攻防世界-Crypto萌新-sleeping-guard(base64解码+文件头异或)-csaw-ctf-2016-quals
打开网页一堆base64码,解码是乱码,也不能转成图片,去查了wp,好像题有问题,少给了一段代码,虽然给了我也做不出来
import base64
from twisted.internet import reactor, protocol
import os
PORT = 9013
import struct
def get_bytes_from_file(filename):
return open(filename, "rb").read()
KEY = "[CENSORED]"
def length_encryption_key():
return len(KEY)
def get_magic_png():
image = get_bytes_from_file("./sleeping.png")
encoded_string = base64.b64encode(image)
key_len = length_encryption_key()
print 'Sending magic....'
if key_len != 12:
return ''
return encoded_string
class MyServer(protocol.Protocol):
def connectionMade(self):
resp = get_magic_png()
self.transport.write(resp)
class MyServerFactory(protocol.Factory):
protocol = MyServer
factory = MyServerFactory()
reactor.listenTCP(PORT, factory)
reactor.run()涉及到了网络的部分,看不太懂,但是
if key_len != 12:
return ''
return encoded_string
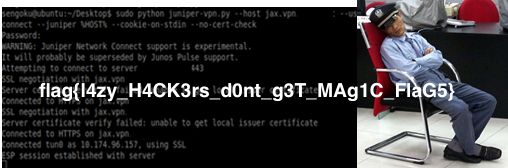
这个地方应该是用了一个长度为12的密文进行了加密(大佬的思路),但是是什么加密呢,大佬就是大佬,这都能想到,还能做出来,用的就是xor异或加密,我们把base64解码并保存为png文件:![]()
下面就用到异或了,把正常的png文件头的前16个(所有的png问件的都一样)和这个文件的文件进行异或:
header = [0x89,0x50,0x4E,0x47,0x0D,0x0A,0x1A,0x0A,0x00,0x00,0x00,0x0D,0x49,0x48,0x44,0x52]
f = open('sleeping.png', 'r') #我的电脑读文件时总要加上encoding='ISO-8859-1'
xor = ''
data = f.read()
i = 0
for char in data:
xor += chr(ord(char) ^ header[i % len(header)])
i += 1
print(xor[:20])结果是这样的:WoAh_A_Key!?WoAhÖð,根据前面的推测密钥长度是12位的话就是WoAh_A_Key!?,接下来用这个密钥对整个base64解码的文件进行异或:
#header = [0x89,0x50,0x4E,0x47,0x0D,0x0A,0x1A,0x0A,0x00,0x00,0x00,0x0D,0x49,0x48,0x44,0x52]
x = 'WoAh_A_Key!?'
f = open('sleeping.png', 'r')#加了encoding='ISO-8859-1',跑出来结果错误
f2 = open('sleep.png','w')
xor = ''
data = f.read()
i = 0
for char in data:
xor += chr(ord(char) ^ ord(x[i % len(x)]))
i += 1
f2.write(xor)open文件的时候都加上了encoding='ISO-8859-1',我的python3不加的话就会报错,但是跑出来的图片文件头不对,打不开,最后去掉编码encoding用Python2跑的也不行,然而,在linux上用python2跑就跑出来了: