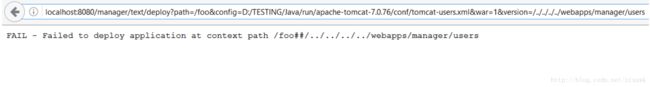
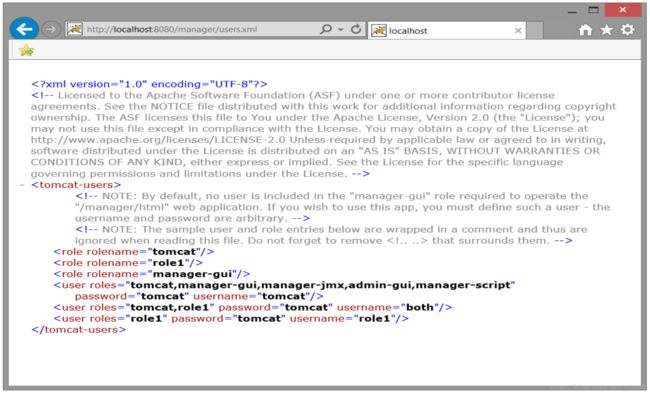
- 国内网站安全测试6大步骤
红酒味蛋糕_
网络安全
网站安全测试目标:1.发现网络系统中存在的安全隐患和可能被入侵者利用的安全漏洞2.与黑客区别:·渗透测试是经过授权的·可控制的、非破坏性的方法3.宏观上的分类:·黑盒测试不了解目标详细信息的情况,模拟黑客攻击.·白盒测试完全了解,代码审计.·灰盒测试了解一部分东西.4.思路和细节名词解释漏洞POC验证漏洞存在的代码片段exploit利用(渗透攻击)exp(利用一个漏洞完整的程序)提权权限提升获取当
- Exploiting server-side parameter pollution in a query string
Zkaisen
Burpsuitburpsuitweb安全
Target:loginastheadministratoranddeletecarlos.1、防止API漏洞在设计API时,确保在一开始就考虑到安全性要确保:保护API文档如果你的API文档不打算公开的话确保文档及时更新以便于合法的测试者能够充分进行API攻击面测试设置HTTP方法的允许列表验证每个请求或响应所期望的内容类型使用通用错误消息来避免泄露可能对攻击者有用的信息。对API的所有版本使用
- 网络安全:kali之MSF工具基本使用方法
诺卡先生
网络安全学习笔记网络安全linux安全服务器linux
1、进入MSF工具:nsfconsole2、查询漏洞利用工具:search漏洞编号3、打开工具:use工具id4、查看工具配置参数:showoptions5、查看工具的详细信息:info6、配置参数:set参数头目标主机set参数头目标端口(参数配置根据实际所缺参数为准)7、运行工具:run或者exploit@返回命令:back@新版kali已经自动配置Payload;不需要再次自己配置(当然也可
- 介绍5大黑客技术网站,一个就能让你成为黑客
编程瞬息全宇宙
安全web安全php网络数据库
5大优秀黑客必逛技术网站HackForums最理想的黑客技术学习技术根据地,也适用于开发人员游戏开发者,程序员,图形设计师以及网络营销人士HackThisSite提供合法而安全的网络安全资源,可以通过·各类挑战题目测试自己的黑客技能EnilZone一个专门面向黑科群体的论坛,其中也涉及科学,编程以及艺术等领域的内容Exploit-DB提供一整套庞大的归档体系,公开的攻击事件,漏洞报告,技术教程等资
- 托福写作的十三个万能理由
考培侠kpx
[if!supportLists]一.[endif]成就感(achievement)关键词句:asenseofachievementvirtuouscycle良性循环grandfeat/exploit辉煌的业绩attainmentofgoalselevateourself-esteembeconductivetoself-actualization有助于自我实现万能段落:Bydoing(somet
- tee漏洞学习-翻译-3:TrustZone exploit for MSM8974
goodcat666
tee安全teepwn
原文:http://bits-please.blogspot.com/2015/08/full-trustzone-exploit-for-msm8974.html在这篇博文中,我们将介绍利用上一篇文章中描述的TrustZone漏洞的完整过程。在开发此漏洞时,我只使用了我值得信赖的(个人)Nexus5设备。这意味着下面写入的所有内存地址和其他特定信息均取自该设备。如果有人想要重新创建下面描述的确切
- 恶意代码分析实战 第十一章 恶意代码的行为
doinb1517
本章主要熟悉恶意代码的行为。下载器和启动器常见的两种恶意代码是下载器和启动器。下载器从互联网上下载其他的恶意代码,然后在本地系统中运行。下载器通常会与漏洞利用(exploit)打包在一起。下载器常用WindowsAPI函数URLDownloadtoFileA和WinExec,来下载并运行新的恶意代码。启动器(也称为加载器)是一类可执行文件,用来安装立即运行或者将来秘密执行的恶意代码。启动器通常包含
- 白帽子学习——Metasploit渗透测试指南
yeapT
渗透测试安全服务器网络
根据pdf,总结自己认为比较重要的,欢迎大佬指错。1.Metasploit基础1.1专业术语1.1.1渗透攻击(Exploit)由攻击者或渗透测试者利用一个系统、应用或服务中心的安全漏洞进行的攻击行为。往往会造成开发者所没有预期到的一种特殊结果。1.1.2攻击载荷(Payload)目标系统在被渗透攻击之后去执行的代码,在Metasploit框架中可以自由地选择、传送和植入。1.1.3Shellco
- 新型Black Matter勒索病毒,勒索300万美金
Promise承诺
安全网络服务器
专注于全球恶意软件的分析与研究BlackMatter勒索病毒是一款基于RAAS模式的新型勒索病毒,该勒索病毒组织成立于2021年7月,该勒索病毒黑客组织对外宣称,已经整合了DarkSide、REvil和LockBit等勒索病毒的最佳功能特点。勒索病毒黑客组织曾表示不会对医疗保健、关键基础设施、石油和天然气、国防、非营利组织和政府进行攻击,该勒索病毒初期通过Exploit和XSS等黑客论坛进行宣传和
- 【深蓝学院】移动机器人运动规划--第3章 基于采样的路径规划--笔记
读书健身敲代码
motionplanning笔记Roboticsmotionplanning
0.Preliminaries做规划都是将WS转到Cspace下进行。找到可行解和最优解(这两个不同)通过增量或者批次地在C-space中采样来增量式地构建树或者图。不显式地构造如果把整个规划问题看成一个大的优化问题,那么大问题可以拆分成小问题进行求解。整个规划问题可以分为两个基本的tasks:Explotration和ExploitationExplotration目的是获取搜索空间中的拓扑信息
- 红队系列-网络安全知识锦囊
amingMM
网络安全-渗透测试web安全安全
网络安全免责声明法律科普学习资源网站靶场/CTF大佬博客笔记思维框图CTF/AWDAPT&&矩阵Web安全/渗透测试ToolsGolang工具FscanGolang工具ChYing信息收集注入攻击ToolsJNDIExploit反序列化ToolsYsoserial权限提升内网横向代理EWNPSproxychainsrakshasareGeorg权限ActiveDirectory域渗透CrackMa
- 揭秘家用路由器0day漏洞挖掘技术原始环境搭建
此人亦非
二进制漏洞路由器固件固件分析Ubuntu12
对于未知的复杂事物,应该先去跟谁它,观察它,然后挖掘其规律。《揭秘家用路由器0day漏洞挖掘技术》出版于2015年,使用的系统环境为ubuntu-12.04.4-desktop-i386(ubuntu1232bit桌面版)。里面涉及的dir-645,dir-815等的溢出漏洞,在exploit-db上的时间为2013年前段,距离当前(2019)已经6年多了。作者当初使用相关的软件和系统距今发生很多
- shellcode
Lyx-0607
笔记
生成shellcode在漏洞利用中,shellcode是不可或缺的部分,所以在网上有许多公开分享的shellcode,在不同平台上并不通用,需要选择适合的shellcode。这里推荐两个常见公开的安全平台:一个为公开的漏洞库exploit-db(见公众号链接10-1),一个为公开的Shell-strom库(见公众号链接10-2),如图10-1和图10-2所示。图10-1exploit-db公开漏洞
- 商务英语中,verbal 和 psychological是什么意思?
