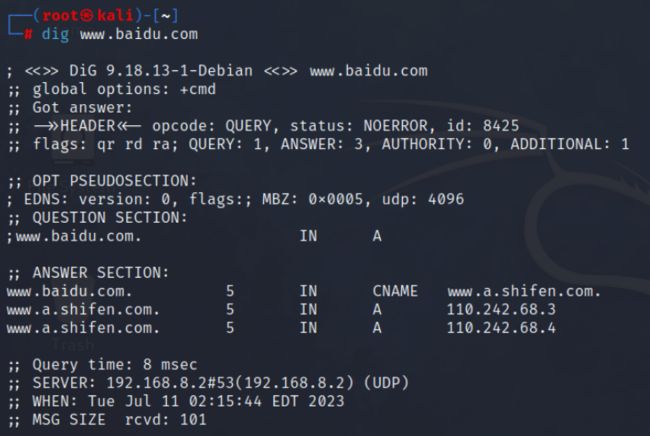
示例 3-1:查询 www.baidu.com 的 DNS 信息。
dig www.baidu.com
结果:
解释:
; <<>> DiG 9.18.13-1-Debian <<>> www.baidu.com # dig 版本和要查询的域
;; global options: +cmd # 全局选项,dig 可以查询多个域,这里显示应用于所有查询的选项。默认为 +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 8425
# 输出从 DNS 返回的技术信息
# opcode(操作码):QUERY(查询),IQUERY(反查询),STATUS(监测状态)等。
# status(状态):NOERROR 表示请求查询成功。
# id:一个随机的将请求与响应绑定在一起的数字。
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
# qr(query)
# rd(recursion desired)
# ra(recursion avaliable)
# aa(authoritative answer)代表权威域名服务器作出了响应
# QUERY:查询数量
# ANSWER:结果数量
# AURHORITY:来自权威域名服务器的结果数量
# ADDITIONAL:附加信息,当其值大于1的时候才会看到额外信息
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; MBZ: 0x0005, udp: 4096
# 选择伪切片
;; QUESTION SECTION:
;www.baidu.com. IN A
# 查询字段,显示要查询的域名以及查询的服务
# IN(Internet)表示互联网查询
# A(Address)表示 A 记录查询,即主机查询
;; ANSWER SECTION:
www.baidu.com. 5 IN CNAME www.a.shifen.com.
www.a.shifen.com. 5 IN A 110.242.68.3
www.a.shifen.com. 5 IN A 110.242.68.4
# 查询结果
;; Query time: 8 msec
;; SERVER: 192.168.8.2#53(192.168.8.2) (UDP)
;; WHEN: Tue Jul 11 02:15:44 EDT 2023
;; MSG SIZE rcvd: 101
# 请求所花的时间,DNS 服务器,当前时间,查询信息的大小
示例 3-2:只显示简要信息,而不显示任何其他信息。
dig www.baidu.com +short
结果:
示例 3-3:查询域名的邮件交换(MX)记录。
dig google.com MX
结果:
示例 3-4:查看 txt 记录。
dig google.com TXT
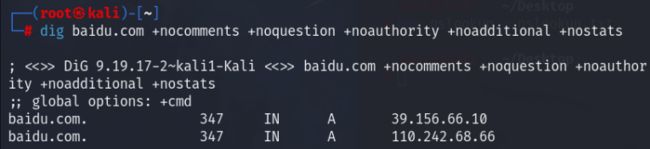
示例 3-5:得到最基本的 DNS 查询结果,不包含注释、问题、权威、附加和统计信息。
dig baidu.com +nocomments +noquestion +noauthority +noadditional +nostats
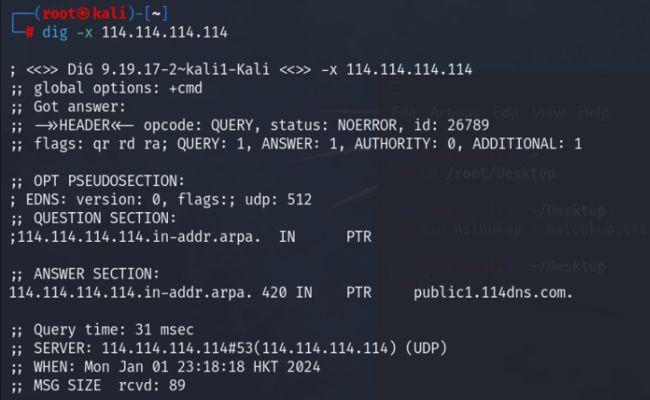
示例 3-6:反向查询与指定 IP 地址相关联的域名。
dig -x 114.114.114.114
示例 3-7:指定 DNS 服务器对相同的域名解析。
dig @114.114.114.114 www.baidu.com
示例 3-8:显示 DNS 查询的整个路由。
dig +trace baidu.com
示例 3-9:指定 DNS 服务端口号。如果 DNS 服务标准端口 53 被更改则可以使用此命令。
dig -p 5300 www.baidu.com
4:其他
其他资料:
《dig 命令的学习》:
https://blog.csdn.net/u014029795/article/details/87226813
《linux 命令总结之 dig 命令》:
https://blog.csdn.net/GzmObject/article/details/124696962
《How to Use the Dig Command in Linux》:
https://www.hostinger.com/tutorials/how-to-use-the-dig-command-in-linux/
《DIG command: Query name servers》:
https://www.ibm.com/docs/en/zos/2.1.0?topic=command-dig-query-name-servers
知我者,谓我心忧;不知我者,谓我何求。
——《黍离》(先秦)