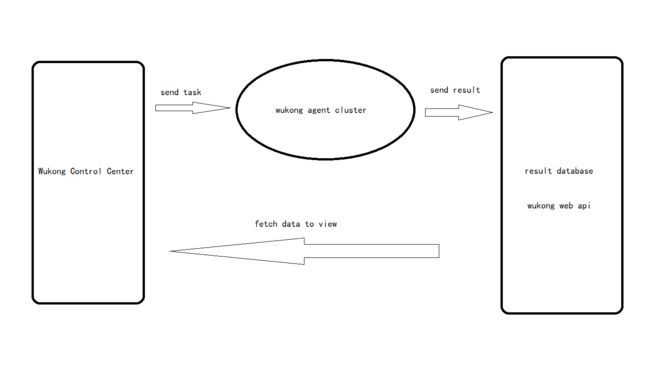
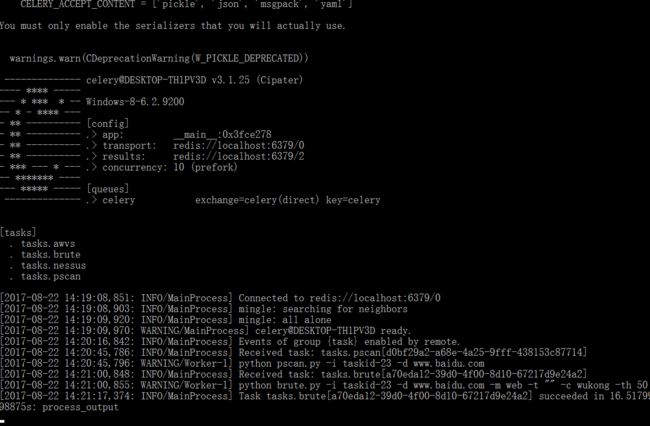
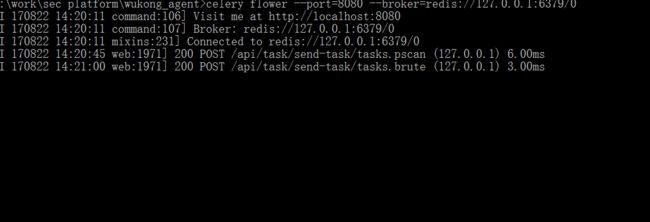
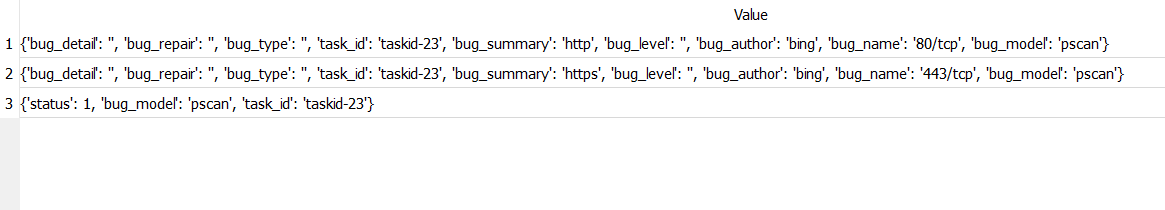
- 利用Requests Toolkit轻松完成HTTP请求
nseejrukjhad
http网络协议网络python
RequestsToolkit的力量:轻松构建HTTP请求Agent在现代软件开发中,API请求是与外部服务交互的核心。RequestsToolkit提供了一种便捷的方式,帮助开发者构建自动化的HTTP请求Agent。本文旨在详细介绍RequestsToolkit的设置、使用和潜在挑战。引言RequestsToolkit是一个强大的工具包,可用于构建执行HTTP请求的智能代理。这对于想要自动化与外
- 【大模型应用开发 动手做AI Agent】第一轮行动:工具执行搜索
AI大模型应用之禅
计算科学神经计算深度学习神经网络大数据人工智能大型语言模型AIAGILLMJavaPython架构设计AgentRPA
【大模型应用开发动手做AIAgent】第一轮行动:工具执行搜索作者:禅与计算机程序设计艺术/ZenandtheArtofComputerProgramming1.背景介绍1.1问题的由来随着人工智能技术的飞速发展,大模型应用开发已经成为当下热门的研究方向。AIAgent作为人工智能领域的一个重要分支,旨在模拟人类智能行为,实现智能决策和自主行动。在AIAgent的构建过程中,工具执行搜索是至关重要
- ansible的安装、使用
ytym00
简介高度模块化,调用特定的模块,完成特定的任务,基于Yaml,来完成批量任务的模板化,来支持playbook。基于Python语言实现,主要使用Paramiko、PyYAML和JinJa2三个关键模块,部署简单(agentless),主从模式,支持自定义模块,支持playbook,幂等性:允许重复执行N次,没有变化时,只会执行第一次。特点:1、Configuration(cfengine,chef
- [移动端自动化] AppAgent介绍
大卫软件测试
自动化
AUITestAgentAUITestAgent/README_zh.mdatmain·bz-lab/AUITestAgent(github.com)1/MobileAgentX-PLUG/MobileAgent:Mobile-Agent:ThePowerfulMobileDeviceOperationAssistantFamily(github.com)2/AppAgentAppAgent/RE
- 【Python爬虫】百度百科词条内容
PokiFighting
数据处理python爬虫开发语言
词条内容我这里随便选取了一个链接,用的是FBI的词条importurllib.requestimporturllib.parsefromlxmlimportetreedefquery(url):headers={'user-agent':'Mozilla/5.0(WindowsNT6.1;Win64;x64)AppleWebKit/537.36(KHTML,likeGecko)Chrome/80.
