1 Introduction “Information at your fingertips anywhere, anytime” has been the driving vision of mobile computing for the past two decades. Throughrelentless pursuit of this vision, spurring innovations in wireless technology, energy-efficient portable hardwareand adaptive software, we have now largely attained this goal. Ubiquitous email and Web access is a reality that is experienced by millions of users worldwide through their BlackBerries, iPhones, Windows Mobile, and other portable devices. Continuing on this road, mobile Web-based services and location-aware advertising opportunities have begun to appear, triggering large commercial investments. Mobile computing has arrived as a lucrative business proposition. What will inspire our research in mobile computing over the next decade and beyond? We begin by considering two hypothetical mobile computing scenarios from the future. We then extract the deep assumptions implicit in thesescenarios, and use them to speculate on the future trajectory of mobile computing. We conclude that there are really two fundamentally distinct strategies atplay, and that the dialectic between these strategies will largely shape the mobile computing landscape of the future.
“信息随时随地都在您的指尖”
一直是移动计算的驱动愿景
过去二十年。通过不懈的追求
这一愿景,激发了无线技术,节能便携式硬件和自适应技术的创新
软件,我们现在基本上达到了这个目标。
无处不在的电子邮件和Web访问是现实
通过全球数百万用户体验
他们的黑莓,iPhone,Windows Mobile和
其他便携式设备。继续走这条道路,移动的基于Web的服务和位置感知广告机会已经开始出现,触发
大型商业投资。移动计算
已经成为一个有利可图的商业主张。
在未来十年甚至更长时间内,我们的移动计算研究能够激发什么?我们从一开始
从未来考虑两个假设的移动计算方案。然后,我们提取这些场景中隐含的深层假设,并使用它们
推测移动计算的未来发展轨迹。我们的结论是,实际上有两种根本不同的策略在起作用,而这些策略之间的辩证法将在很大程度上塑造这种策略
移动计算未来的景观。
2 Scenario 1: Lost Child Five-year old John is having a wonderful time with his family at the Macy’s Thanksgiving Day parade in Manhattan. Mid-way through the parade, John sees a group of friends in the crowd nearby. He shows his parents where his friends are, and tells them he is going over to meet them. Since his parents see responsible adults in the group, they are fine with John walking over to see his friends. An hour later, John’s parents walk over to where they expect to find him. To their shock, they discover that the friends have not seen John at all. He has been missing for an entire hour now, and John’s parents are very concerned. Searching for a lost child in a Manhanttan crowd is a daunting task. Fortunately, a police officer nearby is able to send out an amber alert via text message to all smartphone users within two miles. He requests them to upload all photographs they may have taken in the past hour to a secure web site that only the police can view. In a matter of minutes, the web site is populated with many photographs. New photographs continue to arrive as more people respond to the amber alert. With John’s parents helping him, the police officer searches these photographs with an application on his smartphone. His search is for the red plaid shirt that John was wearing. After a few pictures of Scottish kilts in the parade, a picture appears that thrills John’s parents. In a corner of that picture, barely visible, is a small boy in a red shirt sitting on the steps of a building. The police officer recognizes the building as being just two blocks further down the parade route, and contacts one of his fellow officers who is closer to that location. Within moments, the officer is with the boy. John is safe now, but he has a lot of explaining to do ...
2情景1:失去的孩子
五岁的约翰正在度过美好的时光
他的家人在梅西百货的感恩节游行
曼哈顿。约翰看到,在游行的中途
一群朋友在附近的人群中。他显示
他的父母在他的朋友所在的地方,告诉他们
正在过去见他们。由于他的父母在小组中看到负责任的成年人,他们对John很好
走过去看他的朋友们。一个小时后,约翰的
父母走到他们希望找到他的地方。
令他们震惊的是,他们发现朋友们没有
看见约翰。他一整个都失踪了
现在一小时,约翰的父母非常担心。
在Manhanttan人群中寻找失踪的孩子是
一项艰巨的任务。
幸运的是,附近的一名警察能够派遣
通过短信向两英里内的所有智能手机用户发出琥珀色警报。他要求他们
上传他们拍摄的所有照片
过去一小时到一个只有警察可以的安全网站
视图。在几分钟内,网站就会被填充
有很多照片。新照片继续
随着更多人回应琥珀警报而到达。
约翰的父母帮助他,警察
通过申请搜索这些照片
他的智能手机他搜索的是红色格子衬衫
约翰穿的。在游行队伍中苏格兰短裙的几张照片后,一张照片显得格外刺激
约翰的父母。在那张照片的一角,几乎没有
可见,是一个穿着红色衬衫的小男孩坐在上面
建筑的步骤。警察认出了这一点
建筑只是两个街区
游行路线,并与他的一名同事联系
谁离那个地方更近。片刻之内
军官和男孩在一起。约翰现在很安全,但他有一个
很多解释要做...
