Reconnaissance
这种关就是人肉一个人,比较蛋疼,不是,是非常蛋疼。
Alexander Taylor( CSAW CTF Qualification Round 2013 )
这个逼把key藏在了官网judges介绍的图片里,非常阴险,就是这货
打开这个图片那python脚本看一下图片的信息,其中有3个tExt的段有tips
大概意思就是让我们找到存储信息的chunk
tEXt:0x25 Length:0x0000002b Context:These aren't the chunks you're looking for. tEXt:0x5c Length:0x0000001f Context:You can go about your business. tEXt:0x87 Length:0x0000000b Context:Move along.自己写一个找非法名字chunk的脚本,运行一下找到了两段比较奇怪的chunk
offset = 8
while (1):
tunck_name = text[offset+4:offset+8]
length = int(binascii.b2a_hex(text[offset:offset+4]),16)
if (tunck_name not in chunkname):
print tunck_name
print "offset:0x%x" % (offset)
print "length:0x%x" % (length)
print binascii.b2a_hex(text[offset+8:offset+8+length])
if (tunck_name=="IEND"):
break
offset = offset + length + 12 根据名字我们好像需要把他们怎么 xor一下子
xORk offset:0xaf length:0x4 43534157 kTXt offset:0x42f2c length:0x34 2836382c100304140a150814020708180d00610416110b12000761030c73021f021d0612630408030b1c1403631d0e030a10042a再来一个脚本,来计算xor的结果
for i in range(52):
print chr(int(a[(i%4)*2:(i%4)*2+2],16) ^ int(b[i*2:i*2+2],16)), OK~这样key就出来了
k e y { S P E C I F I C A T I O N S S U B J E C T T O C H A N G E W I T H O U T N O T I C E }
Julian Cohen( CSAW CTF Qualification Round 2013 )
这货在比赛的时候,其实已经快要找到答案了。
他在twitter和wiki上面分别留下了网站, http://catsoncupcakes.com/ 和 http://omnom.nom.co/
其实只要把域名换成IP访问就可以出key了 http://23.23.196.37/
这两个域名也是绑在同一IP下的,DNS解析的时候会带着请求域名的信息,服务提通过这个信息指定不同目录。
Jordan Wiens( CSAW CTF Qualification Round 2013 )
这个题目给了个网站http://key.psifertex.com上面说,那么就去人肉这个叫做迈克尔的人
Michael Vario sure does some suspicious signs, hope he doesn't do me.找啊找啊找啊找,在他的twitter上找到了一个PGP 0x4b74e38aedd31e2a
这个PGP在一个 PGP SERVER网站上有收录,是一段base64编码
http://pgp.mit.edu:11371/pks/lookup?op=get&search=0x9FBEBC5EA827D636使用一段python脚本解码一下
>>> file_object = open('c:\data.txt','r')
>>> text = file_object.read()
>>> file_object_out = open('c:\data2.txt','wb')
>>> text = base64.decodestring(text)
>>> file_object_out.write(text)
>>> file_object_out.close() 把输出的文件拿WinHex打开,发现FF D8 是JPGE的文件头,把这个东西截取出来,打开一看,我擦竟然是key
其实这题我觉得使用这个公钥解密一个他发布的私钥加密的文件更有意思
Kevin Chung( CSAW CTF Qualification Round 2013 )
这逼貌似是一个亚洲人,亚洲人何苦为难亚洲人,哎。。。
这种东西就是搜啊搜啊搜,搜到一个页面
https://hsf.isis.poly.edu/previous_winners/点开里面这逼名字的一个链接就是key了。。。。
historypeats( CSAW CTF Qualification Round 2013 )
这个比较简单,直接找到GitHub,发现他最近有一次更新
点开一看,就是key
Brandon Edwards( CSAW CTF Qualification Round 2013 )
这道题也在github里面,使劲找一找就能发现这个
Odin( CSAW CTF Qualification Round 2013 )
这个貌似是一个希腊神话的神明,叫奥丁什么的,不是一个人名,不知道怎样去人肉。
这个竟然要去IRC打命令,尼玛这我咋知道啊。先来观察聊天室有这样一个人snOwDIN
之后打whois snOwDIN会返回一大串
19:20 -!- snOwDIN [[email protected]]19:20 -!- ircname : linkedin:chinesespies 19:20 -!- channels : @#odin @#csaw19:20 -!- server : isis.poly.edu [ISIS IRC Server] 19:20 -!- : is using a Secure Connection 19:20 -!- idle : 0 days 0 hours 1 mins 18 secs [signon: Thu Sep 19 21:04:20 2013]19:20 -!- End of WHOIS这里线索指向
linkedin:chinesespies去这里找找··就可以得到key啦~
prosauce.org( CSAW CTF Qualification Round 2013 )
这题是一个网站,貌似东西还很多。
其实就是一顿猛找,找到这样一个页面
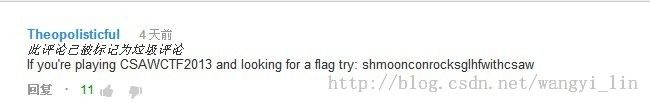
http://prosauce.org/projects/其中有一个链接指向一个视频,youtube上面的
http://www.youtube.com/all_comments?v=RCTRSK45bS4看下面的一条评论,就是key