加解密原理实验
加解密原理
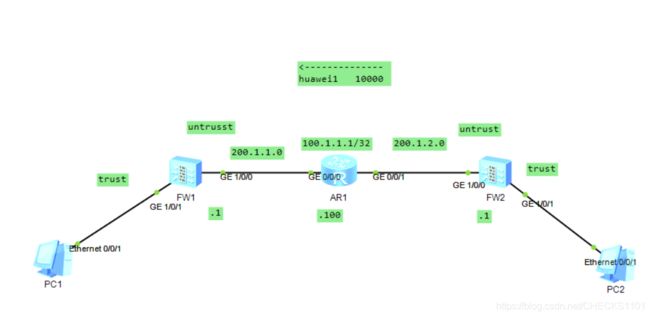
- 实验拓扑
- 实验准备
-
- 防火墙
-
- FW1
- FW2
- ISP路由
- 连通性测试
- 实验内容
-
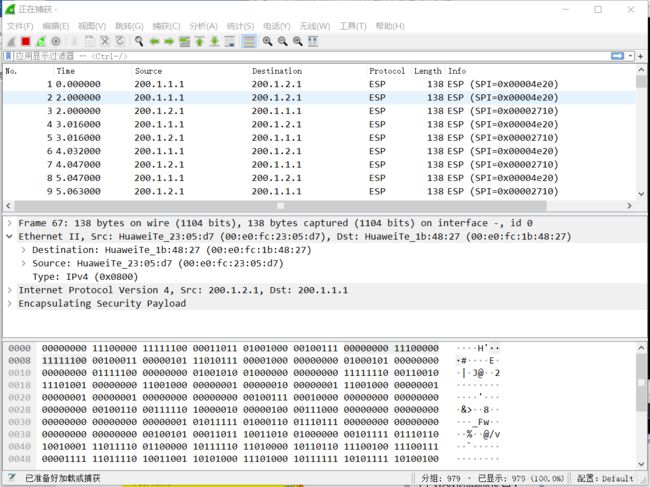
- ESP
- IKE
-
- 设置IKE
- 查看路由的公钥
实验拓扑
实验准备
防火墙
防火墙的接口默认不允许ping,打开后该接口也必须划分到安全域内才能被ping通
FW1
<USG6000V1>undo ter mo
Info: Current terminal monitor is off.
<USG6000V1>sy
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sy fw1
[fw1]int g1/0/1
[fw1-GigabitEthernet1/0/1]ip addr 192.168.1.100 24
[fw1-GigabitEthernet1/0/1]
[fw1-GigabitEthernet1/0/1]int g1/0/0
[fw1-GigabitEthernet1/0/0]ip addr 200.1.1.1 24
[fw1-GigabitEthernet1/0/0]
[fw1-GigabitEthernet1/0/0]firewall zone trust
[fw1-zone-trust]add int g1/0/1
[fw1-zone-trust]
[fw1-zone-trust]firewall zone untrust
[fw1-zone-untrust]add int g1/0/0
[fw1-zone-untrust]
[fw1-zone-untrust]dis th
2020-07-31 01:21:28.930
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
return
[fw1-zone-untrust]
[fw1-zone-untrust]
[fw1-zone-untrust]q
[fw1]
[fw1]int g1/0/0
[fw1-GigabitEthernet1/0/0]
[fw1-GigabitEthernet1/0/0]ser
[fw1-GigabitEthernet1/0/0]service-m
[fw1-GigabitEthernet1/0/0]service-manage ping permit
[fw1-GigabitEthernet1/0/0]q
[fw1]
[fw1]
[fw1]ip route-s
[fw1]ip route-static 0.0.0.0 0 200.1.1.100
[fw1]
[fw1]
FW2
<USG6000V1>undo ter mo
Info: Current terminal monitor is off.