3 Scenario 2: Disaster Relief The Big One, measuring 9.1 on the Richter scale, has just hit Northern California. The entire Bay Area is one seething mass of humanity in anguish. Many highways, power cables and communication lines are severely damaged. Disaster on such a scale has not been seen since World War II. With limited manpower, unreliable communication and marginal transportation, disaster relief personnel are stretched to the limit. Internet infrastructure, including many key data centers, have been destroyed. The Googleplex has been reduced to a smoking hulk. In spite of heroic efforts, disaster relief is painfully slow and hopelessly inadequate relative to the scale of destruction. Sudden obsolescence of information regarding terrain and buildings is a major contributor to slow response. Vital sources of knowledge such as maps, surveys, photographs, building floor plans, and so on are no longer valid. Major highways on a map are no longer usable. Bridges, buildings, and landmarks have collapsed. GoogleEarth and GoogleMaps are now useless for this reqion. Even the physical topography of an affected area may be severely changed. Conducting search and rescue missions in the face of obsolete information is difficult and dangerous. New knowledge of terrain and buildings has to be reconstructed from scratch at sufficient resolution to make important life and death decisions in search and rescue missions. In desperation, the rescue effort turns to an emerging technology: camera-based GigaPan sensing. Using off-the-shelf consumer-grade cameras in smartphones, local citizens take hundreds of close-up images of disaster scenes. Transmission of these images sometimes occurs via spotty low-grade wireless communication; more often, the images are physically transported by citizens or rescue workers. The captured images are then stitched together into a zoomable panorama using compute-intensive vision algorithms. To speed up the process, small GigaPan robots that can systematically photograph a scene with hundreds of close-up images are air-dropped over the area for use by citizens. Slowly and painstakingly, detailed maps and topographical overlays are constructed bottom-up. As they become available, rescue efforts for those areas are sped up and become more effective. Rescuing trapped people is still dangerous, but at least the search teams are now armed with accurate information that gives them a fighting chance ...
3情景2:赈灾
The Big One,里氏9.1级,
刚刚袭击北加州。整个海湾
面积是痛苦的人类中的一个沸腾。
许多高速公路,电力电缆和通信
线条严重受损。这样的灾难
自第二次世界大战以来,没有看到过规模。同
有限的人力,不可靠的沟通和
边际交通,救灾人员
被拉伸到极限。互联网基础设施,包括许多关键数据中心,已被销毁。
Googleplex已经变成了一个吸烟的废船。
尽管做出了英勇的努力,但救灾却是痛苦的
相对于规模来说,缓慢且绝望地不足
破坏。
关于地形和建筑物的信息突然过时是导致响应缓慢的主要原因。重要的知识来源,如地图,
调查,照片,建筑平面图等
不再有效。地图上的主要高速公路是
不再可用。桥梁,建筑物和地标
已经崩溃了。 GoogleEarth和GoogleMaps是
现在对这个要求毫无用处。甚至受影响区域的物理地形也可能会发生严重变化。
面对的执行搜救任务
过时的信息既困难又危险。新
必须以足够的分辨率从头开始重建地形和建筑物的知识
搜索和救援任务中重要的生死决定。
无奈之下,救援工作转向了一项新兴技术:基于摄像头的GigaPan传感。当地公民在智能手机中使用现成的消费级相机,拍摄数百张灾难场景特写图像。这些图像的传输有时通过参差不齐的低级无线发生
通讯;更常见的是,图像是由公民或救援人员物理运输的。该
然后将拍摄的图像拼接成一个
使用计算密集型视觉的可缩放全景
算法。为了加快这个过程,小GigaPan
可以系统地拍摄场景的机器人
数以百计的特写图像都是空投的
在该地区供公民使用。
慢慢地,艰苦地,自下而上地构建详细的地图和地形覆盖。如
它们变得可用,这些区域的救援工作加快并变得更加有效。拯救被困人员仍然是危险的,但至少是
搜索团队现在拥有准确的信息,给他们一个战斗机会......
