- [XDCTF 2015]filemanager
_rev1ve
sql注入数据库安全web安全学习
[XDCTF2015]filemanager我们打开题目,大概看了下存在文件上传功能,并且可以执行重命名和删除文件的操作扫描目录发现有源码泄露我们逐一分析upload.phpquote($path_parts["filename"]);//Fix$path_parts['filename']=addslashes($path_parts['filename']);$sql="select*from
- XDctf-2015 Return-to-dl-resolve
Sadmess
准备知识相关结构体定义typedefstruct{Elf32_Wordst_name;//Symbolname(stringtblindex)Elf32_Addrst_value;//SymbolvalueElf32_Wordst_size;//Symbolsizeunsignedcharst_info;//Symboltypeandbindingunsignedcharst_other;//Sy
- dl_runtime_resolve利用
zs0zrc
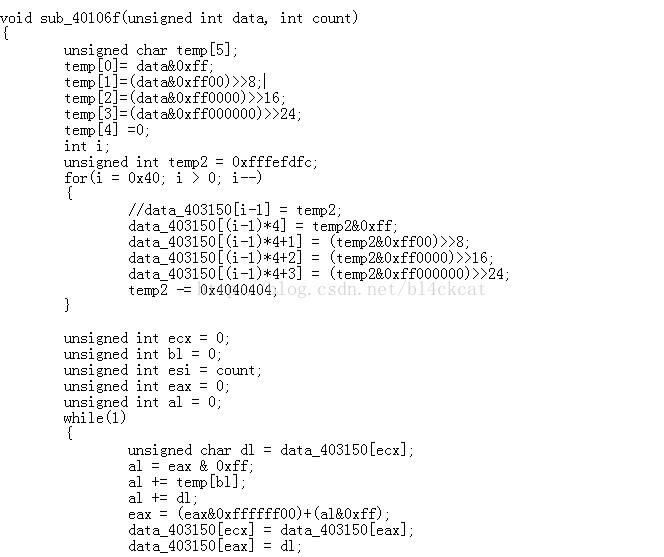
利用_dl_runtime_resolve来解析特定的函数这里以这里以XDCTF2015的pwn200为例基础前置知识请看这篇文章_dl_runtime_resolve利用的步骤主要有5步控制程序的栈转移到我们可以控制的地址控制程序调用_dl_runtime_resolve函数,控制reloc_offset的大小,使reloc项落在我们控制的栈上伪造reloc项中的内容,使sym落在我们的栈中伪造
- [XDCTF]MISC
JasonChiu17
OWASPhttp://ctf.xidian.edu.cn/challenges文件下载下载是一个pdf文件,利用pdf隐写工具:wbStego4.3open打开期间遇到输入密码,之间下一步,第四布创建一个txt来放数据,得到数据:C9t,lnRDRrgerYenY�,wecRnnotdedlcRte,wecRnnotconYecrRte,wecRnnot0RDDowt0lYgro9nd.T0eb
- [XDCTF](Stego)Base64
王一航
Base64隐写:可以参考这篇文章https://www.tr0y.wang/2017/06/14/Base64steg/https://github.com/ctfs/write-ups-2016/tree/master/open-ctf-2016/steganography/ultra-encryption-100给出本题的脚本:https://gist.github.com/WangYiha
- 记XDCTF的misc之旅---base64隐写
dizhan1070
bWFpbigpe2ludCBpLG5bXT17KCgoMSA8PDEpPDwgKDE8PDEpPDwoMTw8Cm==ICAgICAgIDEpPDwoMTw8KDE+PjEpKSkrKCgxPDwxKTw8KDE8PDEpKSksKCgoMQp=ICAgICAgIDw8ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAxKQq=ICAgICAgIDw8
- 好好说话之ret2_dl_runtime_resolve
hollk
pwn
当初毕业论文就写了一万五千字,没想到一篇博客三万两千字我吐了。由于内容比较详细,无法避免有些知识点会忘记,可以通过目录翻阅忘记的内容编写不易,如果能够帮助到你,希望能够点赞收藏加关注哦Thanks♪(・ω・)ノ题目出自CTFWiki中的XDCTF2015pwn200例题,可以在ctf-wiki/ctf-challenges中下载题目。感谢在学习过程中帮助到我的大佬们:r0se、NoOne、yich
- XDCTF PWN300&400 Writeup
zh_explorer
pwn没事撸题
