SM4算法简介
SM4为分组对称密码算法,明文、密文以及密钥长度均为 128 128 128 bits。SM4算法主要包括加解密算法和密钥扩展算法,采用 32 32 32 轮非线性迭代的数学结构,其中算法中每一次迭代运算为一轮非线性变换。主要操作包括异或、合成置换、非线性迭代、反序变换、循环移位以及S盒变换等。加密算法和解密算法的数学架构、运算法则、运算操作等都是完全相同的,解密运算只需要将加密算法中生成的轮密钥进行反序使用。其流程图如下图所示。
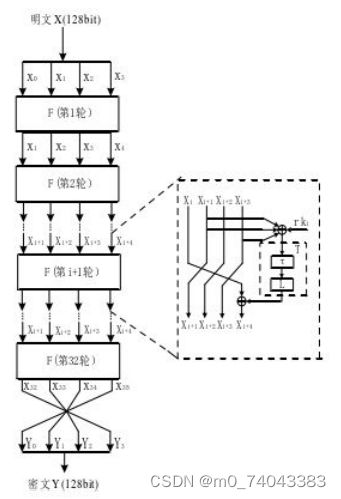
图1. SM4密码算法加密流程图
密钥扩展算法
设加密主密钥 M K = ( M K 0 , M K 1 , M K 2 , M K 3 ) MK = (MK_0, MK_1, MK_2, MK_3) MK=(MK0,MK1,MK2,MK3), M K i ∈ { 0 , 1 } 32 MK_i \in \{0,1\}^{32} MKi∈{0,1}32
( K 0 , K 1 , K 2 , K 3 ) = ( M K 0 ⊕ F K 0 , M K 1 ⊕ F K 1 , M K 2 ⊕ F K 2 , M K 3 ⊕ F K 3 ) (K_0,K_1,K_2, K_3) = (MK_0 \oplus FK_0, MK_1 \oplus FK_1, MK_2 \oplus FK_2, MK_3 \oplus FK_3) (K0,K1,K2,K3)=(MK0⊕FK0,MK1⊕FK1,MK2⊕FK2,MK3⊕FK3)
r k i = K i + 4 = K i ⊕ T ′ ( K i + 1 ⊕ K i + 2 ⊕ K i + 3 ⊕ C K i ) rk_i = K_{i+4} = K_i \oplus T^{'}(K_{i+1} \oplus K_{i+2} \oplus K_{i+3} \oplus CK_i) rki=Ki+4=Ki⊕T′(Ki+1⊕Ki+2⊕Ki+3⊕CKi)
T ′ T^{'} T′变换
T ′ ( B ) = B ⊕ ( B < < < 13 ) ⊕ ( B < < < 23 ) T^{'}(B) = B \oplus (B <<< 13) \oplus (B <<< 23) T′(B)=B⊕(B<<<13)⊕(B<<<23)
系统参数 F K FK FK
| F K i FK_i FKi | 十六进制取值 |
|---|---|
| F K 0 FK_0 FK0 | A3B1BAC6 |
| F K 1 FK_1 FK1 | 56AA3350 |
| F K 2 FK_2 FK2 | 677D9197 |
| F K 3 FK_3 FK3 | B27022DC |
固定参数 C K CK CK
| 固定参数 CK 的取值 | |||
| 000070e15 | 1c232a31 | 383f464d | 545b6269 |
| 70777e85 | 8c939aa1 | a8afb6bd | c4cbd2d9 |
| e0e7eef5 | fc030a11 | 181f262d | 343b4249 |
| 50575e65 | 6c737a81 | 888f969d | a4abb2b9 |
| c0c7ced5 | dce3eaf1 | f8ff060d | 141b2229 |
| 3037aeb5 | 4c535a61 | 686f767d | 848b9299 |
| a0a7aeb5 | bcc3cad1 | d8dfe6ed | f4fb0209 |
| 10171e25 | 2e333a41 | 484f565d | 646b7279 |
加解密算法
