Steganography
Steganography就是隐写术的意思,整理一下相关题目。
http://utilitymill.com/edit/Steganography_Decode
Windows~(Asis-CTF2013)
这个题是一段视频,里面有些乱七八糟的声音,视频上一直在显示一些不断闪动的小窗户,像这样。
首先处理音频,这里使用了格式工厂和Audacity,使用格式工厂转换成wav格式,之后用Audacity打开,使用其中的特效,前后颠倒,之后就可以听到一串数字
51324984652187698521487459648201
之后处理视频,根据提示小窗子们会排列成一个二维码。
这里使用kmp的捕获功能,将每一帧的文件抓取出来,会得到100个图片文件,将他们整合起来还是很费劲的,使用ps的动作功能来处理。
这里注意,录制动作脚本时,处理下一个文件的时候一定要关闭上一个文件,要不会导致内存不足。
执行100次之后得到的图片,差不多是个二维码的样子了。
之后我们把它简单的处理一下,不过这样貌似也是不能读取的·
再修修补补,读出内容xorwinth313
综合得出的信息,音频得出的数字,再xor上313就是key了。
ChessBorad(Asis-CTF2013)
这个题也是给了一个图片,首先明确在表示颜色的位中是没有藏数据的(LSB-stegano),这一点很重要。
同时这种题目使用算法藏数据会变得很没意思。
观察一下图片,每个小格子的颜色貌似不一样,在ps中吸取其中的RGB(xxx,xxx,xxx) 因为是灰色,三个值就是一样的。
都统计出来是这样
0 140 0 0 0 35 0 0 0 80 0 0 110 30 70 150 0 95 0 0 0 0 0 0 0 155 100 170 130 0 0 0 135 175 85 145 0 75 165 0 5 115 105 45 25 10 125 90 180 20 0 160 65 15 0 120 0 0 0 0 50 55 40 60很容易就看出,这些数都可以被5整除,我们可以整除一下试试
0 28 0 0 0 7 0 0 0 16 0 0 22 6 14 30 0 19 0 0 0 0 0 0 0 31 20 34 26 0 0 0 27 35 17 29 0 15 33 0 1 23 21 9 5 2 25 18 36 4 0 32 13 3 0 24 0 0 0 0 10 11 8 12至于这里看到规律就要敢于尝试,说不定就是正确思路。
整除过后的矩阵通过观察可以看出,里面的数字从1开始到一直到34
那么很容易联想到,1-34代表Flag的1-34位,他们在矩阵所处的位置通过一定方式的计算来得出ASCII码。
先尝试一下1所处的位置,上下左右作为(0,0)坐标的话也会产生不同的结果
竖着看(5,0) (2,0) (5,7) (2,7) 横着看(0,2) (0,5) (7,2) (7,5)
这里利用题目给的一句话,得知Flag是以ASIS_开头的
Find the flag. Flag is in the form of ASIS_X which X is not a MD5 hash
这里考虑到FLAG是经过编码后的,所以列举了一些常用的编码
base64 : QVNJU18= ascii : 65 83 73 83 95 UTF-7 :+AEEAUwBJAFMAXw-
之后就是一顿尝试,确定base64编码和一个正确的原点坐标。
这里还有一个点也是此题比价变态的一个地方。
字母和数组并不是使用ASCII码来表示,而是做了一个位移,做题的时候很容易卡在这里。
按部就班,就可以解出FLAG了。
Base64 : QVNJU19GTEFHM2dxaXpiS0RPWkY5b3hLejZI Flag : ASIS_FLAG3gqizbKDOZF9oxKz6H
Fragmentation(Asis-CTF2013)
这一题也是直接给了一个图片,怎么都是图片。不过这题相对来说比较简单。
解开做这题的关键在于,网站的主页上放了另外一张同样的图片,对比两张图片的不同之处就可以简单地得出Flag。
这里使用两种工具都可以达到目的,ImageMagick 或者 stegSolve
ImageMagick 的话简单实用这样的命令可以比较两个图片的不同之处并输出到另一个图片
compare 1.png 2.png 3.png
得到的图片如下,仔细看的话可以找到Falg
stegSolve是图形化界面操作简单,有一个combine功能支持两个图片的位以各种方式运算,使用sub方式也可达到FLAG
Mysterious Points(Asis-CTF2013)
照例给个图,题目提示说 Inernet is your frient
根据提示,那这张图片去google搜索一下,发现一张类似的图片。
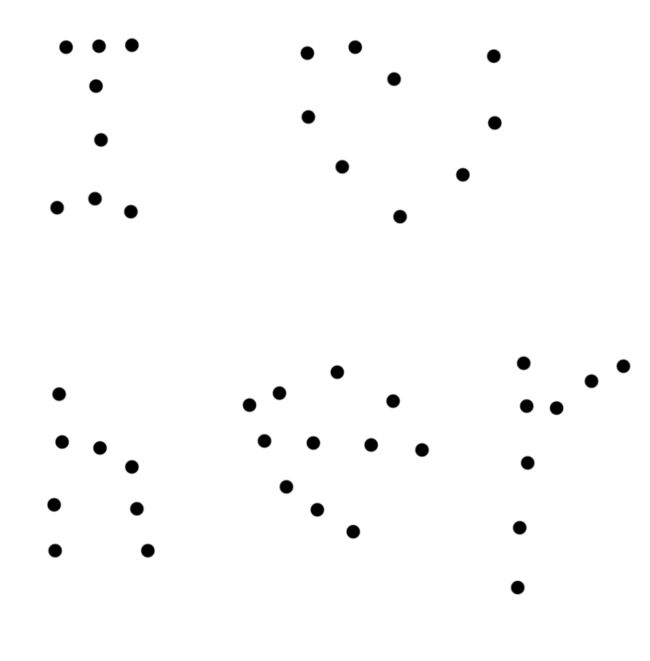
一般情况下,找到了原图剩下的工作就是找不同了,比较出两图中不同的点,发现组成了几个字母
到这里陷入了窘境,I love her这一句,不是Flag,而且再无其他线索。
这里考虑到这个可能作为一个图片位隐写的,KEY,但是加密的方法有很多种,甚至有可能是自定义的简单加密方法,这就蛋疼了。
这里看提示,使用的是这种隐写
http://utilitymill.com/utility/Steganography_Decode源码可以在这个网站看到,不过加密方式就不研究了,解码出来是一个压缩包,但是需要密码。
这里有一点,我解压出的压缩包提示坏损,题解对这方面没有做过多阐述。
后还得知是因为二进制写文件的问题,WINHEX这个软件能很好的解决吧16进制串转成文件的问题
根据作者提示在tiwwer 的账号 fact0real 头像是一个奇怪的二维码
解码后是一串乱七八糟的数字
KioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKgoqIEknbSBmYWN0b3JlYWwsIG1lbWJlciBvZiBBU0lTIENURiB0ZWFtIGFuZCAqCiogbWFuYWdlciBvZiBBRU9JIENURiEgWW91IGNhbiBjb250YWN0IG1lICAgICoKKiB3aXRoIGN0ZkBhc2lzLWN0Zi5pci4JCSAgICAgICAgICAgICAqCiogSSBsb3ZlIEZhdGltYWggOikgICAgICAgICAgICAgICAgICAgICAgICAgICoKKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKioqKgoKbase64解压之
********************************************** * I'm factoreal, member of ASIS CTF team and * * manager of AEOI CTF! You can contact me * * with [email protected]. * * I love Fatimah :) * **********************************************这里通过上面的线索,可以猜测压缩包的密码就是
I love Fatimah :)解压之后即可得到Flag.txt
Misc200( CSAW CTF Qualification Round 2013 )
这题也是给了一个白板的图片,这个图片有一个CRC校验错误,这里png图片的每个数据块末尾都会有一个CRC校验,来确保之前数据块里的内容是否正确
按照题解的思路,这个图片的长度被认为的缩小了,只要在HexEditor里面修改一下,就可以看到下面的Key
这里顺便写了一个读取PNG数据块的脚本,以及验证CRC功能。
from struct import pack
import binascii
import string
crc32 = lambda s: binascii.crc32(s) & 0xFFFFFFFF
chunkname={'IHDR','cHRM','gAMA','sBIT','PLTE','bKGD','hIST',
'tRNS','oFFs','pHYs','sCAL','IDAT','tIME','tEXt','zTXt','fRAc',
'gIFg','gIFt','gIFx','IEND'}
file_object = open('1.png','rb')
text = file_object.read()
for each in chunkname:
pos=0
while (text.find(each,pos+1)!=-1):
pos = text.find(each,pos+1)
if (pos != -1):
print "%s:0x%x" % (each,pos)
if (each=='IHDR'):
print " Length:0x%s" % (binascii.b2a_hex(text[pos-4:pos]))
print " Chunk:0x%s" % (binascii.b2a_hex(text[pos:pos+4]))
print " Width:0x%s" % (binascii.b2a_hex(text[pos+4:pos+8]))
print " Height:0x%s" % (binascii.b2a_hex(text[pos+8:pos+12]))
print " BitDepth:0x%s" % (binascii.b2a_hex(text[pos+12:pos+13]))
print " ColorType:0x%s" % (binascii.b2a_hex(text[pos+13:pos+14]))
print " ComdivssionMethod:0x%s" % (binascii.b2a_hex(text[pos+14:pos+15]))
print " FilterMethod:0x%s" % (binascii.b2a_hex(text[pos+15:pos+16]))
print " InterlaceMethod:0x%s" % (binascii.b2a_hex(text[pos+16:pos+17]))
print " CRC:0x%s" % (binascii.b2a_hex(text[pos+17:pos+21]))
#print (crc32(text[pos:pos+17]))
'''if (each=='IDAT'):
print " Length:0x%s" % (binascii.b2a_hex(text[pos-4:pos]))'''
if (each=='PLET'):
print " Length:0x%s" % (binascii.b2a_hex(text[pos-4:pos]))
'''00 00 00 27 说明调色板数据长为39字节,既13个颜色数
50 4C 54 45 PLTE标识
FF FF 00 颜色0
FF ED 00 颜色1
…… ……
09 00 B2 最后一个颜色,12
5F F5 BB DD CRC校验
'''
if (each=='tEXt'):
print " Length:0x%s" % (binascii.b2a_hex(text[pos-4:pos]))
length = int(binascii.b2a_hex(text[pos-4:pos]),16)
print " Context:%s" % (text[pos+4:pos+length+4])
Misc100( CSAW CTF Qualification Round 2013 )
一上来给了一个空白的图,其实有很多办法,Stegsolve.通过RGB通道可以看到Key。
或者另一种思路使用,使用ImageMigic
之后使用PS颜色选取,选择一下就看到Key了