Unity查安卓Native Crash的方法,定位SO报错函数
这边需要用到两个工具Il2CppDumper和IDA_Pro,网上可以下到对应的软件
日志分析
下面是出错的日志
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: FATAL EXCEPTION: UnityMain
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Process: com.yourcompany.yourapp, PID: 20882
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: java.lang.Error: *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Version '2020.1.0f1c1 (7a56d016043e)', Build type 'Release', Scripting Backend 'il2cpp', CPU 'arm64-v8a'
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Build fingerprint: 'vivo/PD2171/PD2171:12/SP1A.210812.003/compiler01090300:user/release-keys'
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Revision: '0'
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: ABI: 'arm64'
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Timestamp: 2022-01-17 18:03:53+0800
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: pid: 20882, tid: 21037, name: UnityMain >>> com.yourcompany.yourapp <<<
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: uid: 10435
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x381
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Cause: null pointer dereference
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x0 0000000000000001 x1 0000007260002020 x2 0000000000000001 x3 0000007342614763
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x4 000000000000019f x5 0404000808000000 x6 0000000000000000 x7 7f7f7f7f7f7f7f7f
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x8 0000000000000001 x9 22fbc14e494d93d0 x10 0000000000000090 x11 0000000000000006
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x12 00000073b1835560 x13 0000000000000266 x14 0000000000000002 x15 0000005c3770c4a6
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x16 0000007342873958 x17 00000076770726ec x18 0000000000000000 x19 000000734289d190
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x20 00000071e1a01fe0 x21 000000734289d238 x22 0000000000000070 x23 000000734288c590
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x24 0000000000000010 x25 000000000000001c x26 000000000000001c x27 000000734288ddc6
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: x28 0000000000000018 x29 0000000000003234
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: sp 00000073b1836fb0 lr 0000007341e9d260 pc 0000007341e9d2a8
01-17 18:03:54.146267 20882 21037 E AndroidRuntime:
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: backtrace:
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #00 pc 00000000005cf2a8 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #01 pc 00000000005cee48 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #02 pc 00000000005ced98 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #03 pc 0000000000186964 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #04 pc 00000000001889e8 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #05 pc 00000000001e0928 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #06 pc 00000000001e0788 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #07 pc 00000000001e0a38 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #08 pc 00000000001e12b8 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #09 pc 00000000001e1204 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #10 pc 00000000001a6c04 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #11 pc 00000000001f7150 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146267 20882 21037 E AndroidRuntime: #12 pc 00000000002ff038 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #13 pc 00000000002ff94c /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #14 pc 00000000002ffaf4 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #15 pc 00000000002ffd38 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #16 pc 0000000000153d78 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #17 pc 0000000000153c24 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #18 pc 000000000014b958 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #19 pc 0000000000168bb0 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libunity.so (BuildId: 6b738db2131ee7b245c098855deeb33ca74d64ae)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #20 pc 0000000000a8a5c8 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #21 pc 000000000150933c /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #22 pc 0000000001509f0c /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #23 pc 000000000158d2f4 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #24 pc 000000000158d3fc /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #25 pc 00000000012edbf8 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #26 pc 000000000144b060 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #27 pc 000000000144a128 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.yourcompany.yourapp-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)分析错误日志,获取一些大致的信息。
第4行日志:01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Version '2020.1.0f1c1 (7a56d016043e)', Build type 'Release', Scripting Backend 'il2cpp', CPU 'arm64-v8a'
这里是64位的设备出错了,这个影响后面解包时候选择的so架构
第12行日志:01-17 18:03:54.146267 20882 21037 E AndroidRuntime: Cause: null pointer dereference
说明出错的问题是空指针
第13行开始到第21行是具体的出错的内容。
第23行 01-17 18:03:54.146267 20882 21037 E AndroidRuntime: backtrace:
backtrace之后的代表是出错时候的调用堆栈
第44行日志:01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #20 pc 0000000000a8a5c8 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.bianfeng.qsgdmj.vivo-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
可以看到报错的位置是libil2cpp.so 0000000000a8a5c8
接下来要做的事情就是找到0000000000a8a5c8对应的函数是哪个
解包
Il2CppDumper解析so文件和符号表,查看对应的函数表
把apk后缀改成zip后解压,获得包内的libil2cpp.so和global-metadata.dat
两个文件路径分别是lib\arm64-v8a\libil2cpp.so和assets\bin\Data\Managed\Metadata\global-metadata.dat(这里取arm64-v8a的文件是根据之前报错日志的显示的架构选择的)
打开Il2CppDumper,先选libil2cpp.so,再选global-metadata.dat
如果成功的话会输出
Dumping...
Done!
Generate script...
Done!
Generate dummy dll...
Done!
然后在Il2CppDumper所在的目录,可以看到dump.cs,这个就是函数表文件
IDA PRO解析SO文件,查看对应报错的函数
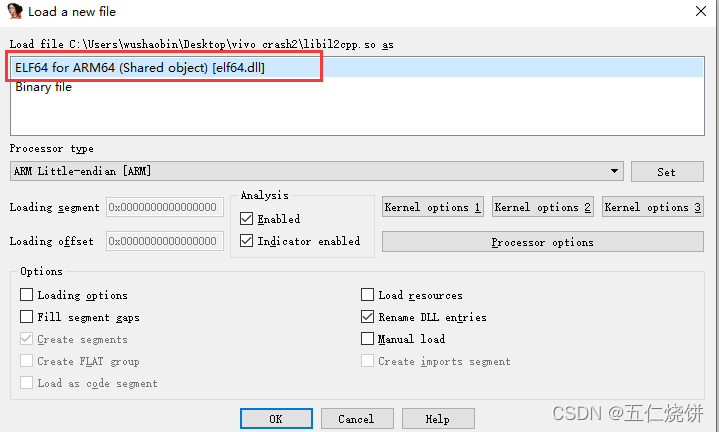
打开IDA PRO,把libil2cpp.so拖进去,选择ARM64
按G弹出跳转框
根据之前堆栈的地址
01-17 18:03:54.146300 20882 21037 E AndroidRuntime: #20 pc 0000000000a8a5c8 /data/app/~~ApTH7g1Fu1WkxGtmxL8uSA==/com.bianfeng.qsgdmj.vivo-_MTRV6bg34Akmituc-BcOA==/lib/arm64/libil2cpp.so (BuildId: 0359cbb668fd200bf13c339d5ba838cb7823d878)
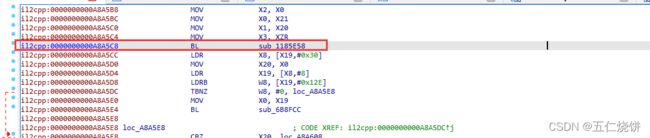
输入a8a5c8 跳转到指定位置
可以看到sub_1185e58。sub后面的1185e58就是函数地址
(有的时候跳转会出现下面的图,效果是一样的,选中的行也是sub_1185e58)
在之前的解出的函数表dump.cs搜索1185e58
找到对应的函数,可以看到报错的函数是LoadAsset,对应的类是AssetBundle
之后通过相同的方式可以找到其他报错函数,可以获得整个调用的函数堆栈。
注意有的时候跳转到对应的行会出现以下的情况,这是因为IDA解析较慢,有时候还未解析出来,可以再等一等