思科CUCM支持LDAP用户的集成,最近计划把CUCM的用户全部转换成了AD域用户,虽然支持了LDAP用户的导入和认证,但是用户只能针对OU,后来研究了一下,可以通过LDAP的FILTER功能来实现,LDAP有自已的表达式方式,下面与大家一起分享一下我的测试过程:
一.CUCM安装好了,需要简单配置一下,这里就不再表述了。
二. “server---LDAP---ldap system".先启用LDAP,选择对应的LDAP类型,以及对应的字段,按下图的设置进行设置并保存。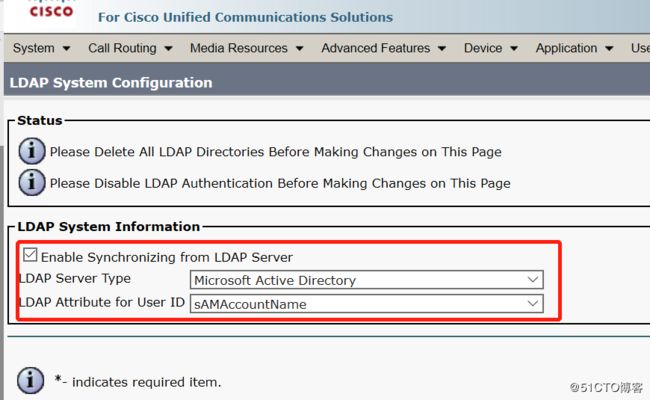
三、server---LDAP---ldap directory".设置LDAP服务器的连接信息,以及对应的同步字段,ldap地址,最后保存一下
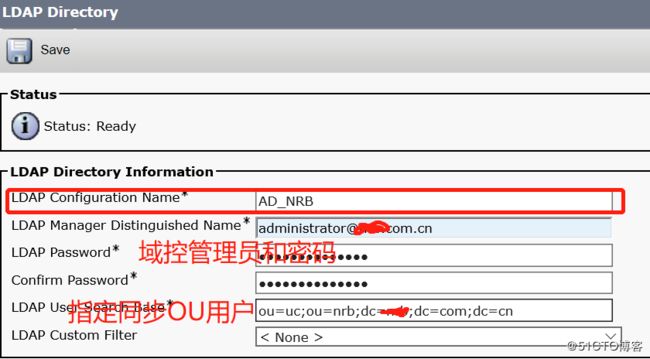
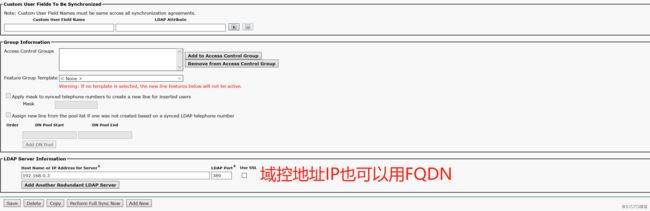
四、server----ldap---ldap authencitation, 设置后续同步过来用户的认证,也是从LDAP服务器进行认证。
五、usermanagement--end user, 查看用户同步情况,从AD的UC的OU中同步两个用户,
图一: AD中UC的OU中有两个用户
图二:同步了两个用户![]()
下面我们验证一下,使用微软AD同步过来的用户和密码登录,jabber登录OK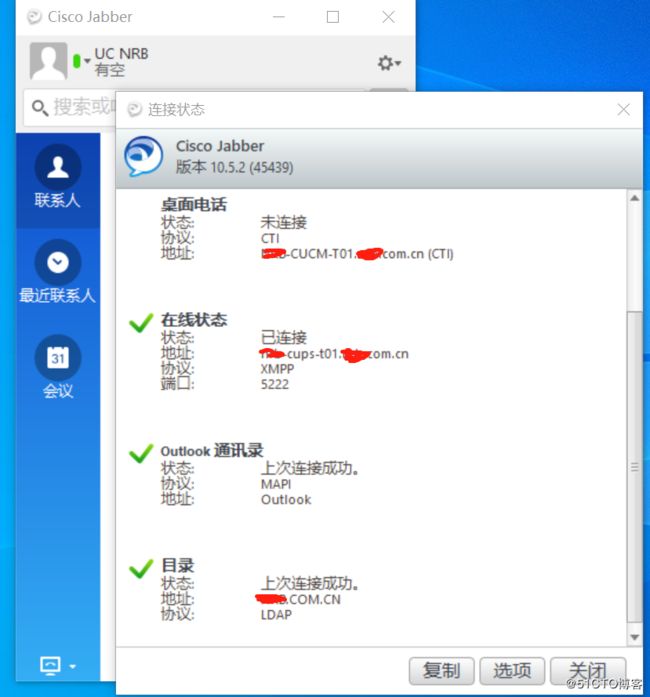
六.从上面可以看出来,不能同步OU中的组,这项功能可以通过ldap的filter功能, 微软有一套自已的表达式,下面与大家共享一下。
图一:在"system-ldap-ldap custom filter--add new“新建一个filter configuration,从AD的指定组同步用户:
表达式-(memberOf=cn=ciscouc,ou=test,dc=S,dc=com,dc=cn) 表示从s.com.cn这个域内的test OU中同步ciscouc这个组的成员。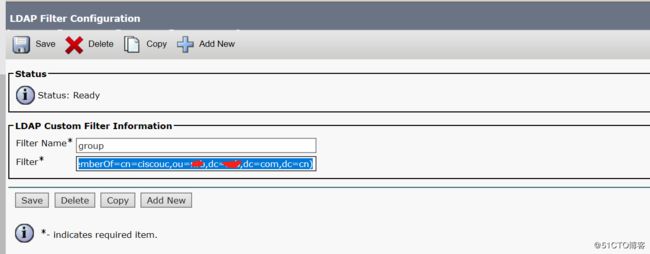
图二:在"system-ldap-ldapdirectory”中调用这个filter;并手动执行一下同步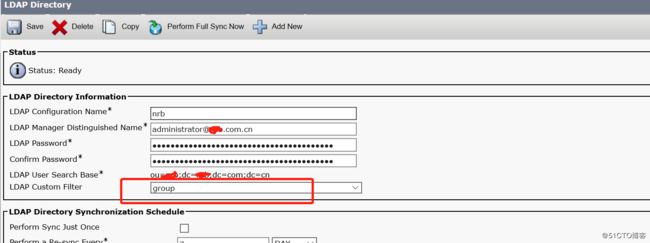
图三:查看用户是否从AD的组中同步到CUCM中,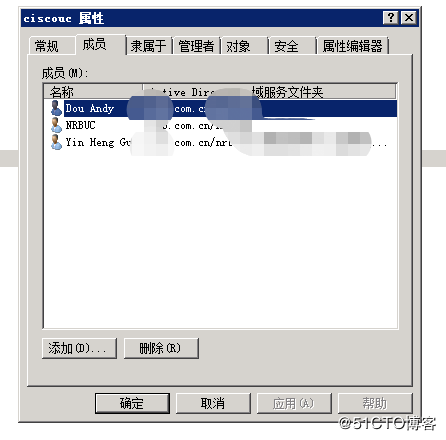
![]()
六、附上ldap Filter的表达式大全供大家参考。
Examples
The following table shows many example LDAP filters that can be useful when you query Active Directory:
Query LDAP Filter
All user objects (&(objectCategory=person)(objectClass=user))
All user objects (Note 1) (sAMAccountType=805306368)
All computer objects (objectCategory=computer)
All contact objects (objectClass=contact)
All group objects (objectCategory=group)
All organizational unit objects (objectCategory=organizationalUnit)
All container objects (objectCategory=container)
All builtin container objects (objectCategory=builtinDomain)
All domain objects (objectCategory=domain)
Computer objects with no description (&(objectCategory=computer)(!(description=)))
Group objects with a description (&(objectCategory=group)(description=))
Users with cn starting with "Joe" (&(objectCategory=person)(objectClass=user)
(cn=Joe))
Object with description "East\West Sales"
(Note 2) (description=East\5CWest Sales)
Phone numbers in form (xxx) xxx-xxx (telephoneNumber=()-)
Groups with cn starting with
"Test" or "Admin" (&(objectCategory=group)
(|(cn=Test)(cn=Admin)))
All users with both a first and last name. (&(objectCategory=person)(objectClass=user)
(givenName=)(sn=))
All users with direct reports but no
manager (&(objectCategory=person)(objectClass=user)
(directReports=)(!(manager=)))
All users with specified email address (&(objectCategory=person)(objectClass=user)
(|(proxyAddresses=:[email protected]) br/>([email protected])))
All users with Logon Script field occupied (&(objectCategory=person)(objectClass=user)(scriptPath=))
Object with Common Name "Jim Smith"
(Notes 3, 19) (cn=Jim \2A Smith)
Objects with sAMAccountName that begins
with "x", "y", or "z" (sAMAccountName>=x)
Objects with sAMAccountName that begins
with "a" or any number or symbol except "$" (&(sAMAccountName<=a)(!(sAMAccountName=$)))
All users with "Password Never Expires" set
(Note 4) (&(objectCategory=person)(objectClass=user)
(userAccountControl:1.2.840.113556.1.4.803:=65536))
All disabled user objects (Note 4) (&(objectCategory=person)(objectClass=user)
(userAccountControl:1.2.840.113556.1.4.803:=2))
All enabled user objects (Note 4) (&(objectCategory=person)(objectClass=user)
(!(userAccountControl:1.2.840.113556.1.4.803:=2)))
All users not required to have a password
(Note 4) (&(objectCategory=person)(objectClass=user)
(userAccountControl:1.2.840.113556.1.4.803:=32))
All users with "Do not require kerberos
preauthentication" enabled (&(objectCategory=person)(objectClass=user)
(userAccountControl:1.2.840.113556.1.4.803:=4194304))
Users with accounts that do not expire
(Note 5) (&(objectCategory=person)(objectClass=user)
(|(accountExpires=0)
(accountExpires=9223372036854775807)))
Users with accounts that do expire (Note 5) (&(objectCategory=person)(objectClass=user)
(accountExpires>=1)
(accountExpires<=9223372036854775806))
Accounts trusted for delegation
(unconstrained delegation) (userAccountControl:1.2.840.113556.1.4.803:=524288)
Accounts that are sensitive and not trusted
for delegation (userAccountControl:1.2.840.113556.1.4.803:=1048576)
All distribution groups (Notes 4, 15) (&(objectCategory=group)
(!(groupType:1.2.840.113556.1.4.803:=2147483648)))
All security groups (Notes 4, 19) (groupType:1.2.840.113556.1.4.803:=2147483648)
All built-in groups (Notes 4, 16, 19) (groupType:1.2.840.113556.1.4.803:=1)
All global groups (Notes 4, 19) (groupType:1.2.840.113556.1.4.803:=2)
All domain local groups (Notes 4, 19) (groupType:1.2.840.113556.1.4.803:=4)
All universal groups (Notes 4, 19) (groupType:1.2.840.113556.1.4.803:=8)
All global security groups (Notes 17, 19) (groupType=-2147483646)
All universal security groups (Notes 17, 19) (groupType=-2147483640)
All domain local security groups
(Notes 17, 19) (groupType=-2147483644)
All global distribution groups (Note 19) (groupType=2)
All objects with service principal name (servicePrincipalName=)
Users with "Allow Access" on "Dial-in"
tab of ADUC
(Note 6) (&(objectCategory=person)(objectClass=user)
(msNPAllowDialin=TRUE))
Users with "Control access though
NPS Network Policy" on "Dial-in" tab of ADUC (&(objectCategory=person)(objectClass=user)
