NSSCTF靶场练习---HNCTF2022Week3&4部分wp
文章目录
- [HNCTF 2022 WEEK3]What's 1n DLL?
- [HNCTF 2022 WEEK3]Try2debugPlusPlus
- [HNCTF 2022 WEEK3]Help_Me!
- [HNCTF 2022 WEEK4]ez_maze
[HNCTF 2022 WEEK3]What’s 1n DLL?
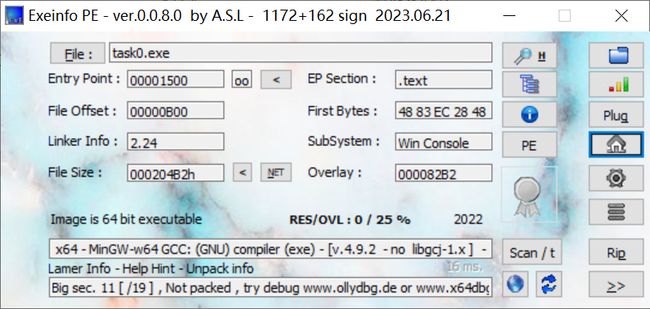
查壳先,64bit文件; IDA64打开;
发现了密文以及一个key,但是decrypt在哪?
hModule = LoadLibraryA("Dll1.dll");
ProcAddress = GetProcAddress(hModule, "ttt");
这里用 LoadLibrary 加载了一个名为Dll1.dll的动态链接库,这个函数会返回一个模块的句柄hModule。之后用 GetProcAddress函数来获取DLL中某个导出函数的地址,在这里就是,加载Dll1.dll,来获取其中名为ttt的函数地址,之后将其保存在ProcAddress变量中。
因此我们直接去逆Dll1.dll就好。
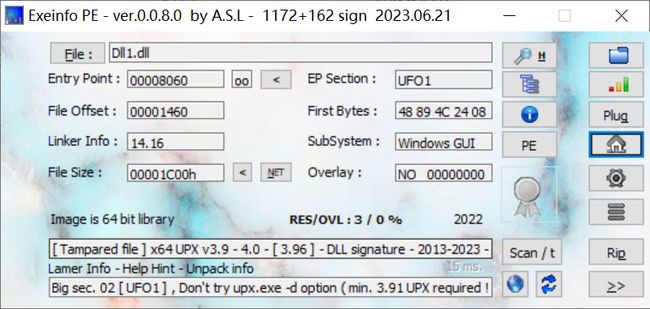
也同样先查个壳
发现了UPX加壳,同时EP Section的UPX标识被魔改了。
用WinHex打开看看
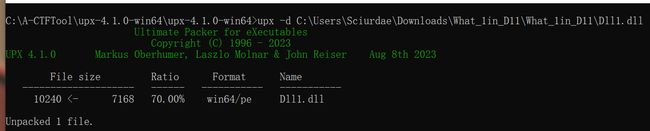
手动修改过来就好。之后再用UPX -d 脱壳
IDA64加载后,找到ttt函数
是一个XXTEA的加密,找个脚本解密。
EXP:
#include [HNCTF 2022 WEEK3]Try2debugPlusPlus
先查壳,无壳,64bit
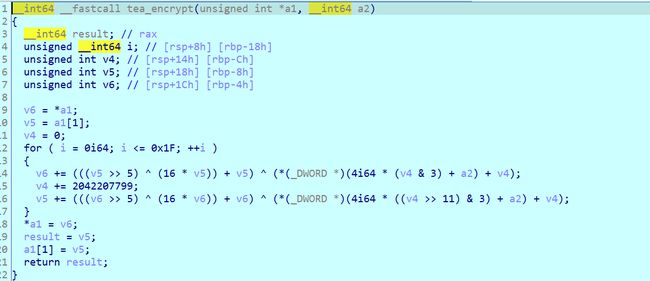
IDA64打开,发现就是一个TEA加密,然后用dododo函数对v6(key)做了加密。
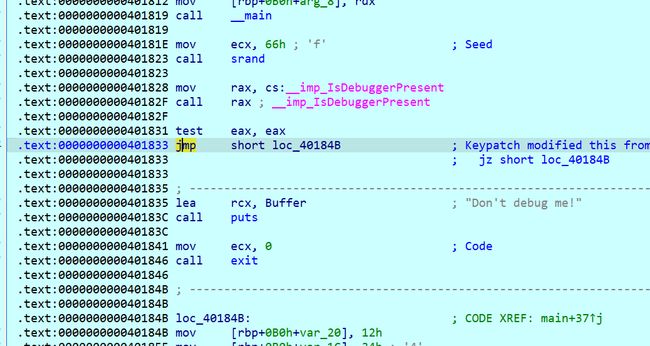
考察的是一个antidebug反调试的技巧。
不过这题不用怎么过,直接动态调试就好,断点下载11行main函数处,之后看汇编,在第一处exit处要跳过
之后就一直F8,直到程序打印出新的key就好了。
看tea_encrypt,
EXP:
#include [HNCTF 2022 WEEK3]Help_Me!
