GDB内存调试初探四
Memory accessing beyond valid range
Here I present a problem of memory accessing beyond valid range for an integer array pointer, the following code has two functions named good_allocation and bad_allocation. Glancing through the code, we can easily find the bug and correct it, the bug is at line 210; but real problems are more difficult to examine and trying to find the hidden bug only by reading millions of lines of source code is simply not practical. Our job now is to find a general method to tackle problems of this particular type:
#include How the bug manifests itself
We need to know how the bug actually causes trouble for our small application. Compilation is important as to enable debugging information:
arm-linux-gnueabihf-g++ -std=c++11 -Wall -O1 -ggdb -march=armv7-a -marm -o access-beyond access-beyond.cpp
Next, as I’ve mentioned in another blog, we need to modify the executable file to load the correct shared libraries which also have debugging information linked in:
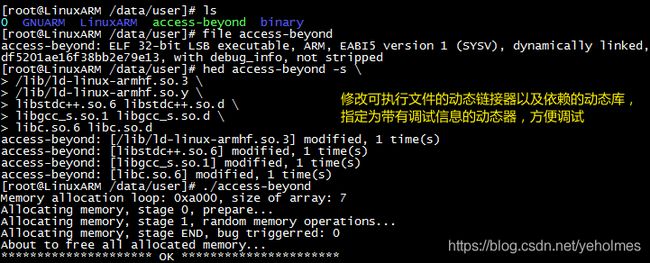
Now we can run the application. The results are stunning: the application random crashes and the crashing scenes vary greatly:
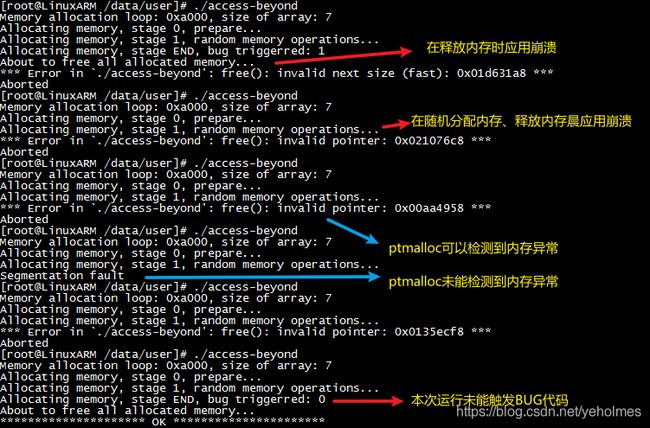
Then we employ the great GNU Debugger to load the application, examine the crashing application:
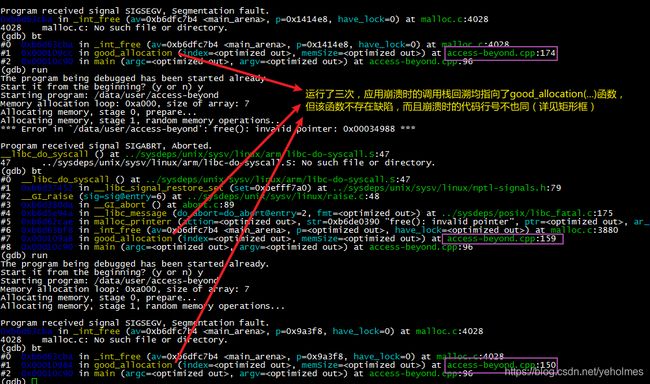
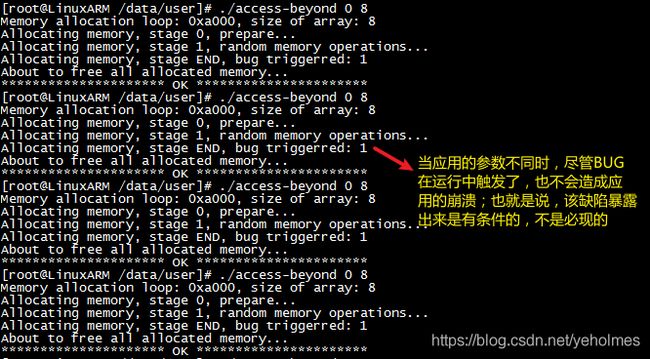
The bug does manifest itself in a bizarre manner: Sometimes the bug has been triggered but without causing application to crash; sometimes the bug will not trigger, and sometimes the bug causes the application to crash at very different locations. With different command-line arguments, the bug triggers but will never cause the application to crash:
Replacing memory allocation functions
