转: CONTINUOUS-VARIABLE QUANTUM COMMUNICATION 连续变量量子通信(英文)
本文转自http://infiniquant.com/tutorial-continuous-variable-quantum-communication/。
This tutorial conveys the basic ideas behind continuous-variable quantum key distribution (QKD). It is targeted at physicists or engineers, preferably with a basic understanding of optics. Please share your thoughts if you have any comments or questions!
Terminology of continuous- and discrete-variable QKD
First, let us understand where the term “continuous-variable” comes from. It is the distinction to what is called “discrete-variable” quantum key distribution. Technically this can be understood as the difference between a single photon detector and a homodyne detector:
A single photon detector detects a click when a photon has hit the detector, or no click otherwise. Mathematically, this can be explained as the set of outcomes {click, no click}. The number of outcomes is discrete – therefore the term discrete-variable quantum key distribution, abbreviated DV-QKD.
A homodyne detector on the other hand measures the quadratures of the electric field of the incident light. The measurement outcomes of such a measurement are a projection of phase and amplitude of the electric field of light onto the quadrature axes. This projection yields a continuous value as a measurement result, therefore justifying the name continuous-variable quantum key distribution, or CV-QKD.
The classical phase space
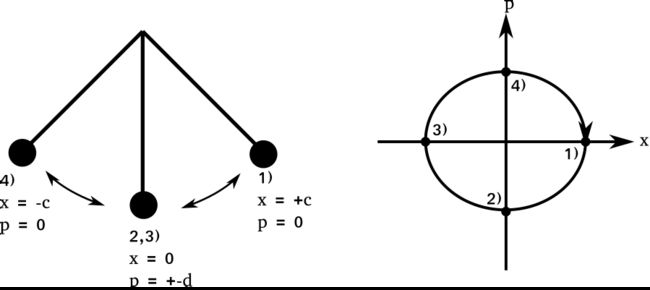
A good tool to depict states of light is the optical phase space. To illustrate this basic concept of quantum mechanics, let us first make an analogy to classical mechanics and talk about the classical phase space instead: A pendulum has two major observable physical quantities: the position x of the pendulum, and its momentum p. If the motion of the pendulum is visualized in a 2D coordinate system with x and p along the two axes, then four interesting points can be identified along the pendulum’s path of evolution in this 2D phase space:
- The pendulum is on the right side and stops, corresponding to maximal positive displacement and zero momentum
- The pendulum is in the center on its way from right to left, has a position of 0 and has maximum velocity and thus momentum
- The pendulum is on the left side and stops, corresponding to maximal negative displacement and zero momentum
- The pendulum is in the center on its way from left to right, has a position of 0 and has maximum momentum
Connecting these points by letting the pendulum oscillate, will result in an ellipse as shown in the above figure on the right.
The optical phase space
States of light can also be depicted in such a phase space, only this time it is called the optical phase space. Light can be described as an electromagnetic wave. Its electric field component can be written as a function of sine and cosine. This makes it very similar to the periodic oscillation of the pendulum we just discussed.
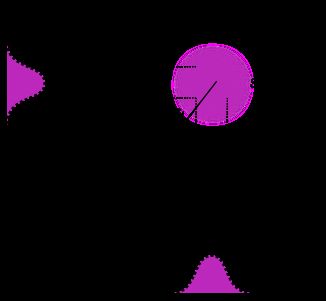
In fact, even the same letters as for momentum and position are used to describe the electric field of light in the optical phase space. These variables are called the electric field quadratures X and P. Measuring these quantities, yields their marginal distributions. Combining these marginal distributions into one plot yields the optical phase space in analogy to the classical phase space composed of position and momentum for the example of the pendulum. The figure below shows a typical state of light, emitted by a laser. This state of light is called the coherent state and is parametrized by its amplitude and phase.
Why does the coherent state have a Gaussian distribution instead of a single point in the optical phase space diagram? The reason is Heisenberg’s uncertainty relation, which causes the exact position and momentum of classical mechanics to be a fuzzy probability distribution in quantum mechanics. Heisenberg’s uncertainty relation states that the simultaneous determination of certain physical properties is not possible with arbitrary precision. And these physical properties are called non-commuting observables. The most prominent pair of non-commuting observables is given by position x and momentum p. The optical analogue of this are the electrical field quadratures X and P. The result of this fact is that the expected measurement distribution of those observables is not a single point anymore, but instead a fuzzy version of that. For a coherent state, a two-dimensional Gaussian distribution in optical phase space.
Transmitting information using coherent states of light
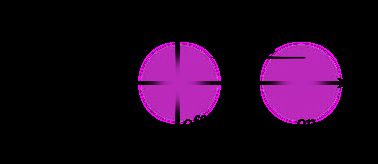
It is long known that lasers can be used for communication. A simple definition of a good communication protocol is that it transmits information with minimal errors. As an example, one can turn a flash light on and off to transmit Morse code to someone else. An analogue in telecommunication is what is called “on-off-keying”, basically turning a laser on and off and encoding a 1 as on and a 0 as off to transmit information. Depicting this in the optical phase space, will yield a diagram with two coherent states, where one is centered in the coordinate system, corresponding to the laser being off and the other one with a certain amplitude and phase when the laser is on.
