最近的任务是整理和优化公司一个项目的登录和权限部分,项目大大小小有10几个子系统必然涉及到SSO,项目本身的单点登录方案实现比较简单,可扩展性不强。于是看了部分开源的解决方案(其实主要是看了CAS,呵呵)。
下面就我体验CAS的单点登录方案,记录整个过程,做个备案。
1.准备工具
cas-server-3.5.2-release.zip
cas-client-java-2.1.1.zip
2.配置环境
计算机系统:winxP
计算机域名:xwtec-1531
数据库:oracle11g
web容器:tomcat6
JDK版本:jdk1.6.0_24
ip:192.168.1.150
3.CAS验证服务器搭建
先解压cas-server-3.5.2-release.zip到任意盘,将modules目录下的cas-server-webapp-3.5.2.war重命名为cas.war复制到tomcat的webapp目录下,启动tomcat
待tomcat启动成功后在浏览器地址栏输入http://192.168.1.150:8080/cas/login显示登录界面
输入用户名和密码可登录(默认输入相同字符串),至此验证服务器搭建完毕,接下来可定制自己的特定需求。
4.密码验证
密码的鉴权在配置文件/WEB-INFO/deployerConfigContext.xml中,如下
<property name="authenticationHandlers"> <list> <!--jdbc鉴权认证--> <bean class="org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler"> <property name="dataSource" ref="dataSource" /> <property name="sql" value="select password from userinfo where username=?" /> <property name="passwordEncoder" ref="passwordEncoderBean"/> </bean> <!-- | This is the authentication handler that authenticates services by means of callback via SSL, thereby validating | a server side SSL certificate. + <bean class="org.jasig.cas.authentication.handler.support.HttpBasedServiceCredentialsAuthenticationHandler" p:httpClient-ref="httpClient" />--> <!-- | This is the authentication handler declaration that every CAS deployer will need to change before deploying CAS | into production. The default SimpleTestUsernamePasswordAuthenticationHandler authenticates UsernamePasswordCredentials | where the username equals the password. You will need to replace this with an AuthenticationHandler that implements your | local authentication strategy. You might accomplish this by coding a new such handler and declaring | edu.someschool.its.cas.MySpecialHandler here, or you might use one of the handlers provided in the adaptors modules. + <bean class="org.jasig.cas.authentication.handler.support.SimpleTestUsernamePasswordAuthenticationHandler" />这里为默认的鉴权方式,即密码等于用户名--> </list> </property>
我这里密码的鉴权采用jdbc的方式来验证,另外密码的加密方式采用MD5
<!-- Data source definition -->
<bean id="dataSource" class="org.springframework.jdbc.datasource.DriverManagerDataSource">
<property name="driverClassName">
<value>oracle.jdbc.driver.OracleDriver</value>
</property>
<property name="url">
<!--如果使用mysql数据库,应该加上后面的编码参数,否则可能导致客户端对TGT票据无法识别的问题-->
<value>jdbc:oracle:thin:@localhost:1521:cring</value>
</property>
<property name="username"><value>xw_uomp</value></property>
<property name="password"><value>xw_uomp123</value></property>
</bean>
<bean id="passwordEncoderBean" class="org.jasig.cas.authentication.handler.DefaultPasswordEncoder">
<!--cas server默认支持MD5和SHA1两种编码方式,如果需要其他的编码方式例如SHA256,512等,可自行实现org.jasig.cas.authentication.handler.PasswordEncoder接口-->
<constructor-arg value="MD5" />