4 Reflecting on these Scenarios These scenarios embody a number of themes that will be central to the evolution of mobile computing over the next decade. We explore these themes next. Common to both scenarios is the prominent role of mobile devices as rich sensors. While their computing andcommunicaton roles continue to be important, it is their rich sensing role (image capture) that stands out most prominently in these scenarios. We use the term “rich” to connote the depth and complexityabout the real world that is being captured. This is in contrast to simple scalar data such as temperature, time and location that are involved in typical sensor network applications. When cell phones with integrated cameras first appeared, people wondered if they represented a solution in search of a problem. Would mobile users take so many photographs that this capability was worth supporting? Today, the value of this functionality is no longer questioned. Tomorrow the roles will be reversed: people will wonder why any digital camera lacks the wireless capability to transmit its images. Video capture, leading to even richer sensing and recording of the real world is also likely to gain traction. A second emergent theme is that of near-real-time data consistency. This is most apparent in the lost child scenario, where the only useful images are very recent ones. Pictures taken before the child was lost are useless in this context. Recency of data is also important in the disaster relief scenario. A major earthquake is often followed by aftershocks for hours or possibly days. These aftershocks can add to the damage caused by the original quake, and in some cases be the “tipping point” that triggers major structural and topographical changes. Regions that have already been mapped after the original quake may need to be remapped. The need for near-real-time data consistency forces rethinking of a long line of work in mobile computing that relates to the use of prefetching and hoarding for failure resiliency. The core concepts behind those techniques may still be valuable, but major changes in their implementations may have to be developed in order to apply them to the new context. In the disaster relief scenario, for example, many old maps and photographs may still be valid if the buildings and terrain involved have only been minimally affected. However, discovering whether it is acceptable to use hoarded information about them is a challenge. No central authority (e.g. a server) can answer this question with confidence. Only an on-the-spot entity (e.g. a user with a mobile device) can assess whether current reality is close enough to old data for safe reuse. That determination may involve human judgement, possibly assisted by software (e.g. a program that compares two images to estimate disruption). A third emergent theme is that of opportunism. This is most evident in the lost child scenario. The users who contribute pictures were completely unaware of their potential use in searching for the lost child. They took the pictures for some other reason, such as a funny float in the parade. But because of the richness of the sensed data, there are potentially “uninteresting” aspects of the image (e.g. small child in the corner of the picture) that prove to be very important in hindsight — it iscontextthat determines importance. Although the theme of opportunism also applies to simpler sensed data (e.g., anti-lock braking devices on cars transmit their GPS coordinates on each activation, enabling a dynamic picture of slick spots on roads to be obtained by maintenance crews), the richness of captured data greatly increases the chances for opportunistic reuse. An airport video image that was deemed uninteresting on 9/10/2001 may prove to be of high interest two days later because it includes the face of a 9/11 hijacker. With such opportunism comes, of course, many deep and difficult questions pertaining to privacy. While these questions already exist today with mining data from surveillance cameras, they will grow in frequency and significance as mobile users increasingly contribute their rich sensed data. One can easily imagine a business model that provides small rewards for contributors of such data, while reaping large profits by mining aggregated data for customers. A final emergent theme is the need to broaden our definition of “mobile computing” to embrace developments that lie well outside our narrow historical concerns. Examples include non-indexed image search in the lost child scenario and GigaPan technology in the disaster relief scenario. These may feel like science fiction, but they arereality today.
4反思这些情景
这些场景体现了许多主题
将成为移动计算发展的核心
在接下来的十年里。我们接下来探讨这些主题。
这两种情景的共同点是
移动设备作为丰富的传感器虽然他们的计算和沟通角色仍然很重要,但是他们的丰富感知角色(图像捕捉)才是
在这些场景中最突出的是突出的。我们
使用“富”这个词来表示正在捕捉的现实世界的深度和复杂性。
这与典型传感器网络应用中涉及的简单标量数据(例如温度,时间和位置)形成对比。当手机
随着集成摄像头的首次出现,人们想知道他们是否代表了寻找解决方案的解决方案
问题。移动用户会拍这么多照片吗?这个功能值得支持吗?
