映象劫持使部分程序不可运行的解决方法
Image File Execution Options (IFEO in short)劫持
一、典型症状:双击某些可执行程序无法正常执行(或者说执行了没看到预期的结果)但改一个名字就可以。
一、典型症状:双击某些可执行程序无法正常执行(或者说执行了没看到预期的结果)但改一个名字就可以。
二、典型案例:OSO.exe新变种60{.exe 美女游戏.pif (转载如下)
============================= 转载Start================================
OSO.exe 新变种
这是OSO.exe,美女游戏.pif,重要资料.exe的又一个新变种,以前截获的样本名为Worm.Pabug.ck ,这次由用户上报的病毒瑞星,金山均没有命名,但在病毒行为上大同小异。以下是具体分析:
此样本于2007年02月01日截获,跟上次的变种一样是采用记事本的图标,是一类IFEO映象劫持病毒 。(变种不同这处用红色加粗标识)
OSO.exe 新变种
这是OSO.exe,美女游戏.pif,重要资料.exe的又一个新变种,以前截获的样本名为Worm.Pabug.ck ,这次由用户上报的病毒瑞星,金山均没有命名,但在病毒行为上大同小异。以下是具体分析:
此样本于2007年02月01日截获,跟上次的变种一样是采用记事本的图标,是一类IFEO映象劫持病毒 。(变种不同这处用红色加粗标识)
病毒行为分析:病毒运行后,会不断打开run time error的消息提示,直到系统资源耗尽,当然用任务管理器,结束error窗口可暂时减少提示的生成。
生成文件如下:(以系统盘为C盘,XP SP2为例)
oso.exe的分析:
生成文件:
C:\WINDOWS\system32\drivers\60{.exe 38,510
C:\WINDOWS\system32\drivers\conime.exe 38,510
C:\WINDOWS\system32\severe.exe 38510
C:\WINDOWS\system32\.exe 38510
C:\WINDOWS\system32\.dll 38400
C:\WINDOWS\system32\drivers\conime.exe 38,510
C:\WINDOWS\system32\severe.exe 38510
C:\WINDOWS\system32\.exe 38510
C:\WINDOWS\system32\.dll 38400
C:\WINDOWS\system32\hx1.dat 生成运行后自删除
C:\WINDOWS\system32\noruns.reg 生成运行后自删除
C:\WINDOWS\system32\kakatool.dll 删除卡卡助手的动态链接库
C:\WINDOWS\system32\kakatool.dll 删除卡卡助手的动态链接库
C:\WINDOWS\system32\drivers\etc\Hosts 1,465 字节 修改HOSTS文件,屏避对手的网站:
| 127.0.0.1 localhost 127.0.0.1 mmsk.cn 127.0.0.1 ikaka.com 127.0.0.1 safe.qq.com 127.0.0.1 360safe.com 127.0.0.1 [url]www.mmsk.cn[/url] 127.0.0.1 [url]www.ikaka.com[/url] 127.0.0.1 tool.ikaka.com 127.0.0.1 [url]www.360safe.com[/url] 127.0.0.1 zs.kingsoft.com 127.0.0.1 forum.ikaka.com 127.0.0.1 up.rising.com.cn 127.0.0.1 scan.kingsoft.com 127.0.0.1 kvup.jiangmin.com 127.0.0.1 reg.rising.com.cn 127.0.0.1 update.rising.com.cn 127.0.0.1 update7.jiangmin.com 127.0.0.1 download.rising.com.cn 127.0.0.1 dnl-us1.kaspersky-labs.com 127.0.0.1 dnl-us2.kaspersky-labs.com 127.0.0.1 dnl-us3.kaspersky-labs.com 127.0.0.1 dnl-us4.kaspersky-labs.com 127.0.0.1 dnl-us5.kaspersky-labs.com 127.0.0.1 dnl-us6.kaspersky-labs.com 127.0.0.1 dnl-us7.kaspersky-labs.com 127.0.0.1 dnl-us8.kaspersky-labs.com 127.0.0.1 dnl-us9.kaspersky-labs.com 127.0.0.1 dnl-us10.kaspersky-labs.com 127.0.0.1 dnl-eu1.kaspersky-labs.com 127.0.0.1 dnl-eu2.kaspersky-labs.com 127.0.0.1 dnl-eu3.kaspersky-labs.com 127.0.0.1 dnl-eu4.kaspersky-labs.com 127.0.0.1 dnl-eu5.kaspersky-labs.com 127.0.0.1 dnl-eu6.kaspersky-labs.com 127.0.0.1 dnl-eu7.kaspersky-labs.com 127.0.0.1 dnl-eu8.kaspersky-labs.com 127.0.0.1 dnl-eu9.kaspersky-labs.com 127.0.0.1 dnl-eu10.kaspersky-labs.com |
X:\autorun.inf (X在此指非系统盘,不包括移动设备)
X:\oso.exe (X在此指非系统盘,不包括移动设备)
U:\autorun.inf (U指移动设备 )
U:\oso.exe
U:\重要资料.exe
U:\美女游戏.pif
X:\oso.exe (X在此指非系统盘,不包括移动设备)
U:\autorun.inf (U指移动设备 )
U:\oso.exe
U:\重要资料.exe
U:\美女游戏.pif
注册表修改情况:
添加自启动项
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
60{
C:\WINDOWS\system32\.exe
60{
C:\WINDOWS\system32\.exe
---------------------
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
@ ---默认项
C:\WINDOWS\system32\severe.exe
@ ---默认项
C:\WINDOWS\system32\severe.exe
被映象劫持的软件名列表(
这次被劫持和软件名多了NOD32杀毒软件和EGHOST)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360Safe.exe
Debugger
C:\WINDOWS\system32\drivers\60{.exe 都是指向此项,以下不一一列述
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\adam.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avp.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IceSword.exe
Debugger
C:\WINDOWS\system32\drivers\60{.exe 都是指向此项,以下不一一列述
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\adam.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avp.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IceSword.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\EGHOST.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iparmo.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kabaload.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KRegEx.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KvDetect.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVMonXP.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KvXP.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MagicSet.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mmsk.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iparmo.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kabaload.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KRegEx.