华为设备上的安全技术总结之dot1x
身份认证是计算机系统的用户在进入系统或访问不同保护级别的系统资源时,系统确认该用户的身份是否真实、合法和唯一的过程。使用身份认证的主要目的是防止非授权用户进入系统,同时防止非授权用户通过非正常操作访问受控信息或恶意破坏系统数据的完整性。近年来,越来越多的单位通过身份认证系统加密用户对网络资源的访问,在众多的解决方案中,Radius认证系统的使用最为广泛。在大量的企业、政府机关、高校,通过Radius认证系统,实现对用户网络访问身份的认证,以决定某一用户是否具有上网权限,并记录相关的信息 。
安全技术1: dot1x 与radius的 AAA服务器,
【实验目的】
①防火墙的单臂路由实现多Vlan间通信。
②利用防火墙的DHCP中继实现多Vlan动态获得地址。
③用户通过AAA认证,访问外网。
④远程带内管理(Telnet)各设备,需要AAA验证。
【拓扑规划】

配置命令
交换机配置
[Quidway]dis cu
#
sysname Quidway
#
super password level 3 simple 123456
#
local-server nas-ip 192.168.30.151 key 123456
#
domain default enable ty
#
dot1x
dot1x authentication-method pap
#
radius scheme system
radius scheme xxx
server-type standard
primary authentication 192.168.30.151
accounting optional
key authentication 123456
user-name-format without-domain
#
domain system
domain ty
scheme radius-scheme xxx
access-limit enable 10
accounting optional
#
vlan 1
#
vlan 10
#
vlan 20
#
vlan 30
#
interface Vlan-interface1
ip address 192.168.1.1 255.255.255.0
#
interface Aux1/0/0
#
interface Ethernet1/0/1
port access vlan 10
dot1x
#
interface Ethernet1/0/2
port access vlan 20
dot1x
#
interface Ethernet1/0/3
port access vlan 30
#
interface Ethernet1/0/4
port link-type trunk
port trunk permit vlan all
#
interface Ethernet1/0/5
#
interface Ethernet1/0/6
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 192.168.1.254 preference 60
#
user-interface aux 0
user-interface vty 0 4
authentication-mode scheme
#
return
防火墙配置
%Aug 12 18:10:37:367 2013 H3C SHELL/4/LOGIN: Console login from con0
sys
System View: return to User View with Ctrl+Z.
[H3C]dis cu
#
sysname H3C
#
super password level 3 simple 123456
#
domain default enable ty
#
firewall packet-filter enable
firewall packet-filter default permit
#
undo insulate
#
firewall statistic system enable
#
radius scheme system
server-type extended
radius scheme ty
server-type standard
primary authentication 192.168.30.151
key authentication 123456
user-name-format without-domain
#
domain system
domain ty
scheme radius-scheme ty
authentication local
access-limit enable 10
accounting optional
#
local-user admin
password cipher .]@USE=B,53Q=^Q`MAF4<1!!<>
service-type telnet terminal
level 3
service-type ftp
#
interface Aux0
async mode flow
#
interface Ethernet0/0
ip address 192.168.1.254 255.255.255.0
dhcp select relay
#
interface Ethernet0/0.10
ip address 192.168.10.1 255.255.255.0
ip relay address 192.168.30.100
dhcp select relay
vlan-type dot1q vid 10
#
interface Ethernet0/0.20
ip address 192.168.20.1 255.255.255.0
ip relay address 192.168.30.100
dhcp select relay
vlan-type dot1q vid 20
#
interface Ethernet0/0.30
ip address 192.168.30.1 255.255.255.0
dhcp select relay
vlan-type dot1q vid 30
#
interface Ethernet0/4
#
interface Encrypt1/0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
add interface Ethernet0/0
add interface Ethernet0/0.10
add interface Ethernet0/0.20
add interface Ethernet0/0.30
set priority 85
#
firewall zone untrust
set priority 5
#
firewall zone DMZ
set priority 50
#
firewall interzone local trust
#
firewall interzone local untrust
#
firewall interzone local DMZ
#
firewall interzone trust untrust
#
firewall interzone trust DMZ
#
firewall interzone DMZ untrust
#
FTP server enable
#
user-interface con 0
user-interface aux 0
user-interface vty 0 4
authentication-mode scheme
#
return
客户端认证