打了2天的XDCTF,被Reverse的题目教做人了。Sad(T.T)到是pwn的题目基本打通了,除了最简单的pwn100(T.T)pwn300和pwn400比较简单,所以writeup我就放在一起了。PWN300做完PWN300,感觉不会再有女朋友了T.T就不吐槽猥琐的出题人了,直接开始分析程序。checksec后发现竟然没有开nx,直接shellcode先准备好,放在一边待命。按照国际管理,先
- 谈一谈php://filter的妙用
涙笑
感觉这篇文章写得相当不错,忍不住转载收藏转自:https://www.leavesongs.com/PENETRATION/php-filter-magic.htmlphp://filter是PHP中独有的协议,利用这个协议可以创造很多“妙用”,本文说几个有意思的点,剩下的大家自己下去体会。本来本文的思路我上半年就准备拿来做XDCTF2016的题目的,没想到被三个白帽的一题抢先用了,我也就只好提前
- (攻防世界)(XDCTF-2015)pwn200
PLpa、
这一题和JarvisOJ中的level4简直不要太像了,只是改变了几个地址,改变了溢出点。既然前面已经讲解了,这里就不再重复讲了,详细解法请看链接:https://blog.csdn.net/qq_43986365/article/details/95081996但是这次使用pop_pop_pop_ret将两个合并为一个。完整exp如下:#!/usr/bin/envpythonfrompwnimp
- XDCTF2015 PWN200
qq_33528164
PWN
XDCTF2015PWN200一.源码(自己敲出来的)#include#include#includeintvuln(){charbuf[80];setbuf(stdin,buf);returnread(0,buf,256);}intmain(intargc,char**argv){char*welcome="WelcometoXDCTF2015~!\n";setbuf(stdout,welcom
- CTF--2015中国西安电子科技大学XDCTF网络安全大赛之pwn
5t4rk
技术文章学习笔记安全札记反汇编二进制逆向工程
writeup0x01基本信息本人初学,可能本题解答对大神来说,有些繁琐。(大神可以忽略飘过)。分享在此,方便自己,也方便他人。文件:xd_jwxt大小:8276字节修改时间:2016年7月13日,16:22:24MD5:07BE390A9328A365549A27D400462B59SHA1:C0175B97E12670373E793F5633C51637B9C809E0CRC32:37CFC2
- pwn-200(XDCTF-2015)--write up
ATFWUS
CTF-PWN#攻防世界-pwn--WriteUpCTFpwn栈溢出DynELF漏洞利用
文件下载地址:链接:https://pan.baidu.com/s/1W-bn57DPwr0GZlOsAl2enQ提取码:z3sy目录0x01.分析checksec:查看源码:分析源码:漏洞利用思路:漏洞利用:0x02.exp这题又遇到本地失败了,远程成功了,本地在开启交互后,输入指令后什么都没有。。。。0x01.分析checksec:32位程序,只开启NX。查看源码:分析源码:从源码可以得出,主
- XDCTF-2015 pwn-200 backdoorctf-2015 echo
pipixia233333
栈溢出堆溢出
XDCTF-2015pwn-200简单的泄露基址这里就不多讲了#!/usr/bin/python2#-*-coding:utf-8-*-frompwnimport*context.log_level="debug"#io=remote("111.198.29.45",32529)io=process("./pwn")elf=ELF("./pwn")libc=ELF("./libc6_2.23_38
- [XDCTF](Web)Upload
王一航
首先题目存在文件包含漏洞,可以通过:php://filter/convert.base64-encode/resource=index.php读取到目标服务器源码例如://page.phperror!";}else{include($file);}}?>//upload.php可以看到upload.php的上传的规则:将上传的文件中非acgtACGT的所有字符替换为空然后再保存那么也就是说我们上传