Lisa_Wang_China
WeexpectourBusinessAssociatestocreateandmaintainanenvironmentthattreatsallemployeeswithdignityandrespect,andwillnotuseanythreatsofviolence,sexualexploitationorabuse,verbalorpsychologicalharassmentorab
- 新型Black Matter勒索病毒,勒索300万美金
熊猫正正
勒索病毒专题报告勒索病毒系统安全安全威胁分析网络安全
前言BlackMatter勒索病毒是一款基于RAAS模式的新型勒索病毒,该勒索病毒组织成立于2021年7月,该勒索病毒黑客组织对外宣称,已经整合了DarkSide、REvil和LockBit等勒索病毒的最佳功能特点。勒索病毒黑客组织曾表示不会对医疗保健、关键基础设施、石油和天然气、国防、非营利组织和政府进行攻击,该勒索病毒初期通过Exploit和XSS等黑客论坛进行宣传和招募合作伙伴及会员,Bla
- web渗透入门
baidu_36461925
应用层安全sql注入xpath
目录工具...2攻击类型...2SQL注入...2Exploit网站及工具...3预防SQL注入...13攻击类型...15跨站点请求伪造...19缓存投毒...20代码注入...21注释注入...23Xpath注入...25XSS.27目录遍历...29爆路径...31跨用户攻击...32会话固定攻击...33PHP对象攻击...34HTTP请求走私...36HTTP响应拆分...38工具Met
- Log4j2漏洞(二)3种方式复现反弹shell
大象只为你
跟我学网安知识log4j漏洞复现网络安全命令执行
★★免责声明★★文章中涉及的程序(方法)可能带有攻击性,仅供安全研究与学习之用,读者将信息做其他用途,由Ta承担全部法律及连带责任,文章作者不承担任何法律及连带责任。1、前言明天就是除夕了,提前祝大家:新年新气象,龙年龖龖!也祝愿自己2024年一切顺利!本文主要是分享log4j2反弹shell的3种方式,第一种方式【JNDI-Injection-Exploit】对jdk版本要求比较高,因此我在靶场
- 渗透测试常用术语总结
沫风港
web安全安全
渗透测试常用术语总结题记人的一生会遇到两个人,一个惊艳了时光,一个温柔了岁月。——苏剧《经年》正文我是会把我遇到很晦涩或者难以理解的词语分享到这的。相信大家和我一样,搞不清这些专业名词的区别,所以我来整理一下。1.POC、EXP、Payload与ShellcodePOC:全称'ProofofConcept',中文'概念验证',常指一段漏洞证明的代码。EXP:全称'Exploit',中文'利用',指
- 小白的第二篇LeetCode(国际版)英文题解 - Problem. 49
春玩其华,秋得其实
Leetcode刷题leetcode算法python
Python||ExtremelySHORT(5lines!)&EASY||FullyexploitPythonGroupAnagrams-LeetCodeLevelupyourcodingskillsandquicklylandajob.Thisisthebestplacetoexpandyourknowledgeandgetpreparedforyournextinterview.https:
- 2023 年已知被利用最多的十大CWE漏洞排名
华为云PaaS服务小智
安全网络web安全
作者:Uncle_Tom原文链接:2023年已知被利用最多的十大CWE漏洞排名-云社区-华为云1.2023年已知被利用最多的十大CWE漏洞排名2023年12月14日,CWE的网站上公布了美国网络安全和基础设施安全局(Cybersecurity&InfrastructureSecurityAgency(CISA),简称CISA),管理的“已知被利用漏洞目录(KnownExploitedVulnera
- 二进制安全虚拟机Protostar靶场(8)heap3 Fastbins unlink exploit
Ba1_Ma0
pwn二进制安全笔记安全pwnctf堆二进制安全
前言这是一个系列文章,之前已经介绍过一些二进制安全的基础知识,这里就不过多重复提及,不熟悉的同学可以去看看我之前写的文章heap3程序静态分析https://exploit.education/protostar/heap-three/#include#include#include#include#includevoidwinner()#定义了一个名为winner的函数{printf("that