Glibc has the ability to preload a shared library, to override some functions provided by other shared libraries(Details Here), via LD_PROLOAD environment variable set to point to the path of preloaded shared library. Please note that I do not claim to have invented the method to solve problems of this type, others have long used the method; but however, I have never read others’ work. The idea is simple: replace a set of memory allocation functions provided by Glibc and set a range of memory to read-only during the allocation of a or every chunk of memory. The complete source code is listed as bellow:
#include We need to compile the above code into a shared library:
arm-linux-gnueabihf-gcc -shared -Wall -O1 -ggdb -march=armv7-a -marm -o mymalloc.so mymalloc.c
Okay, now we can be 99% positive that by simply preloading the shared library mymalloc.so, we are able the find the bug:
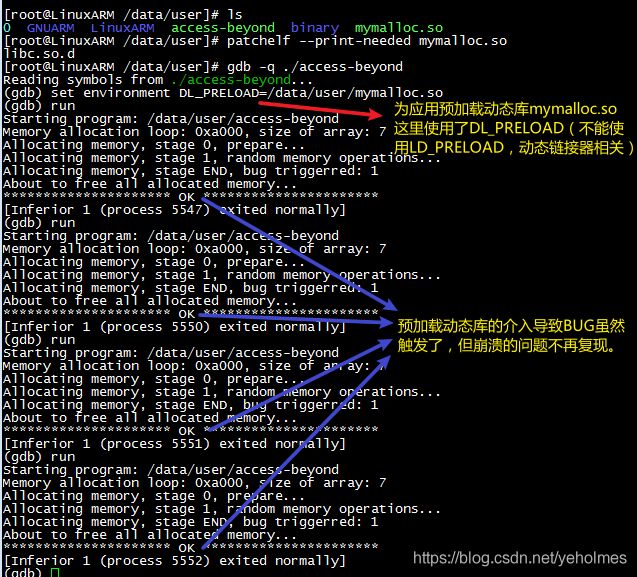
To our surprise, preloading mymalloc.so shared library causes the bug to silently go away without crashing the application! I know the reason why but it might be better left to anyone who is interested in the problem. What we should know now is that, setting a small chunk of memory to read-only will not sometimes solve our problem: it actually makes it worse. Recall that by setting the command-line arguments to 0 8, the application will not crash despite the bug will sometimes be triggered. We can again set the arguments and see what happens:
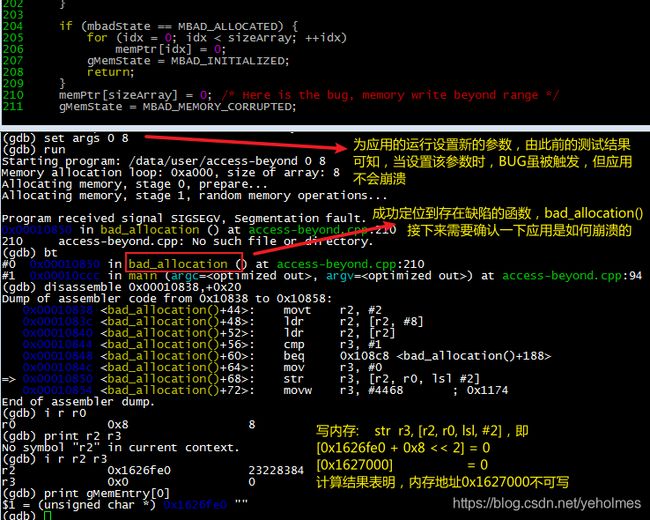
The code runs only once and the application crashes, and the stack back-tracing brings us to the buggy function bad_allocation(...)! What a strange debugging result! After careful calculation, we infer that pointer 0x1627000 is not writable:
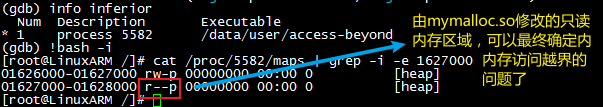
And the memory map of our small application does indicate that pointer address 0x1627000 is read-only. Now as the case is closed, and with the bug found, we can next correct the bug.
Conclusion
Again, I do not invent the method to solve problems of this type, and the method presented here sometimes fails to help us to find the bug, accessing beyond valid range of memory. Next, we need to craft another similar but different method to solve the bug.