- BUUCTF:[XDCTF 2015]filemanager
m0c1nu7
CTF_WEB_WriteupXDCTF2015filemanagerBuuCTF
题目地址:https://buuoj.cn/challenges#[XDCTF%202015]filemanager首先网站目录下/www.tar.gz是隐藏源码文件xdctf.sql:数据库表结构common.inc.php对所有传入的参数进行了addslashes()转义upload.php上传的文件名经过:$file[‘name’]->pathinfo()–>$path_parts["fil
- 32位下利用_dl_runtim_resolve函数
zs0zrc
pwn
利用_dl_runtime_resolve来解析特定的函数这里以这里以XDCTF2015的pwn200为例基础前置知识请看这篇文章_dl_runtime_resolve利用的步骤主要有5步控制程序的栈转移到我们可以控制的地址控制程序调用_dl_runtime_resolve函数,控制reloc_offset的大小,使reloc项落在我们控制的栈上伪造reloc项中的内容,使sym落在我们的栈中伪造
- CTF--2016XDCTF全国网络安全大赛之reverse5
5t4rk
反汇编二进制逆向工程技术文章
0x01题目介绍题目名称reverse5题目描述File:reverse5.exeSize:121344bytesFileVersion:1.0.0.1Modified:Friday,September30,2016,01:24:54MD5:01C16460135B1BA4BCA48E3AB0173A17SHA1:06ACD42197A5F52A9CCFEC0B12EE52F647B1E71DCR
- CTF--2016XDCTF全国网络安全大赛之reverse2
5t4rk
技术文章二进制反汇编逆向工程学习笔记网络安全逆向二进制安全测试XDCTF
0x01题目介绍题目名称reverse2题目描述File:XDCTF2.exeSize:195584bytesFileVersion:1.0.0.1Modified:Tuesday,March07,2017,00:11:41MD5:1B0EA0BD4B8DA116C7D590F05BE6692ASHA1:81174B9D39D467308818B0BB0C99D427ED80EB6CCRC32:4
- [XDCTF2016](pwn)pwn200
王一航
简介:2016西电CTF线上赛pwn200分析:首先该题目没有开启NX保护,也就是有可能需要将shellcode写入到栈上该题目需要进行两次溢出1.第一次溢出可以leak出main函数的栈底地址,这样可以得到我们写入的shellcode的地址2.第二次溢出可以覆盖strcpy的dest参数指针,达到任意地址写的目的Paste_Image.pngPaste_Image.pngPaste_Image.
- 20171001小记
大白兔_X
没错,今天就是大家盼星星盼月亮的国庆节了。不知道大家出行玩的怎么样了?我在这里就祝各位国庆快乐。我一个人在宿舍里孤独学习。吃饭也就随便吃点。果然一个人就很随便了。中午睡觉起来都没刷牙洗脸,就这样随随便便的出去买饭吃饭学习,无奈。今天早上9点有XDCTF比赛,所以我读完英语,送完小谋子出门,就开始打比赛了。好久没有解题了,再加上之前重装过系统,原来用的工具和收藏过的神站都没有了,当然最重要的是我的手
- 20171002小记
大白兔_X
今天感觉没干什么就到了要睡觉的时间了。今晚9点XDCTF结束比赛,而我只是参与了一小会,感觉有些遗憾。平时说自己后悔没参加比赛,真正比赛来临时我却是如此随便应付一下,发现自己都不会写,就放弃,所以这导致我以后就没有什么参赛记录,刚刚进去就放弃了,还谈什么拿奖。真想打自己两巴掌。怂包!今天还是读了接近3小时的英语,一遍比一遍有进步,虽然今天还是没有按照我自己的任务达标,但听力进入耳中一次比一次清晰,