- 二进制安全虚拟机Protostar靶场(7)heap2 UAF(use-after-free)漏洞
Ba1_Ma0
二进制安全笔记pwn安全linuxctf二进制安全堆pwn
前言这是一个系列文章,之前已经介绍过一些二进制安全的基础知识,这里就不过多重复提及,不熟悉的同学可以去看看我之前写的文章heap2程序静态分析https://exploit.education/protostar/heap-two/#include#include#include#include#includestructauth{#定义了一个名为auth的结构体charname[32];#定义了
- 【Web】CVE-2021-22448 Log4j RCE漏洞学习
Z3r4y
javalog4jCVECVE-2021-22448RCE网络安全
目录复现流程漏洞原理复现流程启动HTTP->启动LDAP->执行Log4jvps起个http服务,放好Exploit.class这个恶意字节码LDAPRefServer作为恶意LDAP服务器importjava.net.InetAddress;importjava.net.MalformedURLException;importjava.net.URL;importjavax.net.Server
- Browser Fingerprinting: Unveiling the Unique Identifier of Web Browsers
进击切图仔
前端
Browserfingerprintingisatechnologyusedtoidentifyandlabelwebbrowsersbyexploitingtheuniquecharacteristicstheyexhibitwhenusersaccesswebsites.Itleveragesthedistinctfeaturesdisplayedbybrowsersduringuserint
- pwn学习笔记(1)
晓幂
学习笔记
pwn学习笔记(1)(1)pwn简介:以下来自于百度百科:”Pwn”是一个黑客语法的俚语词,是指攻破设备或者系统发音类似“砰”,对黑客而言,这就是成功实施黑客攻击的声音——砰的一声,被“黑”的电脑或手机就被你操纵了。(2)几个简单的名词:exploit:用于攻击的脚本与方案payload:攻击载荷,是对目标进程劫持控制流的数据shellcode:调用攻击目标的shell代码,常见的有bash和sh
- MSF手工导入模块小记
涛__涛
首先是msf模块所在的路径root@kali:~#cd/usr/share/metasploit-framework/modules/root@kali:/usr/share/metasploit-framework/modules#lsauxiliaryencodersevasionexploitsnopspayloadspost假如要导入exp模块root@kali:/usr/share/me
- kail使用msf工具利用永恒之蓝漏洞攻击win7
只喜欢打乒乓球
安全
实验环境靶机:win7IP:192.168.43.144攻击机:kaliip:192.168.43.150实验开始:第一步:打开msfconsole进入到工具里面搜索一下永恒之蓝漏洞searchms17_010这上面有三个可以利用的漏洞我们选择第一个useexploit/windows/smb/ms17_010_eternalblue接下来我们可以查看需要设置的IP地址和端口showoptions
- 适配器模式的三种实现
乔布
java适配器模式java开发语言
1.接口适配器模式,借助中间抽象类空实现目标接口所有方法,子类选择性重写,可以减少实现不必要方法先写一个接口,里面有三种方法publicinterfaceTeam{voidexploitation();//开发voidtest();//测试voidproducts();//产品}写一个实现类,实现这个接口publicclassAbstractAdapterimplementsTeam{@Overr
- 收集常用端口信息
QiWi
文件共享端口PortInfoExploit21/22/69Ftp/Tftp文件传输协议允许匿名的上传、下载、爆破和嗅探操作2049Nfs服务配置不当139Samba服务爆破、未授权访问、远程代码执行389Ldap目录访问协议注入、允许匿名访问、弱口令远程连接端口PortInfoExploit22SSH远程连接爆破、ssh隧道及内网代理转发、文件传输23Telnet远程连接爆破、弱口令、嗅探3389
- 红日靶场之sta&&ck远程桌面控制 个人学习)
