Cisco NAT-T实验
Cisco NAT-T
实验
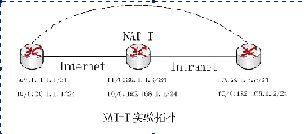
实验拓扑图:
实验步骤:
1
使用
DynamipsGUI
构建网络拓扑结构:
2
分别配置
3
台路由器:
R1
:
hostname R1
no ip domain lookup
line console 0
exec-timeout 0 0
logging synchronous
interface Loopback0
ip address 1.1.1 .1 255.255.255.0
interface FastEthernet0/0
ip address 20.1.1 .1 255.255.255.0
crypto map test
crypto isakmp enable
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 20.1.1 .1
access-list 101 permit i p 1.1.1 .0 0.0.0.255 3.3.3.0 0.0.0.255
crypto ipsec transform-set huyiqian ah-md5-hmac esp-3des
crypto map test 1 ipsec-isakmp
set peer 20.1.1 .2
set transform-set huyiqian
match address 101
ip route 0.0.0 .0 0.0.0.0 FastEthernet0/0
R2
:
hostname R2
no ip domain lookup
line console 0
exec-timeout 0 0
logging synchronous
interface FastEthernet0/0
ip address 192.168.1.1 255.255.255.0
ip nat inside
interface FastEthernet1/0
ip address 20.1.1 .2 255.255.255.0
ip nat outside
access-list 100 permit i p 3.3.3 .0 0.0.0.255 any
ip nat inside source list 100 interface FastEthernet0/0 overload
ip nat inside source static udp 192.168.1.2 500 interface FastEthernet1/0 500
ip nat inside source static udp 192.168.1.2 4500 interface FastEthernet1/0 4500
ip nat inside source static esp 192.168.1.2 interface FastEthernet1/0
ip route 0.0.0 .0 0.0.0.0 FastEthernet1/0
ip route 3.3.3 .0 255.255.255.0 FastEthernet0/0
R3
:
hostname R3
no ip domain lookup
line console 0
exec-timeout 0 0
logging synchronous
interface Loopback0
ip address 3.3.3 .3 255.255.255.0
interface FastEthernet0/0
ip address 192.168.1.2 255.255.255.0
crypto map test
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 20.1.1 .1
access-list 101 permit i p 3.3.3 .0 0.0.0.255 1.1.1.0 0.0.0.255
crypto ipsec transform-set huyiqian ah-md5-hmac esp-3des
crypto map test 1 ipsec-isakmp
set peer 20.1.1 .1
set transform-set huyiqian
match address 101
ip route 0.0.0 .0 0.0.0.0 FastEthernet0/0
3
检测网络连通性:
R1
:

R3
:

R2
: