re学习笔记(71)大吉杯DJBCTF - re - 部分WP
大吉杯DJBCTF - re - 部分WP
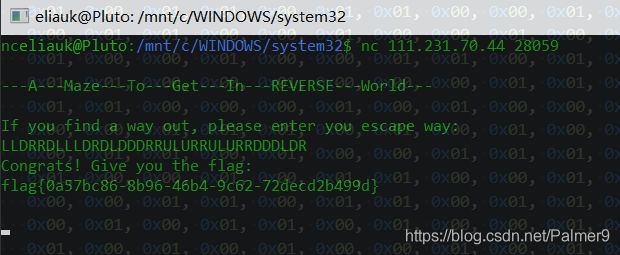
A-Maze-In
迷宫题,WDLR控制上下左右,数组是328的
映射的迷宫是88的,我理解为每四位显示着该位置的上下左右能不能走,为1能走为0不能走
写深度优先搜索脚本
import sys
sys.setrecursionlimit(100000) # 递归限制
mkey = [
0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x01,
0x01, 0x00, 0x01, 0x01, 0x00, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01,
0x00, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00,
0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x01, 0x00, 0x01, 0x01, 0x00,
0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x01, 0x00, 0x00,
0x01, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x01,
0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01,
0x00, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x00,
0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01,
0x00, 0x00, 0x01, 0x01, 0x00, 0x01, 0x01, 0x00, 0x01, 0x01, 0x00, 0x00,
0x00, 0x01, 0x00, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01,
0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x00,
0x01, 0x01, 0x00, 0x00, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01,
0x00, 0x01, 0x01, 0x00, 0x01, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01,
0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x00, 0x00,
0x01, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x00, 0x01, 0x00,
0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x00,
0x00, 0x01, 0x00, 0x01, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x00, 0x00,
0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01,