曼达洛战士
学习
我们首先打开webshell工具然后切换到C盘的www的文件夹下面然后我们打开MSF工具进行监听模板msfconsole启动MSF工具然后是useexploit/multi/handler使用漏洞辅助模块setpayloadwindows/meterpreter/reverse_tcp这是利用漏洞tcp回弹模块setlhost192.168.52.129这是设置回弹的主机这里是我们的kali攻击机
- 插入表主键冲突做更新
a-john
有以下场景:
用户下了一个订单,订单内的内容较多,且来自多表,首次下单的时候,内容可能会不全(部分内容不是必须,出现有些表根本就没有没有该订单的值)。在以后更改订单时,有些内容会更改,有些内容会新增。
问题:
如果在sql语句中执行update操作,在没有数据的表中会出错。如果在逻辑代码中先做查询,查询结果有做更新,没有做插入,这样会将代码复杂化。
解决:
mysql中提供了一个sql语
- Android xml资源文件中@、@android:type、@*、?、@+含义和区别
Cb123456
@+@?@*
一.@代表引用资源
1.引用自定义资源。格式:@[package:]type/name
android:text="@string/hello"
2.引用系统资源。格式:@android:type/name
android:textColor="@android:color/opaque_red"
- 数据结构的基本介绍
天子之骄
数据结构散列表树、图线性结构价格标签
数据结构的基本介绍
数据结构就是数据的组织形式,用一种提前设计好的框架去存取数据,以便更方便,高效的对数据进行增删查改。正确选择合适的数据结构,对软件程序的高效执行的影响作用不亚于算法的设计。此外,在计算机系统中数据结构的作用也是非同小可。例如常常在编程语言中听到的栈,堆等,就是经典的数据结构。
经典的数据结构大致如下:
一:线性数据结构
(1):列表
a
- 通过二维码开放平台的API快速生成二维码
一炮送你回车库
api
现在很多网站都有通过扫二维码用手机连接的功能,联图网(http://www.liantu.com/pingtai/)的二维码开放平台开放了一个生成二维码图片的Api,挺方便使用的。闲着无聊,写了个前台快速生成二维码的方法。
html代码如下:(二维码将生成在这div下)
? 1
&nbs
- ImageIO读取一张图片改变大小
3213213333332132
javaIOimageBufferedImage
package com.demo;
import java.awt.image.BufferedImage;
import java.io.File;
import java.io.IOException;
import javax.imageio.ImageIO;
/**
* @Description 读取一张图片改变大小
* @author FuJianyon
- myeclipse集成svn(一针见血)
7454103
eclipseSVNMyEclipse
&n
- 装箱与拆箱----autoboxing和unboxing
darkranger
J2SE
4.2 自动装箱和拆箱
基本数据(Primitive)类型的自动装箱(autoboxing)、拆箱(unboxing)是自J2SE 5.0开始提供的功能。虽然为您打包基本数据类型提供了方便,但提供方便的同时表示隐藏了细节,建议在能够区分基本数据类型与对象的差别时再使用。
4.2.1 autoboxing和unboxing
在Java中,所有要处理的东西几乎都是对象(Object)
- ajax传统的方式制作ajax
aijuans
Ajax
//这是前台的代码
<%@ page language="java" import="java.util.*" pageEncoding="UTF-8"%> <% String path = request.getContextPath(); String basePath = request.getScheme()+
- 只用jre的eclipse是怎么编译java源文件的?
avords
javaeclipsejdktomcat
eclipse只需要jre就可以运行开发java程序了,也能自动 编译java源代码,但是jre不是java的运行环境么,难道jre中也带有编译工具? 还是eclipse自己实现的?谁能给解释一下呢问题补充:假设系统中没有安装jdk or jre,只在eclipse的目录中有一个jre,那么eclipse会采用该jre,问题是eclipse照样可以编译java源文件,为什么呢?
