MPLS(多协议标签交换)实验——华为设备
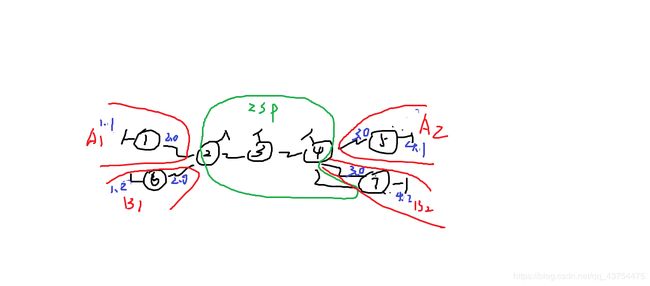
实验要求:中间ISP区域为公网,周围有四个私网,要求A公司可以ping通A公司,B公司可以ping通B公司,但是AB之间不互通,要求要涉及到MPLS技术来完成实验;
思路:
先配置ISP公网区域,要求将公网区域全网可达,这里利用OSPF协议;
然后整个公网的开启MPLS——MPLS LDP,然后在公网的所有接口上调用;
之后就是在与CE直连的PE上创建VR空间,然后将于CE直连的接口绑定到对应的VR空间里;
VR空间创建之后,就可以给CE路由器进行IP配置了,配置完IP之后,所有的CE都启用OSPF协议(也可以用静态,但是为了方便,就全部用动态协议);
CE启用OPSF协议后,要求CE与PE之间互通,在PE上再起一个工作在VR空间的OSPF协议进程,只宣告与CE直连的接口;
这时进行PE之间的MP-BGP邻居关系的建立,用来传递MPLS-VPN的路由;
最后在PE上进行双向重发布,将BGP和对应的OSPF进程互相进行重发布;
操作完成后,实验要求就达到了。
命令配置:
R1:
[V200R003C00]
#
sysname R1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack1
ip address 192.168.1.1 255.255.255.0
#
ospf 1
area 0.0.0.0
network 192.168.0.0 0.0.255.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R2:
[V200R003C00]
#
sysname R2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
ip -instance a
ipv4-family
route-distinguisher 1:1
-target 1:1 export-extcommunity
-target 1:1 import-extcommunity
#
ip -instance b
ipv4-family
route-distinguisher 2:2
-target 2:2 export-extcommunity
-target 2:2 import-extcommunity
#
mpls lsr-id 2.2.2.2
mpls
lsp-trigger all
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip binding -instance a
ip address 192.168.2.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 23.1.1.1 255.255.255.0
mpls
mpls ldp
#
interface GigabitEthernet0/0/2
ip binding -instance b
ip address 192.168.2.2 255.255.255.0
#
interface NULL0
#
interface LoopBack1
ip address 2.2.2.2 255.255.255.0
#
bgp 1
router-id 2.2.2.2
peer 4.4.4.4 as-number 1
peer 4.4.4.4 connect-interface LoopBack1
#
ipv4-family unicast
undo synchronization
peer 4.4.4.4 enable
peer 4.4.4.4 next-hop-local
#
ipv4-family v4
policy -target
peer 4.4.4.4 enable
#
ipv4-family -instance a
import-route ospf 2
#
ipv4-family -instance b
import-route ospf 3
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 2.2.2.2 0.0.0.0
network 23.1.1.1 0.0.0.0
area 0.0.0.1
#
ospf 2 -instance a
import-route bgp
area 0.0.0.0
network 192.168.2.2 0.0.0.0
#
ospf 3 -instance b
import-route bgp
area 0.0.0.0
network 192.168.0.0 0.0.255.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R3:
[V200R003C00]
#
sysname R3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
mpls lsr-id 3.3.3.3
mpls
lsp-trigger all
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 23.1.1.2 255.255.255.0
mpls
mpls ldp
#
interface GigabitEthernet0/0/1
ip address 34.1.1.1 255.255.255.0
mpls
mpls ldp
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack1
ip address 3.3.3.3 255.255.255.0
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 3.3.3.3 0.0.0.0
network 23.1.1.2 0.0.0.0