- 探索未来,大规模分布式深度强化学习——深入解析IMPALA架构
汤萌妮Margaret
探索未来,大规模分布式深度强化学习——深入解析IMPALA架构scalable_agent项目地址:https://gitcode.com/gh_mirrors/sc/scalable_agent在当今的人工智能研究前沿,深度强化学习(DRL)因其在复杂任务中的卓越表现而备受瞩目。本文要介绍的是一个开源于GitHub的重量级项目:“ScalableDistributedDeep-RLwithImp
- Python——俄罗斯方块
星和月
pythonpygame开发语言
俄罗斯方块游戏是一款经典的益智游戏,通常使用编程语言Python来实现。下面是一个简单的俄罗斯方块游戏的示例代码:importpygameimportrandom#定义颜色BLACK=(0,0,0)WHITE=(255,255,255)RED=(255,0,0)GREEN=(0,255,0)BLUE=(0,0,255)CYAN=(0,255,255)MAGENTA=(255,0,255)YELLO
- 2022-01-03 day62 pipaline流水线作业
zhaocheng690
今日作业:1.pipeline实现流程:拉取代码-->编译-->部署测试-->发送测试通知-->确认是否部署-->部署服务-->发送部署结果通知pipeline{agentanyparameters{gitParameterbranch:'',branchFilter:'.*',defaultValue:'v1.0',description:'请选择要发布的版本:',name:'git_versi
- Jmeter性能测试六--Jmeter录制+服务器监控
鱼排也爱小白菜
jmeter
一、排除模式填写测试计划右键添加-->非测试原件-->HTTP代理服务器端口设置:不能填本机已存在的端口排除模式填写:(?i).*\.(bmp|css|js|gif|ico|jpe?g|png|swf|woff|woff2|html|htm).*点击启动录制结果二、服务器脚本运行1.上传脚本包后需要先解压unzipServerAgent-2.2.3.zipcdServerAgent-2.2.3.z
- Python 抓取图片
weixin_30477797
python
#coding:utf-8frombs4importBeautifulSoupimportrequestsimporturllibuser_agent='Mozilla/5.0(WindowsNT6.1;Win64;x64)AppleWebKit/537.36(KHTML,likeGecko)Chrome/63.0.3239.132Safari/537.36'headers={'User-Agen
- 使用requests-html 遇见的问题
柒柒钏
爬虫
使用requests-html遇见的问题1、解决无头浏览器问题(可能有反爬,所以需要使用模拟浏览器)修改requests_html源码,如图所示,添加红框里的代码示例爬虫代码:fromrequests_htmlimportHTMLSessionsession=HTMLSession()headers={"User-Agent":"Mozilla/5.0(WindowsNT10.0;WOW64)Ap
- RPM安装的程序在哪里?
年薪丰厚
linux服务器centosrpm
假如我要安装zabbix的客户端zabbix-agent2,刚好我在网上下载到了他的安装包zabbix-agent2-5.0.42-1.el7.x86_64.rpm。这个安装包zabbix-agent2-5.0.42-1.el7.x86_64.rpm就是rpm文件。如果我用rpm方式去安装这个rpm文件,机器首先会检查当下这个环境里面有没有zabbix-agent2所需要的依赖。举个例子,yumi
- zabbix的组件
BK_小小关
各种服务运维linuxcentoszabbix
组件说明1)zabbixserver:负责接收agent发送的报告信息的核心组件,所有配置、统计数据及操作数据都由它组织进行;2)databasestorage:专用于存储所有配置信息,以及由zabbix.收集的数据;e3)webinterface:zabbix的GUI接口;e4)proxy:可选组件,常用于监控节点很多的分布式环境中,代理server收集部分数据转发到server,可以减轻ser
- sqlserver常用的sql命令
一心只为学
sqlserversql数据库
查看当前用户查看当前用户selectsystem_user检查SQLAgent是否开启IFEXISTS(SELECTTOP11FROMsys.sysprocessesWHEREprogram_name='SQLAgent-GenericRefresher')SELECT'Running'ELSESELECT'NotRunning'查看是否做了镜像selecta.database_id,a.name
- [晕事]今天做了件晕事44 wireshark 首选项IPv4:Reassemble Fragented IPv4 datagrams
mzhan017
网络云平台运维wireshark测试工具分片假象
不知不觉,已经来到了晕事系列的第四十四个晕事。今天办的晕事和Wireshark查看网络包相关。说,在Wireshark的编辑-首选项协议里的IPv4协议,有一个参数设置是:ReassembleFragentedIPv4datagrams。这个参数的含义是指定Wireshark,在打开pcap文件进行解析的时候要:先解包;还是先组装分片包,再解包。如果是选择了这个选项,就代表,分片重组之后再进行解析
- Agent Q: 实现自主网页代理的提升
新加坡内哥谈技术
人工智能语言模型自然语言处理
每周跟踪AI热点新闻动向和震撼发展想要探索生成式人工智能的前沿进展吗?订阅我们的简报,深入解析最新的技术突破、实际应用案例和未来的趋势。与全球数同行一同,从行业内部的深度分析和实用指南中受益。不要错过这个机会,成为AI领域的领跑者。点击订阅,与未来同行!订阅:https://rengongzhineng.io/近年来,大型语言模型(LLMs)的能力在自然语言处理和理解领域取得了显著进展,达到了多个
- 洞悉LangChain:LangChain工程化设计,从API到智能Agent的全面探索
汀、人工智能
AIAgentLLM技术汇总langchain人工智能自然语言处理大模型AgentLangGraphAIAgent
洞悉LangChain:LangChain工程化设计,从API到智能Agent的全面探索1.LangChain简介LangChain是2022年10月底,由哈佛大学的HarrisonChase发起的基于开源大语言模型的AI工程开发框架。当然也可以问一下AI:通义千问2.5:LangChain是一个开源框架,专注于简化开发者利用大型语言模型(LLM)创建应用程序的过程。这些大型语言模型,如GPT-3
- jmeter远程启动配置
雪霁_
性能测试压力测试jmeterlinux
前提条件保持windows端、linux端jdk版本一致配置linux压力机(配置agent)修改文件jmeter.properties,打开注释server_port开启端口(默认1099);打开注释,修改server.rmi.ssl.disable=false为true运行命令,./jmeter-server-Djava.rmi.server.hostname=10.0.0.48(ip为lin
- 基于ReAct提示词框架的大语言模型Agent原理
会写代码的孙悟空
chatGPT语言模型chatgpt人工智能智能体agent
简介论文出自ReAct:SynergizingReasoningandActinginLanguageModelsReAct=reason+actreason:推理act:行动先看reason和act都是哪种模式思维链技术(ChainofThought)是一种用于提高大型语言模型(如GPT)解决问题能力的技巧。这种技术的核心思想是将复杂的问题分解成一系列更简单的步骤,然后逐步解决这些步骤,最终达到
- 华为云全栈可观测平台(APM)8月新功能特性
华为云PaaS服务小智
华为云
华为云应用性能管理服务(ApplicationPerformanceManagement,简称APM)帮助运维人员快速发现应用的性能瓶颈,以及故障根源的快速定位,为用户体验保驾护航。您无需修改代码,只需为应用安装一个APMAgent,就能够对该应用进行全方位监控,帮助您快速定位出错接口和慢接口、重现调用参数、发现系统瓶颈,从而大幅提升线上问题诊断的效率。8月APM更新了3大新特性,一起来看看吧!(