<USG6000V1>sy
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sy fw2
[fw2]
[fw2]int g1/0/0
[fw2-GigabitEthernet1/0/0]ip addr 200.1.2.1 24
[fw2-GigabitEthernet1/0/0]
[fw2-GigabitEthernet1/0/0]ser
[fw2-GigabitEthernet1/0/0]service-
[fw2-GigabitEthernet1/0/0]service-manage ping
[fw2-GigabitEthernet1/0/0]service-manage ping permit
[fw2-GigabitEthernet1/0/0]
[fw2-GigabitEthernet1/0/0]
[fw2-GigabitEthernet1/0/0]q
[fw2]firewall zone untrust
[fw2-zone-untrust]
[fw2-zone-untrust]
[fw2-zone-untrust]add int g1/0/0
[fw2-zone-untrust]
[fw2-zone-untrust]q
[fw2]int g1/0/1
[fw2-GigabitEthernet1/0/1]ip addr 192.168.2.100 24
[fw2-GigabitEthernet1/0/1]
[fw2-GigabitEthernet1/0/1]
[fw2-GigabitEthernet1/0/1]q
[fw2]
[fw2]firewall zone trust
[fw2-zone-trust]
[fw2-zone-trust]add int g1/0/1
[fw2-zone-trust]
[fw2-zone-trust]
[fw2-zone-trust]q
[fw2]ip route-s
[fw2]ip route-static 0.0.0.0 0 200.1.2.100
[fw2]
[fw2]
ISP路由
<Huawei>sy
Enter system view, return user view with Ctrl+Z.
[Huawei]sy isp
[isp]int g0/0/0
[isp-GigabitEthernet0/0/0]ip addr 200.1.1.100 24
[isp-GigabitEthernet0/0/0]
[isp-GigabitEthernet0/0/0]
[isp-GigabitEthernet0/0/0]q
[isp]int g0/0/1
[isp-GigabitEthernet0/0/1]ip addr 200.1.2.100 24
[isp-GigabitEthernet0/0/1]
[isp-GigabitEthernet0/0/1]
[isp-GigabitEthernet0/0/1]q
[isp]
[isp]in loo0
[isp-LoopBack0]ip addr 100.1.1.1 32
[isp-LoopBack0]
[isp-LoopBack0]
连通性测试
fw1:
[fw1]sec
[fw1]security-policy
[fw1-policy-security]rule name ping
[fw1-policy-security-rule-ping]source-zone local
[fw1-policy-security-rule-ping]destination-zone untrust
[fw1-policy-security-rule-ping]ser
[fw1-policy-security-rule-ping]service icmp
[fw1-policy-security-rule-ping]service icmp
[fw1-policy-security-rule-ping]
[fw1-policy-security-rule-ping]action permit
[fw1-policy-security-rule-ping]
[fw1-policy-security-rule-ping]ping 200.1.2.1 //这个是FW2端的接口,因为已经开启了ping服务,所以可以ping通
PING 200.1.2.1: 56 data bytes, press CTRL_C to break
Reply from 200.1.2.1: bytes=56 Sequence=1 ttl=254 time=11 ms
Reply from 200.1.2.1: bytes=56 Sequence=2 ttl=254 time=11 ms
Reply from 200.1.2.1: bytes=56 Sequence=3 ttl=254 time=10 ms
Reply from 200.1.2.1: bytes=56 Sequence=4 ttl=254 time=10 ms
Reply from 200.1.2.1: bytes=56 Sequence=5 ttl=254 time=10 ms
--- 200.1.2.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 10/10/11 ms
[fw1-policy-security-rule-ping]
实验内容
ESP
1.设置一个acl,指定进入隧道的源端IP和目的IP
2.设置ipsec策略
3.设定隧道的源端和终端ip(FW1连接到FW2)
4.设置出栈入栈的密钥
5.设置出栈入栈的安全索引编号
6.在ipsec策略中应用该acl
7.把该安全提议交由FW2
8.在防火墙的接口处应用该ipsec策略
FW1和FW2的隧道出入站的密钥和安全索引编号相反
FW1:
[fw1]ipsec pr
[fw1]ipsec proposal fw2
[fw1-ipsec-proposal-fw2]enca
[fw1-ipsec-proposal-fw2]encapsulation-mode ?