- [XDCTF](Misc)ntfs流
王一航
题目链接:hint:ntfs流文件下载地址分析:下载题目提供文件:Paste_Image.png发现是一个RAR文件,打开后发现其中有一个大小只有Paste_Image.png注意到压缩包和源文件的大小有着非常大的差距,一个四百多K,另一个只有十几字节打开这个文本文件得到:Paste_Image.png经过主办方的提示:NTFS流通过百度得到一个文章:利用NTFS流隐藏文件将其解压缩后进行手动提起
- XMAN结营攻防赛总结
王一航
排行榜截图QQ图片20170821103303.jpgQQ图片20170821103307.jpg总结:第一次打线下赛是在16年10月份的时候的XDCTF,说实话当时线下赛确实打得挺懵逼的当时真的是几乎啥也不懂,不懂运维,不懂代码审计完全没有任何经验,完全被吊打,我们队伍总共三个人,两个学长带我,非常感谢他们俩对我的照顾当时每个队伍需要维护一个Linux服务器,一个Windows服务器所有队伍两台
- [XDCTF-2017-Final] 总结
ShadowGlint
我男神@美男全程带飞~,主要写一写感想和awd基本流程总结1.上来一般会有30min防御,先备份整站以及各种题。Linux命令:[root@linux~]#tar[-cxtzjvfpPN]文件与目录....将整个/etc目录下的文件全部打包成为/tmp/etc.tar:[root@linux~]#tar-zcvf/tmp/etc.tar.gz/etcdatabase.sql也可winscp连接,整
- [XDCTF](MISC)OWASP
王一航
题目链接:http://ctf.xidian.edu.cn/challenges(由于官网在比赛结束后已经关闭,因此将题目文件发到网盘中)文件下载地址分析:下载题目提供文件,格式为:pdf,打开查看,并没有发现异常.考虑到是pdf隐写,利用搜索引擎找到PDF隐写工具:wbStego4.3open使用该工具将该pdf解密,解密时需要输入密码,是用空的弱密码成功解出隐写数据.Paste_Image.p
- 奇葩webshell技巧
hackjason
www.hackjason.com前段时间看XDCTF的一道web题,发现了一种很奇特的构造webshell的方法。Base64一句话木马题目的大概意思就是允许包含,但限制了使用的字符,仅允许使用'acgtACGT'这8个字符。emmm,就像我第一次看到一样,感觉这根本不能构造webshell嘛,这要能弄出来,我直播吃……冰激凌。不废话了,原理如下:先大致讲一下,任何由{A-Z|a-z|0-9|+
- [XDCTF-2017-Final] 经验总结
王一航
本文首发地址:https://xianzhi.aliyun.com/forum/先知技术社区独家发表本文,如需要转载,请先联系先知技术社区授权;未经授权请勿转载。先知技术社区投稿邮箱:
[email protected]今天早上看到沐师傅在知乎上的回答,感觉自己还是有点太为了比赛而比赛了以后还是得多联系实际的网络攻防对抗写一篇小总结吧,记录一些小经验和一些比较有意思
- 栈溢出高级ROP
小白King
ret2_dl_runtime_resolve前置知识:*32位情况下如果return的函数不再使用,便直re+AAAA+参数,如果需要连续执行的话,就需要用到ROP技术去维持栈平衡(主动清空栈),得以继续运行下面直接刚一道题来看看:XDCTF2015的pwn题:bof查看保护措施,没有栈溢出保护,只有堆栈不可执行保护,爆破出栈大小为112,这题分为好几步骤:stage1:先实现write函数的调
- 浅谈php://filter的妙用
PHITHON
php://filter是PHP中独有的协议,利用这个协议可以创造很多“妙用”,本文说几个有意思的点,剩下的大家自己下去体会。本来本文的思路我上半年就准备拿来做XDCTF2016的题目的,没想到被三个白帽的一题抢先用了,我也就只好提前分享一下。XXE中的使用php://filter之前最常出镜的地方是XXE。由于XXE漏洞的特殊性,我们在读取HTML、PHP等文件时可能会抛出此类错误parsere