(!(msNPAllowDialin=)))
All groups created after March 1, 2011 (&(objectCategory=group)
(whenCreated>=20110301000000.0Z))
All users where an administrator has set that they must change their password at next logon (&(objectCategory=person)(objectClass=user)
(pwdLastSet=0))
All users that changed their password since
April 15, 2011 (CST) (Note 7) (&(objectCategory=person)(objectClass=user)
(pwdLastSet>=129473172000000000))
All users with "primary" group
other than "Domain Users" (&(objectCategory=person)(objectClass=user)
(!(primaryGroupID=513)))
All computers with "primary" group
"Domain Computers" (&(objectCategory=computer)
(primaryGroupID=515))
Object with GUID
"90395F191AB51B4A9E9686C66CB18D11"
(Note 8) (objectGUID=\90\39\5F\19\1A\B5\1B\4A\9E\96
\86\C6\6C\B1\8D\11)
Object beginning with GUID
"90395F191AB51B4A"
(Note 8) (objectGUID=\90\39\5F\19\1A\B5\1B\4A)
Object with SID "S-1-5-21-73586283
-152049171-839522115-1111" (Note 9) (objectSID=S-1-5-21-73586283-152049171
-839522115-1111)
Object with SID "010500000000000515000
0006BD662041316100943170A3257040000"
(Note 9) (objectSID=\01\05\00\00\00\00\00\05\15
\00\00\00\6B\D6\62\04\13\16\10\09\43\17\0A\32
\57\04\00\00)
All computers that are not
Domain Controllers (Note 4) (&(objectCategory=computer)
(!(userAccountControl:1.2.840.113556.1.4.803:=8192)))
All Domain Controllers (Note 4) (&(objectCategory=computer)
(userAccountControl:1.2.840.113556.1.4.803:=8192))
All Domain Controllers (Notes 14, 19) (primaryGroupID=516)
All servers (&(objectCategory=computer)
(operatingSystem=server))
All member servers (not DC's) (Note 4) (&(objectCategory=computer)
(operatingSystem=server)
(!(userAccountControl:1.2.840.113556.1.4.803:=8192)))
All direct members of specified group (memberOf=cn=Test,ou=East,dc=Domain,dc=com)
All users not direct members of
a specified group (&(objectCategory=person)(objectClass=user)
(!(memberOf=cn=Test,ou=East,dc=Domain,dc=com)))
All groups with specified direct member
(Note 19) (member=cn=Jim Smith,ou=West,
dc=Domain,dc=com)
All members of specified group, including
due to group nesting (Note 10) (memberOf:1.2.840.113556.1.4.1941:=
cn=Test,ou=East,dc=Domain,dc=com)
All groups specified user belongs to,
including due to group nesting (Notes 10, 19) (member:1.2.840.113556.1.4.1941:=
cn=Jim Smith,ou=West,dc=Domain,dc=com)
Objects with givenName "Jim" and sn
"Smith", or with cn "Jim Smith" (Note 11) (anr=Jim Smith)
All attributes in the Schema container
replicated to the GC (Notes 6, 12) (&(objectCategory=attributeSchema)
(isMemberOfPartialAttributeSet=TRUE))
All operational (constructed) attributes in
the Schema container (Notes 4, 12) (&(objectCategory=attributeSchema)
