物联网与嵌入式系统概论-week4-Networking and the Internet-Lesson3: Network Layers and MANETS
This series of articles are the study notes of "An Introduction to Programming the Internet of Things", by Prof.Harris, Department of Computer Science, University of California, Irvine. This article is week 4, Lessen 3: Network Layers and MANETS.
3. Lesson 3 Network Layers and MANETS
3.1 Lecture 3.1 TCP/IP Application Layer
This lecture we'll talk about protocol stack, the Internet standard protocol stack which involves TCP/IP and I'll talk a little bit, give a little bit of an example about an application layer protocol, what that would look like.
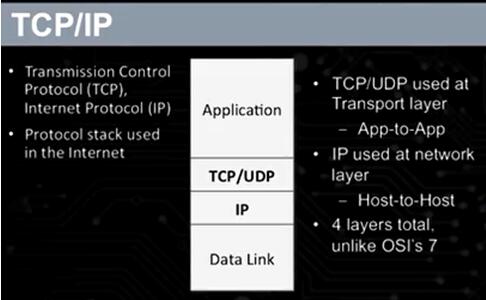
The OSI protocol stack has seven layers, and it’s more complicated. TCP/IP is simplified, this has four layers in it. To player is the application layer, below that is the transport layer where you seeTCP/UDP. That's transport layer. Then below that you see IP which is, that'scalled the network layer, and that's the Internet protocol is there. And then below that is what's called the data link layer. Actually, there's really twolayers merged there, data link and physical. So, the very bottom layer that you don't see there, is merged in is physical, where it actually drives it onto the wires, drives the signal onto the wires or onto the radio.
(1) Top layer: application layer
- Protocols that directly support applications
- Information is application-specific
- Simple Mail Transfer Protocol (SMTP): email
- Hypertext Transfer Protocol (HTTP): web
- Line Printer Daemon (LPD): printing
Application layer example
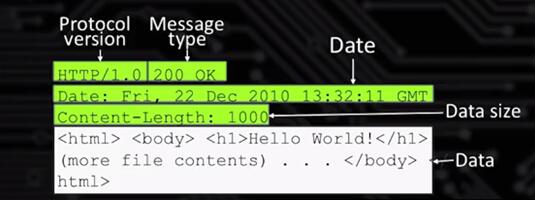
HTTP, hypertext transfer protocol. You've heard of that, HTTP: You've seen this in your URLs, and your addresses on the web, http:// whatever. So, anything that's HTTP, that's web interaction, which is most likely what you, which is most commonly used for.
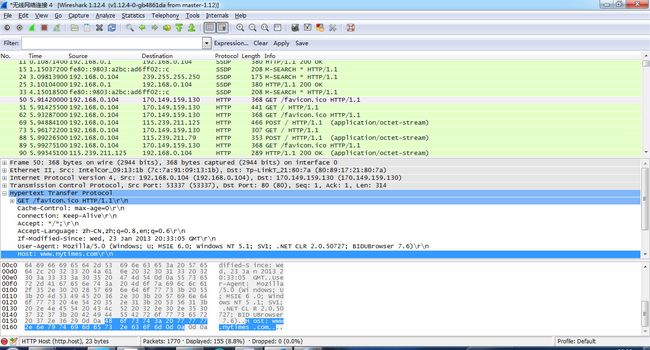
This is HTTP, this is a typical request on the web. Little hard to see, but if you look at the, actually the one we're looking at right here, this is the response message. So, it has several lines. Actually, that code right there has six lines. The top three lines, the ones in green, those are the header. And the bottom lines in white, those are the body, or the data, right, the payload. Whatever term you want to use. So the header are going to be basically those top three lines. Now, the header information, it gives information about the message but it's not the actual content.
HTTP protocol, is application specific. It's for web transfers. It's got header. There's some header lines which may or may not be useful to you, but the data is actually what you want to send.
(2) Second layer: TCP/UDP layer
(3) Third layer: IP layer
(4) Forth layer: Data Link
And actually, if we look at these layers there's code associated with each layer. They're typically library functions. When you write network code, or when you work on network code. You'll be calling application layer library functions. Only top layer, you don't have to worry about the lower layers at all, almost at all. Just the top layer is what you're really going to be dealing with but this whole stack has already been implemented and it will be given to you.
3.2 Lecture 3.2 MANETs
Now we'll talk about MANETs, Mobile Ad Hoc Networks and how they’re used in Internet of Things to connect Internet of Things objects to bigger networks, to the Internet itself. And a we'll talk a little bit about how the code that we're gonna write. That your gonna write inclass, and how it a, you won't directly have to know the details of these thing because you'll be writing generally high level code, but still it's importantfor you to be familiar with these concepts.