&nb
- 前端模块化
bee1314
模块化
背景: 前端JavaScript模块化,其实已经不是什么新鲜事了。但是很多的项目还没有真正的使用起来,还处于刀耕火种的野蛮生长阶段。 JavaScript一直缺乏有效的包管理机制,造成了大量的全局变量,大量的方法冲突。我们多么渴望有天能像Java(import),Python (import),Ruby(require)那样写代码。在没有包管理机制的年代,我们是怎么避免所
- 处理百万级以上的数据处理
bijian1013
oraclesql数据库大数据查询
一.处理百万级以上的数据提高查询速度的方法: 1.应尽量避免在 where 子句中使用!=或<>操作符,否则将引擎放弃使用索引而进行全表扫描。
2.对查询进行优化,应尽量避免全表扫描,首先应考虑在 where 及 o
- mac 卸载 java 1.7 或更高版本
征客丶
javaOS
卸载 java 1.7 或更高
sudo rm -rf /Library/Internet\ Plug-Ins/JavaAppletPlugin.plugin
成功执行此命令后,还可以执行 java 与 javac 命令
sudo rm -rf /Library/PreferencePanes/JavaControlPanel.prefPane
成功执行此命令后,还可以执行 java
- 【Spark六十一】Spark Streaming结合Flume、Kafka进行日志分析
bit1129
Stream
第一步,Flume和Kakfa对接,Flume抓取日志,写到Kafka中
第二部,Spark Streaming读取Kafka中的数据,进行实时分析
本文首先使用Kakfa自带的消息处理(脚本)来获取消息,走通Flume和Kafka的对接 1. Flume配置
1. 下载Flume和Kafka集成的插件,下载地址:https://github.com/beyondj2ee/f
- Erlang vs TNSDL
bookjovi
erlang
TNSDL是Nokia内部用于开发电信交换软件的私有语言,是在SDL语言的基础上加以修改而成,TNSDL需翻译成C语言得以编译执行,TNSDL语言中实现了异步并行的特点,当然要完整实现异步并行还需要运行时动态库的支持,异步并行类似于Erlang的process(轻量级进程),TNSDL中则称之为hand,Erlang是基于vm(beam)开发,
- 非常希望有一个预防疲劳的java软件, 预防过劳死和眼睛疲劳,大家一起努力搞一个
ljy325
企业应用
非常希望有一个预防疲劳的java软件,我看新闻和网站,国防科技大学的科学家累死了,太疲劳,老是加班,不休息,经常吃药,吃药根本就没用,根本原因是疲劳过度。我以前做java,那会公司垃圾,老想赶快学习到东西跳槽离开,搞得超负荷,不明理。深圳做软件开发经常累死人,总有不明理的人,有个软件提醒限制很好,可以挽救很多人的生命。
相关新闻:
(1)IT行业成五大疾病重灾区:过劳死平均37.9岁
- 读《研磨设计模式》-代码笔记-原型模式
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
/**
* Effective Java 建议使用copy constructor or copy factory来代替clone()方法:
* 1.public Product copy(Product p){}
* 2.publi
- 配置管理---svn工具之权限配置
chenyu19891124
SVN
今天花了大半天的功夫,终于弄懂svn权限配置。下面是今天收获的战绩。
安装完svn后就是在svn中建立版本库,比如我本地的是版本库路径是C:\Repositories\pepos。pepos是我的版本库。在pepos的目录结构
pepos
component
webapps
在conf里面的auth里赋予的权限配置为
[groups]
- 浅谈程序员的数学修养
comsci
设计模式编程算法面试招聘
浅谈程序员的数学修养
- 批量执行 bulk collect与forall用法
daizj
oraclesqlbulk collectforall
BULK COLLECT 子句会批量检索结果,即一次性将结果集绑定到一个集合变量中,并从SQL引擎发送到PL/SQL引擎。通常可以在SELECT INTO、
FETCH INTO以及RETURNING INTO子句中使用BULK COLLECT。本文将逐一描述BULK COLLECT在这几种情形下的用法。
有关FORALL语句的用法请参考:批量SQL之 F
- Linux下使用rsync最快速删除海量文件的方法
dongwei_6688
OS
1、先安装rsync:yum install rsync
2、建立一个空的文件夹:mkdir /tmp/test
3、用rsync删除目标目录:rsync --delete-before -a -H -v --progress --stats /tmp/test/ log/这样我们要删除的log目录就会被清空了,删除的速度会非常快。rsync实际上用的是替换原理,处理数十万个文件也是秒删。
