网刃杯复现misc+流量包
签到
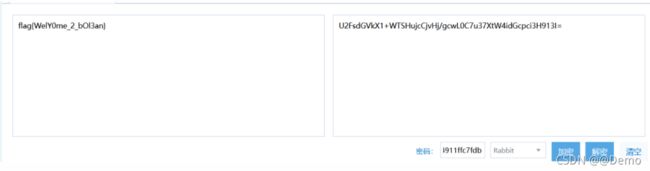
cipher.txt
U2FsdGVkX1+WTSHujcCjvHj/gcwL0C7u37XtW4idGcpci3H913I=
U2F那些,考虑为aes,des啥的
f71b6b842d2f0760c3ef74911ffc7fdb
mspaint
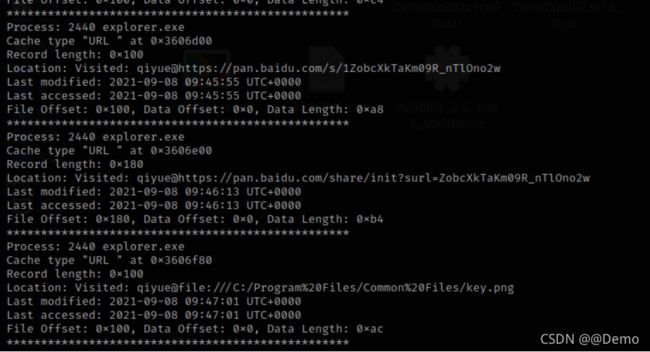
volatility -f mspaint.raw --profile=Win7SP1x64 filescan | grep key.png
![]()
volatility -f mspaint.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003e96e7d0 -D ./
得到百度网盘的密码
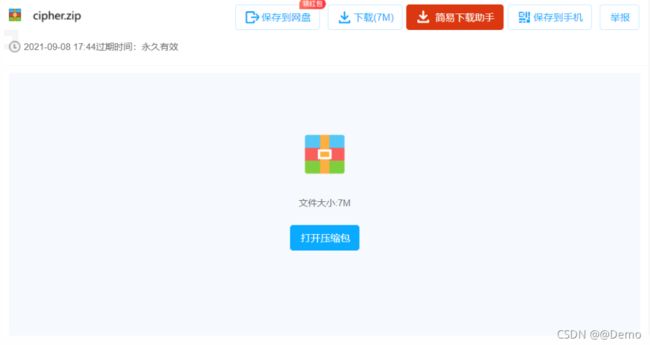
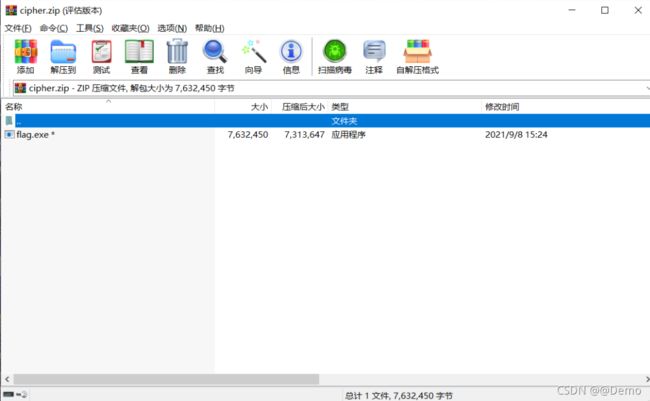
发现加密的压缩包,还需要key
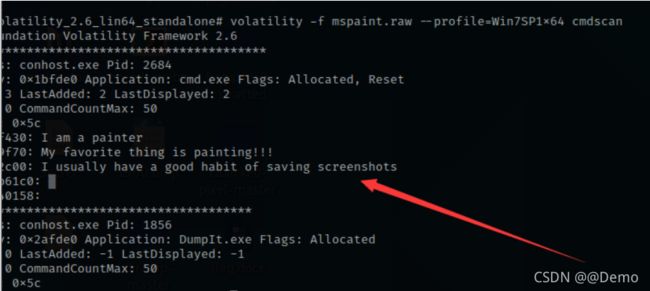
想到截屏
volatility -f mspaint.raw --profile=Win7SP1x64 screenshot -D ./
th1s_1s_th3_k3y
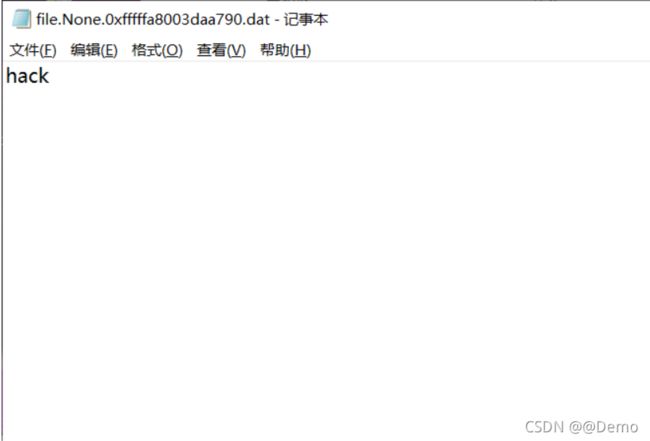
在看进程的时候有一个dumpit.exe,dump一下这个进程
volatility -f mspaint.raw --profile=Win7SP1x64 memdump -p 1064 -D ./
q2A!~R%8
后面是队里的re手个人秀
把flag.exe转成flag.pyc

文件夹里出现
修改文件头为pyc
key = 'xxxxxxxxxxxxxxx'
flag = 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx'
data = ''
for i in range(0, len(flag)):
data += hex(ord(flag[i]) ^ ord(key[(i % 15)]))[2:].zfill(2)
else:
print(data.upper())
data = '12045014240343684450506E5E1E1C165D045E6B52113C5951006F091E4F4C0C54426A52466A165B0122'
这里的key15位 就是那张图片里的th1s_1s_th3_k3y
写出解密脚本
key = 'th1s_1s_th3_k3y'
flag = ''
data = '12045014240343684450506E5E1E1C165D045E6B52113C5951006F091E4F4C0C54426A52466A165B0122'
data_list = []
for i in range(0,len(data),2):
data_list.append('0x' + data[i:i+2])
print(data_list)
for i in range(0,len(data_list)):
flag += chr(int(data_list[i],16)^ord(key[(i % 15)]))
print(flag)
flag{20708c15-eb55-4cbc-930b-68de15c55b32}
藏在s7里的秘密
题目描述:某工厂的安全设备捕获了攻击者向PLC中写入恶意数据的数据包,你能分析出并找到其中隐藏的数据吗?
附件打开发现流量包损坏打不开,010打开发现文件头被修改了,直接pcapfix修复下就好。
打开后,追踪tcp流发现png图片
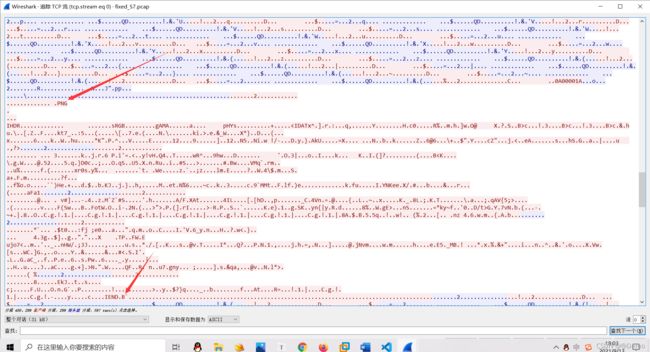
保存后发现只能看清楚一半的图

显然十六进制数据是不完整的,然后因为没咋做过流量包,到这思路也就停滞了。赛后看师傅的wp发现要看,这个流量包中出现最多的流s7comm,
先使用上面的过滤框,单独过滤这个协议
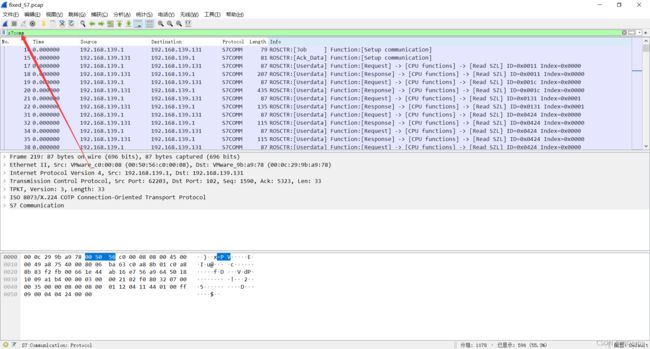
在查看这个流的时候发现长度有不一样的地方,看第一个长度541的包,发现存在png的文件头,最后一个长度329的包存在png的文件尾

拿导出第一部分举例
选中data->显示分组字节
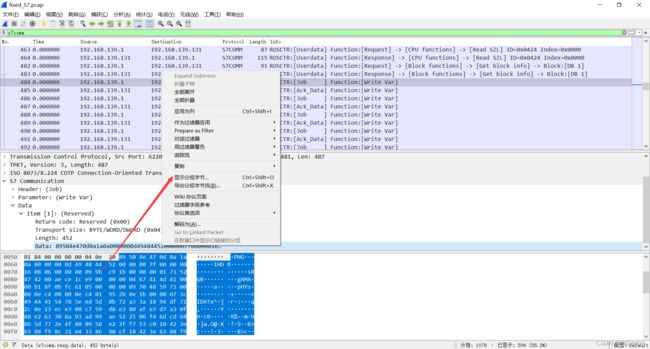
单击左下角改为原始数据

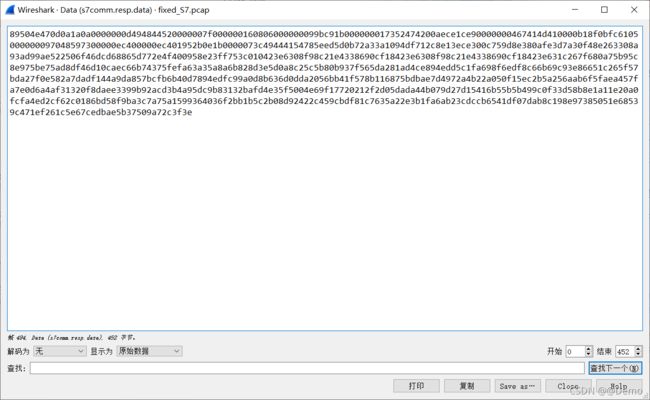
选中010,ctrl+shift+v保存即可。按照顺序依次把数据加进去即可。
保存后发现crc的值报错,说明宽高被修改了,修改高度获得flag