auto Specify automatic mode. The responder can accept negotiations in
transport or tunnel mode. The initiator initiates negotiations in
tunnel mode
transport Only the payload of IP packet is protected(transport mode)
tunnel The entire IP packet is protected(tunnel mode)
[fw1-ipsec-proposal-fw2]encapsulation-mode
[fw1]ipsec po
[fw1]ipsec policy 1 ma
[fw1]ipsec policy 1 manual
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]tu
[fw1-ipsec-policy-manual--1]tunnel ?
local Specify the IP address of IPSec tunnel local peer
remote Specify the IP address of IPSec tunnel remote peer
[fw1-ipsec-policy-manual--1]tunnel l
[fw1-ipsec-policy-manual--1]tunnel local 200.1.1.1
[fw1-ipsec-policy-manual--1]tun
[fw1-ipsec-policy-manual--1]tunnel remote 200.1.2.1
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]dis th
2020-07-31 01:54:03.130
#
ipsec policy 1 manual
tunnel local 200.1.1.1
tunnel remote 200.1.2.1
#
return
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]sa ? //安全联盟是双向的
authentication-hex Specify the authentication key of manual SA with
hexadecimal format
binding Enable binding of an SA with a VPN instance
encryption-hex Specify the encryption key of manual SA with hexadecimal
format
spi Specify the SPI parameter of manual SA
string-key Specify the key of manual SA with string format
[fw1-ipsec-policy-manual--1]sa str
[fw1-ipsec-policy-manual--1]sa string-key in
[fw1-ipsec-policy-manual--1]sa string-key inbound esp huawei //出栈
[fw1-ipsec-policy-manual--1]sa string-key outbound esp huawei2 //入栈
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]dis th //看看效果
2020-07-31 01:58:58.170
#
ipsec policy 1 manual
tunnel local 200.1.1.1
tunnel remote 200.1.2.1
sa string-key inbound esp %^%#-Xe2${}#i-D3ZpX&v%f4b-h#S|CP#:)oF$GeX~oA%^%#
sa string-key outbound esp %^%#jf@sGqIttEdAwf1a@2a0{2X,L@q{WMme="K=:Q.W%^%#
#
return
[fw1-ipsec-policy-manual--1]sa spi ? //设置spi安全索引编号
inbound Specify parameters of inbound manual SA
outbound Specify parameters of outbound manual SA
[fw1-ipsec-policy-manual--1]sa spi in
[fw1-ipsec-policy-manual--1]sa spi inbound esp?
esp
[fw1-ipsec-policy-manual--1]sa spi inbound esp 10000
[fw1-ipsec-policy-manual--1]sa spi outbound esp 20000
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]dis th
2020-07-31 02:02:17.930
#
ipsec policy 1 manual
tunnel local 200.1.1.1
tunnel remote 200.1.2.1
sa spi inbound esp 10000
sa string-key inbound esp %^%#-Xe2${}#i-D3ZpX&v%f4b-h#S|CP#:)oF$GeX~oA%^%#
sa spi outbound esp 20000
sa string-key outbound esp %^%#jf@sGqIttEdAwf1a@2a0{2X,L@q{WMme="K=:Q.W%^%#
#
return
[fw1-ipsec-policy-manual--1]q
[fw1]
[fw1]
[fw1]acl 3000 //通过acl将流量引入隧道
[fw1-acl-adv-3000]dis th
2020-07-31 02:03:39.420
#
acl number 3000
#
return
[fw1-acl-adv-3000]rule permit ip sou
[fw1-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 192.16
8.2.0 0.0.0.255 //来源-目的IP匹配的流量进入隧道
[fw1-acl-adv-3000]
[fw1-acl-adv-3000]q
[fw1]ip
[fw1]ips
[fw1]ipsec policy 1
[fw1-ipsec-policy-manual--1]se
[fw1-ipsec-policy-manual--1]security acl 3000 //应用acl3000
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]pro
[fw1-ipsec-policy-manual--1]proposal fw2
[fw1-ipsec-policy-manual--1]
[fw1-ipsec-policy-manual--1]dis th
2020-07-31 02:08:15.930
#
ipsec policy 1 manual
security acl 3000 //控制哪些流量进入隧道
proposal fw2 //安全提议
tunnel local 200.1.1.1 //隧道发起方
tunnel remote 200.1.2.1 //隧道目的方
sa spi inbound esp 10000
sa string-key inbound esp %^%#-Xe2${}#i-D3ZpX&v%f4b-h#S|CP#:)oF$GeX~oA%^%#
sa spi outbound esp 20000
sa string-key outbound esp %^%#jf@sGqIttEdAwf1a@2a0{2X,L@q{WMme="K=:Q.W%^%#
#
return
[fw1-ipsec-policy-manual--1]q