DHCP动态获得地址

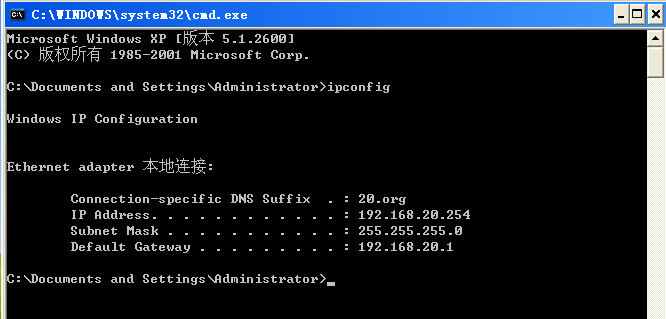
TELNET界面

安全技术2:对于dot1x下还用一种是基于mac地址的认证:【本地的 和acs的】
本地的
【实验目的】
通过在交换机上创建用户限制访问
基于客户机mac地址一种认证方式
【实验拓扑】
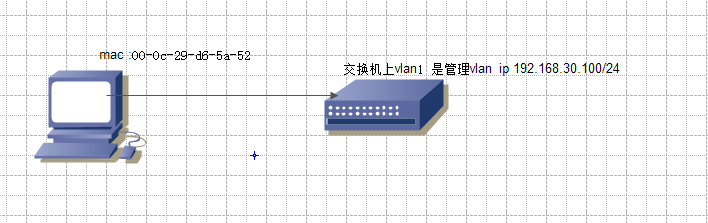
客服集地址 12.168.30.1
【实验配置】
交换机配置命令
[Quidway]dis cu
#
sysname Quidway
#
MAC-authentication
MAC-authentication authmode usernameasmacaddress usernameformat with-hyphen
#
radius scheme system
#
domain system
#
local-user 00-0c-29-d6-5a-52
password simple 00-0c-29-d6-5a-52
service-type lan-access
#
vlan 1
#
interface Vlan-interface1
ip address 192.168.30.100 255.255.255.0
#
interface Aux1/0/0
#
interface Ethernet1/0/1
#
interface Ethernet1/0/2
#
interface Ethernet1/0/3
#
interface Ethernet1/0/4
#
interface Ethernet1/0/5
#
interface Ethernet1/0/6
#
interface Ethernet1/0/7
#
interface Ethernet1/0/8
#
interface Ethernet1/0/9
#
interface Ethernet1/0/10
MAC-authentication
#
interface Ethernet1/0/11
#
interface Ethernet1/0/12
#
interface Ethernet1/0/13
#
interface Ethernet1/0/14
#
interface Ethernet1/0/15
#
#
interface NULL0
#
user-interface aux 0
user-interface vty 0 4
#
return
【实验验证】

基于acs的认证
【实验目的】
通过在交换机上创建用户限制访问
基于客户机mac地址一种认证方式
通过AAA服务器建立
【实验拓扑】

【实验配置】
dis cu
#
sysname Quidway
#
MAC-authentication
MAC-authentication authmode usernameasmacaddress usernameformat with-hyphen
#
radius scheme system
radius scheme xxx
server-type standard
primary authentication 192.168.30.151
accounting optional
key authentication 123456
user-name-format without-domain
#
domain system
scheme radius-scheme xxx
access-limit enable 10
accounting optional
#
vlan 1
#
interface Vlan-interface1
ip address 192.168.30.10 255.255.255.0
#
interface Aux1/0/0
#
interface Ethernet1/0/1
#
interface Ethernet1/0/2
#
interface Ethernet1/0/3
#
interface Ethernet1/0/4
#
interface Ethernet1/0/5
#
interface Ethernet1/0/6
#
interface Ethernet1/0/7
#
interface Ethernet1/0/8
#
interface Ethernet1/0/9
#
interface Ethernet1/0/10
#
interface Ethernet1/0/11
#
interface Ethernet1/0/12
#
interface Ethernet1/0/13
#
interface Ethernet1/0/14
#
interface Ethernet1/0/15
#
interface Ethernet1/0/16
#
interface Ethernet1/0/17
#
interface Ethernet1/0/18
#
interface Ethernet1/0/19
#
interface Ethernet1/0/20
#
interface Ethernet1/0/21
#
interface Ethernet1/0/22
#
interface Ethernet1/0/23
MAC-authentication
#
interface Ethernet1/0/24
#
interface NULL0
#
user-interface aux 0
user-interface vty 0 4
#
Return
【实验验证】