- 大模型LLM面试常见算法题-包括Attention和Transformer常见面试题
剑圣土豆
算法面试大模型学习自然语言处理transformer算法nlp自然语言处理面试深度学习人工智能
大模型:位置编码有哪些?介绍LoRA与QLoRARAG和微调的区别是什么?哪些因素会导致LLM的偏见?什么是思维链(CoT)提示?Tokenizer的实现方法及原理解释一下大模型的涌现能力?解释langchainAgent的概念langchain有哪些替代方案?RLHF完整训练过程是什么?为什么RLHF的效果这么好?RLHF使用的训练数据是什么样的?RAG和微调的区别是什么?有了解过什么是稀疏微调
- 深入解析五大 LLM 可视化工具:Langflow、Flowise、Dify、AutoGPT UI 和 AgentGPT
花千树-010
AI编程langchain机器学习AI编程python机器人
近年来,大语言模型(LLM)技术的迅猛发展推动了智能代理(Agent)应用的广泛应用。从任务自动化到智能对话系统,LLM代理可以极大简化复杂任务的执行。为了帮助开发者更快地构建和部署这些智能代理,多个开源工具应运而生,尤其是那些提供可视化界面的工具,让开发者通过简单的图形界面设计、调试和管理智能代理。本文将详细介绍五款热门的LLM可视化工具,分别是Langflow、Flowise、Dify、Aut
- nginx过滤爬虫访问
梓沂
nginx爬虫运维
思路来自ai:Nginx可以通过多种方式来限制爬虫的行为:1.**User-Agent限制**:可以通过检查HTTP请求的User-Agent头部来识别并限制某些爬虫。例如,可以在Nginx配置文件中使用`if`语句来检查User-Agent,并使用`return`指令拒绝特定的User-Agent。```nginxif($http_user_agent~*(BadCrawler|AnotherB
- 一文告诉你程序员该掌握和应用大模型
大耳朵爱学习
语言模型人工智能自然语言处理AI大模型大模型程序员大模型入门
训练大模型:场景:自训练大模型人才需求:算法工程师门槛:极高机会:较高特点:这个方向需要深厚的算法和机器学习知识,适合那些对研究和开发新模型感兴趣的人。微调大模型:场景:垂直大模型人才需求:算法工程师门槛:高机会:高特点:专注于特定领域的大模型优化,适合有一定领域知识且希望在细分市场深耕的工程师。AIAgent:场景:工作流人才需求:懂业务和大模型的研发工程师门槛:较高机会:一般特点:需要结合业务
- 区分PC端还是移动端
praycis
varos=function(){varua=navigator.userAgent,isWindowsPhone=/(?:WindowsPhone)/.test(ua),isSymbian=/(?:SymbianOS)/.test(ua)||isWindowsPhone,isAndroid=/(?:Android)/.test(ua),isFireFox=/(?:Firefox)/.test(u
- jenkins配置流水线
iteye_10392
jenkinsjenkinselasticsearch运维
新建任务,随便选一个名字,选中流水线配置git的用户名和密码,记录ID,后面配置流水线的时候用。pipeline{agentanystages{stage('stopapp'){steps{script{defremote=[:]//配置服务地址,用户名和密码remote.name='prd'remote.host='114.116.1.1'remote.user='test'remote.pas
- LlamaIndex 使用 RouterOutputAgentWorkflow
hawk2014bj
llamaIndexLLMagent
LlamaIndex中提供了一个RouterOutputAgentWorkflow功能,可以集成多个QueryTool,根据用户的输入判断使用那个QueryEngine,在做查询的时候,可以从不同的数据源进行查询,例如确定的数据从数据库查询,如果是语义查询可以从向量数据库进行查询。本文将实现两个搜索引擎,根据不同Query使用不同QueryEngine。安装MySQL依赖pipinstallmys
- pyspark kafka mysql_数据平台实践①——Flume+Kafka+SparkStreaming(pyspark)
weixin_39793638
pysparkkafkamysql
蜻蜓点水Flume——数据采集如果说,爬虫是采集外部数据的常用手段的话,那么,Flume就是采集内部数据的常用手段之一(logstash也是这方面的佼佼者)。下面介绍一下Flume的基本构造。Agent:包含Source、Channel和Sink的主体,它是这3个组件的载体,是组成Flume的数据节点。Event:Flume数据传输的基本单元。Source:用来接收Event,并将Event批量传
- python 线程池内存泄露_Python2.6的multiprocessing.dummy.Pool的一个内存泄露的问题
