OWASP 2017 年发布的 Top 10安全风险
原文链接:
https://sdtimes.com/app-development/owasp-releases-top-10-2017-security-risks/
今天在网上查查现在OWASP发布的最新的WEB应用安全风险都有哪些,看到了这篇文章,翻译后转载一下。
The Open Web Application Security Project (OWASP) officially released its Top 10 most critical web application security risks. This is the first time the organization has updated the Top 10 since 2013.
OWASP正式发布了其十大最关键的Web应用程序安全风险。这是该组织自2013年以来首次更新 Top 10的安全风险。
“Change has accelerated over the last four years, and the OWASP Top 10 needed to change. We’ve completely refactored the OWASP Top 10, revamped the methodology, utilized a new data call process, worked with the community, re-ordered our risks, rewritten each risk from the ground up, and added references to frameworks and languages that are now commonly used,” the OWASP wrote in the Top 10 2017.
“过去四年,变化加速,OWASP前10名需要改变。我们已经完全重构了OWASP Top 10,改进了方法,利用了新的数据调用过程,与社区合作,重新排序了我们的风险,从头开始重写每个风险,并添加了对现在普遍使用的框架和语言的引用,”OWASP在Top 10 2017中写道。
According to the OWASP, some significant changes over the past couple of years that resulted in an update to the Top 10 include microservices, single page apps, and the dominance of JavaScript as a primary language on the web.
根据OWASP,在过去几年中,一些重大的变化导致了对 Top 10安全风险排名的更新,包括微服务、单页应用程序以及JavaScript作为主要语言在网络上的统治地位。
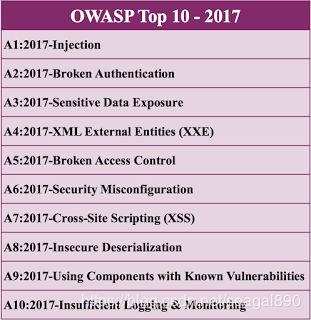
The Top 10 now consists of:
- Injection
- Broker Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Script (XSS)
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
XXE, insecure deserialization and insufficient logging and monitoring are new to the Top 10. Broken access control is a combination of 2013’s insecure direct object references and missing function level access control. In addition, the OWASP has removed unvalidated redirects and forwards, and cross-site request forgery from the Top 10.
XXE,不安全的反序列化(Insecure Deserialization)和日志记录和监视不足(Insufficient Logging and Monitoring)是前十名的新问题。中断访问控制(Broken Access Control)是2013年不安全的直接对象引用(Insecure Direct Object References)和缺失功能级访问控制(Insecure Direct Object References)的组合。此外,OWASP还从前10名中删除了未经验证的重定向和转发(Unvalidated Redirects and Forwards)以及跨站点请求伪造(XSS,Cross-Site Scripting)。
“Why have CSRF and unvalidated redirects and forwards been removed? It’s time to move on. The data for these is no longer strong enough to warrant inclusion, especially when we only have 8 data supported spots with our new methodology, and these two items didn’t rank in the community survey. This is actually a sign of success; the fact that CSRF is finally going away is a sign that the OWASP Top 10 has been successful at its mission,” the OWASP wrote in a blog post.
“为什么CSRF和未验证重定向和转发被删除?”该走了。这些数据不再足够强大,不能保证被纳入,尤其是当我们用新方法仅支持8个数据点的时候,而这两个项目在社区调查中没有排名。这实际上是成功的标志;CSRF最终离去的事实是OWASP Top 10在其使命中成功的标志,”OWASP在博客中写道。
The community survey, which received more than 500 responses, did agree on the inclusion insecure deserialization and insufficient logging and monitoring, according to the OWASP. “These two items were obviously top of mind for many this year considering the era of the mega breach is not slowing down,” the OWASP wrote.
根据OWASP,收到500多份回复的社区调查确实就包括不安全的反序列化(Insecure Deserialization)和日志记录和监视不足(Insufficient Logging and Monitoring)达成一致。OWASP写道:“考虑到大规模违约事件没有减缓的时代,这两项显然在今年对许多人来说都是头等大事。”
According to the OWASP, insecure deserialization leads to remote code execution, and insufficient logging and monitoring coupled with missing or weak integration results in hackers being able to attack systems and maintain persistence.
根据OWASP,不安全的反序列化(Insecure Deserialization)导致远程代码执行,并且不足的日志记录和监视(Insufficient Logging and Monitoring)加上缺少或弱的集成导致黑客能够攻击系统和维护持久性。
XXE is a new category supported by data. “Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks,” the OWASP wrote.
XXE是一个由数据支持的新类别。“许多较老的或配置不良的XML处理器评估XML文档中的外部实体引用。外部实体可以用来使用文件URI处理程序、内部文件共享、内部端口扫描、远程代码执行和拒绝服务攻击来公开内部文件,”OWASP写道。
To defend against the Top 10, the OWASP believes developers need to establish and use repeatable processes and security controls, security testers need to establish continuous application security testing, application managers need to take charge of the full application lifecycle from an IT perspective, and the organization as a whole needs to have an application security program in place.
为了防范Top的安全风险,OWASP认为开发人员需要建立和使用可重复的过程和安全控制,安全测试人员需要建立连续的应用程序安全测试,应用程序经理需要从IT角度负责整个应用程序生命周期,而整个组织需要具备应用安全的程序。
“A great deal of feedback was received during the creation of the OWASP Top 10 – 2017, more than for any other equivalent OWASP effort. This shows how much passion the community has for the OWASP Top 10, and thus how critical it is for OWASP to get the Top 10 right for the majority of use cases,” the OWASP wrote.
“在创建OWASP Top 10–2017期间,收到了大量的反馈,比任何其他等效的OWASP工作都要多。这显示了社区对OWASP前10名有多大的热情,因此对于OWASP来说,在大多数用例中正确地获得前10名是多么关键,”OWASP写道。
回顾:2013年 OWASP发布的TOP 10 安全漏洞
漏洞分类,参考OWASP Top Ten (2013)
- Injection
- Broken Authentication and Session Management
- Cross-Site Scripting (XSS)
- Insecure Direct Object References
- Security Misconfiguration
- Sensitive Data Exposure
- Missing Function Level Access Control
- Cross-Site Request Forgery (CSRF)
- Using Components with Known Vulnerabilities
- Unvalidated Redirects and Forwards
(完)