- ROS常用命令
火山大兄
ROS机器人
一、ROS1、ROSShell命令roscd-移动到指定的ROS功能包目录rosls-显示ROS功能包的文件与目录rosed-编辑ROS功能包的文件roscp-复制ROS功能包的文件rospd-添加目录至ROS目录索引rosd-显示ROS目录索引中的目录具体使用(只介绍常见使用):roscd[功能包名称]。使用它,无需再使用cd一层层到查找,进入功能包里rosls[功能包名称]。等价与roscd+
- Action通信学习记录(一)
看不懂文献小天才
学习python笔记
1.action通信自定义action文件action、srv、msg文件内的可用数据类型一致,且三者实现流程类似:按照固定格式创建action文件;编辑配置文件;编译生成中间文件。1.定义action文件首先新建功能包,并导入依赖:roscpprospystd_msgsactionlibactionlib_msgs;然后功能包下新建action目录,新增Xxx.action(比如:AddInts
- 用C++编写一个简单的Publisher和Subscriber
网路元素
1.创建PublisherNoderoscdbeginner_tutorials创建src/talker.cpp文件,内容如下(可从https://raw.github.com/ros/ros_tutorials/kinetic-devel/roscpp_tutorials/talker/talker.cpp获取源码):#include"ros/ros.h"#include"std_msgs/St
- OSCP vulhub LORD OF THE ROOT: 1.0.1
GuiltyFet
OSCPlinux服务器ubuntu
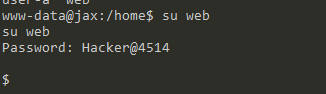
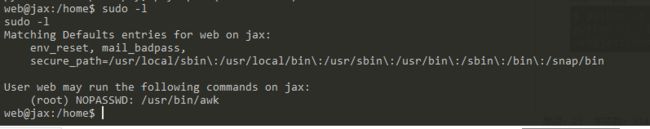
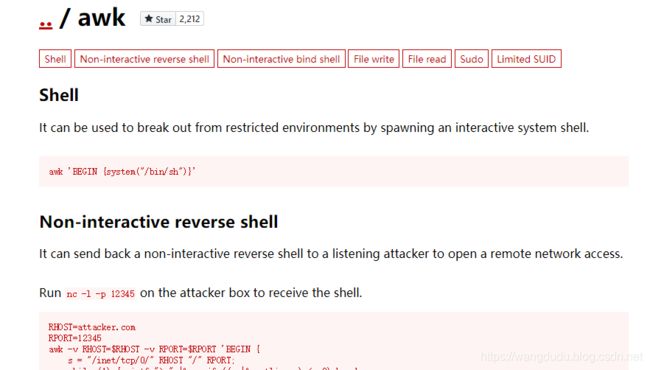
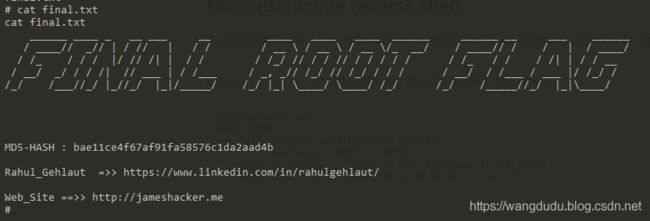
vulhubLORDOFTHEROOT:1.0.1靶场信息&安装Description一、信息收集第一种ssh爆破第二种猜二、漏洞探测三、漏洞利用四、提权第二种方法:udf提权第三种缓冲区溢出提权靶场信息&安装地址:https://www.vulnhub.com/entry/lord-of-the-root-101,129/发布日期:2015年9月23日目标:得到root权限Description
- VulnHub-Lord Of The Root_1.0.1-靶机渗透学习
嗯嗯呐
linuxmysql运维base64ubuntu
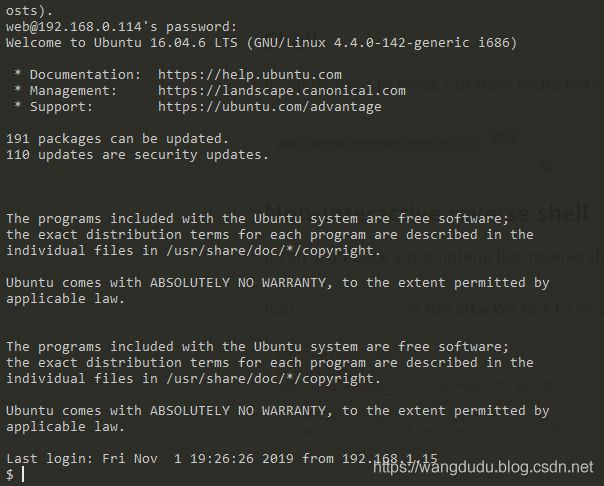
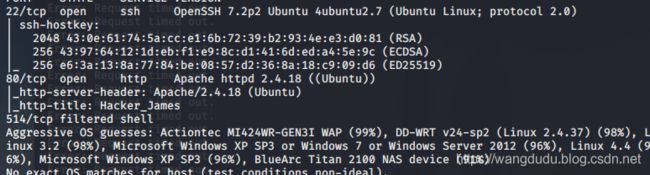
靶机地址:https://www.vulnhub.com/entry/lord-of-the-root-101,129/靶机难度:中等(CTF)靶机描述:这是KoocSec为黑客练习准备的另一个Boot2Root挑战。他通过OSCP考试的启发准备了这一过程。它基于伟大的小说改制电影《指环王》的概念。目标:得到root权限&找到flag.txt作者:嗯嗯呐一、信息采集nmap扫描确定靶机IP地址扫描
- No.6-VulnHub-Lord Of The Root: 1.0.1-Walkthrough渗透学习
大余xiyou
linuxpython数据库安全
**VulnHub-LordOfTheRoot:1.0.1-Walkthrough**靶机地址:https://www.vulnhub.com/entry/lord-of-the-root-101,129/靶机难度:中等(CTF)靶机发布日期:2015年9月23日靶机描述:这是KoocSec为黑客练习准备的另一个Boot2Root挑战。他通过OSCP考试的启发准备了这一过程。它基于伟大的小说改制电
- OSCP 靶场 - Vault
安鸾彭于晏
哈希算法算法
端口扫描nmapnmap-O192.168.162.172smb枚举smbmap(kali自带)//枚举GUEST用户可以使用的目录smbmap-uGUEST-H192.168.162.172NTLMrelay—smbrelay1.制作钓鱼文件使用https://github.com/xct/hashgrabpython3hashgrab.py192.168.45.212test2.上传钓鱼文件使
- LINUX上新建用户无法进入hbase进行操作 2020-08-26
1edee8a22fc9
1.在LINUX上新建用户coscp用户,coscp用户没有权限,进入hbase进行操作,调用脚本在hbase上新建表,会提示没有权限解决方法给用户授权:grant'coscp','RWXCA'2.使用coscp用户hbase进行操作的时候,会提示未认证“FATALipc.RpcClientImpl:SASLauthenticationfailed.Themostlikelycauseismiss
- 误操作卸载audit-libs 导致共享库 libaudit.so.1文件丢失
千里不留行_
linux服务器运维
问题:误操作卸载audit-libs导致共享库libaudit.so.1文件丢失,sudoscp等外部命令不能使用解决办法:想办法把包上传到linux中(这里我是放到/root/)重启服务器(1)按e进入单用户模式(2)linux16最后面加入init=/bin/bash(3)按ctrl+x(4)mount-oremount,rw/#重新挂载根目录赋予读写权限(5)vim/etc/selinux/
- oscp_靶场练习_Brainfuck
0rch1d
hackthebox渗透测试信息搜集网络安全
oscp_靶场练习_Brainfuck1.nmap扫描端口扫描:┌──(root㉿kali)-[~/Downloads]└─#nmap10.10.10.17-PnStartingNmap7.92(https://nmap.org)at2023-02-2106:19ESTNmapscanreportfor10.10.10.17Hostisup(0.23slatency).Notshown:995fi
- oscp_靶场练习_Lame
0rch1d
hackthebox渗透测试网络安全
oscp_靶场练习_Lame1.nmap扫描:└─#nmap10.10.10.3StartingNmap7.92(https://nmap.org)at2023-02-2023:21ESTNmapscanreportfor10.10.10.3Hostisup(0.22slatency).Notshown:996filteredtcpports(no-response)PORTSTATESERVIC
- Roscpp中构造函数与析构函数及在无人机串口通信应用
LENG_Lingliang
Linux/ROS/无人机无人机c++
1.概念辨析构造函数作用:初始化,在创建对象时会自动调用,有点像Python中的__init__方法特点:命名为class命名,在public中声明。析构函数作用:完成释放前的一些清理工作。特点:命名为~+class命名,在public中声明。调用顺序栈的顺序,先构造的后析构。2.编写示例ROScpp中在include文件夹下的.h头文件中声明class类别。以一个无人机串口通信代码为例:clas
- 靶场实战(11):OSCP备考之VulnHub Insanity 1
OneMoreThink
安全网络
靶场思路主机发现端口发现(服务、组件、版本)漏洞发现(获取权限)21端口/FTP服务组件漏洞口令漏洞22端口/SSH服务组件漏洞口令漏洞80端口/HTTP服务组件漏洞URL漏洞(目录、文件)提升权限elliot用户sudosuidcron内核提权信息收集一、主机发现本次靶场是Insanity:1[1],指定目标IP,不涉及主机发现过程。二、端口发现(服务、组件、版本)使用命令sudo-urootn
- 靶场实战(12):OSCP备考之VulnHub SEPPUKU
OneMoreThink
安全网络服务器web安全运维
打靶思路资产发现主机发现服务发现(端口、服务、组件、版本)漏洞发现(获取权限)21端口/FTP服务组件漏洞口令漏洞80端口/HTTP服务组件漏洞URL漏洞(目录、文件)7080端口/HTTPS服务组件漏洞URL漏洞(目录、文件)7601端口/HTTP服务组件漏洞URL漏洞(目录、文件)提升权限seppuku用户sudosuidcron内核提权信息收集samurai用户sudosuidcron内核提
- 靶机实战(5):OSCP备考之VulnHub SUNSET DECOY
OneMoreThink
网络安全服务器运维
靶机官网:SUNSET:DECOY[1]实战思路:主机发现端口发现(服务、组件、版本)1漏洞发现(获取权限)222端口/SSH服务2组件漏洞2口令漏洞280端口/HTTP服务2组件漏洞2URL漏洞(目录、文件)3越权提权601、sudo602、suid03、信息收集704、tty905、sudo906、suid07、信息收集1108、chkrootkit一、主机发现本次攻击指定IP,不涉及主机发现
- 靶场实战(7):OSCP备考之VulnHub Potato 1
OneMoreThink
安全web安全网络
靶机官网:Potato:1[1]实战思路:主机发现端口发现(服务、组件、版本)漏洞发现(获取权限)2112端口/FTP服务组件漏洞口令漏洞80端口/HTTP服务组件漏洞URL漏洞1(目录、文件)URL漏洞2(目录、文件)22端口/SSH服务组件漏洞口令漏洞提升权限01、suid02、cron03、sudo一、主机发现本次攻击指定IP,不涉及主机发现过程。二、端口发现(服务、组件、版本)使用命令su
- 靶场实战(13):OSCP备考之VulnHub GAARA
OneMoreThink
网络服务器安全tcp/ip运维
打靶思路资产发现主机发现服务发现漏洞发现(获取权限)80端口/HTTP服务组件漏洞URL漏洞22端口/SSH服务组件漏洞口令漏洞80端口/HTTP服务22端口/SSH服务提升权限gaara用户sudosuid1、资产发现1.1、主机发现本次靶机GAARA[1]指定攻击IP,不涉及主机发现过程。1.2、服务发现使用命令sudo-uroot172.16.33.69-n-Pn-p---reason-sV
- 靶机实战(9):OSCP备考之VulnHub BTRSys v2.1
OneMoreThink
安全网络
靶机官网:BTRSys:v2.1[1]实战思路:一、主机发现二、端口发现(服务、组件、版本)三、漏洞发现(获取权限)21端口/FTP服务组件漏洞口令漏洞22端口/SSH服务组件漏洞口令漏洞80端口/HTTP服务组件漏洞URL漏洞(目录、文件)四、提升权限www-data用户sudosuidcron内核提权信息收集btrisk用户sudo一、主机发现本次攻击指定IP,不涉及主机发现过程。二、端口发现
- OSCP 靶场 - Vault
安鸾彭于晏
web安全安全网络
端口扫描nmapnmap-O192.168.162.172smb枚举smbmap(kali自带)//枚举GUEST用户可以使用的目录smbmap-uGUEST-H192.168.162.172NTLMrelay—smbrelay1.制作钓鱼文件使用GitHub-xct/hashgrab:generatepayloadsthatforceauthenticationagainstanattacker
- 靶机实战(10):OSCP备考之VulnHub Tre 1
OneMoreThink
靶机官网:Tre:1[1]实战思路:一、主机发现二、端口发现(服务、组件、版本)三、漏洞发现(获取权限)8082端口/HTTP服务组件漏洞URL漏洞(目录、文件)80端口/HTTP服务组件漏洞URL漏洞(目录、文件)22端口/SSH服务组件漏洞口令漏洞80端口/HTTP服务URL漏洞(目录、文件)四、提升权限tre用户sudosuidcron后记一、主机发现本次攻击指定IP,不涉及主机发现过程。二
- GPM合并资料整理-GEM部分
酷爽
iOScocoamacosobjective-c
一、性能数据上报项1.CPU模块上报键值说明采集平台cpu当前进程cpu使用率平均值Android&iOStotcpu系统cpu总使用率平均值Android&iOScpu_temp_maxcpu最高温度Androidcpu_temp_avgcpu温度平均值Androidgpu_temp_avggpu温度平均值Androidgpu_temp_maxgpu最高温度Androidgpugpu使用率平均值
- vulnhub7
清风--
web安全安全
靶机地址:https://download.vulnhub.com/hackerkid/Hacker_Kid-v1.0.1.ova这次的靶机风格比较偏向OSCP风格,区别于传统的CTF类型的靶机,只需要提权到root即可,而且这次打靶确实触碰到很多知识盲区了提示:本地不需要任何暴力破解的地方,而且每个点都会有响应的提示信息收集老传统nmap信息收集了:扫描端口:┌──(kali㉿kali)-[~/
- ROS学习笔记(9)进一步深入了解ROS第三步
星影沉璧
ROS学习学习笔记