- 插入表主键冲突做更新
a-john
有以下场景:
用户下了一个订单,订单内的内容较多,且来自多表,首次下单的时候,内容可能会不全(部分内容不是必须,出现有些表根本就没有没有该订单的值)。在以后更改订单时,有些内容会更改,有些内容会新增。
问题:
如果在sql语句中执行update操作,在没有数据的表中会出错。如果在逻辑代码中先做查询,查询结果有做更新,没有做插入,这样会将代码复杂化。
解决:
mysql中提供了一个sql语
- Android xml资源文件中@、@android:type、@*、?、@+含义和区别
Cb123456
@+@?@*
一.@代表引用资源
1.引用自定义资源。格式:@[package:]type/name
android:text="@string/hello"
2.引用系统资源。格式:@android:type/name
android:textColor="@android:color/opaque_red"
- 数据结构的基本介绍
天子之骄
数据结构散列表树、图线性结构价格标签
数据结构的基本介绍
数据结构就是数据的组织形式,用一种提前设计好的框架去存取数据,以便更方便,高效的对数据进行增删查改。正确选择合适的数据结构,对软件程序的高效执行的影响作用不亚于算法的设计。此外,在计算机系统中数据结构的作用也是非同小可。例如常常在编程语言中听到的栈,堆等,就是经典的数据结构。
经典的数据结构大致如下:
一:线性数据结构
(1):列表
a
- 通过二维码开放平台的API快速生成二维码
一炮送你回车库
api
现在很多网站都有通过扫二维码用手机连接的功能,联图网(http://www.liantu.com/pingtai/)的二维码开放平台开放了一个生成二维码图片的Api,挺方便使用的。闲着无聊,写了个前台快速生成二维码的方法。
html代码如下:(二维码将生成在这div下)
? 1
&nbs
- ImageIO读取一张图片改变大小
3213213333332132
javaIOimageBufferedImage
package com.demo;
import java.awt.image.BufferedImage;
import java.io.File;
import java.io.IOException;
import javax.imageio.ImageIO;
/**
* @Description 读取一张图片改变大小
* @author FuJianyon
- myeclipse集成svn(一针见血)
7454103
eclipseSVNMyEclipse
&n
- 装箱与拆箱----autoboxing和unboxing
darkranger
J2SE
4.2 自动装箱和拆箱
基本数据(Primitive)类型的自动装箱(autoboxing)、拆箱(unboxing)是自J2SE 5.0开始提供的功能。虽然为您打包基本数据类型提供了方便,但提供方便的同时表示隐藏了细节,建议在能够区分基本数据类型与对象的差别时再使用。
4.2.1 autoboxing和unboxing
在Java中,所有要处理的东西几乎都是对象(Object)
- ajax传统的方式制作ajax
aijuans
Ajax
//这是前台的代码
<%@ page language="java" import="java.util.*" pageEncoding="UTF-8"%> <% String path = request.getContextPath(); String basePath = request.getScheme()+
- 只用jre的eclipse是怎么编译java源文件的?
avords
javaeclipsejdktomcat
eclipse只需要jre就可以运行开发java程序了,也能自动 编译java源代码,但是jre不是java的运行环境么,难道jre中也带有编译工具? 还是eclipse自己实现的?谁能给解释一下呢问题补充:假设系统中没有安装jdk or jre,只在eclipse的目录中有一个jre,那么eclipse会采用该jre,问题是eclipse照样可以编译java源文件,为什么呢?