network 34.1.1.1 0.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R4:
[V200R003C00]
#
sysname R4
#
board add 0/2 1GEC
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
ip -instance a
ipv4-family
route-distinguisher 1:1
-target 1:1 export-extcommunity
-target 1:1 import-extcommunity
#
ip -instance b
ipv4-family
route-distinguisher 2:2
-target 2:2 export-extcommunity
-target 2:2 import-extcommunity
#
mpls lsr-id 4.4.4.4
mpls
lsp-trigger all
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 34.1.1.2 255.255.255.0
mpls
mpls ldp
#
interface GigabitEthernet0/0/1
ip binding -instance a
ip address 192.168.3.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 47.1.1.1 255.255.255.0
#
interface GigabitEthernet2/0/0
ip binding -instance b
ip address 192.168.3.1 255.255.255.0
#
interface NULL0
#
interface LoopBack1
ip address 4.4.4.4 255.255.255.0
#
bgp 1
router-id 4.4.4.4
peer 2.2.2.2 as-number 1
peer 2.2.2.2 connect-interface LoopBack1
#
ipv4-family unicast
undo synchronization
peer 2.2.2.2 enable
peer 2.2.2.2 next-hop-local
#
ipv4-family v4
policy -target
peer 2.2.2.2 enable
#
ipv4-family -instance a
import-route ospf 2
#
ipv4-family -instance b
import-route ospf 3
#
ospf 1 router-id 4.4.4.4
area 0.0.0.0
network 4.4.4.4 0.0.0.0
network 34.1.1.2 0.0.0.0
network 47.1.1.1 0.0.0.0
#
ospf 2 -instance a
import-route bgp
area 0.0.0.0
network 192.168.3.1 0.0.0.0
#
ospf 3 -instance b
import-route bgp
area 0.0.0.0
network 192.168.3.1 0.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R5:
[V200R003C00]
#
sysname R5
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.3.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack1
ip address 192.168.4.1 255.255.255.0
#
ospf 1
area 0.0.0.0
network 192.168.0.0 0.0.255.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R6:
[V200R003C00]
#
sysname R6
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack1
ip address 192.168.1.2 255.255.255.0
#
ospf 1
area 0.0.0.0
network 192.168.0.0 0.0.255.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R7:
[V200R003C00]
#
sysname R7
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 47.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.3.2 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack1
ip address 192.168.4.2 255.255.255.0
#
ospf 1
area 0.0.0.0
network 192.168.0.0 0.0.255.255
#
ip route-static 0.0.0.0 0.0.0.0 47.1.1.1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
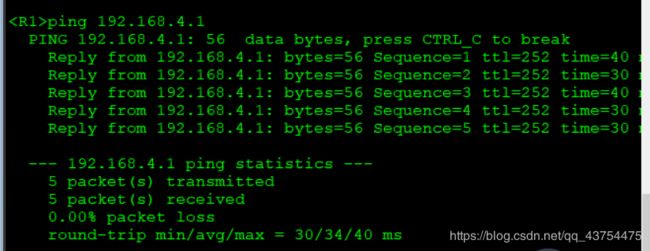
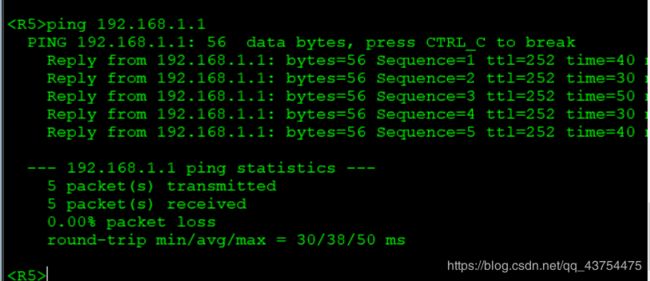
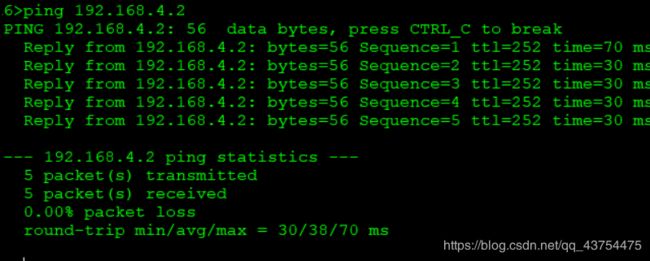
测试:
A1环回地址为192.168.1.1,A2环回地址为192.168.4.1
B1环回地址为192.168.1.2,B2环回地址为192.168.4.2
实验要求达成,实验完成。