0.前提1.(C++)Whydidyouincludetheheaderfileofthemessagefileinsteadofthemessagefileitself?(为包含消息的头文件而不是消息本身?)回答:msg文件是描述ROS消息字段的文本文件,用于生成不同语言消息的源代码。按官方给的描述,我理解为在编译时要将文本文件转换成源代码,在将他包含进rospy或者roscpp,而直接包含消息
- 安装mac os 未能与服务器取得联系,Apple服务器问题导致应用程序安装与macOS更新失败等问题...
weixin_39640444
安装macos未能与服务器取得联系
在星期四的几个小时中,Apple证书检查功能出现问题,导致应用程序在启动时挂起,并且在macOSBigSur更新失败中占了很大一部分。开发商JeffJohnson表示,当尝试连接到Apple的在线证书状态协议网站(oscp.apple.com)时,具体地说,称为“受信任”的过程失败。大量报告表明应用程序性能不佳,其中一些人认为升级到macOSBigSur的用户迷是罪魁祸首。Johnson体验了ma
- rosrun/ros2 run命令
geniusNMRobot
ros2ros
rosrunrosrunallowsyoutorunanexecutableinanarbitrarypackagewithouthavingtocd(orroscd)therefirst.这个命令最开始的用途是:不用输入包的地址就可以启动那个包内的可执行文件。比较记忆地址还是要Usage:rosrunpackageexecutableExample:rosrunroscpp_tutorialst
- 2018 ACM-ICPC Syrian Collegiate Programming Contest(部分题解,待补)
Mitsuha_
思维计算几何状压DPACM-ICPC
传送门2018ACM-ICPC叙利亚大学生程序设计竞赛ProblemA:HelloSCPC2018!签到题ProblemB:BinaryHamming简单题#includeusingnamespacestd;constintMAX=1e6+10;constintINF=1e9+7;typedeflonglongll;chara[200],b[200];intmain(){freopen("hamm
- 如何将一个cpp文件放入到已有ROS工作空间中编译通过以及如何调用第三方库
lanhuazhiyue
vscode
如何将一个cpp文件放入到已有ROS工作空间中编译通过以及如何调用第三方库1.创建一个新的功能包catkin_create_pkg自定义ROS包名roscpprospystd_msgs2.helloworld在src中添加你的cpp文件,并放开cmakelist.txt里关于add_executable()和target_link_libraries()的注释,修改名字为你的cpp文件名(add_
- 机械臂仿真程序记录贴(2)
drivenzyw
ubuntu
一、新建功能包catkin_create_pkgmotion_planningrospyroscppstd_msgs二、vscode打开code./三、新建cpp文件来规划路径(看官方文档吧)MoveGroupC++Interface—moveit_tutorialsMelodicdocumentation这个是c++版本的↑,主要看他给你推的那个参考包里面有不同的demo,仿照它写就好
- iOS将framework转为xcframework
培根芝士
iOSios
拆分framework先把framework拷贝到两个文件夹下边,这里只需要armv7、arm64、x86_64。mkdiriphoneosiphonesimulatorcp-Rmysdk.frameworkiphoneoscp-Rmysdk.frameworkiphonesimulator把iphoneos中的模拟器指令集删除lipo-removei386-removex86_64iphoneo
- 注册中心
go_2021
百发失一,不足谓善射;千里蹞步不至,不足谓善御;伦类不通,仁义不一,不足谓善学。学也者,固学一之也。一出焉,一入焉,涂巷之人也;其善者少,不善者多,桀纣盗跖也;全之尽之,然后学者也。常用的注册中心对比name协议语言zkcp(zab)eurekaapjavanacoscp&&apjavaetcdcp(raft)goconsulcp(raft)gohttps://mp.weixin.qq.com/s
- 对股票分析时要注意哪些主要因素?
会飞的奇葩猪
股票 分析 云掌股吧
众所周知,对散户投资者来说,股票技术分析是应战股市的核心武器,想学好股票的技术分析一定要知道哪些是重点学习的,其实非常简单,我们只要记住三个要素:成交量、价格趋势、振荡指标。
一、成交量
大盘的成交量状态。成交量大说明市场的获利机会较多,成交量小说明市场的获利机会较少。当沪市的成交量超过150亿时是强市市场状态,运用技术找综合买点较准;
- 【Scala十八】视图界定与上下文界定
bit1129
scala
Context Bound,上下文界定,是Scala为隐式参数引入的一种语法糖,使得隐式转换的编码更加简洁。
隐式参数
首先引入一个泛型函数max,用于取a和b的最大值
def max[T](a: T, b: T) = {
if (a > b) a else b
}
因为T是未知类型,只有运行时才会代入真正的类型,因此调用a >
- C语言的分支——Object-C程序设计阅读有感
darkblue086
applec框架cocoa
自从1972年贝尔实验室Dennis Ritchie开发了C语言,C语言已经有了很多版本和实现,从Borland到microsoft还是GNU、Apple都提供了不同时代的多种选择,我们知道C语言是基于Thompson开发的B语言的,Object-C是以SmallTalk-80为基础的。和C++不同的是,Object C并不是C的超集,因为有很多特性与C是不同的。
Object-C程序设计这本书
- 去除浏览器对表单值的记忆
周凡杨
html记忆autocompleteform浏览
&n
- java的树形通讯录
g21121
java
最近用到企业通讯录,虽然以前也开发过,但是用的是jsf,拼成的树形,及其笨重和难维护。后来就想到直接生成json格式字符串,页面上也好展现。
// 首先取出每个部门的联系人
for (int i = 0; i < depList.size(); i++) {
List<Contacts> list = getContactList(depList.get(i
- Nginx安装部署
510888780
nginxlinux
Nginx ("engine x") 是一个高性能的 HTTP 和 反向代理 服务器,也是一个 IMAP/POP3/SMTP 代理服务器。 Nginx 是由 Igor Sysoev 为俄罗斯访问量第二的 Rambler.ru 站点开发的,第一个公开版本0.1.0发布于2004年10月4日。其将源代码以类BSD许可证的形式发布,因它的稳定性、丰富的功能集、示例配置文件和低系统资源
- java servelet异步处理请求
墙头上一根草
java异步返回servlet
servlet3.0以后支持异步处理请求,具体是使用AsyncContext ,包装httpservletRequest以及httpservletResponse具有异步的功能,
final AsyncContext ac = request.startAsync(request, response);
ac.s
- 我的spring学习笔记8-Spring中Bean的实例化
aijuans
Spring 3
在Spring中要实例化一个Bean有几种方法:
1、最常用的(普通方法)
<bean id="myBean" class="www.6e6.org.MyBean" />
使用这样方法,按Spring就会使用Bean的默认构造方法,也就是把没有参数的构造方法来建立Bean实例。
(有构造方法的下个文细说)
2、还
- 为Mysql创建最优的索引
annan211
mysql索引
索引对于良好的性能非常关键,尤其是当数据规模越来越大的时候,索引的对性能的影响越发重要。
索引经常会被误解甚至忽略,而且经常被糟糕的设计。
索引优化应该是对查询性能优化最有效的手段了,索引能够轻易将查询性能提高几个数量级,最优的索引会比
较好的索引性能要好2个数量级。
1 索引的类型
(1) B-Tree
不出意外,这里提到的索引都是指 B-
- 日期函数
百合不是茶
oraclesql日期函数查询
ORACLE日期时间函数大全
TO_DATE格式(以时间:2007-11-02 13:45:25为例)
Year:
yy two digits 两位年 显示值:07
yyy three digits 三位年 显示值:007
- 线程优先级
bijian1013
javathread多线程java多线程
多线程运行时需要定义线程运行的先后顺序。
线程优先级是用数字表示,数字越大线程优先级越高,取值在1到10,默认优先级为5。
实例:
package com.bijian.study;
/**
* 因为在代码段当中把线程B的优先级设置高于线程A,所以运行结果先执行线程B的run()方法后再执行线程A的run()方法
* 但在实际中,JAVA的优先级不准,强烈不建议用此方法来控制执
- 适配器模式和代理模式的区别
bijian1013
java设计模式
一.简介 适配器模式:适配器模式(英语:adapter pattern)有时候也称包装样式或者包装。将一个类的接口转接成用户所期待的。一个适配使得因接口不兼容而不能在一起工作的类工作在一起,做法是将类别自己的接口包裹在一个已存在的类中。 &nbs
- 【持久化框架MyBatis3三】MyBatis3 SQL映射配置文件
bit1129
Mybatis3
SQL映射配置文件一方面类似于Hibernate的映射配置文件,通过定义实体与关系表的列之间的对应关系。另一方面使用<select>,<insert>,<delete>,<update>元素定义增删改查的SQL语句,
这些元素包含三方面内容
1. 要执行的SQL语句
2. SQL语句的入参,比如查询条件
3. SQL语句的返回结果
- oracle大数据表复制备份个人经验
bitcarter
oracle大表备份大表数据复制
前提:
数据库仓库A(就拿oracle11g为例)中有两个用户user1和user2,现在有user1中有表ldm_table1,且表ldm_table1有数据5千万以上,ldm_table1中的数据是从其他库B(数据源)中抽取过来的,前期业务理解不够或者需求有变,数据有变动需要重新从B中抽取数据到A库表ldm_table1中。
- HTTP加速器varnish安装小记
ronin47
http varnish 加速
上午共享的那个varnish安装手册,个人看了下,有点不知所云,好吧~看来还是先安装玩玩!
苦逼公司服务器没法连外网,不能用什么wget或yum命令直接下载安装,每每看到别人博客贴出的在线安装代码时,总有一股羡慕嫉妒“恨”冒了出来。。。好吧,既然没法上外网,那只能麻烦点通过下载源码来编译安装了!
Varnish 3.0.4下载地址: http://repo.varnish-cache.org/
- java-73-输入一个字符串,输出该字符串中对称的子字符串的最大长度
bylijinnan
java
public class LongestSymmtricalLength {
/*
* Q75题目:输入一个字符串,输出该字符串中对称的子字符串的最大长度。
* 比如输入字符串“google”,由于该字符串里最长的对称子字符串是“goog”,因此输出4。
*/
public static void main(String[] args) {
Str
- 学习编程的一点感想
Cb123456
编程感想Gis
写点感想,总结一些,也顺便激励一些自己.现在就是复习阶段,也做做项目.
本专业是GIS专业,当初觉得本专业太水,靠这个会活不下去的,所以就报了培训班。学习的时候,进入状态很慢,而且当初进去的时候,已经上到Java高级阶段了,所以.....,呵呵,之后有点感觉了,不过,还是不好好写代码,还眼高手低的,有
- [能源与安全]美国与中国
comsci
能源
现在有一个局面:地球上的石油只剩下N桶,这些油只够让中国和美国这两个国家中的一个顺利过渡到宇宙时代,但是如果这两个国家为争夺这些石油而发生战争,其结果是两个国家都无法平稳过渡到宇宙时代。。。。而且在战争中,剩下的石油也会被快速消耗在战争中,结果是两败俱伤。。。
在这个大
- SEMI-JOIN执行计划突然变成HASH JOIN了 的原因分析
cwqcwqmax9
oracle
甲说:
A B两个表总数据量都很大,在百万以上。
idx1 idx2字段表示是索引字段
A B 两表上都有
col1字段表示普通字段
select xxx from A
where A.idx1 between mmm and nnn
and exists (select 1 from B where B.idx2 =
- SpringMVC-ajax返回值乱码解决方案
dashuaifu
AjaxspringMVCresponse中文乱码
SpringMVC-ajax返回值乱码解决方案
一:(自己总结,测试过可行)
ajax返回如果含有中文汉字,则使用:(如下例:)
@RequestMapping(value="/xxx.do") public @ResponseBody void getPunishReasonB
- Linux系统中查看日志的常用命令
dcj3sjt126com
OS
因为在日常的工作中,出问题的时候查看日志是每个管理员的习惯,作为初学者,为了以后的需要,我今天将下面这些查看命令共享给各位
cat
tail -f
日 志 文 件 说 明
/var/log/message 系统启动后的信息和错误日志,是Red Hat Linux中最常用的日志之一
/var/log/secure 与安全相关的日志信息
/var/log/maillog 与邮件相关的日志信
- [应用结构]应用
dcj3sjt126com
PHPyii2
应用主体
应用主体是管理 Yii 应用系统整体结构和生命周期的对象。 每个Yii应用系统只能包含一个应用主体,应用主体在 入口脚本中创建并能通过表达式 \Yii::$app 全局范围内访问。
补充: 当我们说"一个应用",它可能是一个应用主体对象,也可能是一个应用系统,是根据上下文来决定[译:中文为避免歧义,Application翻译为应
- assertThat用法
eksliang
JUnitassertThat
junit4.0 assertThat用法
一般匹配符1、assertThat( testedNumber, allOf( greaterThan(8), lessThan(16) ) );
注释: allOf匹配符表明如果接下来的所有条件必须都成立测试才通过,相当于“与”(&&)
2、assertThat( testedNumber, anyOf( g
- android点滴2
gundumw100
应用服务器android网络应用OSHTC
如何让Drawable绕着中心旋转?
Animation a = new RotateAnimation(0.0f, 360.0f,
Animation.RELATIVE_TO_SELF, 0.5f, Animation.RELATIVE_TO_SELF,0.5f);
a.setRepeatCount(-1);
a.setDuration(1000);
如何控制Andro
- 超简洁的CSS下拉菜单
ini
htmlWeb工作html5css
效果体验:http://hovertree.com/texiao/css/3.htmHTML文件:
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>简洁的HTML+CSS下拉菜单-HoverTree</title>
- kafka consumer防止数据丢失
kane_xie
kafkaoffset commit
kafka最初是被LinkedIn设计用来处理log的分布式消息系统,因此它的着眼点不在数据的安全性(log偶尔丢几条无所谓),换句话说kafka并不能完全保证数据不丢失。
尽管kafka官网声称能够保证at-least-once,但如果consumer进程数小于partition_num,这个结论不一定成立。
考虑这样一个case,partiton_num=2
- @Repository、@Service、@Controller 和 @Component
mhtbbx
DAOspringbeanprototype
@Repository、@Service、@Controller 和 @Component 将类标识为Bean
Spring 自 2.0 版本开始,陆续引入了一些注解用于简化 Spring 的开发。@Repository注解便属于最先引入的一批,它用于将数据访问层 (DAO 层 ) 的类标识为 Spring Bean。具体只需将该注解标注在 DAO类上即可。同时,为了让 Spring 能够扫描类
- java 多线程高并发读写控制 误区
qifeifei
java thread
先看一下下面的错误代码,对写加了synchronized控制,保证了写的安全,但是问题在哪里呢?
public class testTh7 {
private String data;
public String read(){
System.out.println(Thread.currentThread().getName() + "read data "
- mongodb replica set(副本集)设置步骤
tcrct
javamongodb
网上已经有一大堆的设置步骤的了,根据我遇到的问题,整理一下,如下:
首先先去下载一个mongodb最新版,目前最新版应该是2.6
cd /usr/local/bin
wget http://fastdl.mongodb.org/linux/mongodb-linux-x86_64-2.6.0.tgz
tar -zxvf mongodb-linux-x86_64-2.6.0.t
- rust学习笔记
wudixiaotie
学习笔记
1.rust里绑定变量是let,默认绑定了的变量是不可更改的,所以如果想让变量可变就要加上mut。
let x = 1; let mut y = 2;
2.match 相当于erlang中的case,但是case的每一项后都是分号,但是rust的match却是逗号。
3.match 的每一项最后都要加逗号,但是最后一项不加也不会报错,所有结尾加逗号的用法都是类似。
4.每个语句结尾都要加分