&nb
- 前端模块化
bee1314
模块化
背景: 前端JavaScript模块化,其实已经不是什么新鲜事了。但是很多的项目还没有真正的使用起来,还处于刀耕火种的野蛮生长阶段。 JavaScript一直缺乏有效的包管理机制,造成了大量的全局变量,大量的方法冲突。我们多么渴望有天能像Java(import),Python (import),Ruby(require)那样写代码。在没有包管理机制的年代,我们是怎么避免所
- 处理百万级以上的数据处理
bijian1013
oraclesql数据库大数据查询
一.处理百万级以上的数据提高查询速度的方法: 1.应尽量避免在 where 子句中使用!=或<>操作符,否则将引擎放弃使用索引而进行全表扫描。
2.对查询进行优化,应尽量避免全表扫描,首先应考虑在 where 及 o
- mac 卸载 java 1.7 或更高版本
征客丶
javaOS
卸载 java 1.7 或更高
sudo rm -rf /Library/Internet\ Plug-Ins/JavaAppletPlugin.plugin
成功执行此命令后,还可以执行 java 与 javac 命令
sudo rm -rf /Library/PreferencePanes/JavaControlPanel.prefPane
成功执行此命令后,还可以执行 java
- 【Spark六十一】Spark Streaming结合Flume、Kafka进行日志分析
bit1129
Stream
第一步,Flume和Kakfa对接,Flume抓取日志,写到Kafka中
第二部,Spark Streaming读取Kafka中的数据,进行实时分析
本文首先使用Kakfa自带的消息处理(脚本)来获取消息,走通Flume和Kafka的对接 1. Flume配置
1. 下载Flume和Kafka集成的插件,下载地址:https://github.com/beyondj2ee/f
- Erlang vs TNSDL
bookjovi
erlang
TNSDL是Nokia内部用于开发电信交换软件的私有语言,是在SDL语言的基础上加以修改而成,TNSDL需翻译成C语言得以编译执行,TNSDL语言中实现了异步并行的特点,当然要完整实现异步并行还需要运行时动态库的支持,异步并行类似于Erlang的process(轻量级进程),TNSDL中则称之为hand,Erlang是基于vm(beam)开发,
- 非常希望有一个预防疲劳的java软件, 预防过劳死和眼睛疲劳,大家一起努力搞一个
ljy325
企业应用
非常希望有一个预防疲劳的java软件,我看新闻和网站,国防科技大学的科学家累死了,太疲劳,老是加班,不休息,经常吃药,吃药根本就没用,根本原因是疲劳过度。我以前做java,那会公司垃圾,老想赶快学习到东西跳槽离开,搞得超负荷,不明理。深圳做软件开发经常累死人,总有不明理的人,有个软件提醒限制很好,可以挽救很多人的生命。
相关新闻:
(1)IT行业成五大疾病重灾区:过劳死平均37.9岁
- 读《研磨设计模式》-代码笔记-原型模式
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
/**
* Effective Java 建议使用copy constructor or copy factory来代替clone()方法:
* 1.public Product copy(Product p){}
* 2.publi
- 配置管理---svn工具之权限配置
chenyu19891124
SVN
今天花了大半天的功夫,终于弄懂svn权限配置。下面是今天收获的战绩。
安装完svn后就是在svn中建立版本库,比如我本地的是版本库路径是C:\Repositories\pepos。pepos是我的版本库。在pepos的目录结构
pepos
component
webapps
在conf里面的auth里赋予的权限配置为
[groups]
- 浅谈程序员的数学修养
comsci
设计模式编程算法面试招聘
浅谈程序员的数学修养
- 批量执行 bulk collect与forall用法
daizj
oraclesqlbulk collectforall
BULK COLLECT 子句会批量检索结果,即一次性将结果集绑定到一个集合变量中,并从SQL引擎发送到PL/SQL引擎。通常可以在SELECT INTO、
FETCH INTO以及RETURNING INTO子句中使用BULK COLLECT。本文将逐一描述BULK COLLECT在这几种情形下的用法。
有关FORALL语句的用法请参考:批量SQL之 F
- Linux下使用rsync最快速删除海量文件的方法
dongwei_6688
OS
1、先安装rsync:yum install rsync
2、建立一个空的文件夹:mkdir /tmp/test
3、用rsync删除目标目录:rsync --delete-before -a -H -v --progress --stats /tmp/test/ log/这样我们要删除的log目录就会被清空了,删除的速度会非常快。rsync实际上用的是替换原理,处理数十万个文件也是秒删。