0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01,
0x00, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x01,
0x01, 0x00, 0x01, 0x00
]
road = []
flag = 0
def smaze(row, col, n):
global flag
global road
if row == 7 and col == 4:
flag = 1
if flag == 1:
if len(road)==34:
print("".join(road))
return 1
if mkey[32 * row + col * 4 + 0] == 1 and n != 'D':
if row > 0:
road.append('U')
smaze(row - 1, col, 'U')
if mkey[32 * row + col * 4 + 1] == 1 and n != 'U':
if row < 7:
road.append('D')
smaze(row + 1, col, 'D')
if mkey[32 * row + col * 4 + 2] == 1 and n != 'R':
if col > 0:
road.append('L')
smaze(row, col-1, 'L')
if mkey[32 * row + col * 4 + 3] == 1 and n != 'L':
if col < 7:
road.append('R')
smaze(row, col+1, 'R')
if len(road) != 0:
road.pop()
#print(road)
if __name__ == '__main__':
smaze(0,3,'0')
# LLDRRDLLLDRDLDDDRRULURRULURRDDDLDR
Matara Okina
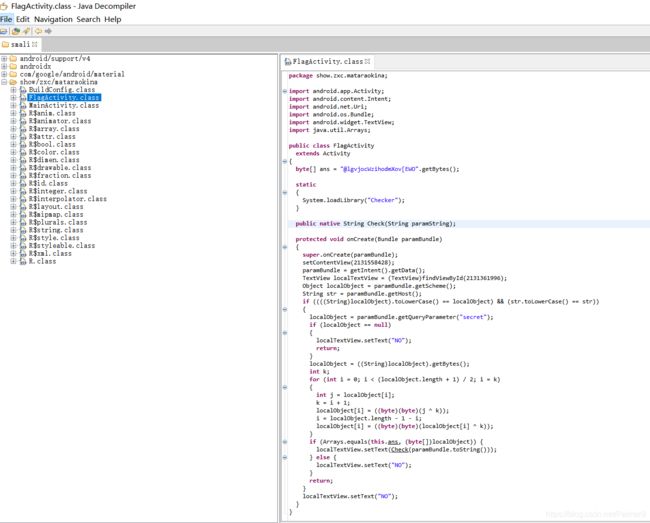
def andr():
ans = "@lgvjocWzihodmXov[EWO"
se = [i for i in ans]
for i in range(len(ans)//2):
k = i+1
se[i] = chr(ord(ans[i])^k)
i = len(ans)-1-i
se[i] = chr(ord(ans[i])^k)
print(''.join(se))
andr()
解出来
Android_scheme_is_FUN
参考博客https://www.cnblogs.com/whoislcj/p/5825333.html
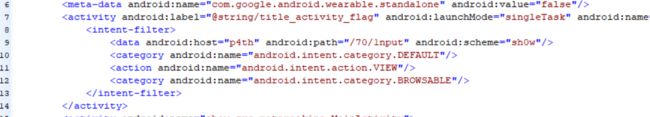
构造出链接
<a href="sh0w://p4th/70/1nput?secret=Android_scheme_is_FUN">打开APPa>
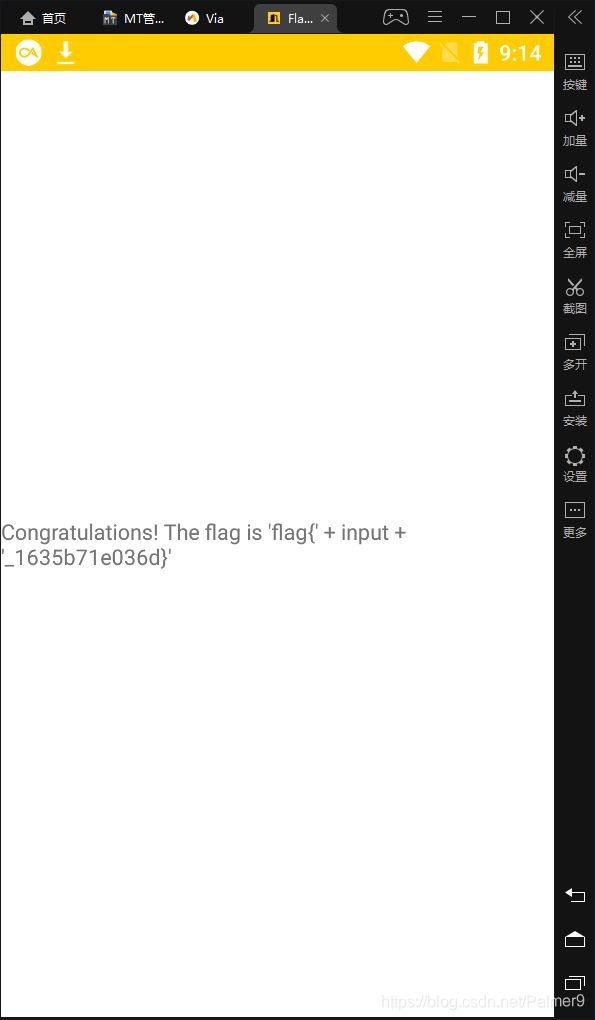
得到flagflag{sh0w://p4th/70/1nput?secret=Android_scheme_is_FUN_1635b71e036d}
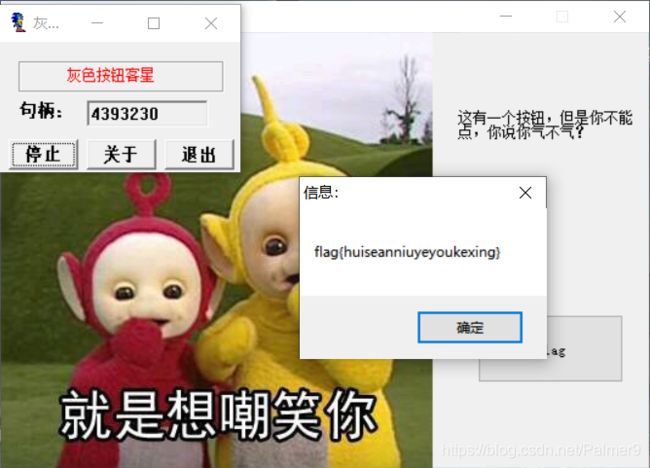
anniu
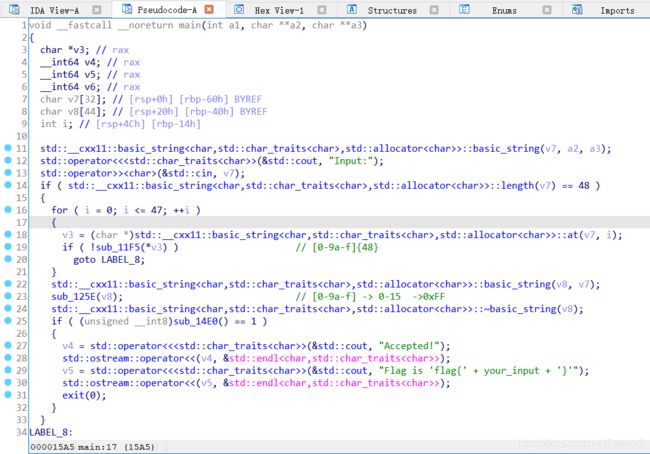
warmup
自己输入了半天输入错了还,就用selenium写了个自动输入