今天,这个功能的价值不再存在
质疑。明天角色将被逆转:
人们会想知道为什么任何数码相机都没有
无线传输其图像的能力。视频捕捉,导致更丰富的感应和录音
现实世界也可能获得牵引力。
第二个新兴主题是近乎实时的主题
数据一致性。这在失落中最为明显
子场景,其中唯一有用的图像非常有用
最近的。孩子失踪前拍的照片
在这种情况下是无用的。数据的新近度也是
在救灾方案中很重要。一个主要的
地震往往伴随着几个小时的余震
或者可能是几天。这些余震可以增加
原始地震造成的破坏,有些
案例是引发重大结构和地形变化的“临界点”。有的区域
已经在原始地震发生后进行了映射
需要重新映射。需要近乎实时的
数据一致性迫使人们重新思考
从事与移动计算相关的工作
预取和囤积故障恢复能力。该
这些技术背后的核心概念可能仍然存在
有价值的,但实施的重大变化
可能必须开发才能应用它们
新的背景。在救灾情景中,为
例如,许多旧地图和照片可能仍然存在
如果涉及的建筑物和地形有效,则有效
只受到了极少的影响。但是,发现使用有关它们的囤积信息是否可以接受是一项挑战。没有中央权威
(例如服务器)可以放心地回答这个问题。只有现场实体(例如,有用户的用户)
移动设备)可以评估当前的现实情况
与旧数据足够接近以便安全重用。这种决定可能涉及人类的判断
由软件辅助(例如,比较的程序)
估计中断的两个图像)。
第三个新兴主题是机会主义。
这在丢失的儿童情景中最为明显。该
贡献图片的用户完全没有意识到他们在搜索丢失时的潜在用途
儿童。他们出于其他原因拍了照片,
比如在游行中有趣的浮动。但是因为
感知数据的丰富性,有潜力
图像的“无趣”方面(例如小孩子)
在事后证明是非常重要的 - 在图片的角落 - 它是确定的背景
重要性。虽然机会主义的主题也是如此
适用于更简单的感测数据(例如,汽车上的防抱死制动装置传输其GPS坐标
每次激活,都能实现光滑的动态画面
维修人员获得的道路上的斑点),
捕获数据的丰富性大大增加了
机会性重用的机会。机场视频
在9/10/2001被认为无趣的形象
两天后可能被证明具有高度兴趣,因为它包括了9/11劫机者的面孔。同
当然,这种机会主义很多都是深刻的
与隐私有关的疑难问题。虽然这些
今天已经存在的问题与挖掘数据有关
监控摄像机,它们会频繁增长
移动用户越来越多地贡献他们丰富的感知数据。人们很容易想象出一种能够提供小额奖励的商业模式
这些数据的贡献者,同时获得巨额利润
通过为客户挖掘汇总数据。
最后一个突出的主题是需要扩大我们对“移动计算”的定义,以接受远远超出我们狭隘的历史关注的发展。示例包括非索引图像
在救灾情景中搜索丢失的儿童情景和GigaPan技术。这些可能会感觉到
像科幻小说,但它们今天是现实。
For example, consider GigaPan technology. Figure 1(a) shows a 5.6 gigapixel panorama that has been stitched together from 378 individual images captured with a consumer-grade digital camera. The software available for navigating such an image allows a user to probe the panorama at very high zoom levels, much like GoogleEarth. This image, and many others, can be explored at the GigaPan web site (http://www.gigapan.org) [5]. The level of detail can be astonishing. For example, Figure 1(b) shows a legible warning sign at a lifeguard station. In Figure 1(a), the entire lifeguard station is barely visible as a speck on the distant beach. Figure 2(a) is relevant to the disaster relief scenario. It shows a panorama stitched together from 225 individual images of downtown Port Au Prince, Haiti that were taken by a news reporter who was covering the earthquake relief effort. These images were stitched together after the reporter’s return to the United States, since the stitching capability was not available at the disaster site. Figure 2(b) shows a zoomed-in view of damaged electrical infrastructure, including the ID number of the tower that has been destroyed. Imagine how valuable this sensing and mapping capability would be if it were available at large scale at a disaster site, very soon after the disaster strikes.