- Yii CModel中rules验证规格
dcj3sjt126com
rulesyiivalidate
Yii cValidator主要用法分析:
yii验证rulesit 分类: Yii yii的rules验证 cValidator主要属性 attributes ,builtInValidators,enableClientValidation,message,on,safe,skipOnError
- 基于vagrant的redis主从实验
dcj3sjt126com
vagrant
平台: Mac
工具: Vagrant
系统: Centos6.5
实验目的: Redis主从
实现思路
制作一个基于sentos6.5, 已经安装好reids的box, 添加一个脚本配置从机, 然后作为后面主机从机的基础box
制作sentos6.5+redis的box
mkdir vagrant_redis
cd vagrant_
- Memcached(二)、Centos安装Memcached服务器
frank1234
centosmemcached
一、安装gcc
rpm和yum安装memcached服务器连接没有找到,所以我使用的是make的方式安装,由于make依赖于gcc,所以要先安装gcc
开始安装,命令如下,[color=red][b]顺序一定不能出错[/b][/color]:
建议可以先切换到root用户,不然可能会遇到权限问题:su root 输入密码......
rpm -ivh kernel-head
- Remove Duplicates from Sorted List
hcx2013
remove
Given a sorted linked list, delete all duplicates such that each element appear only once.
For example,Given 1->1->2, return 1->2.Given 1->1->2->3->3, return&
- Spring4新特性——JSR310日期时间API的支持
jinnianshilongnian
spring4
Spring4新特性——泛型限定式依赖注入
Spring4新特性——核心容器的其他改进
Spring4新特性——Web开发的增强
Spring4新特性——集成Bean Validation 1.1(JSR-349)到SpringMVC
Spring4新特性——Groovy Bean定义DSL
Spring4新特性——更好的Java泛型操作API
Spring4新
- 浅谈enum与单例设计模式
247687009
java单例
在JDK1.5之前的单例实现方式有两种(懒汉式和饿汉式并无设计上的区别故看做一种),两者同是私有构
造器,导出静态成员变量,以便调用者访问。
第一种
package singleton;
public class Singleton {
//导出全局成员
public final static Singleton INSTANCE = new S
- 使用switch条件语句需要注意的几点
openwrt
cbreakswitch
1. 当满足条件的case中没有break,程序将依次执行其后的每种条件(包括default)直到遇到break跳出
int main()
{
int n = 1;
switch(n) {
case 1:
printf("--1--\n");
default:
printf("defa
- 配置Spring Mybatis JUnit测试环境的应用上下文
schnell18
springmybatisJUnit
Spring-test模块中的应用上下文和web及spring boot的有很大差异。主要试下来差异有:
单元测试的app context不支持从外部properties文件注入属性
@Value注解不能解析带通配符的路径字符串
解决第一个问题可以配置一个PropertyPlaceholderConfigurer的bean。
第二个问题的具体实例是:
- Java 定时任务总结一
tuoni
javaspringtimerquartztimertask
Java定时任务总结 一.从技术上分类大概分为以下三种方式: 1.Java自带的java.util.Timer类,这个类允许你调度一个java.util.TimerTask任务; 说明: java.util.Timer定时器,实际上是个线程,定时执行TimerTask类 &
- 一种防止用户生成内容站点出现商业广告以及非法有害等垃圾信息的方法
yangshangchuan
rank相似度计算文本相似度词袋模型余弦相似度
本文描述了一种在ITEYE博客频道上面出现的新型的商业广告形式及其应对方法,对于其他的用户生成内容站点类型也具有同样的适用性。
最近在ITEYE博客频道上面出现了一种新型的商业广告形式,方法如下:
1、注册多个账号(一般10个以上)。
2、从多个账号中选择一个账号,发表1-2篇博文