flag{FSfeQefjg}
老练的黑客
题目描述:一黑客成功入侵某核电站且获得了操作员站控制权,该操作员站可控制离心机的转速,当离心机的转速持续高于5000时将导致设备损坏,为了保护设备,操作员站检测到转速超过5000时会自动限制转速。但该黑客非常老练,他在修改了转速后,还欺骗了操作员站,使得操作员站读取到错误的转速数据。你能找到黑客修改后的转速值和操作员站读取到的错误转速值吗?(flag格式:flag{修改后转速的+读取的错误转速} 值用16进制表示
通过查看发现转速的数据位于data
5000的十六进制为1388,所以只要找到data大于1388的包查看数据即可
使用过滤器
modbus.data>1338

所以第一部分的flag为22b8。
又说转速被修改了,往下翻倒数read的几个包,找到一个4500对应十六进制为1194,肯定是被修改的转速。

flag{22b81194}
baby-usb
usb流量找到有数据的包,发现是八字节的,可能是键盘流量。
那就找键盘流量的脚本梭一下。
用脚本直接跑没啥输出,所以先用tshark提取了一下
tshark -r key.pcapng -T fields -e usb.capdata | sed '/^\s*$/d' > fileaaa.txt
然后修改了下脚本有输出了
import os,sys
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"" ,"29":"" ,"2a":"", "2b":"\t",
"2c":"" ,"2d":"-","2e":"=","2f":"[","30":"]","31":"\\",
"32":"" ,"33":";","34":"'","35":"" ,"36":",","37":".",
"38":"/","39":"" ,"3a":"" ,"3b":"" , "3c":"" ,"3d":"" ,
"3e":"" ,"3f":"" ,"40":"" ,"41":"" ,"42":"" ,"43":"" ,
"44":"" ,"45":"" }
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"" ,"29":"" ,"2a":"", "2b":"\t","2c":"" ,
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"" ,"33":"\"",
"34":":","35":"" ,"36":"<","37":">","38":"?","39":"" ,"3a":"" ,
"3b":"" , "3c":"" ,"3d":"" ,"3e":"" ,"3f":"" ,"40":"" ,
"41":"" ,"42":"" ,"43":"" ,"44":"" ,"45":"" }
#pcapFilePath = sys.argv[1]
#os.system("tshark -r "+pcapFilePath+" -T fields -e usb.capdata | sed '/^\s*$/d' > out.txt")
output = []
keys = open('out.txt')
for line in keys:
line = ''.join(line[i:i+2]+':' for i in range(0,len(line)-1,2)).strip(':')
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
#print("".join(output))
for i in range(len(output)):
try:
a=output.index('')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="" :
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))
os.system("rm -rf out.txt"
output :congratulationsonfindingmebutiwillnottellyouwherethepasswordofworddocumentisgoandfinditagain
到这其实就没什么思路了,尝试了各种东西,赛后看发现方向错了。
借用盖乐希师傅的脚本
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"" ,"29":"" ,"2a":"", "2b":"\t",
"2c":"" ,"2d":"-","2e":"=","2f":"[","30":"]","31":"\\",
"32":"" ,"33":";","34":"'","35":"" ,"36":",","37":".",
"38":"/","39":"" ,"3a":"" ,"3b":"" , "3c":"" ,"3d":"" ,
"3e":"" ,"3f":"" ,"40":"" ,"41":"" ,"42":"" ,"43":"" ,
"44":"" ,"45":"" }
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"" ,"29":"" ,"2a":"", "2b":"\t","2c":"" ,
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"" ,"33":"\"",
"34":":","35":"" ,"36":"<","37":">","38":"?","39":"" ,"3a":"" ,
"3b":"" , "3c":"" ,"3d":"" ,"3e":"" ,"3f":"" ,"40":"" ,
"41":"" ,"42":"" ,"43":"" ,"44":"" ,"45":"" }
output = []
keys = open('filebbb.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="" :
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))
ctonhgratuelatiokensonfinydingmebutiwiillnsottellyouwheretqahepzasswordwsoxfweodrddoccumentisgoarfvndfinditagain
output :congratulationsonfindingmebutiwillnottellyouwherethepasswordofworddocumentisgoandfinditagain
每个前面的字符就是key qazwsxedcrfv
flag{685b42b0-da3d-47f4-a76c-0f3d07ea962a}