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KvDetect.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVMonXP.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KvXP.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MagicSet.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mmsk.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NOD32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PFW.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PFWLiveUpdate.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQDoctor.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ras.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rav.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMon.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\runiep.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SREng.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojDie.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WoptiClean.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PFW.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PFWLiveUpdate.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQDoctor.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ras.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rav.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMon.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.com
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\runiep.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SREng.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojDie.kxp
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WoptiClean.exe
用一个批处理hx1.dat
修改系统时间为2004-1-22 使防病毒软件失效
由于此病毒修改的内容较多手动修复相当麻烦,U盘病毒专杀工具USBCleaner可彻底清除此病毒。
此版本已在之官方网站发布,欢迎下载使用!
[url]http://nick429.135.hezu1.com/[/url]
永久转向域名: [url]http://nick429.126.com[/url]
友情提示:U盘病毒专杀工具USBCleaner 为免费绿色的查杀U盘类病毒木马的小工具
============================= 转载End================================
三、解决方法:
三、解决方法:
可以手动删除添加的非法 IFEO 劫持项目,重启后即可。
四、提示:
防止Image File Execution Options hijack(映象劫持)的方法是通过在SSM等行为防火墙中添加一条注册表的监控规则(如下图)来防御,具体可google ,或点此此处链接。
防止Image File Execution Options hijack(映象劫持)的方法是通过在SSM等行为防火墙中添加一条注册表的监控规则(如下图)来防御,具体可google ,或点此此处链接。
 图1
图1
 图2
图2
~~~~~~~~~ 如下设置图与SSM版本有关 仅供参考,原作: [email protected]
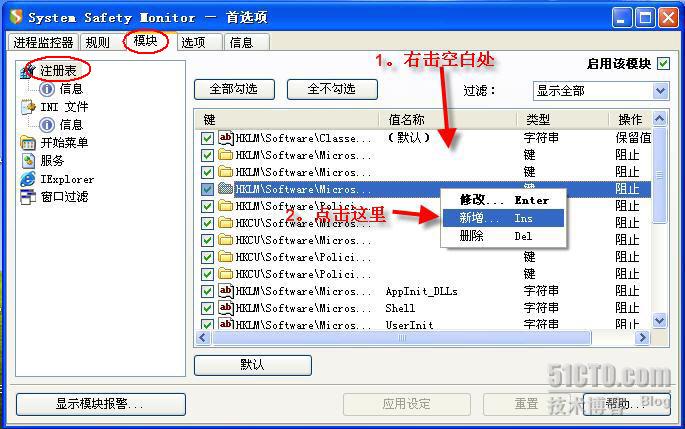





位置:HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution
五、部分技术内幕:
Image File Execution Options (IFEO in short)
五、部分技术内幕:
Image File Execution Options (IFEO in short)
You can set up your application to start Visual Studio when you launch the application from Windows. Visual Studio will load your application, ready for debugging, but will not commence debugging until you issue an execution command. Having Visual Studio launch the debugger in this way is useful for debugging services and COM out-of-proc servers.
To setup an application to launch the debugger automatically
- Start the Registry Editor (regedit).
- In the Registry Editor, open the HKEY_LOCAL_MACHINE folder.
- Navigate to HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\currentversion\image file execution options.
- Under the Image File Execution Options folder, locate the name of the application you want to debug (myapp.exe, for example). If you cannot find the application you want to debug:
- Right-click the Image File Execution Options folder and choose New Key from the shortcut menu.
- Right-click the new key and choose Rename from the shortcut menu.
- Edit the key name to the name of your application, for example,
myapp.exe.
- Right-click the myapp.exe folder and choose New String Value from the shortcut menu.
- Right-click the new string value and choose Rename from the shortcut menu.
- Change the name to
debugger. - Right-click the new string value and choose Modify from the shortcut menu.
The Edit String dialog box appears.
- In the Value data box, type
devenv /debugexe. - Click OK.
- From the Registry menu, choose Exit.
The directory containing devenv.exe must be in your system path.Now, use any method to start your application. Visual Studio .NET will start and load the application.
Note If the application is managed, Visual Studio launches with the Debugger Type set to Auto. Before you debug, change the Debugger Type from Auto to Mixed in the Property Pages dialog box. For more information, see Specifying Debugger Settings .
See Also
Using the Debugger
来自天下无毒