例如,考虑GigaPan技术。图1(a)显示了一个5.6千兆像素的全景图
从378个单独的图像缝合在一起
使用消费级数码相机拍摄。该
可用于导航这种图像的软件允许用户以非常高的变焦探测全景
级别,很像GoogleEarth。这个图像,和
许多其他人,可以在GigaPan网站上进行探索
网站(http://www.gigapan.org)[5]。细节水平可能令人惊讶。例如,图1(b)
在救生站显示一个清晰的警告标志。
在图1(a)中,整个救生站几乎没有
在遥远的海滩上可见一斑点。图2(a)
与救灾情景有关。它显示了一个
从海地太子港市中心的225张个人照片拼凑而成的全景
由一位报道抗震救灾工作的新闻记者拍摄。记者返回美国后,这些照片拼凑在一起,
因为没有拼接功能
灾难现场。图2(b)显示了放大视图
损坏的电气基础设施,包括身份证
被摧毁的塔的数量。想象一下这种传感和映射能力有多么宝贵
灾难发生后很快就会在灾难现场大规模提供。
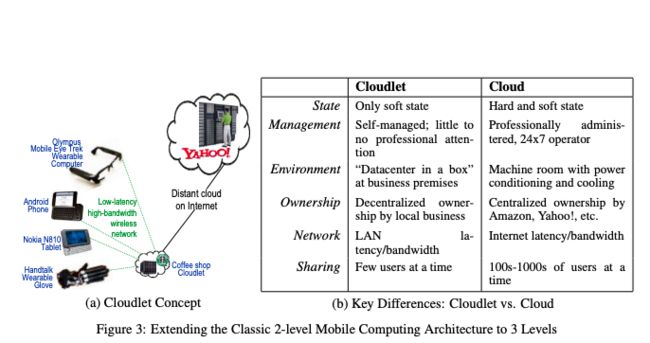
三层网络结构:
Cloudlet Cloud
状态仅软状态硬和软状态
管理自我管理; 很少
没有专业的关注
专业管理,24x7运营商
环境“数据中心在一个盒子里”
在营业场所
机房有电
调节和冷却
所有权分散本地业务的所有权
集中所有权
亚马逊,雅虎等等
网络LAN延迟/带宽
互联网延迟/带宽
一次共享少数用户100s-1000s的用户
时间
5 Transient Infrastructure Since birth, mobile computing has implicitly assumed a 2-level hierarchy. Originally, the two levels were identified as “servers” and “clients.” More recent terminology uses “cloud” to connote the computational and information resources represented by a collection of servers. Regardless of terminology, however, the 2-level concept is woven quite deeply into our thinking about mobile computing. The upper layer (“cloud” or “server”) is assumed to bewellmanaged, trusted by the lower layer, and free from concerns that are specific to mobility such as battery life and size/weight constraints. Future architectures for mobile computing are likely to extend this 2-level hierarchy to at least one additional layer, possibly more. The case for an intermediate layer called a cloudlet was articulated in a recent paper [3]. In that work, the rationale offered for the architectural extension is low latency network communication to computational resources in order to enable a new genre of immersive mobile applications. Cloudlets are viewed as decentralized and widely-dispersed Internet infrastructure whose compute cycles and storage resources can be leveraged by nearby mobile computers. A natural implementation is to extend Wi-Fi access points to include substantial processing, memory and persistent storage for use by associated mobile devices. A cloudlet can be viewed as a “data center in a box.” It is self-managing, requiring little more than power, Internet connectivity, and access controlfor setup. This simplicity of management corresponds to an appliance model of computingresources, and makes it trivial to deploy. For safe deployment in unmonitored areas, the cloudlet may be packaged in a tamper-resistant or tamper-evident enclosure with third-party remote monitoring of hardware integrity. Figure 3(b) summarizes some of the key differences between cloudlets and clouds. Most importantly, a cloudlet only contains soft state such as cache copies of data or code that is available elsewhere. Loss or destruction of a cloudlet is hence not catastrophic. This stateless model leads to an important research challenge: how can a mobile device rapidly and safely customize a cloudlet for its specific use? A possible solution, based on dynamic virtual machine synthesis, is sketched in [3]. Other approaches may also need to be explored. Although originally motivated by considerations of network latency, cloudlets have much broader relevance. In particular, they are relevant to both the scenarios presented earlier. The GigaPan approach relies on compute-intensive vision algorithms to stitch together a zoomable panorama from individual images. Under