Communication only makes sense, if the information is transmitted over a certain distance. A typical way to cover the distance is transmission through glass fiber. Light propagation through such a fiber comes at the cost of a loss of intensity, exponentially tied to the distance. In logarithmic units, a typical value is 0.2 dB of loss per km of fiber. The effect on the original states prepared will bring the on-state closer to the center, since its amplitude is diminished by loss.
As we originally defined communication, it was our goal to achieve minimal errors when discriminating our measured states to recover the 0s and 1s from our measurement signal. This is achieved, when the loss of amplitude is kept such that the measurement distributions of the on-state and the off-state do not overlap significantly. In other words, discriminating the two states that transmit information, depends on the initial amplitude and the loss after propagation.
Eavesdropping the communication
An adversarial eavesdropper “Eve” is tapping in on the on-off-keying communication protocol we are running. Eve is tapping off the full amount of the transmitted light and is using a homodyne detector to establish measurement distributions constituting the optical phase space. The result of the measurement is two Gaussian distributions that can be well discriminated.
Eve does not want to get caught while performing the eavesdropping. As such, she has her own transmitter system and modulates coherent states with the amplitude and phase she detected. The receiver “Bob” will therefore think that no one was in the line, since the on-off-states arrive unchanged with respect to normal operation.
So what can we do against this situation?
Forcing Eve to leave a signature
Opposed to the communication goal of transmitting information with minimal errors, let us change the goal towards transmitting information with a fixed and non-negligible amount of errors. This can be achieved by lowering the amplitude of the on-state such that the two Gaussian distributions have a good overlap. The result for an eavesdropper will be that Eve cannot discriminate the two states without significant errors, unless she knew in the first place, which state was sent when. Note that this is not an argument about technical noise, but can be proven using quantum mechanics.
If Eve now wants to remain undetected, she has – again – to intercept and resend the states of light using her own detector and transmitter. However, this time, the states she prepared will not correspond to the original ones a certain fraction of the time, since she made errors discriminating them in the first place. This will leave Eve’s signature in the measurement distribution that Bob will later measure.
Detecting Eve’s signature
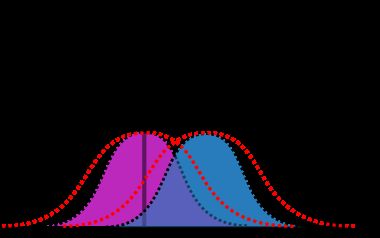
Since Bob is bound to the same state discrimination laws of quantum physics as Eve is, he also does not know, which of his measurements to assign to which state. However, Bob has help from Alice. Bob can disclose a random fraction of his measurements and Alice can tell him which state she sent for that random fraction. This allows Bob to properly assign his measurement values to the right state. He can then plot the distribution and calculate the variance of the distribution. If this variance is above the expected variance of a quantum noise-limited coherent state, he knows that something went wrong in the transmission and has to assume that Eve tampered with the quantum states along the way. The increased variance is indicated by the dotted red line in the picture below. This step is known as parameter estimation.
Handling the measurement data to generate a secret key
In case Alice and Bob do not detect an eavesdropper, they can continue to execute the protocol and move towards distilling a secret key from the measured data. Of course the publicly disclosed values in the previous step have to be thrown away, since they are no longer secret and can therefore not be used for a secret key.
The undisclosed part of the key may be used to generate a secret key. Bob’s measurement data can be seen as a version of Alice’s modulation but with added noise. He therefore does not have a perfect copy of Alice’s data, which he would need to have the same key as Alice. Speaking in terms of classical communication, a solution to this problem, would be to apply an error correction protocol. This is not possible for QKD, since Bob does not want to disclose any information that could compromise the secrecy of the key we are trying to generate.
The trick is now to only publicly disclose information, that does not tell Eve anything about the key, while still allowing Alice to correct Bob’s noise. We will not go into detail here on how this is done, but state that this can be done without leaking too much information. “Too much” means that the difference between the information leaked and the information gained through the quantum state exchange and the subsequent post-processing is still positive, allowing for a generation of a secret key rate greater than 0.
Finishing the protocol to get the final key
A few finishing touches are necessary to provide both parties with a final key. A confirmation step is necessary to ensure that the error correction worked correctly. After that, privacy amplification is performed to decrease the length of the error corrected key to a final key by reducing it by an amount that corresponds to the information leaked to Eve during the whole protocol. Finally, Alice and Bob authenticate themselves using a classical authentication method in order to ensure that they have established the secret key with the right person.
Here is a summary of the steps required to establish a key by performing a QKD protocol:
- Quantum optical state exchange
- Send a random sequence of overlapping (non-orthogonal) quantum states from Alice to Bob to establish a raw key
- Classical post-processing
- Parameter estimation to detect Eve and abort the protocol if an eavesdropper was detected
- Error correction to get an error corrected key
- Privacy amplification to reduce the information leaked to Eve to a negligible amount
- Authenticate the communication
After these steps, a final secret key can be established between Alice and Bob, which is secret to Eve. This final key can now be used for encryption with encryption methods like the one-time pad or if no information-theoretic security level is required, AES.