from selenium import webdriver
from time import sleep
map = [
0x08, 0x0E, 0xFF, 0x0C, 0x09, 0x0D, 0xFF, 0x01, 0x0A, 0x0F, 0x03, 0x0B,
0x00, 0x02, 0xFF, 0x04, 0x01, 0x06, 0x03, 0x02, 0x05, 0x0A, 0x07, 0x00,
0x08, 0x09, 0xFF, 0x04, 0x0F, 0x0E, 0x0B, 0x0D, 0x0A, 0x00, 0xFF, 0x0D,
0x04, 0x0F, 0x03, 0x0B, 0x07, 0x05, 0x0E, 0x02, 0x06, 0x08, 0x0C, 0x01,
0x04, 0x0B, 0x05, 0x0F, 0xFF, 0x02, 0xFF, 0x0C, 0x06, 0x0D, 0x01, 0x00,
0xFF, 0x0A, 0x03, 0x09, 0x02, 0x0A, 0xFF, 0x03, 0x0D, 0x00, 0x0B, 0x05,
0x0C, 0xFF, 0x09, 0x01, 0xFF, 0x0F, 0x07, 0x0E, 0x0D, 0x07, 0x0C, 0x0B,
0x0F, 0x0E, 0x0A, 0x08, 0x00, 0xFF, 0x05, 0x03, 0x09, 0x06, 0x01, 0x02,
0xFF, 0x01, 0x0F, 0xFF, 0x0C, 0x09, 0x04, 0x06, 0x02, 0x0E, 0x0D, 0xFF,
0xFF, 0x03, 0x0A, 0xFF, 0x09, 0x04, 0x06, 0x0E, 0x02, 0x07, 0x01, 0x03,
0x0B, 0x08, 0x0A, 0x0F, 0x05, 0xFF, 0x00, 0x0C, 0xFF, 0x03, 0x0A, 0x07,
0x0E, 0x08, 0x0C, 0x04, 0x09, 0xFF, 0x00, 0x0D, 0x02, 0xFF, 0x06, 0xFF,
0x0C, 0x09, 0x01, 0xFF, 0x0B, 0x03, 0x0F, 0x0D, 0x0E, 0x0A, 0xFF, 0xFF,
0x08, 0x00, 0x04, 0x07, 0x06, 0x0D, 0x00, 0x08, 0x0A, 0x01, 0x02, 0xFF,
0xFF, 0x07, 0x04, 0x05, 0x0C, 0x0B, 0xFF, 0x0F, 0x0B, 0x02, 0x0E, 0xFF,
0x00, 0xFF, 0x05, 0xFF, 0x0F, 0x01, 0xFF, 0x0C, 0x0A, 0x09, 0x0D, 0x03,
0xFF, 0x0F, 0x0B, 0xFF, 0x03, 0x0C, 0xFF, 0x0E, 0x05, 0xFF, 0xFF, 0x09,
0xFF, 0x04, 0x08, 0x0A, 0x0E, 0x08, 0xFF, 0xFF, 0x07, 0x05, 0x0D, 0x0F,
0x04, 0x03, 0xFF, 0xFF, 0x01, 0x0C, 0x09, 0x00, 0xFF, 0x05, 0x0D, 0x09,
0x06, 0x04, 0x08, 0x0A, 0x01, 0x0C, 0x0F, 0x0E, 0xFF, 0x07, 0x02, 0x0B,
0x03, 0xFF, 0x04, 0x0A, 0xFF, 0x0B, 0x09, 0x02, 0x0D, 0x00, 0xFF, 0x08,