normal conditions, these algorithms can be executed in the cloud. However, cloud computing may be compromised in the aftermath of a disaster. The physical infrastructure necessary for good Internet connectivity may have been destroyed and it may be many days or weeks before these can be repaired. Limited Internet connectivity may be re-established soon after the catastrophic event, but there will be very high demand on this scarce resource from diverse sources: families trying to desperately learn and share information about the fate of loved ones, citizen reporters and professional journalists sharing videos, images, blogs, and tweets of the disaster area with the outside world, and disaster relief agencies coordinating their efforts with their home bases. Under these conditions, cloudlets may be needed to support cloud computing. We envision opportunistic deployment of cloudlets in disaster relief. In the immediate aftermath of a disaster, before external IT supplies have arrived, any available hardware such as an undamaged desktop can be pressed into service as a cloudlet. A cloudlet can even be built around a high-end laptop, with its few hours of battery life being priceless prior to the arrival of emergency electrical generators. As IT supplies arrive, temporary cloudlets may be replaced by purpose-designed equipment. Cloudlets also have relevance to the lost child scenario. In that scenario, the near-real-time image search will require extensive computation since pre-computed indexes are not available for the contributed images. Cloud computing is the obvious answer for this, but exactly where in the cloud to compute is an open question. The task involvessubmission of images from a lot of people in the immediate neighborhood of the lost child; the search results will also be viewedthere. This suggestsuse of local infrastructure (i.e., a cloudlet) rather than distant infrastructure. Once the search is completed (successfully or unsuccessfully) the contributed images can be discarded. This fits well with the stateless model of cloudlets and their use as transient infrastructure.
5瞬态基础设施
自诞生以来,移动计算已隐含地假定为2级层次结构。最初,这两个级别被确定为“服务器”和“客户端”。更多
最近的术语使用“云”来表示由...表示的计算和信息资源
一组服务器。无论术语如何,
然而,2级概念编织得相当深刻
进入我们对移动计算的思考。假设上层(“云”或“服务器”)管理良好,由下层信任,并且没有
特别针对移动性的问题,如电池
生活和尺寸/重量限制。
未来的移动计算架构是
可能会将这个2级层次结构扩展到至少一个
附加层,可能更多。关于称为cloudlet的中间层的情况已被明确表达
最近的一篇论文[3]。在这项工作中,提出了理由
对于架构扩展是低延迟网络
按顺序与计算资源进行通信
实现一种新型的沉浸式移动应用程序。 Cloudlets被视为分散的
广泛分散的互联网基础设施,可以利用其计算周期和存储资源
附近的移动电脑。一种自然的实现方式是扩展Wi-Fi接入点,以包括大量处理,内存和持久存储
供相关移动设备使用。
云可以被视为“数据中心”
“这是自我管理,只需要一点点
电源,互联网连接和设置的访问控制。这种简单的管理相对应
到计算资源的设备模型,和
使部署变得微不足道。为了安全部署
在不受监控的区域,可以打包云
防篡改或防篡改外壳
第三方远程监控硬件完整性。
图3(b)总结了cloudlet和云之间的一些关键差异。最重要的是,cloudlet只包含软状态,如
缓存其他地方可用的数据或代码的副本。因此,云的丢失或破坏不是
灾难性的。这种无状态模型带来了一个重要的研究挑战:移动设备如何
为特定用途快速安全地定制cloudlet?基于动态虚拟机综合的可能解决方案在[3]中概述。其他
也可能需要探索方法。
虽然最初的动机是考虑因素
对于网络延迟,cloudlets有更广泛的应用
关联。特别是,它们与两者都相关
前面介绍的情景。 GigaPan方法依赖于计算密集型视觉算法
从单个图像拼接可缩放的全景图。在正常情况下,这些算法可以在云中执行。但是,云
计算可能会在后果中受到影响
灾难。必要的物理基础设施
良好的互联网连接可能已被破坏
这些可能需要很多天或几周
得到修复。有限的互联网连接可能是
灾难性事件发生后不久就重新建立,但对来自不同来源的稀缺资源的需求非常高:家庭试图拼命学习和分享有关命运的信息。
亲人,公民记者和专业记者分享视频,图像,博客和推特
灾区与外界,灾难
救济机构与他们协调他们的努力
家庭基地。在这些条件下,cloudlets可能会
需要支持云计算。
我们设想机会主义部署
救灾中的小云。在灾难发生后,在外部IT供应之前
已经到了,任何可用的硬件,如
未损坏的桌面可以作为服务使用
一个小云。甚至可以围绕a建立一个cloudlet
高端笔记本电脑,电池续航时间短
在紧急情况到来之前是无价的
发电机。随着IT供应的到来,临时cloudlet可能会被特定设计所取代