[fw1]security-policy
[fw1-policy-security]undo rule name ping //删掉之前测试用安全策略
[fw1-policy-security]
[fw1-policy-security]d
[fw1-policy-security]default a
[fw1-policy-security]default action p
[fw1-policy-security]default action permit //放行所有流量
Warning:Setting the default packet filtering to permit poses security risks. You
are advised to configure the security policy based on the actual data flows. Ar
e you sure you want to continue?[Y/N]y
[fw1-policy-security]
[fw1-policy-security]q
[fw1]int g1/0/0
[fw1-GigabitEthernet1/0/0]dis th
2020-07-31 02:29:07.030
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 200.1.1.1 255.255.255.0
service-manage ping permit
#
return
[fw1-GigabitEthernet1/0/0]ips
[fw1-GigabitEthernet1/0/0]ipsec policy //应用到该接口,不然不会成功
[fw1-GigabitEthernet1/0/0]
[fw1-GigabitEthernet1/0/0]
Jul 31 2020 02:29:30 fw1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.191.3
.1 configurations have been changed. The current change number is 30, the change
loop count is 0, and the maximum number of records is 4095.
[fw1-GigabitEthernet1/0/0]
FW2:
[fw2]ipsec pr
[fw2]ipsec proposal fw1
[fw2-ipsec-proposal-fw1]
[fw2-ipsec-proposal-fw1]q
[fw2]acl 3000
[fw2-acl-adv-3000]rule permit ip source 192.168.2.0 0.0.0.255 de
[fw2-acl-adv-3000]rule permit ip source 192.168.2.0 0.0.0.255 dest
[fw2-acl-adv-3000]rule permit ip source 192.168.2.0 0.0.0.255 destination 192.16
8.1.0 0.0.0.255
[fw2-acl-adv-3000]
[fw2-acl-adv-3000]
[fw2-acl-adv-3000]q
[fw2]
[fw2]
[fw2]ip
[fw2]ips
[fw2]ipsec pol
[fw2]ipsec policy ?
STRING<1-15> Name of IPSec security policy
[fw2]ipsec policy 1 m
[fw2]ipsec policy 1 manual
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]dis th
2020-07-31 02:18:10.950
#
ipsec policy 1 manual
#
return
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]tu
[fw2-ipsec-policy-manual--1]tunnel local
[fw2-ipsec-policy-manual--1]tunnel local 200.1.2.1
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]tu
[fw2-ipsec-policy-manual--1]tunnel re
[fw2-ipsec-policy-manual--1]tunnel remote 200.1.1.1
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]se
[fw2-ipsec-policy-manual--1]security acl 3000
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]pr
[fw2-ipsec-policy-manual--1]proposal fw1
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]sa spi out
[fw2-ipsec-policy-manual--1]sa spi outbound esp 10000
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]sa spi in
[fw2-ipsec-policy-manual--1]sa spi inbound esp 20000
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]sa str
[fw2-ipsec-policy-manual--1]sa string-key out
[fw2-ipsec-policy-manual--1]sa string-key outbound esp huawei
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]sa string-key in
[fw2-ipsec-policy-manual--1]sa string-key inbound esp huawei2
[fw2-ipsec-policy-manual--1]
[fw2-ipsec-policy-manual--1]q
[fw2]int g1/0/0
[fw2-GigabitEthernet1/0/0]ips
[fw2-GigabitEthernet1/0/0]ipsec policy //应用到该接口
[fw2-GigabitEthernet1/0/0]q
[fw2]sec
[fw2]security-policy
[fw2-policy-security]de
[fw2-policy-security]default action permit
Warning:Setting the default packet filtering to permit poses security risks. You
are advised to configure the security policy based on the actual data flows. Ar
e you sure you want to continue?[Y/N]Y
[fw2-policy-security]
IKE
1.设置ipsec策略
2.设置感兴趣流
3.配置IKE安全提议
4.配置IKE对等体
5.配置ipsec策略
6.应用到接口
先删除掉上一个实验设下的ipsec策略
FW1:
[fw1]undo ips
[fw1]undo ipsec po
[fw1]undo ipsec policy
Warning: This operation may delete the corresponding SA, Continue? [Y/N]:y
Info:All IPSec configurations with this policy group are deleted.