weixin_39687189
python线程池内存泄露
线上一个监控系统的agent内存单调增长,查了半天,在我的开发环境的python2.7下重现不了,好不容易找了个老古董的RHEL6环境用python2.6才能重现.Agent里面,用multiprocessing.dummy.Pool开一个线程池,然后通过map方法,批量执行一批预先配置的任务,测试发现用python2.6运行时,如果某种任务一条也没配置的话,就会有明显的内存泄露.把重现的方法最简
- linux自动化运维之ansible实战
浓黑的daidai
运维自动化ansible
ansible基础介绍优点-相比于saltatack和puppet,没有客户端,更轻量级-只是一个工具,可以很容易实现分布式拓展-更强的远程执行命令特点-模块化-支持自定义模块,可以用任何语言编写模块-基于python语言实现-部署简单,基于python和ssh,agentless,无需代理-安全安装yum安装首先安装epel源:yuminstallepel-release-y下载ansible:
- 多线程编程之卫生间
周凡杨
java并发卫生间线程厕所
如大家所知,火车上车厢的卫生间很小,每次只能容纳一个人,一个车厢只有一个卫生间,这个卫生间会被多个人同时使用,在实际使用时,当一个人进入卫生间时则会把卫生间锁上,等出来时打开门,下一个人进去把门锁上,如果有一个人在卫生间内部则别人的人发现门是锁的则只能在外面等待。问题分析:首先问题中有两个实体,一个是人,一个是厕所,所以设计程序时就可以设计两个类。人是多数的,厕所只有一个(暂且模拟的是一个车厢)。
- How to Install GUI to Centos Minimal
sunjing
linuxInstallDesktopGUI
http://www.namhuy.net/475/how-to-install-gui-to-centos-minimal.html
I have centos 6.3 minimal running as web server. I’m looking to install gui to my server to vnc to my server. You can insta
- Shell 函数
daizj
shell函数
Shell 函数
linux shell 可以用户定义函数,然后在shell脚本中可以随便调用。
shell中函数的定义格式如下:
[function] funname [()]{
action;
[return int;]
}
说明:
1、可以带function fun() 定义,也可以直接fun() 定义,不带任何参数。
2、参数返回
- Linux服务器新手操作之一
周凡杨
Linux 简单 操作
1.whoami
当一个用户登录Linux系统之后,也许他想知道自己是发哪个用户登录的。
此时可以使用whoami命令。
[ecuser@HA5-DZ05 ~]$ whoami
e
- 浅谈Socket通信(一)
朱辉辉33
socket
在java中ServerSocket用于服务器端,用来监听端口。通过服务器监听,客户端发送请求,双方建立链接后才能通信。当服务器和客户端建立链接后,两边都会产生一个Socket实例,我们可以通过操作Socket来建立通信。
首先我建立一个ServerSocket对象。当然要导入java.net.ServerSocket包
ServerSock
- 关于框架的简单认识
西蜀石兰
框架
入职两个月多,依然是一个不会写代码的小白,每天的工作就是看代码,写wiki。
前端接触CSS、HTML、JS等语言,一直在用的CS模型,自然免不了数据库的链接及使用,真心涉及框架,项目中用到的BootStrap算一个吧,哦,JQuery只能算半个框架吧,我更觉得它是另外一种语言。
后台一直是纯Java代码,涉及的框架是Quzrtz和log4j。
都说学前端的要知道三大框架,目前node.
- You have an error in your SQL syntax; check the manual that corresponds to your
林鹤霄
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'option,changed_ids ) values('0ac91f167f754c8cbac00e9e3dc372
- MySQL5.6的my.ini配置
aigo
mysql
注意:以下配置的服务器硬件是:8核16G内存
[client]
port=3306
[mysql]
default-character-set=utf8
[mysqld]
port=3306
basedir=D:/mysql-5.6.21-win
- mysql 全文模糊查找 便捷解决方案
alxw4616
mysql
mysql 全文模糊查找 便捷解决方案
2013/6/14 by 半仙
[email protected]
目的: 项目需求实现模糊查找.
原则: 查询不能超过 1秒.
问题: 目标表中有超过1千万条记录. 使用like '%str%' 进行模糊查询无法达到性能需求.