设备。
Cloudlets还与失去的孩子有关
场景。在那种情况下,近实时图像搜索将需要大量计算
预先计算的索引不适用于提供的图像。云计算就是明显的答案,但云计算的确切位置是一个悬而未决的问题。这项任务涉及从失踪儿童附近的许多人那里提交图像;搜索结果
也会在那里看到。这表明使用本地
基础设施(即云端)而不是远程基础设施。一旦搜索完成(成功或不成功),贡献的图像就可以
被丢弃这非常适合无状态模型
cloudlet及其作为瞬态基础设施的用途。
6 Competing Design Strategies So far, this paper has focused on how mobile computing today and tomorrow differs from the past. Amidst all this change, however, certain fundamental challenges of mobility have remained invariant since they were articulated over 15 years ago [2]. First, wireless connectivity is highly variable in performance and reliability. Many real-world factors hinder ubiquitous high-bandwidth wireless connectivity. For example, Wi-Fi connectivity in public spaces often requires a subscription or one-time payment to the service provider. In private spaces (such as inside a customer’s premises), there may be organizational or access control reasons that prevent Wi-Fi connectivity. 3G or 4G connectivity has wider coverage, but offers signifiantly poorer bandwidth. Even these lower-bandwidth alternatives are sometimes unavailable within buildings. Finally, there are situations where wireless transmissions are forbidden: for example, during air travel. Second, mobile hardware is necessarily resourcepoor relative to static client and server hardware. Considerations of weight, size, battery life, ergonomics, and heat dissipation exact a severe penalty in processor speed, memory size, disk capacity, etc. For a user, a mobile device can never be too small, too light or have too long a battery life. While mobile hardware continues to evolve and improve, computation on mobile devices will always be a compromise. An additional obstacle is the slow pace of improvement in battery technology, especially when compared to Moore’s Law. The first challenge (uncertain connectivity) leads to a “Swiss Army Knife” design philosophy: try to cram as much functionality as possible into a compact design that is self-contained and as frugal as possible in resource usage. Unfortunately, this approach often compromises usability, just as the tools in a real Swiss Army Knife (such as knife, fork, can opener, and corkscrew) are poor substitutes for full-sized implementations. Miniscule displays and keyboards are especially challenging for mobile users, particularly in the context of a graying population. Unfortunately, the incentives of today’s marketplace tend to reward itemizable functionality enhancements rather than improvements to more diffuse attributes such as usability. The second challenge (resource poverty) combined with the limitations of the Swiss Army Knife approach will eventually lead to a very different design philosophy. Rather than relying exclusively on a self-contained mobile device, one can use that device to leverage other resources such as a distant cloud, a nearby cloudlet, or an interaction device such as a large display. We refer to this as a “wallet” design philosophy because it resembles the role of wallets in everyday life. A typical wallet contains things like cash, credit cards, and ID cards. None of these items are intrinsically valuable. Rather, their value lies in their ability to elicit useful goods and services on demand from the environment. Using a large wall-mounted display to augment the small display of