华为USG6000V防火墙telnet+安全策略!!!
实验拓扑
实验要求:
- 实现在内部的clound1上可以telnet、ssh以及web方式访问防火墙
- 实现内部的pc1可以访问外部的pc2,而pc3不可以访问
- 实现外部的pc2可以访问dmz中的服务器(ftp,http以及icmp)
一、配置防火墙允许telnet
1)配置接口ip
[USG6000V1]int g0/0/0
[USG6000V1-GigabitEthernet0/0/0]ip add 192.168.0.1 24
[USG6000V1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 192.168.1.1 24
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 192.168.2.1 24
[USG6000V1-GigabitEthernet1/0/0]quit
[USG6000V1]int g1/0/2
[USG6000V1-GigabitEthernet1/0/2]ip add 192.168.3.1 24
2)将防火墙g口加入安全区域
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add int g1/0/0
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add int g1/0/1
0/0/0加入安全区域
[USG6000V1-GigabitEthernet0/0/0]quit
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add int g0/0/0
3)将接
4)将接口加入安全区域
[USG6000V1-GigabitEthernet1/0/2]quit
[USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]add int g1/0/2
[USG6000V1-zone-dmz]quit
6)将防火墙配置域间包过滤,以保证网络基本通信正常,因为telnet流量属于防火墙自身收发,所以需要配置trust区域到local区域的安全策略
[USG6000V1-zone-trust]quit
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name allow_telnet
[USG6000V1-policy-security-rule-allow_telnet]source-zone trust
[USG6000V1-policy-security-rule-allow_telnet]destination-zone local
[USG6000V1-policy-security-rule-allow_telnet]action permit
[USG6000V1-policy-security-rule-allow_telnet]quit
[USG6000V1-policy-security]
7)配置允许telnet配置认证模式及本地用户信息
- 打开防火墙的telnet功能
[USG6000V1]telnet server enable
[USG6000V1]int g0/0/0
[USG6000V1-GigabitEthernet0/0/0]service-manage enable
[USG6000V1-GigabitEthernet0/0/0]service-manage telnet permit
[USG6000V1-GigabitEthernet0/0/0]
- 配置认证模式
[USG6000V1-policy-security]quit
[USG6000V1]user-interface vty 0 4
[USG6000V1-ui-vty0-4]authentication-mode aaa //配置认证模式
[USG6000V1-ui-vty0-4]protocol inbound telnet //允许telnet连接虚拟终端
[USG6000V1-ui-vty0-4]quit
- 配置本地用户信息
[USG6000V1]aaa
[USG6000V1-aaa]manager-user demo //配置本地用户为demo
[USG6000V1-aaa-manager-user-demo]password cipher demo@1234 //配置密码
Info: You are advised to config on man-machine mode.
[USG6000V1-aaa-manager-user-demo]service-type telnet //配置服务类型
[USG6000V1-aaa-manager-user-demo]level 3
[USG6000V1-aaa-manager-user-demo]quit
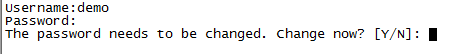
测试:
从cloud1客户端上使用登录防火墙,首次登录需要修改密码,然后再重新用新密码连接
二、配置安全策略
1.让内部的pc1可以ping通外部的主机
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name pc1toout
[USG6000V1-policy-security-rule-pc1toout]source 192.168.1.2 32
#32网络位
[USG6000V1-policy-security-rule-pc1toout]service icmp
[USG6000V1-policy-security-rule-pc1toout]destination-zone untrust
[USG6000V1-policy-security-rule-pc1toout]action permit
测试:从pc1和pc2分别 ping untrust区域主机
1)ping测试
2)查看会话
2.让外部的主机可以访问dmz中的ftp,http以及ping
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name outtodmz
[USG6000V1-policy-security-rule-outtodmz]source-zone untrust
[USG6000V1-policy-security-rule-outtodmz]destination-address 192.168.3.2 32
[USG6000V1-policy-security-rule-outtodmz]service icmp
[USG6000V1-policy-security-rule-outtodmz]service http
[USG6000V1-policy-security-rule-outtodmz]service ftp
[USG6000V1-policy-security-rule-outtodmz]action permit
测试:从pc2 ping dmz中的主机192.168.3.2