设输入明文为: ( X 0 , X 1 , X 2 , X 3 ) ∈ { 0 , 1 } 32 × 4 (X_0, X_1, X_2, X_3) \in \{0,1\}^{32 \times 4} (X0,X1,X2,X3)∈{0,1}32×4, 密文输出为: ( Y 0 , Y 1 , Y 2 , Y 3 ) ∈ { 0 , 1 } 32 × 4 (Y_0, Y_1, Y_2, Y_3) \in \{0,1\}^{32 \times 4} (Y0,Y1,Y2,Y3)∈{0,1}32×4, 轮密钥 r k i ∈ { 0 , 1 } 32 × 4 rk_i \in \{0,1\}^{32 \times 4} rki∈{0,1}32×4, 其中 i ∈ { 0 , 1 , ⋯ 31 } i \in \{0,1,\cdots 31\} i∈{0,1,⋯31}.SM4密码算法的具体加密过程如下:
X i + 1 = F ( X i , X i + 1 , X i + 2 , X i + 3 , r k i ) = X i ⊕ T ( X i + 1 ⊕ X i + 2 ⊕ X i + 3 ⊕ r k i ) X_{i+1} = F(X_{i}, X_{i+1}, X_{i+2}, X_{i+3}, rk_i)=X_{i}\oplus T(X_{i+1}\oplus X_{i+2}\oplus X_{i+3}\oplus rk_i) Xi+1=F(Xi,Xi+1,Xi+2,Xi+3,rki)=Xi⊕T(Xi+1⊕Xi+2⊕Xi+3⊕rki);
( Y 0 , Y 1 , Y 2 , Y 3 ) = R ( X 32 , X 33 , X 34 , X 35 ) = ( X 35 , X 34 , X 33 , X 32 ) (Y_0, Y_1, Y_2, Y_3) = R(X_{32}, X_{33}, X_{34}, X_{35}) = (X_{35}, X_{34}, X_{33}, X_{32}) (Y0,Y1,Y2,Y3)=R(X32,X33,X34,X35)=(X35,X34,X33,X32)
合成置换 T
由非线性变换 τ \tau τ和线性变换 L L L的转换, T ( ⋅ ) = L ( τ ( ⋅ ) ) T(\cdot)=L(\tau(\cdot)) T(⋅)=L(τ(⋅))
非线性变换 τ \tau τ : 长度为 32 bits, 由4 个并行的8位输入输出的S盒组成,表示为 S b o x ( ⋅ ) Sbox(\cdot) Sbox(⋅)
( B 0 , B 1 , B 2 , B 3 ) = τ ( A ) = ( S b o x ( A 0 ) , S b o x ( A 1 ) , S b o x ( A 2 ) , S b o x ( A 3 ) ) (B_0, B_1, B_2, B_3) = \tau(A) = (Sbox(A_0), Sbox(A_1), Sbox(A_2), Sbox(A_3)) (B0,B1,B2,B3)=τ(A)=(Sbox(A0),Sbox(A1),Sbox(A2),Sbox(A3))
线性变换 L L L : B = L ( A ) = A ⊕ ( A < < < 2 ) ⊕ ( A < < < 10 ) ⊕ ( A < < < 18 ) ⊕ ( A < < < 24 ) B = L(A) = A\oplus(A <<< 2)\oplus(A <<< 10)\oplus(A <<< 18)\oplus(A <<< 24) B=L(A)=A⊕(A<<<2)⊕(A<<<10)⊕(A<<<18)⊕(A<<<24)
S盒
S盒是SM4算法中唯一的非线性逻辑单元,国家密码局公布的SM4密码时,直接给出了算法中S盒的查找表信息,输入为8 bits,其中,高4bits为查找表的行信息,后4bits为查找表的列信息。
| - | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | a | b | c | d | e | f |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 0xd6 | 0x90 | 0xc9 | 0xfe | 0xcc | 0xe1 | 0x3d | 0xb7 | 0x16 | 0xb6 | 0x14 | 0xc2 | 0x28 | 0xfb | 0x2c | 0x05 |
