防火墙NAT Server实验
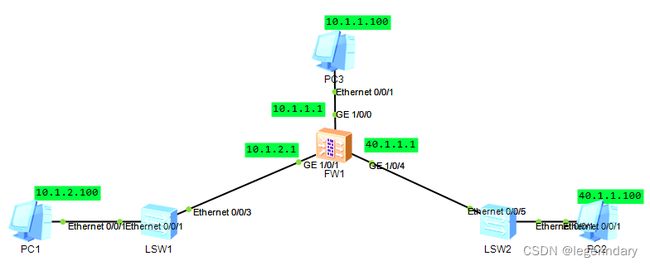
- 实验拓扑
2.实验步骤
步骤 1 完成 USG6330-1 上、下行业务接口的配置。配置各接口 IP 地址并加入相应安全区域。
[USG6000V1]sysname USG6330-1
[USG6330-1] interface GigabitEthernet 1/0/1
[USG6330-1-GigabitEthernet1/0/1] ip address 10.1.2.1 255.255.255.0
[USG6330-1-GigabitEthernet1/0/1] quit
[USG6330-1] interface GigabitEthernet 1/0/4
[USG6330-1-GigabitEthernet1/0/4] ip address 40.1.1.1 255.255.255.0
[USG6330-1-GigabitEthernet1/0/4] quit
[USG6330-1] firewall zone trust
[USG6330-1-zone-trust] add interface GigabitEthernet 1/0/1
[USG6330-1-zone-trust] quit
[USG6330-1] firewall zone untrust
[USG6330-1-zone-untrust] add interface GigabitEthernet 1/0/4
[USG6330-1-zone-untrust] quit
步骤 2 配置域间包过滤策略。
[USG6330-1]security-policy
[USG6330-1-policy-security] rule name bidectinal_nat
[USG6330-1-policy-security-rule-policy_sec] source-zone untrust
[USG6330-1-policy-security-rule-policy_sec] destination-zone dmz
[USG6330-1-policy-security-rule-policy_sec] action permit
[USG6330-1-policy-security-rule-policy_sec] service ftp
[USG6330-1-policy-security-rule-policy_sec] quit
步骤 3 配置 NAT server。
[USG6330-1] nat server ftpserver protocol tcp global 40.1.1.2 ftp inside 10.1.1.100 ftp
[USG6330-1]nat address-group natpool2
[USG6330-1-address-group-natpool]section 10.1.1.10 10.1.1.20
步骤 5 在 DMZ 与 Untrust 域间应用 NAT ALG 功能,使服务器可以正常对外提供 FTP 服务。
[USG6330-1] firewall interzone dmz untrust
[USG6330-1 -interzone-dmz-untrust] detect ftp
[USG6330-1 -interzone-dmz-untrust] quit
步骤 6 创建 DMZ 区域和 Untrust 区域之间的 NAT 策略,确定进行 NAT 转换的源地址范围,并且将其与 NAT 地址池 2 进行绑定。
[USG6330-1]nat-policy
[USG6330-1-policy-nat]rule name biderectinal_nat
[USG6330-1-policy-nat-rule-source_nat]destination-zone dmz
[USG6330-1-policy-nat-rule-source_nat]source-zone untrust
[USG6330-1-policy-nat-rule-source_nat]source-address 40.1.1.0 24
[USG6330-1-policy-nat-rule-source_nat]action nat address-group natpool2
步骤 7 配置 Switch。
分别将两台 Switch 的三个接口加入同一个 VLAN,缺省即可。