解某麦数据请求参数analysis加密
意外发现一个可以查询app下载量得网站,
想筛选一下哪些下载量在1w-10w之间,大概需要5k个.。
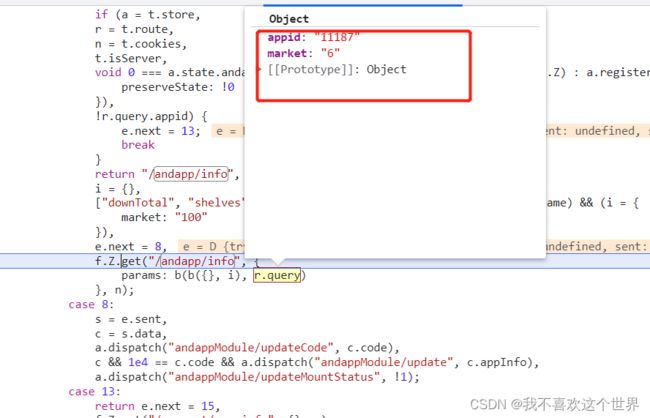
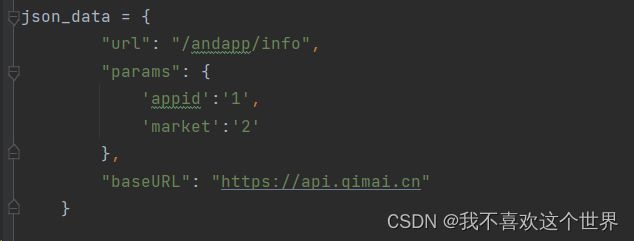
感觉应该没啥加密,好把,是我小看了,有个参数是加密得,如图。
analysis
扣js开始,
f12 去资源文件里 先去搜一下analysis,竟然没搜到,比较懵逼,咋回事。
多次换了搜索 依旧没有。那说明 这个字段被拆分了,或者被做了隐藏操作
那就只有拦截请求看看,这里也没有,奇了怪了。
先稳住,一个萝卜一个坑。待我仔细想想。
这个应该还不是最终提交的地方们,继续跟,显先看看是 fetch还是xhr请求
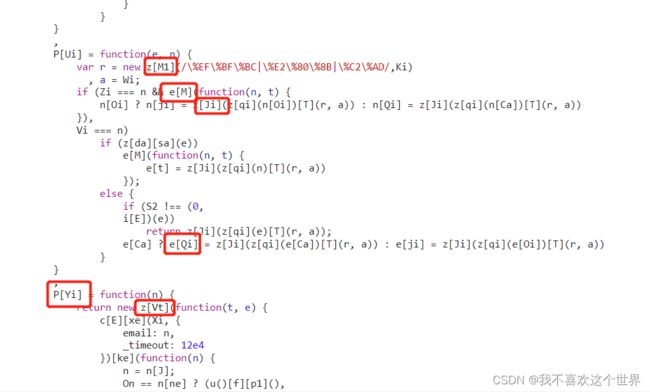
应该是xhr,直接去跟,就当我准备去跟的时候,突然返现一个问题,大量的这种代码。根据以往的经验,跑不掉了,这个就是给某些字符串 做了混淆赋值。
不要着急,编程有个规则那就是先定义后使用,直接往上层去找,随便找个字符串去搜索一下,
比如P[Yi]中的Yi,直接定位到了最上面,哈哈,就在这了。写段js把这里面定义的变量都打印出来看一下
写段js 打印一下看看:
let list1 = [z, b, t, e, C, Y, A, k, x, P, R, B, H, X, S, n2, t2, e2, r2, a2, i2, L, o2, u2, c2, _, M, f2, s2, d2, m2, l2, v2, p2, h2, y2, g2, w2, b2, T, k2, x2, S2, E, L2, N, G, I, D, M2, T2, C2, A2, P2, z2, R2, B2, H2, _2, E2, N2, G2, I2, D2, $2, F2, U2, K2, W2, Z2, O2, j2, J2, $, q2, F, Q2, V2, Y2, U, K, X2, n1, t1, e1, r1, a1, i1, o1, u1, c1, f1, s1, d1, m1, l1, v1, p1, h1, y1, g1, w1, b1, k1, x1, S1, L1, M1, T1, C1, A1, P1, W, z1, R1, B1, H1, _1, E1, N1, G1, I1, D1, $1, F1, U1, K1, W1, Z1, O1, j1, J1, q1, Q1, V1, Y1, X1, n3, t3, e3, r3, a3, i3, o3, u3, c3, f3, s3, d3, m3, l3, v3, p3, h3, y3, g3, Z, w3, b3, k3, x3, S3, L3, M3, T3, C3, A3, P3, z3, R3, B3, H3, _3, E3, N3, G3, I3, D3, $3, F3, U3, K3, W3, Z3, O3, j3, J3, q3, Q3, V3, Y3, r, a, i, u, c, d, m, l, v, p, h, X3, n5, t5, e5, r5, a5, i5, o5, u5, c5, f5, s5, d5, m5, l5, v5, p5, h5, y5, g5, w5, b5, k5, x5, S5, L5, M5, T5, C5, A5, P5, z5, R5, B5, H5, _5, E5, N5, G5, I5, D5, $5, F5, U5, K5, W5, Z5, O5, j5, J5, q5, Q5, V5, Y5, X5, n6, t6, e6, r6, a6, i6, o6, u6, c6, f6, s6, d6, m6, l6, v6, p6, h6, y6, g6, w6, b6, k6, x6, S6, L6, M6, T6, C6, A6, P6, z6, R6, B6, H6, _6, E6, N6, G6, I6, D6, $6, F6, U6, K6, W6, Z6, O6, j6, J6, q6, Q6, V6, Y6, X6, n4, t4, e4, r4, a4, i4, o4, u4, c4, f4, s4, d4, m4, l4, v4, p4, h4, y4, g4, w4, b4, k4, x4, S4, L4, M4, T4, C4, A4, P4, z4, R4, B4, H4, _4, E4, N4, G4, I4, D4, $4, F4, U4, K4, W4, Z4, O4, j4, J4, q4, Q4, V4, Y4, X4, n7, t7, e7, r7, a7, i7, o7, u7, c7, f7, s7, d7, m7, l7, v7, p7, y, g, h7, y7, g7, w7, b7, k7, x7, O, w, S7, L7, M7, T7, C7, A7, P7, z7, R7, B7, H7, _7, E7, N7, G7, I7, D7, $7, F7, U7, j, K7, W7, Z7, O7, j7, J7, q7, Q7, V7, Y7, X7, n0, t0, e0, r0, a0, i0, o0, u0, c0, f0, s0, d0, m0, l0, v0, p0, h0, y0, g0, w0, b0, k0, x0, S0, L0, M0, T0, C0, A0, P0, J, z0, R0, B0, H0, _0, E0, N0, G0, I0, D0, $0, F0, U0, K0, W0, Z0, O0, j0, J0, q0, Q0, V0, Y0, X0, nn, tn, en, rn, an, on, un, cn, fn, sn, dn, mn, ln, vn, pn, hn, yn, gn, wn, bn, kn, xn, Sn, Ln, Mn, Tn, Cn, An, Pn, zn, Rn, Bn, Hn, _n, En, Nn, Gn, In, Dn, $n, Fn, Un, Kn, Wn, Zn, On, jn, Jn, qn, Qn, Vn, Yn, Xn, nt, tt, et, rt, at, it, ot, ut, ct, ft, st, dt, mt, lt, vt, pt, ht, yt, gt, wt, bt, kt, xt, St, Lt, Mt, Tt, Ct, At, Pt, zt, Rt, Bt, Ht, _t, Et, Nt, Gt, It, Dt, $t, Ft, Ut, Kt, Wt, Zt, Ot, jt, Jt, qt, Qt, Vt, Yt, Xt, ne, te, ee, re, ae, ie, oe, ue, ce, fe, se, de, me, le, ve, pe, he, ye, ge, we, be, ke, xe, Se, Le, Me, Te, Ce, Ae, Pe, ze, Re, Be, He, _e, Ee, Ne, Ge, Ie, De, $e, Fe, f, Ue, Ke, We, Ze, Oe, je, Je, qe, Qe, Ve, Ye, Xe, nr, tr, er, rr, ar, ir, or, ur, cr, fr, sr, dr, mr, lr, vr, pr, hr, yr, gr, wr, br, kr, xr, Sr, Lr, Mr, Tr, Cr, Ar, Pr, zr, Rr, Br, Hr, _r, Er, Nr, Gr, Ir, Dr, $r, Fr, Ur, Kr, Wr, Zr, Or, jr, Jr, qr, Qr, Vr, Yr, Xr, n9, t9, e9, r9, a9, i9, o9, u9, c9, f9, s9, d9, m9, l9, v9, p9, h9, y9, g9, w9, b9, k9, x9, S9, L9, M9, T9, C9, A9, P9, z9, R9, B9, H9, _9, E9, N9, G9, I9, D9, $9, F9, U9, K9, W9, Z9, O9, j9, J9, q9, Q9, V9, Y9, X9, na, ta, ea, ra, aa, ia, oa, ua, ca, fa, sa, da, ma, la, va, pa, ha, ya, ga, wa, ba, ka, xa, Sa, o, La, Ma, Ta, Ca, q, Q, Aa, Pa, za, Ra, Ba, Ha, _a, Ea, Na, s, Ga, V, Ia, Da, $a, Fa, Ua, Ka, Wa, Za, Oa, ja, Ja, qa, Qa, Va, Ya, Xa, n8, t8, e8, r8, a8, i8, o8, u8, c8, f8, s8, d8, m8, l8, v8, p8, h8, y8, g8, w8, b8, k8, x8, S8, L8, M8, T8, C8, A8, P8, z8, R8, B8, H8, _8, E8, N8, G8, I8, D8, $8, F8, U8, K8, W8, Z8, O8, j8, J8, q8, Q8, V8, Y8, X8, ni, ti, ei, ri, ai, ii, oi, ui, ci, fi, si, di, mi, li, vi, pi, hi, yi, gi, wi, bi, ki, xi, Si, Li, Mi, Ti, Ci, Ai, Pi, zi, Ri, Bi, Hi, _i, Ei, Ni, Gi, Ii, Di, $i, Fi, Ui, Ki, Wi, Zi, Oi, ji, Ji, qi, Qi, Vi, Yi, Xi, no, to, eo, ro, ao, io, oo, uo, co, fo, so, mo, lo, vo, po, ho, yo, go, wo, bo, ko, xo, So, Lo, Mo, To, Co, Ao, Po, zo, Ro, Bo, Ho, _o, Eo, No, Go, Io, Do, $o, Fo, Uo, Ko, Wo, Zo, Oo, jo, Jo, qo, Qo, Vo, Yo, Xo, nu, tu, eu, ru, au, iu, ou, uu, cu, fu, su, du, mu, lu, vu, pu, hu, yu, gu, wu, bu, ku, xu, Su, Lu, Mu, Tu, Cu, Au, Pu, zu, Ru, Bu, Hu, _u, Eu, Nu, Gu, Iu, Du, $u, Fu, Uu, Ku, Wu, Zu];
for(let i=0;i好了都出来了,打印结果里搜一下analysis,找到了,p这个字段是他
那就直接找到p在哪被用了,哈哈搜索大法,直接定位到,注意大家别傻乎乎的去搜p会很多,
可以搜"[p]"或者类似的 "p," "=p", "= p","p=","p ="," p ="
好吧,难点来了,一堆这个混淆变量,得把上下文中涉及到得js都扣出来
我就不截图了,现在博客审核得严格,贴太多会发不了
历经了半小时,全部扣完,扣得过程就不展示了:
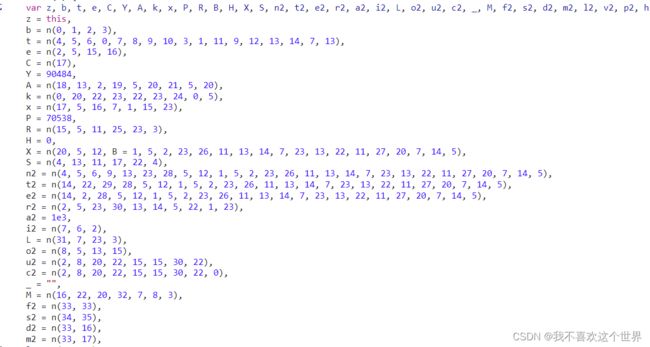
他这个是根据url生成得,删减后主要参数就这个几个,主要参数格式如图,
修改这几个变量就行了
先随机生成100w个analysis看看:
哦吼这玩意是改变得,因为代码里有时间字符串,我用的python调用得js,最好是弄个node服务看着清爽一点。拜拜 。【+qq】