[fw1]
Jul 31 2020 02:43:30 fw1 DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5.25.191.3
.1 configurations have been changed. The current change number is 31, the change
loop count is 0, and the maximum number of records is 4095.
[fw1]dis cu
[fw1]dis current-configuration int
[fw1]dis current-configuration interface
2020-07-31 02:43:47.840
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding -instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 200.1.1.1 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.1.100 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
return
[fw1]
[fw1]
[fw1]
FW2:
[fw2]undo ip
[fw2]undo ips
[fw2]undo ipsec p
[fw2]undo ipsec po
[fw2]undo ipsec policy
Warning: This operation may delete the corresponding SA, Continue? [Y/N]:y
Info:All IPSec configurations with this policy group are deleted.
[fw2]
设置IKE
FW1:
[fw1]ips
[fw1]ipsec p
[fw1]ipsec proposal fw2
[fw1-ipsec-proposal-fw2]
[fw1-ipsec-proposal-fw2]
[fw1-ipsec-proposal-fw2]q
[fw1]acl 3000 //上面已经设置过了
[fw1-acl-adv-3000]dis th
2020-07-31 02:50:08.810
#
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
return
[fw1-acl-adv-3000]
[fw1-acl-adv-3000]q
[fw1]ike p
[fw1]ike proposal 1
[fw1-ike-proposal-1]
[fw1-ike-proposal-1]dis th
2020-07-31 02:54:04.620
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
return
[fw1-ike-proposal-1]q
[fw1]ike peer fw2 //设置IKE
[fw1-ike-peer-fw2]
[fw1-ike-peer-fw2]
[fw1-ike-peer-fw2]pre-s
[fw1-ike-peer-fw2]pre-shared-key [email protected] //设置密钥
[fw1-ike-peer-fw2]
[fw1-ike-peer-fw2]dis th
2020-07-31 02:58:37.480
#
ike peer fw2
pre-shared-key %^%#7|%;~'e^6RDgdRIcLiK!%nj!R\a.C"[dzo~_hxT$%^%#
#
return
[fw1-ike-peer-fw2]
[fw1-ike-peer-fw2]ike-
[fw1-ike-peer-fw2]ike-proposal 1
[fw1]ike peer fw2
[fw1-ike-peer-fw2]remote-a
[fw1-ike-peer-fw2]remote-address 200.1.2.1
[fw1-ike-peer-fw2]
[fw1-ike-peer-fw2]undo ver
[fw1-ike-peer-fw2]undo version 2
[fw1-ike-peer-fw2]dis th
2020-07-31 03:02:23.880
#
ike peer fw2
undo version 2 //取消版本2
pre-shared-key %^%#7|%;~'e^6RDgdRIcLiK!%nj!R\a.C"[dzo~_hxT$%^%# //配置的密钥
ike-proposal 1 //绑定IKE安全提议
remote-address 200.1.2.1 //对端的IP地址
#
return
[fw1-ike-peer-fw2]q
[fw1]
[fw1]dis ike peer
2020-07-31 03:03:02.660
Number of IKE peers: 1
-----------------------------------------------------------
Peer name : fw2
IKE version : v1
VPN instance : -
Remote IP : 200.1.2.1
Authentic IP address : -
Proposal : 1
Exchange mode : main on phase 1
Pre-shared-key : %^%#7|%;~'e^6RDgdRIcLiK!%nj!R\a.C"[
dzo~_hxT$%^%#
Local ID type : IP
Local ID : -
Remote ID type : -
Remote ID : -
certificate local-filename : -
certificate peer-filename : -