| 1 | 0x2b | 0x67 | 0x9a | 0x76 | 0x2a | 0xbe | 0x04 | 0xc3 | 0xaa | 0x44 | 0x13 | 0x26 | 0x49 | 0x86 | 0x06 | 0x99 |
| 2 | 0x9c | 0x42 | 0x50 | 0xf4 | 0x91 | 0xef | 0x98 | 0x7a | 0x33 | 0x54 | 0x0b | 0x43 | 0xed | 0xcf | 0xac | 0x62 |
| 3 | 0xe4 | 0xb3 | 0x1c | 0xa9 | 0xc9 | 0x08 | 0xe8 | 0x95 | 0x80 | 0xdf | 0x94 | 0xfa | 0x75 | 0x8f | 0x3f | 0xa6 |
| 4 | 0x47 | 0x07 | 0xa7 | 0xfc | 0xf3 | 0x73 | 0x17 | 0xba | 0x83 | 0x59 | 0x3c | 0x19 | 0xe6 | 0x85 | 0x4f | 0xa8 |
| 5 | 0x68 | 0x6b | 0x81 | 0xb2 | 0x71 | 0x64 | 0xda | 0x8b | 0xf8 | 0xeb | 0x0f | 0x4b | 0x70 | 0x56 | 0x9d | 0x35 |
| 6 | 0x1e | 0x24 | 0x0e | 0x5e | 0x63 | 0x58 | 0xd1 | 0xa2 | 0x25 | 0x22 | 0x7c | 0x3b | 0x01 | 0x21 | 0x78 | 0x87 |
| 7 | 0xd4 | 0x00 | 0x46 | 0x57 | 0x9f | 0xd3 | 0x27 | 0x52 | 0x4c | 0x36 | 0x02 | 0xe7 | 0xa0 | 0xc4 | 0xc8 | 0x9e |
| 8 | 0xea | 0xbf | 0x8a | 0xd2 | 0x40 | 0xc7 | 0x38 | 0xb5 | 0xa3 | 0xf7 | 0xf2 | 0xce | 0xf9 | 0x61 | 0x15 | 0xa1 |
| 9 | 0xe0 | 0xae | 0x5d | 0xa4 | 0x9b | 0x34 | 0x1a | 0x55 | 0xad | 0x93 | 0x32 | 0x30 | 0xf5 | 0x8c | 0xb1 | 0xe3 |
| a | 0x1d | 0xf6 | 0xe2 | 0x2e | 0x82 | 0x66 | 0xca | 0x60 | 0xc0 | 0x29 | 0x23 | 0xab | 0x0d | 0x53 | 0x4e | 0x6f |
| b | 0xd5 | 0xdb | 0x37 | 0x45 | 0xde | 0xfd | 0x8e | 0x2f | 0x03 | 0xff | 0x6a | 0x72 | 0x6d | 0x6c | 0x5b | 0x51 |
| c | 0x8d | 0x1b | 0xaf | 0x92 | 0xbb | 0xdd | 0xbc | 0x7f | 0x11 | 0xd9 | 0x5c | 0x41 | 0x1f | 0x10 | 0x5a | 0xd8 |
| d | 0x0a | 0xc1 | 0x31 | 0x88 | 0xa5 | 0xcd | 0x7b | 0xbd | 0x2d | 0x74 | 0xd0 | 0x12 | 0xb8 | 0xe5 | 0xb4 | 0xb0 |
| e | 0x89 | 0x69 | 0x97 | 0x4a | 0x0c | 0x96 | 0x77 | 0x7e | 0x65 | 0xb9 | 0xf1 | 0x09 | 0xc5 | 0x6e | 0xc6 | 0x84 |
| f | 0x18 | 0xf0 | 0x7d | 0xec | 0x3a | 0xdc | 0x4d | 0x20 | 0x79 | 0xee | 0x5f | 0x3e | 0xd7 | 0xcb | 0x39 | 0x48 |