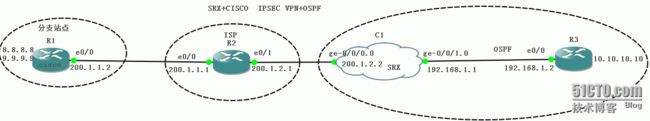
今天演示一下Juniper SRX防火墙与思科的路由器跑IPSEC ×××+OSPF
拓扑:
R1模拟的是cisco的设备,相当于分支站点,R2模拟的是运营商设备,C1是一朵云,与SRX桥接,那么就相当于防火墙(总部),R3模拟内部的路由器
8.8.8.8和9.9.9.9 两个网段用来模拟身后的用户,10.10.10.10用来模拟R3身后的用户
配置:
1.ISP
int e0/0
ip add 200.1.1.1 255.255.255.0
no sh
int e0/1
ip add 200.1.2.1 255.255.255.0
ISP配这点就行了,不需要其他的配置,×××的好处就是骗过ISP,所以在ISP不需要跑路由协议
2.R1
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key cisco address 200.1.2.2
!
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
!
crypto ipsec profile ipsecprof
set transform-set cisco
interface Loopback0
ip address 8.8.8.8 255.255.255.0
ip ospf 110 area 0
!
interface Loopback1
ip address 9.9.9.9 255.255.255.0
ip ospf 110 area 0
!
interface Tunnel0
ip address 172.16.1.1 255.255.255.0
ip ospf mtu-ignore
ip ospf 110 area 0
tunnel source 200.1.1.2
tunnel destination 200.1.2.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsecprof
!
interface Ethernet0/0
ip address 200.1.1.2 255.255.255.0
ip route 0.0.0.0 0.0.0.0 200.1.1.1
3.SRX
version 12.1X44.4;
system {
root-authentication {
encrypted-password "$1$91AvSN/4$ernVRIttwUahn.nTXm8Mp/"; ## SECRET-DATA
}
services {
ssh;
web-management {
http {
interface ge-0/0/0.0;
}
}
}
license {
autoupdate {
url https://ae1.juniper.net/junos/key_retrieval;
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 200.1.2.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.1.1/24;
}
}
}
st0 {
unit 0 {
family inet {
address 172.16.1.2/24;
}
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 200.1.2.1;
}
}
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/1.0;
interface st0.0;
}
}
}
security {
ike {
proposal L2L-P1-Proposal {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm md5;
encryption-algorithm 3des-cbc;
}
policy L2L-P1-Policy {
mode main;
proposals L2L-P1-Proposal;
pre-shared-key ascii-text "$9$7jVb2ji.5z6wY.5"; ## SECRET-DATA
}
gateway L2L-P1-Gateway {
ike-policy L2L-P1-Policy;
address 200.1.1.2;
external-interface ge-0/0/0.0;
}
}
ipsec {
proposal L2L-P2-Proposal {
protocol esp;
authentication-algorithm hmac-md5-96;
encryption-algorithm 3des-cbc;
}
policy L2L-P2-Policy {
proposals L2L-P2-Proposal;
}
*** Route-vs-SVTI {
bind-interface st0.0;
ike {
gateway L2L-P1-Gateway;
proxy-identity {
local 0.0.0.0/0;
remote 0.0.0.0/0;
service any;
}
ipsec-policy L2L-P2-Policy;
}
establish-tunnels immediately;
}
}
screen {
ids-option untrust-screen {
icmp {
ping-death;
}
ip {
source-route-option;
tear-drop;
}
tcp {
syn-flood {
alarm-threshold 1024;
attack-threshold 200;
source-threshold 1024;
destination-threshold 2048;
queue-size 2000; ## Warning: 'queue-size' is deprecated
timeout 20;
}
land;
}
}
}
policies {
from-zone trust to-zone SVTI {
policy permit-all {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone SVTI to-zone trust {
policy permit-all {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone untrust {
interfaces {
ge-0/0/0.0 {
host-inbound-traffic {
system-services {
ping;
ssh;
ike;
}
}
}
}
}
security-zone SVTI {
interfaces {
st0.0 {
host-inbound-traffic {
protocols {
ospf;
}
}
}
}
}
security-zone trust {
interfaces {
ge-0/0/1.0 {
host-inbound-traffic {
system-services {
ping;
}
protocols {
ospf;
}
}
}
}
}
}
}
[edit]
4.R3
int e0/0
ip add 192.168.1.2 255.255.255.0
ip os 110 ar 0
no shut
int l0
ip add 10.10.10.10 255.255.255.0
ip os 110 ar 0
测试:
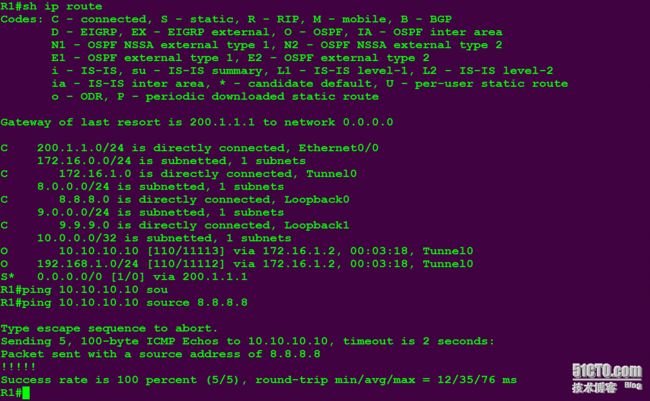
R1查看路由表并ping
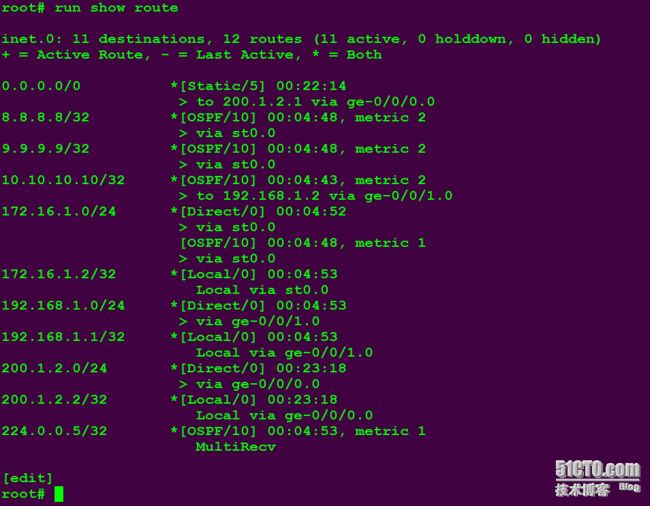
SRX查看路由表
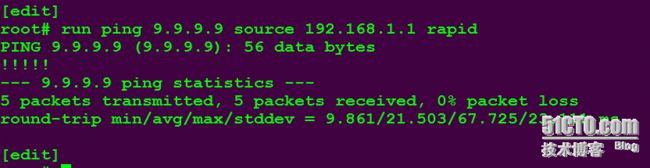
ping
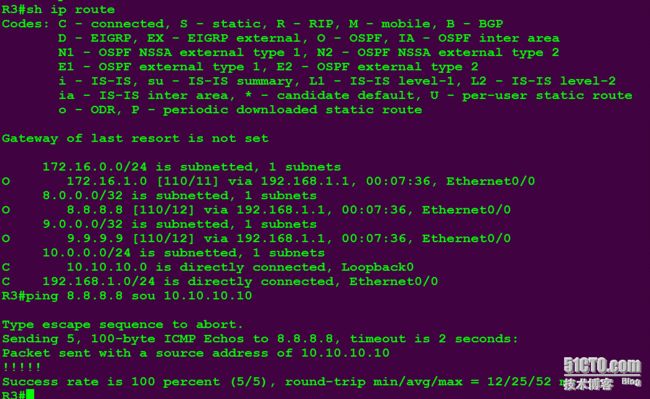
R3查看路由表并ping
SRX配置完一定要commit提交一下,不然配置不生效,还要接口一定放行IKE OSPF PING这些流量