- Yii CModel中rules验证规格
dcj3sjt126com
rulesyiivalidate
Yii cValidator主要用法分析:
yii验证rulesit 分类: Yii yii的rules验证 cValidator主要属性 attributes ,builtInValidators,enableClientValidation,message,on,safe,skipOnError
- 基于vagrant的redis主从实验
dcj3sjt126com
vagrant
平台: Mac
工具: Vagrant
系统: Centos6.5
实验目的: Redis主从
实现思路
制作一个基于sentos6.5, 已经安装好reids的box, 添加一个脚本配置从机, 然后作为后面主机从机的基础box
制作sentos6.5+redis的box
mkdir vagrant_redis
cd vagrant_
- Memcached(二)、Centos安装Memcached服务器
frank1234
centosmemcached
一、安装gcc
rpm和yum安装memcached服务器连接没有找到,所以我使用的是make的方式安装,由于make依赖于gcc,所以要先安装gcc
开始安装,命令如下,[color=red][b]顺序一定不能出错[/b][/color]:
建议可以先切换到root用户,不然可能会遇到权限问题:su root 输入密码......
rpm -ivh kernel-head
- Remove Duplicates from Sorted List
hcx2013
remove
Given a sorted linked list, delete all duplicates such that each element appear only once.
For example,Given 1->1->2, return 1->2.Given 1->1->2->3->3, return&
- Spring4新特性——JSR310日期时间API的支持
jinnianshilongnian
spring4
Spring4新特性——泛型限定式依赖注入
Spring4新特性——核心容器的其他改进
Spring4新特性——Web开发的增强
Spring4新特性——集成Bean Validation 1.1(JSR-349)到SpringMVC
Spring4新特性——Groovy Bean定义DSL
Spring4新特性——更好的Java泛型操作API
Spring4新
- 浅谈enum与单例设计模式
247687009
java单例
在JDK1.5之前的单例实现方式有两种(懒汉式和饿汉式并无设计上的区别故看做一种),两者同是私有构
造器,导出静态成员变量,以便调用者访问。
第一种
package singleton;
public class Singleton {
//导出全局成员
public final static Singleton INSTANCE = new S
- 使用switch条件语句需要注意的几点
openwrt
cbreakswitch
1. 当满足条件的case中没有break,程序将依次执行其后的每种条件(包括default)直到遇到break跳出
int main()
{
int n = 1;
switch(n) {
case 1:
printf("--1--\n");
default:
printf("defa
- 配置Spring Mybatis JUnit测试环境的应用上下文
schnell18
springmybatisJUnit
Spring-test模块中的应用上下文和web及spring boot的有很大差异。主要试下来差异有:
单元测试的app context不支持从外部properties文件注入属性
@Value注解不能解析带通配符的路径字符串
解决第一个问题可以配置一个PropertyPlaceholderConfigurer的bean。
第二个问题的具体实例是:
- Java 定时任务总结一
tuoni
javaspringtimerquartztimertask
Java定时任务总结 一.从技术上分类大概分为以下三种方式: 1.Java自带的java.util.Timer类,这个类允许你调度一个java.util.TimerTask任务; 说明: java.util.Timer定时器,实际上是个线程,定时执行TimerTask类 &
- 一种防止用户生成内容站点出现商业广告以及非法有害等垃圾信息的方法
yangshangchuan
rank相似度计算文本相似度词袋模型余弦相似度
本文描述了一种在ITEYE博客频道上面出现的新型的商业广告形式及其应对方法,对于其他的用户生成内容站点类型也具有同样的适用性。
最近在ITEYE博客频道上面出现了一种新型的商业广告形式,方法如下:
1、注册多个账号(一般10个以上)。
2、从多个账号中选择一个账号,发表1-2篇博文