certificate peer-name : -
PKI realm : NULL
Inband OCSP : Disable
Inband CRL : Disable
cert-request empty-payload : Disable
VPN instance bound to the SA : -
NAT-traversal : Enable
Xauth : Disable
Xauth type : CHAP
DSCP : -
Lifetime-notification-message : Disable
DPD : Disable
DPD message : seq-hash-notify
DPD message learning : Enable
DPD packet receive if-related : Disable
RSA encryption-padding : PKCS1
RSA signature-padding : PKCS1
ipsec sm4 version : draft-standard
Certificate-access-policy : -
IKE negotiate compatible : -
Certificate-check : Enable
Resource acl : -
validate-certificate whitelist : Disable
whitelist-fuzzy-match : Disable
Local ID Certificate Preference : Enable
IKEv2 Local ID Reflect : Enable
IKEv1 phase1-phase2 sa dependent : Enable
IKEv2 fragmentation : Disable
IKEv2 authentication signature-hash : SHA1
-----------------------------------------------------------
[fw1]
[fw1]ips
[fw1]ipsec p
[fw1]ipsec pol
[fw1]ipsec policy 1
Error: This IPSec policy/sequence combination is new, please indicate the mode t
o finish creating it.
[fw1]ipsec policy 1 isakmp //创建策略
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[fw1-ipsec-policy-isakmp--1]sec
[fw1-ipsec-policy-isakmp--1]security
[fw1-ipsec-policy-isakmp--1]security acl 3000 //绑定感兴趣流
[fw1-ipsec-policy-isakmp--1]
[fw1-ipsec-policy-isakmp--1]dis th
2020-07-31 03:09:40.780
#
ipsec policy 1 isakmp
security acl 3000
#
return
[fw1-ipsec-policy-isakmp--1]
[fw1-ipsec-policy-isakmp--1]ike-peer fw2 //绑定IKE对等体
[fw1-ipsec-policy-isakmp--1]
[fw1-ipsec-policy-isakmp--1]pr
[fw1-ipsec-policy-isakmp--1]proposal
[fw1-ipsec-policy-isakmp--1]proposal fw2 //绑定ipsec安全提议
[fw1-ipsec-policy-isakmp--1]
[fw1-ipsec-policy-isakmp--1]dis th
2020-07-31 03:10:05.370
#
ipsec policy 1 isakmp
security acl 3000
ike-peer fw2
proposal fw2
#
return
[fw1-ipsec-policy-isakmp--1]q
[fw1]
[fw1]int g1/0/0
[fw1-GigabitEthernet1/0/0]ipsec policy
[fw1-GigabitEthernet1/0/0]
FW2:
[fw2]
[fw2]ips
[fw2]ipsec p
[fw2]ipsec proposal fw1
[fw2-ipsec-proposal-fw1]
[fw2-ipsec-proposal-fw1]q
[fw2]
[fw2]acl 3000
[fw2-acl-adv-3000]dis th
2020-07-31 03:22:55.620
#
acl number 3000
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
#
return
[fw2-acl-adv-3000]q
[fw2]
[fw2]ike p
[fw2]ike proposal 1
[fw2-ike-proposal-1]
[fw2-ike-proposal-1]dis th
2020-07-31 03:23:23.290
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
return
[fw2-ike-proposal-1]q
[fw2]
[fw2]ike peer fw1
[fw2-ike-peer-fw1]
[fw2-ike-peer-fw1]ike-p
[fw2-ike-peer-fw1]ike-proposal 1
[fw2-ike-peer-fw1]
[fw2-ike-peer-fw1]pr
[fw2-ike-peer-fw1]pre-shared-key [email protected]