0x0E, 0xFF, 0x0F, 0x06
]
l = []
key = []
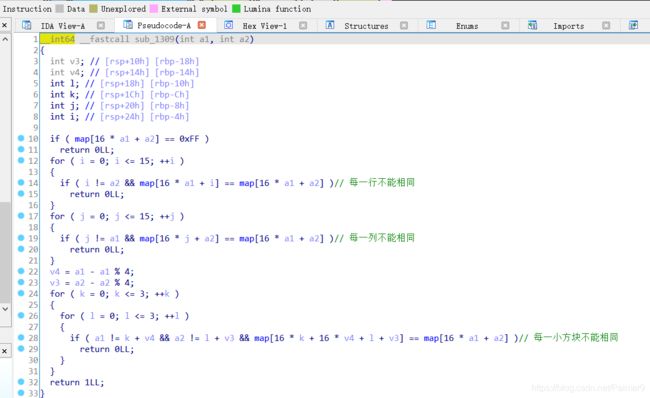
def warmup():
for i in range(16):
for j in range(16):
k = map[16 * i + j]
if k != 0xFF:
print(k + 1, '\t', end="")
l.append(k + 1)
else:
print('#\t', end='')
l.append("")
key.append(16 * i + j)
print('')
warmup()
# 4 自定义设置chrome路径,并用chromedriver控制
options = webdriver.ChromeOptions()
#options.add_argument('--headless')
#options.add_argument('--disable-gpu')
# chrome可执行文件的路径,需要修改chrome文件名
options.binary_location = r'F:\palmer\MiniSoftware\RunningCheeseChrome\App\chrom.exe'
bro = webdriver.Chrome(executable_path='./chromedriver.exe',
chrome_options=options)
bro.get('https://sudokuspoiler.azurewebsites.net/Sudoku/Sudoku16')
# page_source 获取浏览器当前页面的html源码数据
page_text = bro.page_source
input_list = bro.find_elements_by_tag_name('input')
print(input_list)
for i in range(256):
input_list[i].send_keys(l[i])
but = bro.find_element_by_xpath('//*[@id="solveButton"]')
sleep(1)
but.click()
sleep(5)
nflag = []
for i in key:
nflag.append(input_list[i].get_attribute('value'))
print(nflag)
# nflag = ['8', '7', '6', '13', '10', '9', '15', '8', '9', '7', '5', '5', '6', '1', '8', '12', '9', '14', '16', '12', '2', '6', '6', '3', '7', '10', '4', '15', '5', '7', '8', '9', '8', '2', '1', '3', '7', '14', '3', '7', '12', '11', '1', '4', '13', '2', '8', '6']
flag = ""
for i in nflag:
i = int(i, 10) - 1
if i < 10:
flag += (str(i))
else:
flag += (chr(87 + i))
print('flag{' + flag + '}')
# flag{765c98e78644507b8dfb1552693e467871026d26ba03c175}
bro.quit()