3.2.1 Mobile Ad Hoc Network (MANET)
Mobile Ad Hoc Network (MANET)
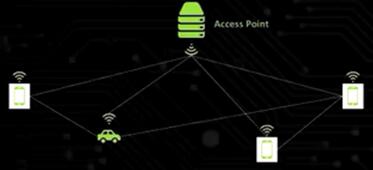
A Mobile Ad Hoc Network, a MANET, is a self-configuring network. By self-configuring we mean that the hosts in the know, in the network configure themselves because they're moving around all the time. So their connections, their connectivity can change across time.
So for instance in this picture, you see a bunch of nodes, you see cell phones, some cell phones, a car, right. Whatever the IoT device is there are a set of them, and then at the top middle is this access point. So this access point is the thing that connects our MANET to the main Internet. Now a MANET could be just independent and not connected to the Internet at all, but most commonly we're going to be connecting to the Internet some way through an access point. Now the access point is typically, usually not mobile.
- Self-configuring network of mobile hosts / routers
- Connected by wireless links
- Often connected to a wired LAN vai an Access Point
- Common for IoT devices
(1) MANET Issues: Power Budget
So that's what a Mobile Ad Hoc Network is. Now, important aspects of MANET, one is a power budget. So you really have to worry about power when you're talking about MANET, because MANETs each one ofthe devices mobile, these IoT devices, they're all mobile They're all running off of batteries and the batteries can run out. So battery power is really important when you're talking about MANET so you change the protocol to save power.
Powerbudget
- Mobile devices are power constrained
- Standard LAN protocols must be modified
- Battery is often the heaviest component
(2) MANET Issues: Data Rate and Security
Data rate
Wireless bandwidth is lower than wired Bandwidth costs power
Compare Bluetooth to Bluetooth low energy. So, Bluetooth is a network protocol, wireless. Bluetooth low energy is another network protocol derived from Bluetooth but is a low energy version of Bluetooth. So Bluetooth, you can send video across Bluetooth. You can get enough data rate sent to transmit video reasonably well. Now Bluetooth low energy, there's no way you get the same data rate. It uses a lot less power but you get a lot lower data rate. So you can't send video. So the fact that you're going to low power restricts you in terms of your data rate and that restricts your functionality in a lot of different ways.
Security
Power is not available for complex security
No encryption, antivirus, etc.
Security, often security costs you in terms of power. So say you wanna do encryption. You wanna take all your messages and encrypt them before sending or something like that takes power. It takes power to do those operations, to encrypt the date, decrypt the data. So security has a cost in terms of power and since your power constraint maybe you can't do as much security as you wanted to do. Alsothings like anti-virus tools. You never see anti-virus tools for cell phones or I think such a thing exists but it's not common. But if you talk about an IoT device, like a watch or something. They don't have antivirus for that because the computational power just isn't there. It doesn't have the extra cycles to be able to do antivirus tasks at the same time as doing its regular tasks. The reason for that is because these IoT devices, and we talked about this before, they're designed to be much more efficient. Meaning a desktop laptop 99.9% of the time, it is being underutilized. Very rarely are you fully utilizing that processor. So, it has extra cycles, extra power, to be spent doing antivirus tasks or something like that. Embedded systems, which IoT devices are they don't have those excess cycles. They use all the power they have, or most of it.
3.2.2 Network Programming in Practice
Now in practice when we do network programming later in specialization. There are levels in the stack. There are different layers in the stack, Application, TCP/UDP and all this. But we don't have to touch those directly in our coding. So, when we use an Arduino or a Raspberry Pi you will be calling library functions at the application layer. So, your code is gonna be at the application layer, almost exclusively at the application layer. So, you call very simple functions which will take care of the details for you.
3.3 Lecture 3.3 Packet Capture Demo
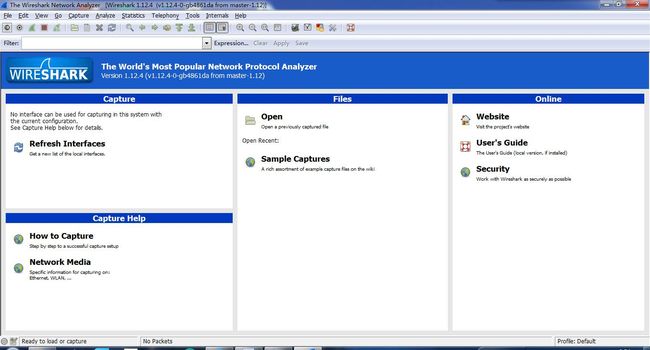
We've been talking about capturing packets on the network interface. I've mentioned it before and now we're going to just try a little bit, let you see how to do it. Actually that will be one of the assignments too, you can give it a try. So we'll start out by starting the WireShark application, which is going to be our packet capture tool.
So WireShark, I have the icon down here onthe bottom. It's this shark fin one. So I'll start that. So network packetprotocol analyzer. So if we look at WireShark, let's pull it up a little bit,first thing it does is, right on the front screen, it gives me a list ofdevices. Interface list here. Let's click on interface list to see theinterfaces.
List the available interface that can be captured.
Now, notice the start button. When I select start, it will start capturing. So I'll hit start, and WireShark should start capturing packets.