IDA打开后
运行一下程序。
一个动态规划的问题,01背包问题。用个脚本解决
EXP:
def knapsack(weights, values, capacity):
n = len(weights)
dp = [[0] * (capacity + 1) for _ in range(n + 1)]
for i in range(1, n + 1):
for w in range(capacity + 1):
if weights[i - 1] <= w:
dp[i][w] = max(dp[i - 1][w], dp[i - 1][w - weights[i - 1]] + values[i - 1])
else:
dp[i][w] = dp[i - 1][w]
selected_items = []
i, w = n, capacity
while i > 0 and w > 0:
if dp[i][w] != dp[i - 1][w]:
selected_items.append(i - 1)
w -= weights[i - 1]
i -= 1
return dp[n][capacity], selected_items
# 作业信息
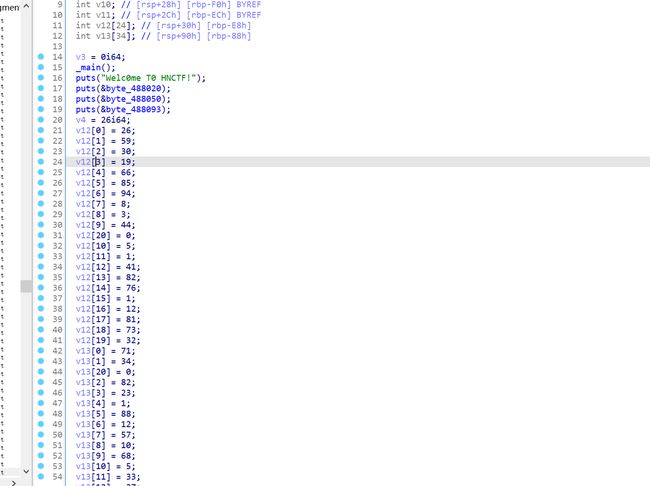
values = [26,59,30,19,66,85,94,8,3,44,5,1,41,82,76,1,12,81,73,32,0]
weights = [71,34,82,23,1,88,12,57,10,68,5,33,37,69,98,24,26,83,16,26,0]
# 容量
capacity = 200
max_value, selected_items = knapsack(weights, values, capacity)
print("最大含金量:", max_value)
print("选择的作业编号:", selected_items)
# 最大含金量: 452
# 选择的作业编号: [19, 18, 13, 12, 10, 6, 4, 1]
之后再次运行程序,输入作业
[HNCTF 2022 WEEK4]ez_maze
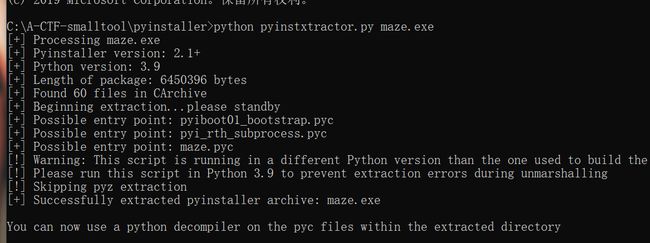
pyinstaller编译的,py逆向
解包一下,然后反编译
迷宫题,
EXP:
maze = [1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1]
maze[31*29+29] = 2
# maze[x * 21 + y]
def check_point_valid(map, x, y):
if (x >= 0) and (x <= 31) and (y >= 0) and (y <= 31):
return (map[x * 31 + y] != 1) and ((map[x * 31 + y] == 0) or (map[x * 31 + y] == 2))
else:
return False
def gen_nex(map, x, y):
all_dir = []
# if check_point_valid(map, x - 1, y, z):
# all_dir.append((x - 1, y, z, 'q'))
# if check_point_valid(map, x + 1, y, z):
# all_dir.append((x + 1, y, z, 'u'))
if check_point_valid(map, x + 1, y):
all_dir.append((x + 1, y, 's'))
if check_point_valid(map, x - 1, y):
all_dir.append((x - 1, y, 'w'))
if check_point_valid(map, x, y - 1):
all_dir.append((x, y - 1, 'a'))
if check_point_valid(map, x, y + 1):
all_dir.append((x, y + 1, 'd'))
return all_dir
def check_success(map, x, y):
if map[x * 31 + y] == 2:
return True
else:
return False
def dfs(mapb, x, y, path):
map = mapb.copy()
if map[x * 31 + y] != 2:
map[x * 31 + y] = 1
if check_success(map, x, y):
print(path)
return True
next_point = gen_nex(map, x, y)
for n in next_point:
pathn = path + n[2]
dfs(map, n[0], n[1], pathn)
outpus = ""
dfs(maze, 1, 1, outpus)
# ssssddssaassddddwwwwddwwddddddwwddddddssddwwddddddddssssaawwaassaassaassddssaassaawwwwwwaaaaaaaassaassddddwwddssddssssaassddssssaaaaaawwddwwaawwwwaassssssssssssddddssddssddddddddwwaaaaaawwwwddssddwwwwwwwwddssddssssssssddddss
# NSSCTF{801f190737434100e7d2790bd5b0732e}