解决方案: 使用mysql全文索引.
1.全文索引 : MySQL支持全文索引和搜索功能。MySQL中的全文索
- 自定义数据结构 链表(单项 ,双向,环形)
百合不是茶
单项链表双向链表
链表与动态数组的实现方式差不多, 数组适合快速删除某个元素 链表则可以快速的保存数组并且可以是不连续的
单项链表;数据从第一个指向最后一个
实现代码:
//定义动态链表
clas
- threadLocal实例
bijian1013
javathreadjava多线程threadLocal
实例1:
package com.bijian.thread;
public class MyThread extends Thread {
private static ThreadLocal tl = new ThreadLocal() {
protected synchronized Object initialValue() {
return new Inte
- activemq安全设置—设置admin的用户名和密码
bijian1013
javaactivemq
ActiveMQ使用的是jetty服务器, 打开conf/jetty.xml文件,找到
<bean id="adminSecurityConstraint" class="org.eclipse.jetty.util.security.Constraint">
<p
- 【Java范型一】Java范型详解之范型集合和自定义范型类
bit1129
java
本文详细介绍Java的范型,写一篇关于范型的博客原因有两个,前几天要写个范型方法(返回值根据传入的类型而定),竟然想了半天,最后还是从网上找了个范型方法的写法;再者,前一段时间在看Gson, Gson这个JSON包的精华就在于对范型的优雅简单的处理,看它的源代码就比较迷糊,只其然不知其所以然。所以,还是花点时间系统的整理总结下范型吧。
范型内容
范型集合类
范型类
- 【HBase十二】HFile存储的是一个列族的数据
bit1129
hbase
在HBase中,每个HFile存储的是一个表中一个列族的数据,也就是说,当一个表中有多个列簇时,针对每个列簇插入数据,最后产生的数据是多个HFile,每个对应一个列族,通过如下操作验证
1. 建立一个有两个列族的表
create 'members','colfam1','colfam2'
2. 在members表中的colfam1中插入50*5
- Nginx 官方一个配置实例
ronin47
nginx 配置实例
user www www;
worker_processes 5;
error_log logs/error.log;
pid logs/nginx.pid;
worker_rlimit_nofile 8192;
events {
worker_connections 4096;}
http {
include conf/mim
- java-15.输入一颗二元查找树,将该树转换为它的镜像, 即在转换后的二元查找树中,左子树的结点都大于右子树的结点。 用递归和循环
bylijinnan
java
//use recursion
public static void mirrorHelp1(Node node){
if(node==null)return;
swapChild(node);
mirrorHelp1(node.getLeft());
mirrorHelp1(node.getRight());
}
//use no recursion bu
- 返回null还是empty
bylijinnan
javaapachespring编程
第一个问题,函数是应当返回null还是长度为0的数组(或集合)?
第二个问题,函数输入参数不当时,是异常还是返回null?
先看第一个问题
有两个约定我觉得应当遵守:
1.返回零长度的数组或集合而不是null(详见《Effective Java》)
理由就是,如果返回empty,就可以少了很多not-null判断:
List<Person> list
- [科技与项目]工作流厂商的战略机遇期
comsci
工作流
在新的战略平衡形成之前,这里有一个短暂的战略机遇期,只有大概最短6年,最长14年的时间,这段时间就好像我们森林里面的小动物,在秋天中,必须抓紧一切时间存储坚果一样,否则无法熬过漫长的冬季。。。。
在微软,甲骨文,谷歌,IBM,SONY
- 过度设计-举例
cuityang
过度设计
过度设计,需要更多设计时间和测试成本,如无必要,还是尽量简洁一些好。
未来的事情,比如 访问量,比如数据库的容量,比如是否需要改成分布式 都是无法预料的
再举一个例子,对闰年的判断逻辑:
1、 if($Year%4==0) return True; else return Fasle;
2、if ( ($Year%4==0 &am
- java进阶,《Java性能优化权威指南》试读
darkblue086
java性能优化
记得当年随意读了微软出版社的.NET 2.0应用程序调试,才发现调试器如此强大,应用程序开发调试其实真的简单了很多,不仅仅是因为里面介绍了很多调试器工具的使用,更是因为里面寻找问题并重现问题的思想让我震撼,时隔多年,Java已经如日中天,成为许多大型企业应用的首选,而今天,这本《Java性能优化权威指南》让我再次找到了这种感觉,从不经意的开发过程让我刮目相看,原来性能调优不是简单地看看热点在哪里,