a mobile device is an intriguing possibility. Transient use of displays in public spaces was prophesized almost two decades ago by Weiser’s seminal paper on ubiquitous computing [4]. Today, there is a convergence of hardware and software technologies that are relevant to this aspect of Weiser’s vision. In the near future, we envision a typical mobile user walking up to a display and using it for tasks that benefit from substantial screen real estate (including collaborative tasks and games). Privacy-sensitive information can be presented to the user on the mobile device, augmenting the less sensitive information that is presented on the large public display. User interactions may also occur through the mobile device. The future evolution of mobile computing systems will largely be driven by the dialectic between resource poverty and uncertain connectivity. Reconciling their contradictory demands will itself be a challenge. Only an adaptive system design that can dynamically switch between a “wallet” mode of operation and a “Swiss army knife” mode is likely to produce satisfactory results. A counterpoint to the “resource-poor mobile device immersed in resource-rich surroundings” paradigm is the state of affairs in the developing world. There, the mobile device is often the most technologically advanced entity in its surroundings. This leads to unique opportunities for high impact, but also requires out-of-the box thinking. A good example is the CAM framework for secure document processing via mobile phones in the developing world [1]. The concept of embedding programs for processing paper documents directly on those documents as 2D bar codes, and using smartphones to decode and process these programs, is an innovation directly inspired by the challenges of the developing world. As the old saying goes, “Necessity is the mother of invention.” It has never been more true than in mobile computing!6竞争设计策略到目前为止,本文主要关注当前和未来的移动计算与过去的不同之处。然而,在所有这些变化中,流动性的某些基本挑战自15年前就被阐明以来一直保持不变[2]。首先,无线连接的性能和可靠性差异很大。许多现实因素阻碍了无处不在的高带宽无线连接。例如,公共场所的Wi-Fi连接通常需要订购或一次性支付给服务提供商。在私人空间(例如客户内部),可能存在阻止Wi-Fi连接的组织或访问控制原因。 3G或4G连接覆盖范围更广,但带宽明显较差。即使这些低带宽替代品有时也无法在建筑物内使用。最后,存在禁止无线传输的情况:例如,在空中旅行期间。其次,移动硬件必然是相对于静态客户端和服务器硬件的资源。对重量,尺寸,电池寿命,人体工程学和散热的考虑严重影响处理器速度,存储器大小,磁盘容量等。对于用户而言,移动设备永远不能太小,太轻或太长电池寿命。虽然移动硬件不断发展和改进,但移动设备上的计算始终是一种妥协。另一个障碍是电池技术的改进步伐缓慢,特别是与摩尔定律相比。第一个挑战(不确定的连接性)导致了“瑞士军刀”的设计理念:尽可能将尽可能多的功能融入紧凑的设计中,这种设计是独立的,并且在资源使用方面尽可能节俭。不幸的是,这种方法通常会影响可用性,就像真正的瑞士军刀(如刀,叉,开罐器和开瓶器)中的工具不是全尺寸实施的替代品一样。微型显示器和键盘对于移动用户来说尤其具有挑战性,特别是在人口老龄化的情况下。不幸的是,当今市场的激励倾向于奖励可列表的功能增强,而不是改进更易扩散的属性,如可用性。第二个挑战(资源贫困)与瑞士军刀方法的局限性相结合,最终将导致一种截然不同的设计理念。可以使用该设备来利用其他资源,例如远程云,附近的云,或诸如大型显示器的交互设备,而不是完全依赖于自包含的移动设备。我们将此称为“钱包”设计理念,因为它类似于钱包在日常生活中的作用。典型的钱包包含现金,信用卡和身份证等物品。这些物品都不具有内在价值。相反,它们的价值在于它们能够根据环境需求获取有用的商品和服务。使用大型壁挂式显示器来增强移动设备的小型显示器是一种有趣的可能性。近二十年前Weiser关于普适计算的开创性论文预言了公共场所中显示器的瞬时使用[4]。如今,与Weiser愿景的这一方面相关的硬件和软件技术融合在一起。在不久的将来,我们设想一个典型的移动用户走到显示器并将其用于受益于大量屏幕空间(包括协作任务和游戏)的任务。可以在移动设备上向用户呈现隐私敏感信息,增加在大型公共显示器上呈现的较不敏感的信息。用户交互也可以通过移动设备发生。移动计算系统的未来发展将主要受资源贫困与不确定连通性之间的辩证关系驱动。调和他们的矛盾需求本身就是一个挑战。只有能够在“钱包”操作模式和“瑞士军刀”模式之间动态切换的自适应系统设计才有可能产生令人满意的结果。与“资源贫乏的移动设备沉浸在资源丰富的环境中”范式相对应的是发展中国家的现状。在那里,移动设备通常是其周围环境中技术最先进的实体。这为高影响力带来了独特的机会,但也需要开箱即用的思维。一个很好的例子是用于通过发展中国家的移动电话进行安全文档处理的CAM框架[1]。将用于处理纸质文档的程序直接嵌入这些文档作为二维条形码,并使用智能手机解码和处理这些程序的概念,是一项直接受到发展中国家挑战启发的创新。正如那句老话所说的那样,“必然性是发明的母亲。”它从未像动员一样真实