(systemFlags:1.2.840.113556.1.4.803:=4))
All attributes in the Schema container not
replicated to other Domain Controllers
(Notes 4, 12) (&(objectCategory=attributeSchema)
(systemFlags:1.2.840.113556.1.4.803:=1))
All objects where deletion is not allowed
(Notes 4) (systemFlags:1.2.840.113556.1.4.803:=2147483648)
Attributes whose values are copied when
the object is copied (Notes 4, 12) (searchFlags:1.2.840.113556.1.4.803:=16)
Attributes preserved in tombstone object
when object deleted (Notes 4, 12) (searchFlags:1.2.840.113556.1.4.803:=8)
Attributes in the Ambiguous Name
Resolution (ANR) set (Notes 4, 12) (searchFlags:1.2.840.113556.1.4.803:=4)
Attributes in the Schema that are
indexed (Notes 4, 12) (searchFlags:1.2.840.113556.1.4.803:=1)
Attributes marked confidential in
the schema (Notes 4, 12) (searchFlags:1.2.840.113556.1.4.803:=128)
Attributes in the RODC filtered attribute
set, or FAS (Notes 4, 12) (searchFlags:1.2.840.113556.1.4.803:=512)
All inter-site connection objects in the Configuration
container (Note 13) (objectClass=siteLink)
All intra-site connection objects in the Configuration
container (Note 13)) (objectClass=nTDSConnection)
The nTDSDSA objects associated with
all Global Catalogs. This will identify all DC's
that are GC's. (Note 4) (&(objectCategory=nTDSDSA)
(options:1.2.840.113556.1.4.803:=1))
The nTDSDSA object associated with the
PDC Emulator. This will identify the DC
with the PDC Emulator FSMO role (Note 18). (&(objectClass=domainDNS)(fSMORoleOwner=))
The nTDSDSA object associated with the
RID Master. This will identify the DC
with the RID Master FSMO role (Note 18). (&(objectClass=rIDManager)(fSMORoleOwner=))
The nTDSDSA object associated with the
Infrastructure Master. This will identify the DC
with this FSMO role (Note 18). (&(objectClass=infrastructureUpdate)
(fSMORoleOwner=))
The nTDSDSA object associated with the
Schema Master. This will identify the DC with
the Schema Master FSMO role (Note 18). (&(objectClass=dMD)(fSMORoleOwner=))
The nTDSDSA object associated with the
Domain Naming Master. This will identify the
DC with this FSMO role (Note 18). (&(objectClass=cro**efContainer)
(fSMORoleOwner=))
All Exchange servers in the Configuration
container (Note 13) (objectCategory=msExchExchangeServer)
All objects protected by AdminSDHolder (adminCount=1)
All trusts established with a domain (objectClass=trustedDomain)
All Group Policy objects (objectCategory=groupPolicyContainer)
All service connection point objects (objectClass=serviceConnectionPoint)
All Read-Only Domain Controllers
(Notes 4, 19) (userAccountControl:1.2.840.113556.1.4.803:=67108864)