- 网络学习笔记初识OSI七层模型与TCP协议
dcj3sjt126com
学习笔记
协议:在计算机网络中通信各方面所达成的、共同遵守和执行的一系列约定 计算机网络的体系结构:计算机网络的层次结构和各层协议的集合。 两类服务: 面向连接的服务通信双方在通信之前先建立某种状态,并在通信过程中维持这种状态的变化,同时为服务对象预先分配一定的资源。这种服务叫做面向连接的服务。 面向无连接的服务通信双方在通信前后不建立和维持状态,不为服务对象
- mac中用命令行运行mysql
dcj3sjt126com
mysqllinuxmac
参考这篇博客:http://www.cnblogs.com/macro-cheng/archive/2011/10/25/mysql-001.html 感觉workbench不好用(有点先入为主了)。
1,安装mysql
在mysql的官方网站下载 mysql 5.5.23 http://www.mysql.com/downloads/mysql/,根据我的机器的配置情况选择了64
- MongDB查询(1)——基本查询[五]
eksliang
mongodbmongodb 查询mongodb find
MongDB查询
转载请出自出处:http://eksliang.iteye.com/blog/2174452 一、find简介
MongoDB中使用find来进行查询。
API:如下
function ( query , fields , limit , skip, batchSize, options ){.....}
参数含义:
query:查询参数
fie
- base64,加密解密 经融加密,对接
y806839048
经融加密对接
String data0 = new String(Base64.encode(bo.getPaymentResult().getBytes(("GBK"))));
String data1 = new String(Base64.decode(data0.toCharArray()),"GBK");
// 注意编码格式,注意用于加密,解密的要是同
- JavaWeb之JSP概述
ihuning
javaweb
什么是JSP?为什么使用JSP?
JSP表示Java Server Page,即嵌有Java代码的HTML页面。使用JSP是因为在HTML中嵌入Java代码比在Java代码中拼接字符串更容易、更方便和更高效。
JSP起源
在很多动态网页中,绝大部分内容都是固定不变的,只有局部内容需要动态产生和改变。
如果使用Servl
- apple watch 指南
啸笑天
apple
1. 文档
WatchKit Programming Guide(中译在线版 By @CocoaChina) 译文 译者 原文 概览 - 开始为 Apple Watch 进行开发 @星夜暮晨 Overview - Developing for Apple Watch 概览 - 配置 Xcode 项目 - Overview - Configuring Yo
- java经典的基础题目
macroli
java编程
1.列举出 10个JAVA语言的优势 a:免费,开源,跨平台(平台独立性),简单易用,功能完善,面向对象,健壮性,多线程,结构中立,企业应用的成熟平台, 无线应用 2.列举出JAVA中10个面向对象编程的术语 a:包,类,接口,对象,属性,方法,构造器,继承,封装,多态,抽象,范型 3.列举出JAVA中6个比较常用的包 Java.lang;java.util;java.io;java.sql;ja
- 你所不知道神奇的js replace正则表达式
qiaolevip
每天进步一点点学习永无止境纵观千象regex
var v = 'C9CFBAA3CAD0';
console.log(v);
var arr = v.split('');
for (var i = 0; i < arr.length; i ++) {
if (i % 2 == 0) arr[i] = '%' + arr[i];
}
console.log(arr.join(''));
console.log(v.r
- [一起学Hive]之十五-分析Hive表和分区的统计信息(Statistics)
superlxw1234
hivehive分析表hive统计信息hive Statistics
关键字:Hive统计信息、分析Hive表、Hive Statistics
类似于Oracle的分析表,Hive中也提供了分析表和分区的功能,通过自动和手动分析Hive表,将Hive表的一些统计信息存储到元数据中。
表和分区的统计信息主要包括:行数、文件数、原始数据大小、所占存储大小、最后一次操作时间等;
14.1 新表的统计信息
对于一个新创建
- Spring Boot 1.2.5 发布
wiselyman
spring boot
Spring Boot 1.2.5已在7月2日发布,现在可以从spring的maven库和maven中心库下载。
这个版本是一个维护的发布版,主要是一些修复以及将Spring的依赖提升至4.1.7(包含重要的安全修复)。
官方建议所有的Spring Boot用户升级这个版本。
项目首页 | 源