</bean>
至此我们重启TOMCAT,输入http://192.168.1.150:8080/cas/login 跳转上图的登录页面后输入userinfo表中自己预置的用户名和密码
这里提下userinfo用的密码是MD5加密的,预置数据时可以参考下DefaultPasswordEncoder.java这个类(在cas-server-core.jar中,见附件auth.rar)
5.HTTPS验证
cmd命令行到c盘的根目录下
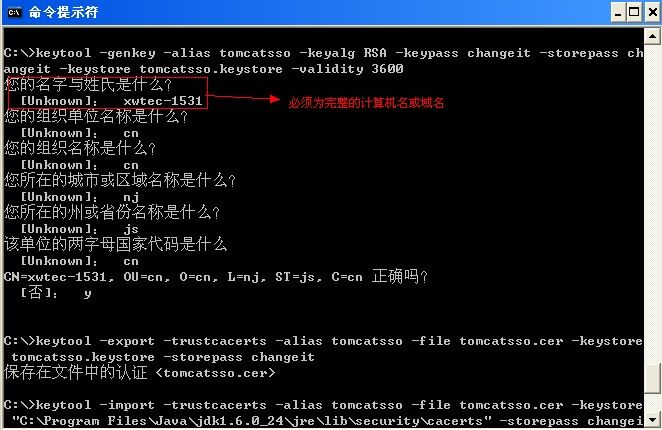
创建key
keytool -genkey -alias tomcatsso -keyalg RSA -keypass changeit -storepass changeit -keystore tomcatsso.keystore -validity 3600
导出证书(服务端)
keytool -export -trustcacerts -alias tomcatsso -file tomcatsso.cer -keystore tomcatsso.keystore -storepass changeit
导入证书到信任库(客户端)
keytool -import -trustcacerts -alias tomcatsso -file tomcatsso.cer -keystore "C:\Program Files\Java\jdk1.6.0_24\jre\lib\security\cacerts" -storepass changeit
删除
keytool -delete -alias tomcatsso -keyalg RSA -keypass changeit -storepass changeit -keystore tomcatsso.keystore -validity 3600
配置tomcat
/conf/server.xml 添加如下行
<Connector protocol="org.apache.coyote.http11.Http11NioProtocol" port="8443" minSpareThreads="5" maxSpareThreads="75" enableLookups="true" disableUploadTimeout="ture"
acceptCount="100" SSLEnabled="true"
maxThreads="200" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS" keystoreFile="c:\tomcatsso.keystore" keystorePass="changeit"/>
至此HTTPS方式验证登陆搞定,https://xwtec-1531:8443/cas/login登陆OK
配置客户端A、B验证CAS单点登录
web.xml 配置文件一样,如下:
<?xml version="1.0" encoding="UTF-8"?> <web-app version="2.5" xmlns="http://java.sun.com/xml/ns/javaee" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://java.sun.com/xml/ns/javaee http://java.sun.com/xml/ns/javaee/web-app_2_5.xsd"> <filter> <filter-name>CAS Filter</filter-name> <filter-class>edu.yale.its.tp.cas.client.filter.CASFilter</filter-class> <init-param> <param-name>edu.yale.its.tp.cas.client.filter.loginUrl</param-name> <param-value>https://xwtec-1531:8443/cas/login</param-value> </init-param> <init-param> <param-name>edu.yale.its.tp.cas.client.filter.validateUrl</param-name> <param-value>https://xwtec-1531:8443/cas/serviceValidate</param-value> </init-param> <init-param> <param-name>edu.yale.its.tp.cas.client.filter.serverName</param-name> <param-value>xwtec-1531:8080</param-value> </init-param> </filter> <filter-mapping> <filter-name>CAS Filter</filter-name> <url-pattern>/*</url-pattern> </filter-mapping> <welcome-file-list> <welcome-file>index.jsp</welcome-file> </welcome-file-list> </web-app>
分别在CASClientA和CASClientB的工程下的index.jsp中添加如下代码区分登录
<span>CASClientA:<%=request.getSession().getAttribute("edu.yale.its.tp.cas.client.filter.user") %></span>
<span>CASClientB:<%=request.getSession().getAttribute("edu.yale.its.tp.cas.client.filter.user") %></span>
OK,全部完成了,测试的效果:
在地址栏输入http://xwtec-1531:8080/CASClientA 会被重定向到cas的登录页面
输入用户名和密码成功后再被跳转到index.jsp,显示
然后在地址栏输入http://xwtec-1531:8080/CASClientB则不需要重新登录了直接跳转到index.jsp