[fw2-ike-peer-fw1]
[fw2-ike-peer-fw1]dis th
2020-07-31 03:24:29.480
#
ike peer fw1
pre-shared-key %^%#*"P=W:|h{NFDVL5To[f(OP@g=TBkH*|d6iN4aGD+%^%#
ike-proposal 1
#
return
[fw2-ike-peer-fw1]re
[fw2-ike-peer-fw1]remote-a
[fw2-ike-peer-fw1]remote-address 200.1.1.1
[fw2-ike-peer-fw1]
[fw2-ike-peer-fw1]undo v
[fw2-ike-peer-fw1]undo version 2
[fw2-ike-peer-fw1]q
[fw2]
[fw2]ip
[fw2]ipsec po
[fw2]ipsec policy vvvv 1 isakmp
Info: The ISAKMP policy sequence number should be smaller than the template poli
cy sequence number in the policy group. Otherwise, the ISAKMP policy does not ta
ke effect.
[fw2-ipsec-policy-isakmp-vvvv-1]sec
[fw2-ipsec-policy-isakmp-vvvv-1]security acl 3000
[fw2-ipsec-policy-isakmp-vvvv-1]pr
[fw2-ipsec-policy-isakmp-vvvv-1]proposal fw1
[fw2-ipsec-policy-isakmp-vvvv-1]
[fw2-ipsec-policy-isakmp-vvvv-1]ike-
[fw2-ipsec-policy-isakmp-vvvv-1]ike-peer fw1
[fw2-ipsec-policy-isakmp-vvvv-1]
[fw2-ipsec-policy-isakmp-vvvv-1]q
[fw2]
[fw2]
[fw2]int g1/0/0
[fw2-GigabitEthernet1/0/0]ipse
[fw2-GigabitEthernet1/0/0]ipsec po
[fw2-GigabitEthernet1/0/0]ipsec policy vvvv
[fw2-GigabitEthernet1/0/0]
[fw2-GigabitEthernet1/0/0]
查看路由的公钥
<r1>sy
Enter system view, return user view with Ctrl+Z.
[r1]rsa ?
local-key-pair Local RSA public key pair operations
peer-public-key Remote peer RSA public key configuration.
[r1]rs lo
[r1]rs local
[r1]rs local-key-pair ?
create Create new local public key pairs
destroy Destroy the local public key pairs
[r1]rs local-key-pair c
[r1]rs local-key-pair create
The key name will be: Host
% RSA keys defined for Host already exist.
Confirm to replace them? (y/n)[n]:n
[r1]dis rsa l
[r1]dis rsa local-key-pair?
local-key-pair Local public key pairs information
[r1]dis rsa local-key-pair public
=====================================================
Time of Key pair created: 2007-08-25 16:35:02-08:00 //作为主机时的公钥
Key name: Host
Key type: RSA encryption Key
=====================================================
Key code:
3047
0240
C974420D DD712C58 36A67819 362FEB9C 9C17E326
24101B32 C272F9C9 E3CD06EB C2C73F7C BC89A0E0
994995EF 7885F359 57B25237 3D441556 A050F823
6087E121
0203
010001
=====================================================
Time of Key pair created: 2007-08-25 17:11:59-08:00 //作为服务器时的公钥
Key name: Server
Key type: RSA encryption Key
=====================================================
Key code:
3067
0260
C1102C7B 2CAB4FAB CD7DCD2C 32D0CCE6 8B995872
2AD83815 39F82B8F 2680B89C A02A8A92 655894E7
48B382E7 B17616E5 01C1B8ED 1D5C7CC3 FFF7453F
E0304E50 D4DBE481 E3CDF7E1 6665569A AC5DEBAE
DC7B048B B954F568 1432935B 92AADCB5
0203
010001
[r1]