Install and Configure OpenStack Identity Service (Keystone)
Based on OpenStack Icehouse release
1. service NetworkManager stop; chkconfig NetworkManager off
service network start; chkconfig network on
disable firewall and selinux
service iptables stop; chkconfig iptables off
service ip6tables stop; chkconfig ip6tables off
2. eth0 for management/public/floating (192.168.1.0/24), eth1 for internal/flat (192.168.20.0/24), it's recommended to use seperated nic for management network
3. set hostname in /etc/sysconfig/network
vi /etc/hosts
192.168.1.10 controller
192.168.1.11 node1
4. yum -y install ntp
vi /etc/ntp.conf
restrict 3.cn.pool.ntp.org
restrict 0.asia.pool.ntp.org
restrict 2.asia.pool.ntp.org
restrict 192.168.1.0 mask 255.255.255.0 nomodify notrap
server 3.cn.pool.ntp.org
server 0.asia.pool.ntp.org
server 2.asia.pool.ntp.org
service ntpd start; chkconfig ntpd on
5. install mysql server
yum -y install mysql-server
vi /etc/my.cnf
[mysqld]
default-storage-engine = innodb
collation-server = utf8_general_ci
init-connect = 'SET NAMES utf8'
character-set-server = utf8
service mysqld start; chkconfig mysqld on
mysql_secure_installation
6. yum -y install qpid-cpp-server
vi /etc/qpidd.conf
# last line: change
auth=no
service qpidd start; chkconfig qpidd on
7. yum -y install http://repos.fedorapeople.org/repos/openstack/openstack-icehouse/rdo-release-icehouse-3.noarch.rpm
yum -y install http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm
yum -y install mysql MySQL-python
8. Install and Configure OpenStack Identity Service (Keystone)
yum -y install openstack-keystone openstack-utils
mysql -uroot -p
mysql> create database keystone;
mysql> grant all privileges on keystone.* to 'keystone'@'localhost' identified by 'KEYSTONE-DBPASS';
mysql> grant all privileges on keystone.* to 'keystone'@'%' identified by 'KEYSTONE-DBPASS';
mysql> flush privileges;
vi /etc/keystone/keystone.conf
[database]
connection = mysql://keystone:keystone@MYSQL-SERVER/keystone
keystone-manage db_sync
vi /etc/keystone/keystone.conf
admin_token = admintoken
token_format = PKI
certfile = /etc/keystone/ssl/certs/signing_cert.pem
keyfile = /etc/keystone/ssl/private/signing_key.pem
ca_certs = /etc/keystone/ssl/certs/ca.pem
ca_key = /etc/keystone/ssl/private/cakey.pem
key_size = 2048
valid_days = 3650
cert_subject = /C=CN/ST=Shanghai/L=Shanghai/O=HKT/CN=controller.test.pri
9. keystone-manage pki_setup --keystone-user keystone --keystone-group keystone
chown -R keystone:keystone /etc/keystone /var/log/keystone
chmod -R o-rwx /etc/keystone/ssl
service openstack-keystone start; chkconfig openstack-keystone on
10. crontab -e
@hourly /usr/bin/keystone-manage token_flush >/var/log/keystone/keystone-tokenflush.log 2>&1
service crond restart
11. export OS_SERVICE_TOKEN=admintoken
export OS_SERVICE_ENDPOINT=http://controller:35357/v2.0
12.# add admin tenant
keystone tenant-create --name admin --description "Admin Tenant"
keystone tenant-create --name service --description "Service Tenant"
# add admin role
keystone role-create --name admin
keystone user-create --tenant admin --name admin --pass ADMIN-USER-PASSWORD
keystone user-role-add --user admin --tenant admin --role admin
# add demo1 tenant
keystone tenant-create --name=demo1 --description="Demo1 Tenant"
# add demo1 user
keystone user-create --tenant demo1 --name demo1 --pass DEMO1-USER-PASSWORD
# add service for keystone
keystone service-create --name=keystone --type=identity --description="Keystone Identity Service"
keystone endpoint-create --region RegionOne --service keystone --publicurl=http://controller:5000/v2.0 --internalurl=http://controller:5000/v2.0 --adminurl=http://controller:35357/v2.0
13. Load environment variables
unset OS_SERVICE_TOKEN OS_SERVICE_ENDPOINT
vi ~/adminrc
export OS_USERNAME=admin
export OS_PASSWORD=ADMIN-USER-PASSWORD
export OS_TENANT_NAME=admin
export OS_AUTH_URL=http://controller:35357/v2.0
chmod 600 ~/adminrc ; source ~/adminrc
echo "source ~/adminrc " >> ~/.bash_profile
vi ~/demo1rc
export OS_USERNAME=demo1
export OS_PASSWORD=DEMO1-USER-PASSWORD
export OS_TENANT_NAME=demo1
export OS_AUTH_URL=http://controller:35357/v2.0
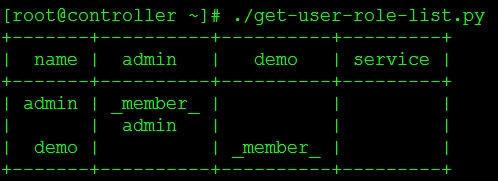
Get user-role-list script
vi get-user-role-list.py
#!/usr/bin/python
import os, prettytable, sys
from keystoneclient.v2_0 import client
from keystoneclient import utils
keystone = client.Client(username=os.environ['OS_USERNAME'], password=os.environ['OS_PASSWORD'],
tenant_name=os.environ['OS_TENANT_NAME'], auth_url=os.environ['OS_AUTH_URL'])
f_user = f_tenant = ""
if "-u" in sys.argv: f_user = sys.argv[sys.argv.index("-u")+1]
if "-t" in sys.argv: f_tenant = sys.argv[sys.argv.index("-t")+1]
tenants = [t for t in keystone.tenants.list() if f_tenant in t.name]
users = [u for u in keystone.users.list() if f_user in u.name]
pt = prettytable.PrettyTable(["name"]+[t.name for t in tenants])
for user in users:
row = [user.name]
for tenant in tenants:
row.append("\n".join([u.name for u in user.list_roles(tenant.id)]))
pt.add_row(row)
print pt.get_string(sortby="name")
chmod +x get-user-role-list.py
./get-user-role-list.py